- ssh command in Linux with Examples
- How to Use SSH Command in Linux
- Installing SSH
- On Ubuntu/Debian
- On RedHat/CentOS
- 1) SSH Commands
- Run SSH without no options
- Specify a username for login
- Specify the port
- Request compression on every data
- Define a cipher algorithm
- Turn on debug mode
- Bind source address
- Change the default configuration file
- Use SSH X11 Forwarding
- Trusted X11 Forwarding
- 2) SSH Options
- StrictHostKeyChecking
- ConnectTimeout
- BatchMode
- Batch mode command execution using SSH — success case
- Batch mode command execution using SSH — Failure case
- Bind IP Example
- Find the version of the SSH command
- 3) SSH Config with Examples
- /etc/ssh/ssh_config ( system-wide configuration file )
- SSH Config File options
- Sample Configuration file for testing with parameter
- Conclusion
ssh command in Linux with Examples
ssh stands for “Secure Shell”. It is a protocol used to securely connect to a remote server/system. ssh is secure in the sense that it transfers the data in encrypted form between the host and the client. It transfers inputs from the client to the host and relays back the output. ssh runs at TCP/IP port 22.
Syntax:
Example: Accessing ubuntu machine via windows10 command prompt using ssh
ssh command consists of 3 different parts:
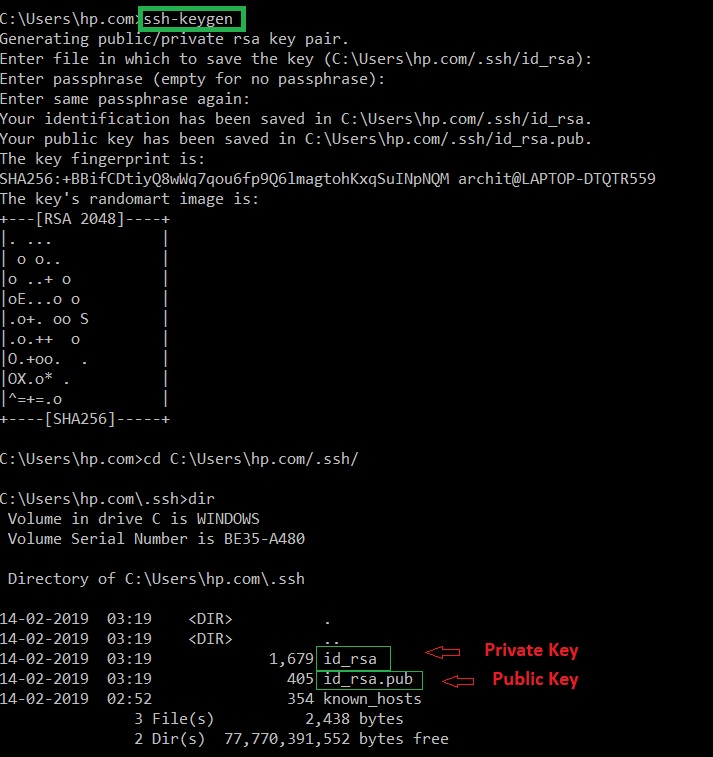
Note: After logging into the host computer, commands will work as if they were written directly to the host terminal. Using a public-private key pair or SSH key pair to login into the remote host is more secure as compared to using passwords. For generating public-private keys use the command:
The private key must remain hidden while the public key must be copied to the remote host. After copying the public key to the remote host the connection will be established using SSH keys and not the password.
Options:
- -1: Forces ssh to use protocol SSH-1 only.
- -2: Forces ssh to use protocol SSH-2 only.
- -4: Allows IPv4 addresses only.
- -6: Allows IPv6 addresses only.
- -A: Authentication agent connection forwarding is enabled.
- -a: Authentication agent connection forwarding is disabled.
- -C: Compresses all data (including stdin, stdout, stderr, and data for forwarded X11 and TCP connections) for a faster transfer of data.
- -f: Requests ssh to go to background just before command execution.
- -g: Allows remote hosts to connect to local forwarded ports.
- -n: Prevents reading from stdin.
- -p port_number: Port to connect to on the remote host.
- -q: Suppresses all errors and warnings
- -V: Display the version number.
- -v: Verbose mode. It echoes everything it is doing while establishing a connection. It is very useful in the debugging of connection failures
- -X: Enables X11 forwarding (GUI Forwarding).
- -c cipher_spec: Selects the cipher specification for encrypting the session. Specific cipher algorithm will be selected only if both the client and the server support it.
SSH is significantly more secure than the other protocols such as telnet because of the encryption of the data. There are three major encryption techniques used by SSH:
- Symmetrical encryption: This encryption works on the principle of the generation of a single key for encrypting as well as decrypting the data. The secret key generated is distributed among the clients and the hosts for a secure connection. Symmetrical encryption is the most basic encryption and performs best when data is encrypted and decrypted on a single machine.
- Asymmetrical encryption: This encryption is more secure because it generates two different keys: Public and Private key. A public key is distributed to different host machines while the private key is kept securely on the client machine. A secure connection is established using this public-private key pair.
- Hashing: One-way hashing is an authentication technique which ensures that the received data is unaltered and comes from a genuine sender. A hash function is used to generate a hash code from the data. It is impossible to regenerate the data from the hash value. The hash value is calculated at the sender as well as the receiver’s end. If the hash values match, the data is authentic.
Источник
How to Use SSH Command in Linux
SSH is a popular, powerful, software-based approach to network security. It is used for logging into a remote machine and for executing commands on a remote machine. Whenever data is sent by a computer to the network, ssh will automatically encrypt it. It is designed and created to provide the best security when accessing another computer remotely. SSH server, by default, listens on the standard TCP port 22.
To use SSH, the destination machine should have a SSH server application installed because SSH is a client-server model.
In this guide, we will learn about SSH command, configuration, usage and options on Linux system to help you connect to a remote server.
Installing SSH
Modern Linux should have installed SSH by default. If it’s not, we can install it manually. The easiest way to install SSH is through your Linux package manager.
On Ubuntu/Debian
Install ssh-client
Install ssh-server
On RedHat/CentOS
Once SSH is installed we can check it by typing ssh from your Linux console.
1) SSH Commands
Run SSH without no options
A common way to use SSH is without any options. Just type “ssh ”. Here’s a sample :
When the first time you connect to a destination host, ssh will confirm you about the authenticity of the destination host. If you answer No, then SSH will not continue while if you said Yes, SSH will continue.
The next time you login into the same host, SSH will not ask you a confirmation. The authenticity oft the host by default is saved under /home/user/.ssh folder in every user.
Specify a username for login
By default, ssh will try to connect using active user as a username. On the previous command, ssh will try to login into the server using a username named ‘pungki’. This is because user ‘pungki’ on the client side, is running ssh client.
What about if in the destination host, there is no user named ‘pungki’? Then you must supply a username that exist in the destination host. To specify the username from the beginning, use -l option
We can also type like this :
Specify the port
SSH default port is 22. Most modern Linux has port 22 open. If you run ssh without defining a port, then ssh will direct the request via port 22.
But some system administrator may change the default SSH port. Let say that the port now is 1234. To contact that host, use -p option followed by SSH port.
To change the port number, we need to modify the /etc/ssh/ssh_config.
Change it into another port, for example above, is 1234. Then restart the SSH service.
Request compression on every data
With this option, all data which sent and received via SSH will be compressed. The data still encrypted. To use compression with SSH, use -C option.
This option will be useful if your connection is slow, such as using a modem. But when you are using a fast connection such as LAN or higher, than compression will be slow down your transfer rate.
The level of compression can be controlled using -o option followed by CompressionLevel option. But this option will only applied for SSH-1.
Define a cipher algorithm
SSH provides some cipher algorithms to be used. These algorithms can be seen inside /etc/ssh/ssh_config or
/.ssh/config file (if exist).
Let say you want to use blowfish algorithm for encrypting your SSH session. Then you can put this line into your /etc/ssh/ssh_config or
By default, SSH will use 3des algorithm
Turn on debug mode
When we are not able to connect to the remote host, it is good to debug and find the exact error messages that causing the issue. Use the -v option for debugging the ssh client.
Bind source address
If your client has more than 2 IP Address, you might not know which IP Address is used to create a connection to the SSH server.
To solve this situation, we can use —b option which will bind an IP Address to SSH connection. This IP Address will be used as the source address of the connection.
On the server side, we can check the established connection to the server using netstat. We see that 192.168.0.200 connection is established.
Change the default configuration file
By default, ssh will use ssh configuration file which located in /etc/ssh/ssh_config. This file is applied to system wide. If you want to apply the particular setting to the specific user, you should put it in
/.ssh/config file. If you don’t see it, you can create it.
Here’s a sample of a custom ssh_config. This config is located in /home/pungki directory.
To use a specific config file, we can use -F option.
Use SSH X11 Forwarding
There are three types of port forwarding with SSH:
1. Local port forwarding : connections from the SSH client are forwarded via the SSH server, then to a destination server
2. Remote port forwarding : connections from the SSH server are forwarded via the SSH client, then to a destination server
3. Dynamic port forwarding : connections from various programs are forwarded via the SSH client, then via the SSH server, and finally to several destination servers
Local Port Forwarding
This would forward two connections, one to 172.18.19.23, the other to 172.18.19.20. Pointing your browser at http://localhost:8080/ would download pages from 172.18.19.23, and pointing your browser to http://localhost:12345/ would download pages from 172.18.19.20.
Remote Port Forwarding
The -R option specifies remote port forwarding. For the duration of the SSH session, ec2-52-66-84-114.ap-south-1.compute.amazonaws.com would be able to access your desktop by connecting a VNC client to port 5900 on his computer (if you had set up a shared desktop)
Dynamic Port Forwarding
The -D option specifies dynamic port forwarding. 1001 is the standard SOCKS port. Although you can use any port number, some programs will only work if you use 1001. -C enables compression, which speeds the tunnel up when proxying mainly text-based information (like web browsing), but can slow it down when proxying binary information (like downloading files).
Next, you would tell Firefox to use your proxy:
Forwarding GUI Programs
Once the connection is made, type the name of your GUI program on the SSH command-line:
Trusted X11 Forwarding
If you pretty sure that your network is secure, then you may want to use Trusted X11 Forwarding. This mean that the remote X11 clients will have full access to the original X11 display. To use this option, we can use -Y option.
2) SSH Options
Lets check what all are the ssh options available.
StrictHostKeyChecking
If you would like to bypass this verification step, you can set the «StrictHostKeyChecking» option to «no» on the command line.
This option disables the prompt and automatically adds the host key to the
ConnectTimeout
I’m executing a script connecting via password-less SSH on a remote host. I want to set a timeout, so that if the remote host is taking an infinite time to run, I want to comeout of that ssh session and continue other lines in my sh script.
BatchMode
If you use ssh -o “BatchMode yes”, and password less connectivity is enable the command execute successfully on remote, else it will return error and continues.
Batch mode command execution using SSH — success case
[Note: This will display the output of remote-host’s who command]
Batch mode command execution using SSH — Failure case
Note: If you didn’t use -o “BatchMode yes”, the above command would’ve asked for the password for my account on the remote host. This is the key difference in using the BatchMode yes option.
Bind IP Example
Find the version of the SSH command
We can find the version of SSH installed on the unix system using the -V option to the ssh.
This is shown below:
-v option for run ssh command in Verbose mode.
Causes ssh to print debugging messages about its progress. This is helpful in debugging connection, authentication, and configuration problems. Multiple -v options increase the verbosity and the maximum is 3.
3) SSH Config with Examples
There is two main configuration files for SSH.
/.ssh/config ( Per-user’s configuration file )
This file is used by the SSH client. this file must have strict permissions: read/write for the user, and not accessible by others. We use all parameter in this file for accessing another computer remotely. This files called client configuration files
/etc/ssh/ssh_config ( system-wide configuration file )
This file provides defaults for those values that are not specified in the user’s configuration file, and for those users who do not have a configuration file. This file must be world-readable. all parameter defined in this file world-readable.
SSH Config File options
The /etc/ssh/ssh_config file is the system-wide configuration file for Open SSH which allows you to set options
that modify the operation of the client programs. The file contains keyword-value pairs, one per line, with keywords being case insensitive.
Here are the most important keywords to configure your ssh for top security.
Description of config file parameter
The option Host restricts all forwarded declarations and options in the configuration file to be only for those hosts that match one of the patterns given after the keyword. The pattern * means for all hosts up to the next Host keyword. With this option, you can set different declarations for different hosts in the same ssh_config file.
The option ForwardAgent specifies which connection authentication agent if any should be forwarded to the remote machine.
The option ForwardX11 is for people that use the Xwindow GUI and want to automatically redirect X11 sessions to the remote machine. Since we setup a server and don’t have GUI installed on it, we can safely turn this option off.
The option RhostsAuthentication specifies whether we can try to use rhosts based authentication. Because rhosts authentication is insecure you shouldn’t use this option.
The option RhostsRSAAuthentication specifies whether or not to try rhosts authentication in concert with RSA host authentication.
The option RSAAuthentication specifies whether to try RSA authentication. This option must be set to yes for better security on your sessions. RSA uses public and private keys pair created with the ssh-keygen1utility for authentication purposes.
The option PasswordAuthentication specifies whether we should use password-based authentication. For strong security. This option must always be set to yes. this parameter protect your server connectivity to other
without password no one connect to server.
The option FallBackToRsh specifies that if a connection with ssh daemon fails rsh should automatically be used instead. Recalling that rsh service is insecure, this option must always be set to no.
The option UseRsh specifies that rlogin/rsh services should be used on this host. As with the FallBackToRsh option, it must be set to no for obvious reasons.
The option BatchMode specifies whether a username and password querying on connect will be disabled. This option is useful when you create scripts and dont want to supply the password. e.g. Scripts that use the scp command to make backups over the network.
The option CheckHostIP specifies whether or not ssh will additionally check the host IP address that connect to the server to detect DNS spoofing. It’s recommended that you set this option to yes.
The option StrictHostKeyChecking specifies whether or not ssh will automatically add new host keys to the $HOME/.ssh/known_hosts file, or never automatically add new host keys to the host file. This option, when set to yes, provides maximum protection against Trojan horse attacks. One interesting procedure with this option is to set it to no at the beginning, allow ssh to add automatically all common hosts to the host file as they are connected to, and then return to set it to yes to take advantage of this feature.
The option IdentityFile specifies an alternate RSA authentication identity file to read. Also, multiple identity files may be specified in the configuration file ssh_config.
The option Cipher specifies what cipher should be used for encrypting sessios. The blowfish use 64-bit blocks and keys of up to 448 bits.
The option EscapeChar specifies the session escape character for suspension.
Sample Configuration file for testing with parameter
We have create /export/oracle/db/config/ssh/config.922pw using multiple parameter for testing .
When we try to connect remote server with our configuration files , all parameter call in ssh connectivity.
Please find the below out of ssh connectivity with config file .
Conclusion
As usual, we can always type man ssh and man ssh_config to display its manual pages and explore more detail. Hope you enjoyed reading and please leave your suggestions in the below comment section.
Источник