- Aircrack-ng
- User Tools
- Site Tools
- Table of Contents
- Installing Aircrack-ng from Source
- Requirements
- Linux
- Windows (Cygwin)
- FreeBSD, OpenBSD, NetBSD, Solaris
- Optional stuff
- Compiling and installing
- Current version
- Compiling with AirPcap support (cygwin only)
- Compiling on *BSD
- Compiling on OS X
- Latest Git (development) Sources
- ./configure flags
- Troubleshooting Tips
- error while loading shared libraries: libaircrack-ng.so.0
- «command not found» error message
- Installing pre-compiled binaries
- Linux/BSD/OSX
- Windows
- Hacking. Wi-Fi Penetration on MacOS
- installation requirements
- identify the target access point
- capturing a traffic
- brute forcing
- my results
- conclusion
- additional information
- You May Also Enjoy
- DELL. Configure Dell 10 gigabit switch with Ansible
- DELL. Upgrade firmware on Dell S4048 switch (S-series, OS9)
- DELL. Disabling SupportAssist on switch
- DELL. Setup SSH server on OS9 switch (S4048 10G switch)
- richardsonlima / Cracking WPA2 WEP Wifi Aircrack 10 seconds guide For Mac OSX Sierra
- This comment has been minimized.
- stepheljobs commented Dec 18, 2017
- This comment has been minimized.
- endianoia commented Dec 26, 2017
- This comment has been minimized.
- mmaffet commented Feb 15, 2018
- This comment has been minimized.
- fadlisaad commented Jun 3, 2018
- This comment has been minimized.
- AndriRomansky commented Dec 12, 2018
- This comment has been minimized.
- JamPlayz commented Apr 26, 2019
- This comment has been minimized.
- ghost commented Oct 6, 2019
- Aircrack ng install mac os
Aircrack-ng
User Tools
Site Tools
Table of Contents
Installing Aircrack-ng from Source
Legacy information can be found here.
Requirements
Linux
Windows (Cygwin)
Install the following via Homebrew (brew):
FreeBSD, OpenBSD, NetBSD, Solaris
Install the following via pkg:
Optional stuff
Compiling and installing
Current version
Compiling with AirPcap support (cygwin only)
Compiling on *BSD
Commands are exactly the same as Linux but instead of make, use gmake (with CC=gcc5 CXX=g++5 or any more recent gcc version installed).
Compiling on OS X
Commands are exactly the same as Linux
Latest Git (development) Sources
Note: Compilation parameters can also be used with the sources from our git repository.
./configure flags
When configuring, the following flags can be used and combined to adjust the suite to your choosing:
Troubleshooting Tips
error while loading shared libraries: libaircrack-ng.so.0
Run ldconfig as root or with “sudo” to solve the issue.
«command not found» error message
After you do “make install” then try to use any of the Aircrack-ng suite commands, you get the error message “command not found” or similar. Your system will look for the Aircrack-ng commands in the directories defined by the PATH command.
Normally, the Aircrack-ng suite programs and man pages are placed in:
On your system, to determine which directories have the Aircrack-ng programs enter the following. If using “locate” be sure to first run “updatedb”.
Once you know the directories (exclude the source directories) then determine which directories are in your PATH. To see which directories are included in PATH on your particular system enter:
It should show something like:
At this point compare the actual locations with the directories in your PATH. If the directories are missing from your PATH then you have a few options:
Installing pre-compiled binaries
Linux/BSD/OSX
We offer packages for a number of Linux distributions in 64 bit thanks to PackageCloud.io so you can use your distro’s package manager to install and keep Aircrack-ng up to date:
While most folks want to use our “release” packages, “git” packages are available too for those who decide to use bleeding edge.
More details about them can be found in our blog post.
On OSX, install it is via Macports or brew. Simply do “brew install aircrack-ng” or “sudo ports install aircrack-ng”
Windows
The Windows version of the Aircrack-ng suite does not have an install program. You must manually install (unzipping archive) the software.
Here are the steps to follow for Windows:
Prior to using the software, make sure to install the drivers for your particular wireless card. See this link for the instructions. We currently only support Airpcap; other adapters may be supported but require development of your own DLL so the different tools can interact with it.
To now use the Aircrack-ng suite, start Windows Explorer and double click on Aircrack-ng GUI .exe inside “bin” subdirectory. The GUI requires .NET version 4.6.1 to run.
Источник
Hacking. Wi-Fi Penetration on MacOS
Disclaimer: this post for education purposes only.
A wireless network with WPA/WPA security not guarantee a total safety. WiFi packets could be sniffed by an attacker that can stole a WiFi passwords, then he connects to your secured network. But he is need to decode a hash of password. The complexity and time to get a password phrase completely depends on the password. Passwords consists only digits cracks minutes or hours, the password “HasGUS%f@$SAfga63efSA%$S(SACSASj)” require a hundred years to crack it.
MacOS isn’t known as an ideal operating system for hacking without customization, but it includes native tools that allow easy control of the Wi-Fi radio for packet sniffing. Changing channels, scanning for access points, and even capturing packets all can be done from the command line.
This manual show a manual to crack WiFi password from my MacBook Pro with MacOS 10.13 (HighSierra). I want to save the instruction to the future. If you want to repeat it you should familiar with console terminal.
Let’s start cracking 😉
installation requirements
Install [JamWifi][https://github.com/0x0XDev/JamWiFi] app. It is a deauthenticating application in which unwanted clients from a Wi-Fi network have to keep off, jamming and especially their connection will be departed like dust in a second. Download and unzip by this link.
Test that all tools installed and available. The commands below should success return some help page about itself:
identify the target access point
- Basic Service Set Identifier (BSSID).
- Service Set Identifier (SSID).
- Radio Frequency (Channel).
- Access Point (AP).
Now, this command will be scanning the available Wi-Fi.
Wait till the installation is done. 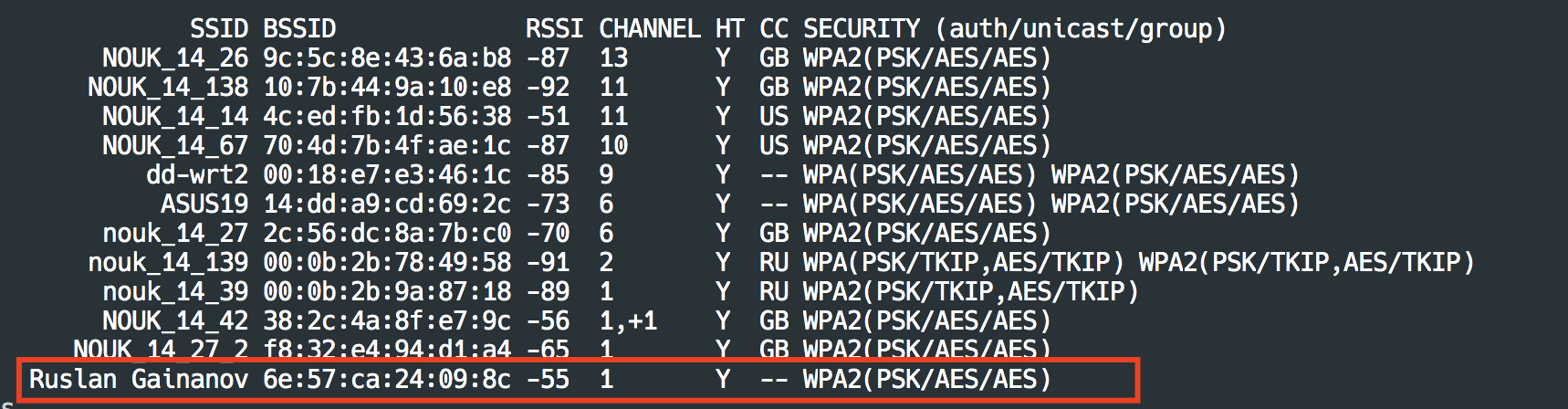
Copy the BSSID (my BSSID= 6e:57:ca:24:09:8c ) of the target Access Point.
capturing a traffic
- Run a command to help find a wireless interface ( en0 )
Deauth connected devices with Jam Wi-Fi app. Open the app. Press Scan, chose the target network and press Monitor, then press Do It! to restart all connections. Wait 15 seconds and press Done
When you “Done” with death, run quickly next command. You have to capture a handshake in time
Wait until you see some gotten frames, like this
After you have it press «Control + C» to stop capturing.
Merge the Beacon and Handshake
brute forcing
- Brute Force — A brute-force attack consists of an attacker submitting many passwords or passphrases with the hope of eventually guessing correctly.
- Wordlist — A written collection of all words derived from a particular source.
.1. Generating HCCPAX File
Hashcat doesn’t take cap files, only hccapx files. So we need convert this files. Other way to made it is use a online tool.
Review the result. You should see the phrase Networks detected: X. Written X WPA Handshakes . The example of success result is:
.2. Now, everything are right to execute the hashcat. We can use a wordlist or a pattern to broke a password. Using a wordlist (example of wordlists — https://github.com/kennyn510/wpa2-wordlists.git):
Using a pattern — 8 digits:
For more examples press here. For more patterns, see the documentation.
my results
I use the hashcat with pattern, that works on GPU. On my MacBook Pro, it yields a performance of 41kH/s: it tests 41000 passwords in a second.
The cracking a WiFi password consists 8 digits took me twenty minutes (20 mins, 17 secs).
Is true that my network named Ruslan Gainanov has a password — 12345670 .
conclusion
Please be aware that attacking Wi-Fi Protected Access (WPA) is illegal unless you have permission from the owner’s access point or affiliation involved. This post should be used as Educational Purposes, to help the public understand how hackers take advantage of your access.
additional information
- Youtube Video — video example of hacking WiFi password
- Hacking: Aircrack-ng on Mac OsX — Cracking wi-fi without kali in parallels — the blog article that I based
- Hacking: Wi-Fi Penetration on MacOS — another good article on Medium
- Cracking WPA/WPA2 with hashcat — brief manual of hashcat using
- New attack on WPA/WPA2 using PMKID — a new technique to crack WPA PSK without capturing a full EAPOL 4-way handshake
Updated: July 17, 2020
You May Also Enjoy
DELL. Configure Dell 10 gigabit switch with Ansible
Use Ansible playbooks to easy configure Dell Networking OS9 system. The post contains many practical examples of using dellos9 modules
DELL. Upgrade firmware on Dell S4048 switch (S-series, OS9)
Instructions for upgrading the last firmware of Dell Networking system.
DELL. Disabling SupportAssist on switch
SupportAssist is a daemon for sending technical reports to Dell servers. It enables by default. Here we disable this unwanted feature (and may be unsecured).
DELL. Setup SSH server on OS9 switch (S4048 10G switch)
Setup and configure ssh server on Dell Networking system with RSA and password authentication.
Источник
richardsonlima / Cracking WPA2 WEP Wifi Aircrack 10 seconds guide For Mac OSX Sierra
| 1 — Install Home Brew. |
| /usr/bin/ruby -e «$(curl -fsSL https://raw.githubusercontent.com/Homebrew/install/master/install)» |
| 2 — Install aircrack-ng: |
| brew install aircrack-ng |
| 3 — Install the latest Xcode, with the Command Line Tools. |
| //Create the following symlink: |
| sudo ln -s /System/Library/PrivateFrameworks/Apple80211.framework/Versions/Current/Resources/airport /usr/local/bin/airport//Figure out which channel you need to sniff: |
| sudo airport -s |
| sudo airport en1 sniff [CHANNEL] |
| 4 — New Terminal Window |
| aircrack-ng -1 -a 1 -b [TARGET_MAC_ADDRESS] [CAP_FILE] |
| // Notes: the cap_file will be located in the /tmp/airportSniff*.cap. |
This comment has been minimized.
Copy link Quote reply
stepheljobs commented Dec 18, 2017
is this working? how to get the cap file?
This comment has been minimized.
Copy link Quote reply
endianoia commented Dec 26, 2017
@stepheljobs the file is like /tmp/airportSniff*.cap , as we can see the notes says.
This comment has been minimized.
Copy link Quote reply
mmaffet commented Feb 15, 2018
Hi!
I got this message:
«Opening airportSnifft****.cap
No matching network found — check your bssid.
Quitting aircrack-ng. »
I set the [TARGET_MAC_ADDRESS] with «14:5f:94:::**»
What i doing wrong?
This comment has been minimized.
Copy link Quote reply
fadlisaad commented Jun 3, 2018
it would take a very long time to generate enough iv before getting even one key. In my case,
[00:00:06] Tested 818473 keys (got 33593 IVs) this take the whole 12 hours since the target may have little network activity
This comment has been minimized.
Copy link Quote reply
AndriRomansky commented Dec 12, 2018
help me.
i got message
macs-MacBook-Pro:
mac$ /tmp/airportSniffk1CJMa.cap
-bash: /tmp/airportSniffk1CJMa.cap: Permission denied
and (comand : /tmp/airportSniff*.cap)
mac$ /tmp/airportSniff*.cap
-bash: /tmp/airportSniffk1CJMa.cap: Permission denied
This comment has been minimized.
Copy link Quote reply
JamPlayz commented Apr 26, 2019
I did not see any cap file open for me?
This comment has been minimized.
Copy link Quote reply
ghost commented Oct 6, 2019
Plase Help Me;
[1] 97518 segmentation fault sudo airport en0 sniff 8
Источник
Aircrack ng install mac os

Aircrack-ng is a complete suite of tools to assess WiFi network security.
It focuses on different areas of WiFi security:
- Monitoring: Packet capture and export of data to text files for further processing by third party tools.
- Attacking: Replay attacks, deauthentication, fake access points and others via packet injection.
- Testing: Checking WiFi cards and driver capabilities (capture and injection).
- Cracking: WEP and WPA PSK (WPA 1 and 2).
All tools are command line which allows for heavy scripting. A lot of GUIs have taken advantage of this feature. It works primarily on Linux but also Windows, macOS, FreeBSD, OpenBSD, NetBSD, as well as Solaris and even eComStation 2.
- Autoconf
- Automake
- Libtool
- shtool
- OpenSSL development package or libgcrypt development package.
- Airmon-ng (Linux) requires ethtool, usbutils, and often pciutils.
- On Windows, cygwin has to be used and it also requires w32api package.
- On Windows, if using clang, libiconv and libiconv-devel
- Linux: LibNetlink 1 or 3. It can be disabled by passing —disable-libnl to configure.
- pkg-config (pkgconf on FreeBSD)
- FreeBSD, OpenBSD, NetBSD, Solaris and OS X with Macports: gmake
- Linux/Cygwin: make and Standard C++ Library development package (Debian: libstdc++-dev)
Note: Airmon-ng only requires pciutils if the system has a PCI/PCIe bus and it is populated. Such bus can be present even if not physically visible. For example, it is present, and populated on the Raspberry Pi 4, therefore pciutils is required on that device.
- If you want SSID filtering with regular expression in airodump-ng (-essid-regex) PCRE development package is required.
- If you want to use airolib-ng and ‘-r’ option in aircrack-ng, SQLite development package >= 3.3.17 (3.6.X version or better is recommended)
- If you want to use Airpcap, the ‘developer’ directory from the CD/ISO/SDK is required.
- In order to build besside-ng , besside-ng-crawler , easside-ng , tkiptun-ng and wesside-ng , libpcap development package is required (on Cygwin, use the Airpcap SDK instead; see above)
- rfkill
- If you want Airodump-ng to log GPS coordinates, gpsd is needed
- For best performance on SMP machines, ensure the hwloc library and headers are installed. It is strongly recommended on high core count systems, it may give a serious speed boost
- CMocka for unit testing
- For integration testing on Linux only: tcpdump, HostAPd, WPA Supplicant and screen
Installing required and optional dependencies
Below are instructions for installing the basic requirements to build aircrack-ng for a number of operating systems.
Note: CMocka, tcpdump, screen, HostAPd and WPA Supplicant should not be dependencies when packaging Aircrack-ng.
Note: autoconf, automake, libtool, and pkgconfig in the repositories are too old. The script centos_autotools.sh automatically installs dependencies to compile then install the tools.
Note: Community repository needs to be enabled for iw
Note: hostapd must be compiled manually, it is not present in the repository
XCode, Xcode command line tools and HomeBrew are required.
Cygwin requires the full path to the setup.exe utility, in order to automate the installation of the necessary packages. In addition, it requires the location of your installation, a path to the cached packages download location, and a mirror URL.
An example of automatically installing all the dependencies is as follows:
To build aircrack-ng , the Autotools build system is utilized. Autotools replaces the older method of compilation.
NOTE: If utilizing a developer version, eg: one checked out from source control, you will need to run a pre- configure script. The script to use is one of the following: autoreconf -i or env NOCONFIGURE=1 ./autogen.sh .
First, ./configure the project for building with the appropriate options specified for your environment:
TIP: If the above fails, please see above about developer source control versions.
Next, compile the project (respecting if make or gmake is needed):
Compilation on *BSD or Solaris:
Finally, the additional targets listed below may be of use in your environment:
Execute all unit testing:
Execute all integration testing (requires root):
When configuring, the following flags can be used and combined to adjust the suite to your choosing:
with-airpcap=DIR: needed for supporting airpcap devices on windows (cygwin or msys2 only) Replace DIR above with the absolute location to the root of the extracted source code from the Airpcap CD or downloaded SDK available online. Required on Windows to build besside-ng , besside-ng-crawler , easside-ng , tkiptun-ng and wesside-ng when building experimental tools. The developer pack (Compatible with version 4.1.1 and 4.1.3) can be downloaded at https://support.riverbed.com/content/support/software/steelcentral-npm/airpcap.html
with-experimental: needed to compile tkiptun-ng , easside-ng , buddy-ng , buddy-ng-crawler , airventriloquist and wesside-ng . libpcap development package is also required to compile most of the tools. If not present, not all experimental tools will be built. On Cygwin, libpcap is not present and the Airpcap SDK replaces it. See —with-airpcap option above.
with-ext-scripts: needed to build airoscript-ng , versuck-ng , airgraph-ng and airdrop-ng . Note: Each script has its own dependencies.
with-gcrypt: Use libgcrypt crypto library instead of the default OpenSSL. And also use internal fast sha1 implementation (borrowed from GIT) Dependency (Debian): libgcrypt20-dev
with-duma: Compile with DUMA support. DUMA is a library to detect buffer overruns and under-runs. Dependencies (debian): duma
disable-libnl: Set-up the project to be compiled without libnl (1 or 3). Linux option only.
without-opt: Do not enable stack protector (on GCC 4.9 and above).
enable-shared: Make OSdep a shared library.
disable-shared: When combined with enable-static, it will statically compile Aircrack-ng.
with-avx512: On x86, add support for AVX512 instructions in aircrack-ng. Only use it when the current CPU supports AVX512.
with-static-simd=: Compile a single optimization in aircrack-ng binary. Useful when compiling statically and/or for space-constrained devices. Valid SIMD options: x86-sse2, x86-avx, x86-avx2, x86-avx512, ppc-altivec, ppc-power8, arm-neon, arm-asimd. Must be used with —enable-static —disable-shared. When using those 2 options, the default is to compile the generic optimization in the binary. —with-static-simd merely allows to choose another one.
enable-maintainer-mode: It is important to enable this flag when developing with Aircrack-ng. This flag enables additional compile warnings and safety features.
Источник