- Инструменты Kali Linux
- Список инструментов для тестирования на проникновение и их описание
- airgeddon
- Описание airgeddon
- Справка по airgeddon
- Руководство по airgeddon
- Примеры запуска airgeddon
- Установка airgeddon
- Penetration Testing Tools
- Kali Linux Tools Listing
- airgeddon
- airgeddon Description
- airgeddon Help
- airgeddon Usage Example
- How to install airgeddon
- Ethical hacking and penetration testing
- InfoSec, IT, Kali Linux, BlackArch
- The easiest and fastest ways to hack Wi-Fi (using airgeddon)
- Software requirements
- Hardware requirements
- How to install airgeddon in Kali Linux
- How to run airgeddon in Kali Linux
- Automated WEP attack
- Automated WPS attack
- Pixie Dust attack
- Known PINs database based attack
- Bruteforce PIN attack
- Custom PIN association
- WPA/WPA2 attack
- Conclusion
Инструменты Kali Linux
Список инструментов для тестирования на проникновение и их описание
airgeddon
Описание airgeddon
airgeddon — это многофункциональный Баш скрипт для систем Linux по аудиту беспроводных сетей.
- Переключение режима интерфейса монитор-управляемый (Monitor-Managed) и сохранение выбора даже при изменении имени интерфейса.
- DoS на беспроводные сети различными методами.
- Помощь в захвате рукопожатия.
- Очистка и оптимизация файлов рукопожатий
- Оффлайн расшифровка паролей из захваченных файлов WPA/WPA2 (по словарю, брут-форс и атака, основанная на правилах).
- Атаки Злой Двойник (мошенническая точка доступа):
- Версия с только мошеннической/файльшивой ТД, для сниффинга используется внешний сниффер (Hostapd + DHCP + DoS).
- Простой встроенный сниффер (Hostapd + DHCP + DoS + ettercap).
- Встроенный сниффинг, sslstrip (Hostapd + DHCP + DoS + Ettercap + Sslstrip).
- Встроенный сниффинг, sslstrip2 и инструмент эксплуатации браузеров BeEF (Hostapd + DHCP + DoS + Bettercap + BeEF).
- Перехватывающий портал с «чёрной дырой DNS» для захвата wifi паролей (Hostapd + DHCP + DoS + Dnsspoff + Lighttpd).
- Опциональный спуфинг MAC для атак Злой Двойник.
- WPS функции:
- WPS сканирование (wash). Самопараметризация для избегания проблемы «bad fcs».
- Ассоциация с пользовательскими PIN (bully и reaver).
- Pixie Dust атаки (bully и reaver).
- Атаки брут-форса PIN attacks (bully и reaver).
- Параметрируемые тайм-ауты.
- Атака по известным WPS PIN’ам (bully и reaver), основывается на онлайн базе PIN’ов с автоматическим обновлением.
- Интеграция самых распространённых алгоритмов генерации PIN.
- Атаки всё-в-одном на WEP (комбинирование различных техник: Chop-Chop, Caffe Latte, Hirte, Fragmentation, Fake association и т.д.)
- Совместимость со многими дистрибутивами Linux.
- Простая навигация и выбор в каждой секции.
- Перетаскивание файлов в окно консоли для ввода путей.
- Динамическое определение разрешения экрана и автоматический размер окон для оптимального вида.
- Контроль за выходом, задачами очистки и временными файлами. Опции для сохранения режима монитора если нужно.
- Поддержка нескольких языков и функция автоматического определения языка ОС.
- Подсказки в каждом разделе/меню для простоты использования.
- Автоматическое обновление. Если возможно, скрипт проверяет наличие новой версии.
- Контейнер Docker для простого и быстрого развёртывания
- Автоматическое определение Http прокси для обновлений
Справка по airgeddon
Справка отсутствует, управление осуществляется через текстовое меню. В настоящее время скрипт полностью русифицирован.
Руководство по airgeddon
Страница man отсутствует.
Примеры запуска airgeddon
Программа требует привилегий суперпользователя:
Установка airgeddon
Установка в Kali Linux
Установка в BlackArch
Программа предустановлена в BlackArch.
Установка в Debian, Linux Mint, Ubuntu
Невозможна совместимость с OSX и Windows.
Информация об установке в другие операционные системы будет добавлена позже.
Зависимости airgeddon
Bash версии 4 или более поздняя.
Протестировано на следующих совместимых дистрибутивах:
- Kali 2.0, 2016.1, 2016.2 и arm версиях (Raspberry Pi)
- Wifislax 4.11.1 и 4.12 и 64-1.0
- Backbox 4.5.1 и 4.6
- Parrot 2.2.1, 3.4.1 и arm versions (Raspberry Pi)
- BlackArch с 2016.01.10 до 2016.12.29
- Cyborg Hawk 1.1
- Debian 7 (Wheezy) и 8 (Jessie)
- Ubuntu/Xubuntu 15.10, 16.04 и 16.04.1
- OpenSUSE Leap 42.1 и 42.2
- CentOS 6 и 7
- Gentoo 20160514 и 20160704
- Fedora 24
- Red Hat 7 (Maipo)
- Arch с 4.6.2-1 до 4.8.13-1
- Raspbian 7 (Wheezy) и 8 (Jessie) (Raspberry Pi)
- OpenMandriva LX3
airgeddon уже включён в некоторые дистрибутивы Linux и репозитории:
- Wifislax 4.12, 64-1.0 или выше
- BlackArch впервые в релизе 2017 или позже
- ArchStrike репозиторий.
В любом случае, скрипт можно использовать на любом дистрибутиве Linux, если вы установили инструменты, которые требуются скрипту. Скрипт проверяет на их наличие при своём запуске.
Опциональные инструменты: aircrack-ng
Инструменты для обновления: curl
Внутренние инструменты: x11-utils / xdpyinfo / xorg-xdpyinfo
Источник
Penetration Testing Tools
Kali Linux Tools Listing
airgeddon
airgeddon Description
This is a multi-use bash script for Linux systems to audit wireless networks.
Features
- Interface mode switcher (Monitor-Managed) keeping selection even on interface name changing
- DoS over wireless networks using different methods
- Assisted Handshake file capturing
- Cleaning and optimizing Handshake captured files
- Offline password decrypting on WPA/WPA2 captured files (dictionary, bruteforce and rule based)
- Evil Twin attacks (Rogue AP)
- Only Rogue/Fake AP version to sniff using external sniffer (Hostapd + DHCP + DoS)
- Simple integrated sniffing (Hostapd + DHCP + DoS + Ettercap)
- Integrated sniffing, sslstrip (Hostapd + DHCP + DoS + Ettercap + Sslstrip)
- Integrated sniffing, sslstrip2 and BeEF browser exploitation framework (Hostapd + DHCP + DoS + Bettercap + BeEF)
- Captive portal with «DNS blackhole» to capture wifi passwords (Hostapd + DHCP + DoS + Dnsspoff + Lighttpd)
- Optional MAC spoofing for all Evil Twin attacks
- WPS features
- WPS scanning (wash). Self parameterization to avoid «bad fcs» problem
- Custom PIN association (bully and reaver)
- Pixie Dust attacks (bully and reaver)
- Bruteforce PIN attacks (bully and reaver)
- Parameterizable timeouts
- Known WPS PINs attack (bully and reaver), based on online PIN database with auto-update
- Integration of the most common PIN generation algorithms
- WEP All-in-One attack (combining different techniques: Chop-Chop, Caffe Latte, ARP Replay, Hirte, Fragmentation, Fake association, etc.)
- Compatibility with many Linux distributions (see Requirements section)
- Easy targeting and selection in every section
- Drag and drop files on console window for entering file paths
- Dynamic screen resolution detection and windows auto-sizing for optimal viewing
- Controlled Exit. Cleaning tasks and temp files. Option to keep monitor mode if desired
- Multilanguage support and autodetect OS language feature (see Supported Languagessection)
- Help hints in every zone/menu for easy use
- Auto-update. Script checks for newer version if possible
- Docker container for easy and quick deployment
- Http proxy auto detection for updates
Tested on these compatible Linux distributions
- Arch 4.6.2-1 to 4.12.3.1
- Backbox 4.5.1 to 5
- BlackArch 2016.01.10 to 2017.06.14
- CentOS 6 and 7
- Cyborg Hawk 1.1
- Debian 7 (Wheezy) to 9 (Stretch)
- Fedora 24
- Gentoo 20160514 and 20160704
- Kali 2.0, 2016.1 to 2017.1 and arm versions (Raspberry Pi)
- OpenMandriva LX3
- OpenSUSE Leap 42.1 and 42.2
- Parrot 2.2.1 to 3.7 and arm versions (Raspberry Pi)
- Raspbian 7 (Wheezy) to 9 (Stretch) (Raspberry Pi)
- Red Hat 7 (Maipo)
- Ubuntu/Xubuntu 15.10 to 17.04
- Wifislax 4.11.1, 4.12 and 64-1.0
airgeddon Help
It is absent, the tool is operated by text (dialog) menu.
airgeddon Usage Example
Start it as root
and follow the instructions in the program.
How to install airgeddon
Installation on Kali Linux
Installation on BlackArch
Installation on other Linux
airgeddon is already included in some Linux distributions and repositories:
- Wifislax 4.12, 64-1.0 or higher
- BlackArch 2017.01.28 or later
- ArchStrike repository
Repositories versions will have auto-update feature disabled in order to avoid breaking dependencies. There is a var at the beginning of the file, «auto_update» can be set to 0 to turn off the auto-update feature.
Anyway, can be used with any Linux distro if you have installed the tools what script needs. The script checks for them at the beginning.
We will enumerate the categories and tools. The format will be: «command -> possible package name». The command can be included in different packages depending of the distro.
Bash version 4.2 or later needed.
Optional tools: aircrack-ng
Update tools: curl
Internal tools: x11-utils / xdpyinfo / xorg-xdpyinfo
Is highly recommended to have the internal tools installed. They improve functionality and performance. For example, xdpyinfo allow the script to detect the desktop resolution in order to print windows in a better way.
Источник
Ethical hacking and penetration testing
InfoSec, IT, Kali Linux, BlackArch
The easiest and fastest ways to hack Wi-Fi (using airgeddon)
Airgeddon is very powerful tool, designed to perform a wide range of effective attacks against wireless Access Points, i.e. Wi-Fi networks.
Airgeddon automates using different tools, so it is not necessary for you type commands. Airgeddon usage does not require deep understanding Wi-Fi protocols or performed attacks. Therefore, absolute beginners are able to hack (audit) wireless networks.
There are some different protocols and cyphers using by Wi-Fi networks. So some different attack vectors exist. Some of the Wi-Fi protocols and cyphers are really weak. Airgeddon helps us to use different techniques. And strategy to reveal the weakest link in the chain let us to increase chances of success and do decrease the time of hacking.
This is the first part of manual, explaining how to use airgeddon to hack Wi-Fi.
Software requirements
In this guide, I will use only free and open source programs. They run in Linux operating system. Actually, you can use any Linux distribution, but you will save a lot of time if you select some special penetration testing distribution.
I operate in Kali Linux. It contains all necessary tools for airgeddon.
You may install Kali Linux as the second operating system on your physical computer or you may set it as virtual machine (for example, using VirtualBox). Both ways are acceptable.
Hardware requirements
There are no special requirements to your computer. If it is able to run Linux, it suits.
But there are requirements to your wireless adapter.
I will not be stuck on ‘monitor mode’, ‘wireless injection’, and ‘drivers for Linux’. In sum, any Kali Linux Compatible USB Wi-Fi adapter from the list will suit the needs. But there is an issue with attacks against WPS. So indeed I recommend you to have two adapters from the above list.
The first one is Alfa AWUS052NH or Panda Wireless PAU09 N600 . Both of them are Dual Band, operate on 2.4GHz and 5GHz Frequencies, have two large 5dBi antennas to improve the signal. Any of them are great choice for almost all wireless attacks. However, they will fail attacking WPS.
For a brute force attack against Wi-Fi Protected Setup (WPS) registrar PINs in order to recover WPA/WPA2 passphrases, Alfa AWUS036NHA is highly recommended.
I also recommend you to combine all these adapters with Wi-Fi antenna to gain signal:
- Alfa ARS-N19 (9dbi Wireless Wi-Fi RP-SMA Dipole Omni Antenna)
- Alfa APA-M04 (2,4Ghz 7dBi Wireless Wi-Fi RP-SMA Directonal Panel Antenna)
- Alfa APA-M25 (Dual Band 10dBi Wireless Wi-Fi RP-SMA Directonal Indoor Antenna)
How to install airgeddon in Kali Linux
While attacking Wi-Fi networks we will need a dictionary. Let’s prepare one for future usage:
Ok, now we have a dictionary to hack Wi-Fi password, it is the /root/newrockyou.txt file.
Almost all airgeddon requirements (dependencies) are already present in Kali Linux. Therefore we have to install only airgeddon itself. To clone it from GitHub execute the command:
Change the shell working directory:
Some packets are needed only for Phishing, Sniffing attacks. We can also install them (currently you can skip the step):
How to run airgeddon in Kali Linux
Plug your wireless USB adapter (if it is unplugged).
Indeed, it is not necessary, but I prefer to unload Network Manager and stop all other processes which would interfere in my activity:
Launch the script:

Select the correct (wireless) interface, named wlan0:

Now select the second option from menu — Put interface in monitor mode:

Now we are armed completely. We are able to hack our first Wi-Fi network.

Automated WEP attack
As I mentioned above, there are some different protocols and cyphers using by Wi-Fi networks. The weakest one is WEP. The WEP protocol had a bad design and can be cracked in a few minutes if we have enough generated traffic. So we should start from checking whether any WEP enabled networks is available around us.
Select ‘9. WEP attacks menu’:

Select the ‘4. Explore for targets (monitor mode needed)’ menu item to find any WEP enabled Wi-Fi networks:

When started, press [Ctrl+C] to stop…

As you can noticed, I can reach the only one WEP enabled network:
Therefore, I enter ‘4’:

Currently I am completely ready to start the attack, I should select the ‘5. WEP «All-in-One» attack’ menu item:

The WEP «All-in-One» attack combines different techniques to generate enough traffic to decrypt the key (Caffe Latte, Hirte, Replay, Chop-Chop, Fragmentation, Fake association, etc.
The program reports:
And asks the path for the file to save the cracked password, I press [Enter] to accept the default proposal:


WEP attack in progress:

The WEP password as ASCII string and in Hexadecimal will be shown in the new window:

In my test they are:
Also you can get them from the /root/wep_captured_key-dlink.txt file:
But in my test the ASCII string does not equal Hexadecimal. To prove that I type the command:
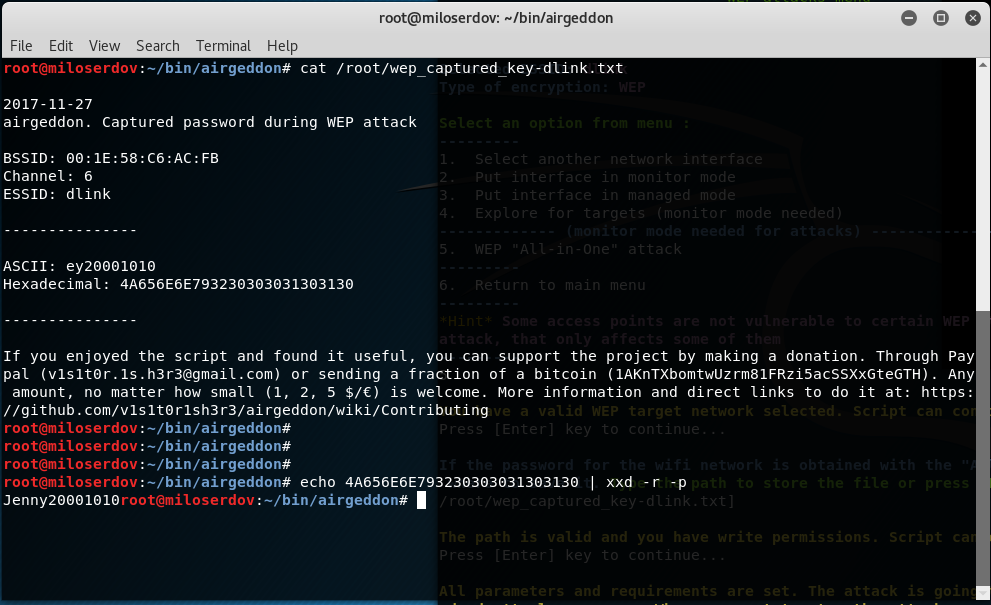
You can convert Hexadecimal value to ASCII string by the following command, where replace Hex_Value with actual Hexadecimal:
Automated WPS attack
Many WPS enabled Wi-Fi Access Points is vulnerable to WPS attacks.
Currently there are known issues with the devices that uses rt2800usb drivers (chips RT3070, RT3272, RT3570, RT3572 etc). There is unfortunately right now no solution. Therefore, the great Alfa AWUS052NH and Panda Wireless PAU09 N600 do not suit for these attacks.
For all WPS attacks, I highly recommend to use Alfa AWUS036NHA . Because it is based on another chipset and uses another driver.
In the main menu select the ‘8. WPS attacks menu’ item:
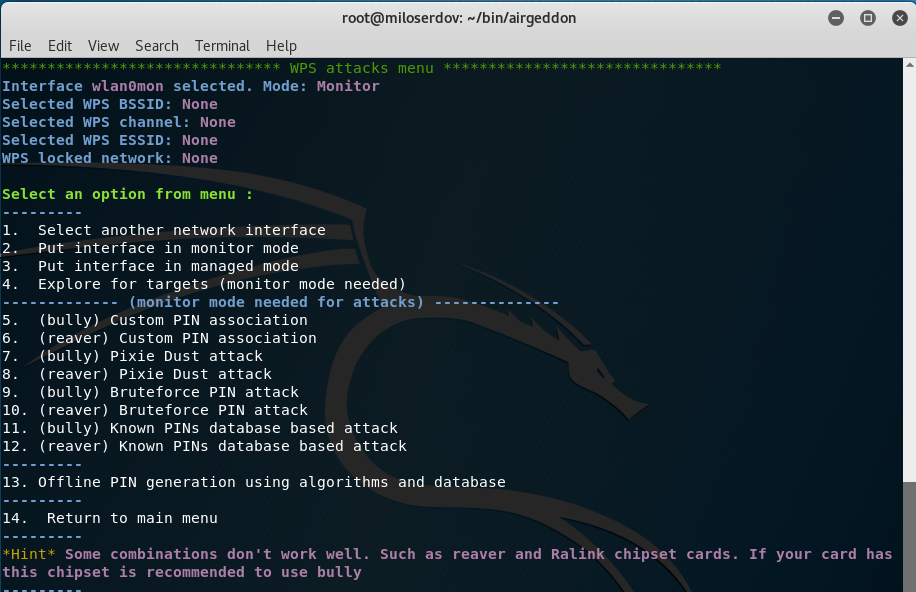
There are 4 WPS attacks in airgeddon:
- Custom PIN association
- Pixie Dust attack
- Bruteforce PIN attack
- Known PINs database based attack
Pixie Dust attack
WPS PIN exploiting the low or non-existing entropy of some Access Points, the so-called «pixie-dust attack» discovered by Dominique Bongard in summer 2014.
As opposed to the traditional online brute-force attack, implemented in tools like Reaver or Bully which aim to recover the pin in a few hours, this method can get the PIN in only a matter of milliseconds to minutes, depending on the target, if vulnerable.
As any other attacks, start from ‘4. Explore for targets (monitor mode needed)’:
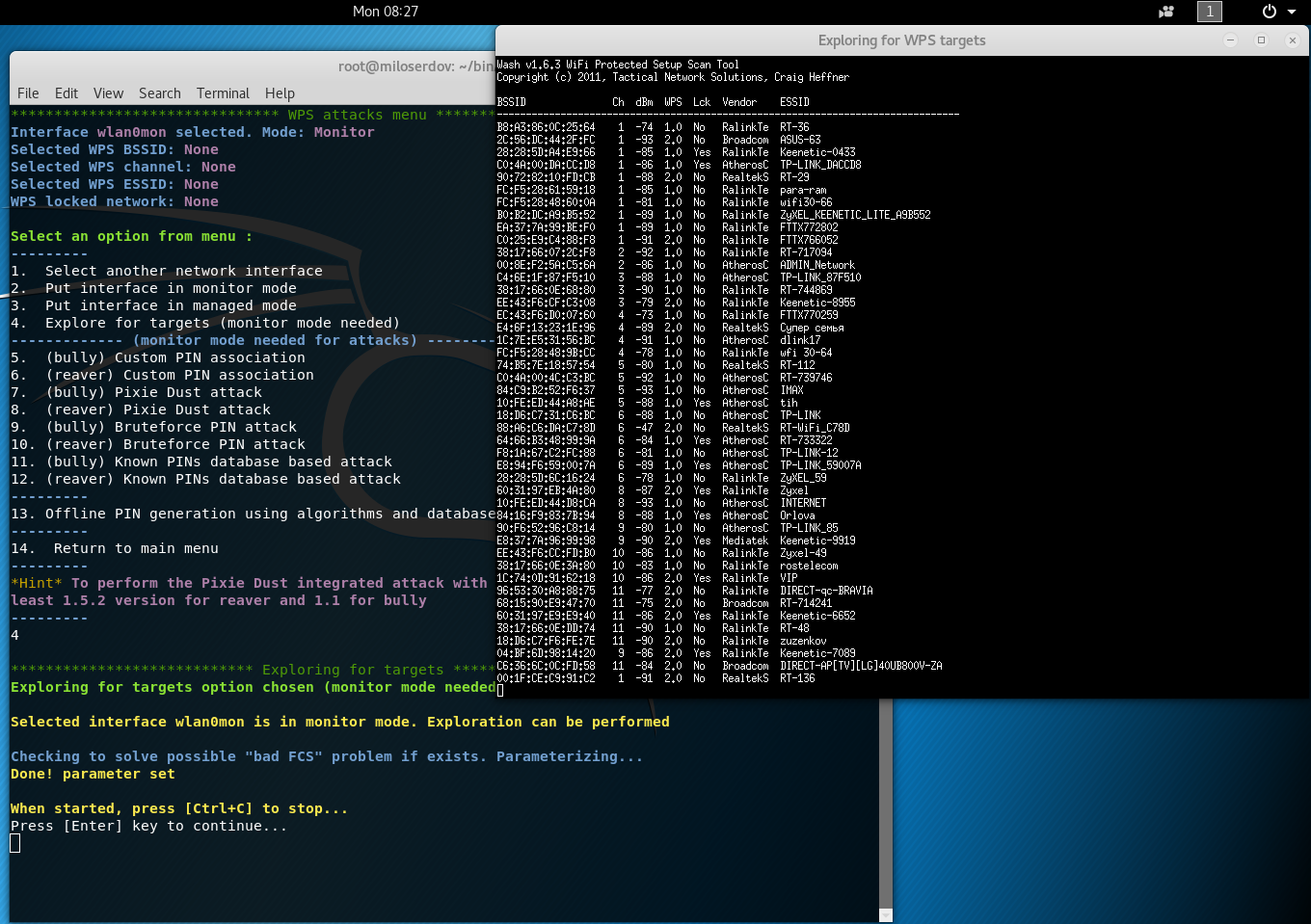
Select not Locked (marked red) AP:

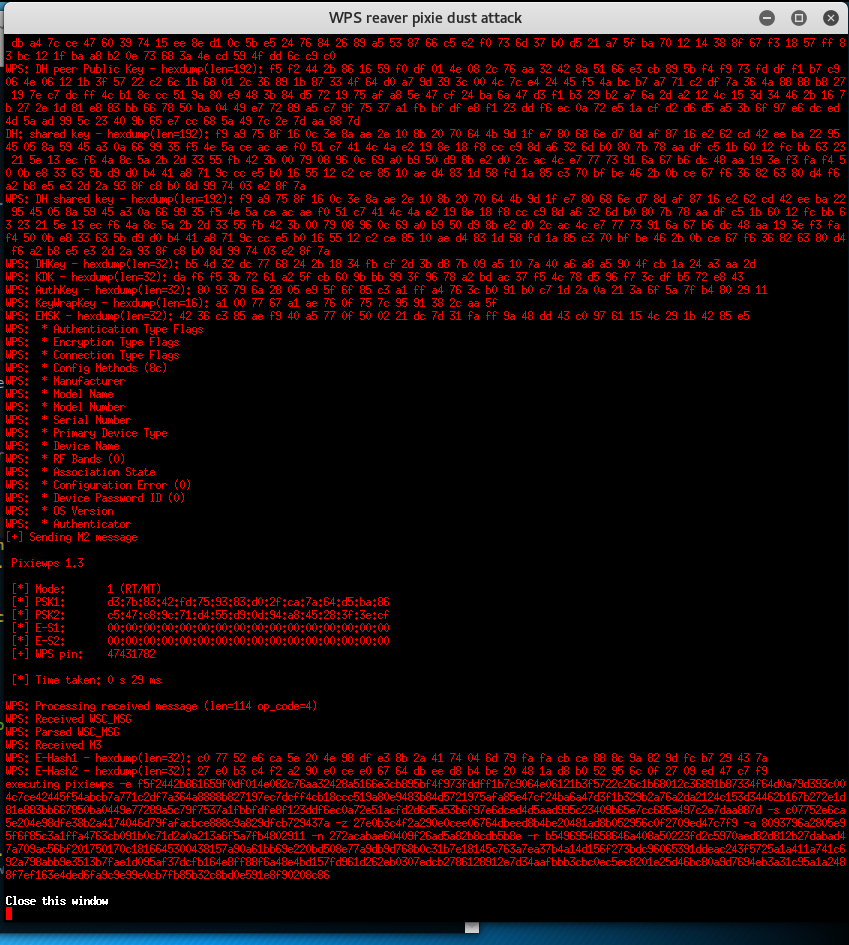
Next select ‘8. (reaver) Pixie Dust attack’. Select Pixie Dust timeout 100 or more seconds.
Starting attack. When started, press [Ctrl+C] to stop…
After stopping the attack (using [Ctrl+C]), the window will not be closed automatically. So you’ll have time to write down the password if successful. You’ll have to close it manually
Known PINs database based attack
Bruteforce PIN attack
This attack requires hours or days to get WPS PIN. Use the attack if previous ones failed.
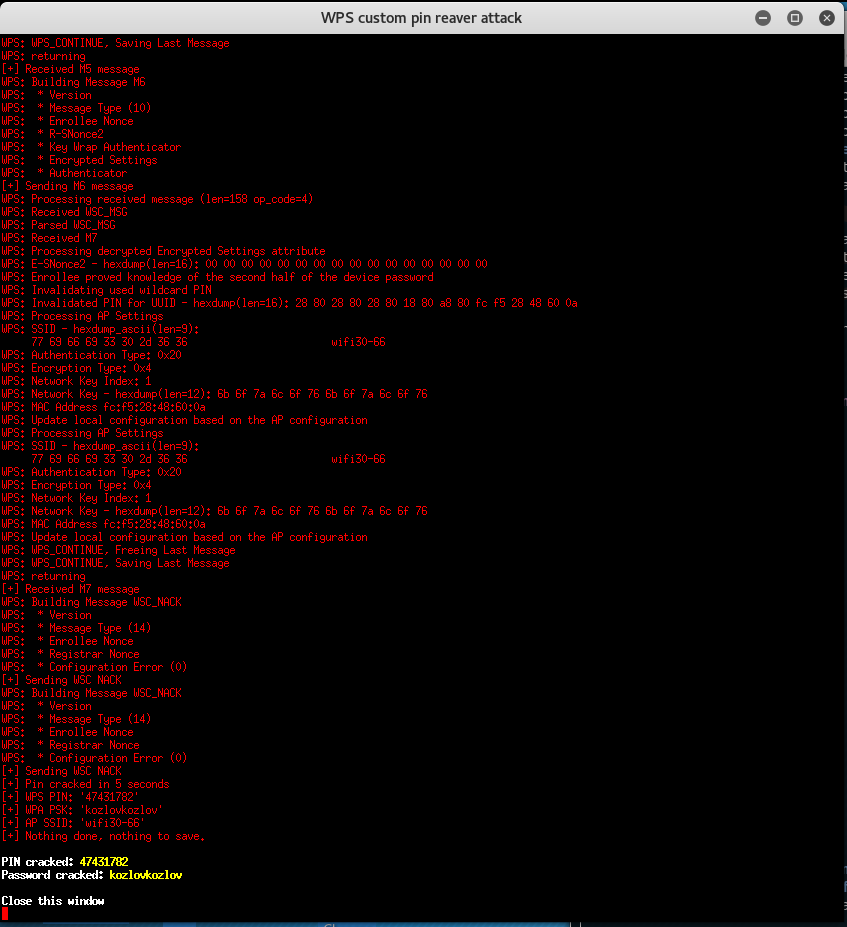
Custom PIN association
This attack lets you reveal WPA-PSK password of Wi-Fi network if you know WPS PIN.
WPA/WPA2 attack
If target Access Point is not WPS enabled or if all WPS attacked failed, we can try to capture Handshake (frames by which the Access Point and Station are exchanged during connection) and decrypt it.
For all the following attacks I will use Alfa AWUS052NH .
First, we have to capture Handshake, therefore select ‘5. Handshake tools menu’ item in the main menu:
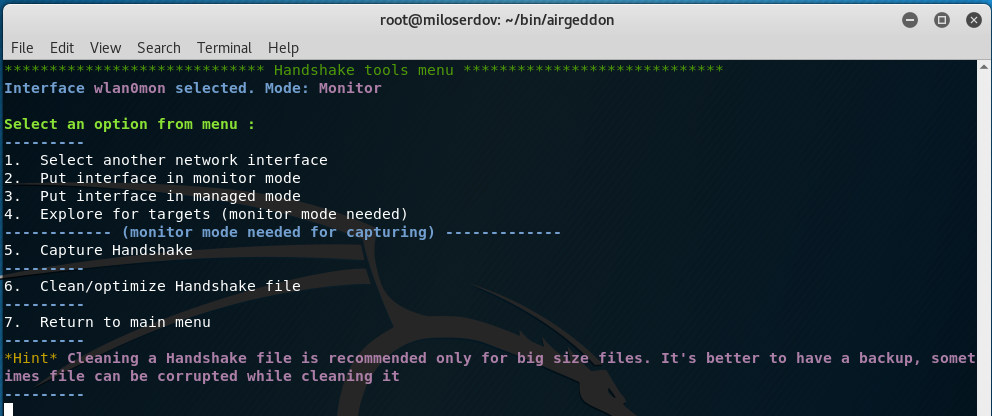
Start from ‘4. Explore for targets (monitor mode needed)’:
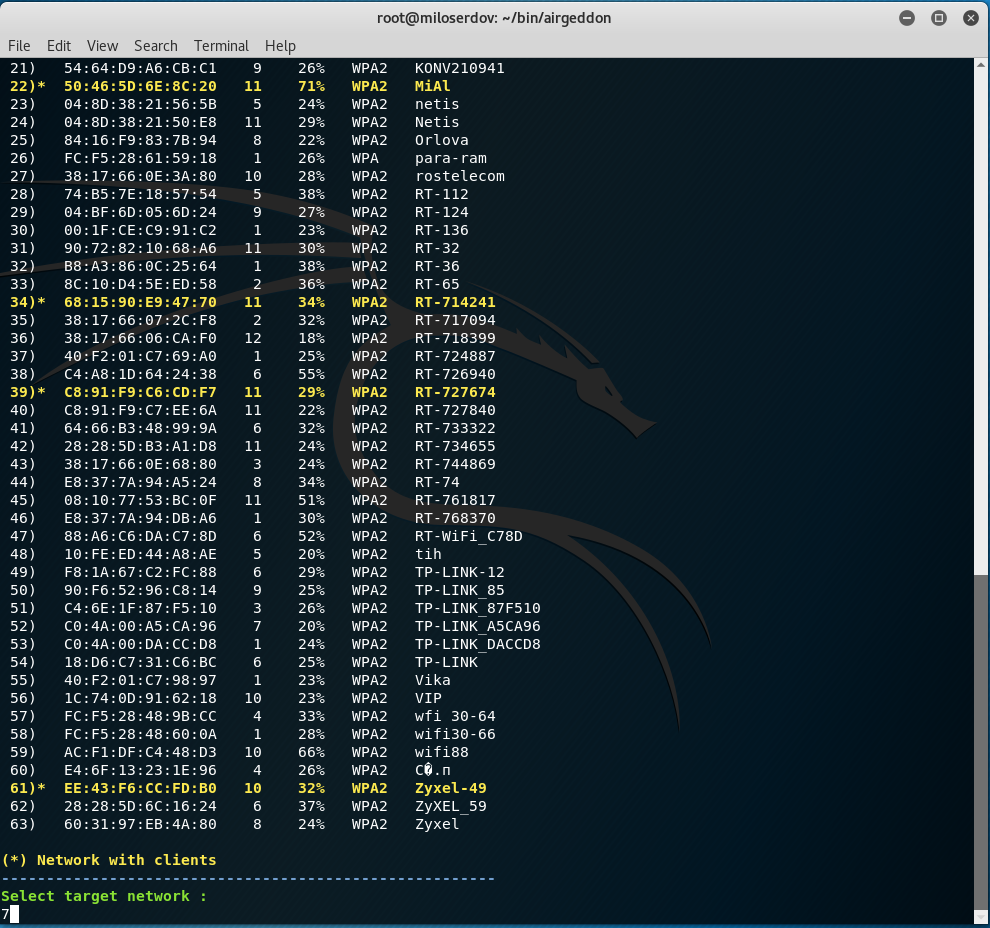
The best targets have:
After I selected the target AP, I enter ‘5. Capture Handshake’:
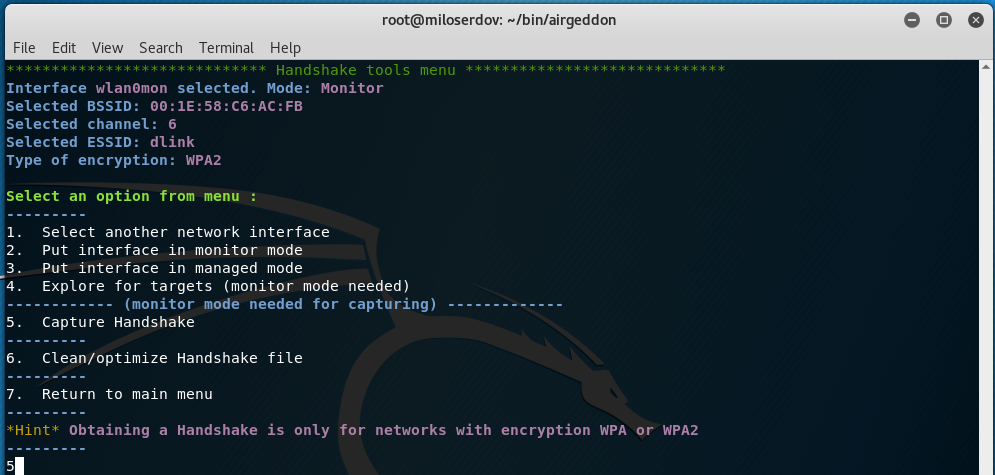
We have 3 options:
- Deauth / disassoc amok mdk3 attack
- Deauth aireplay attack
- WIDS / WIPS / WDS Confusion attack
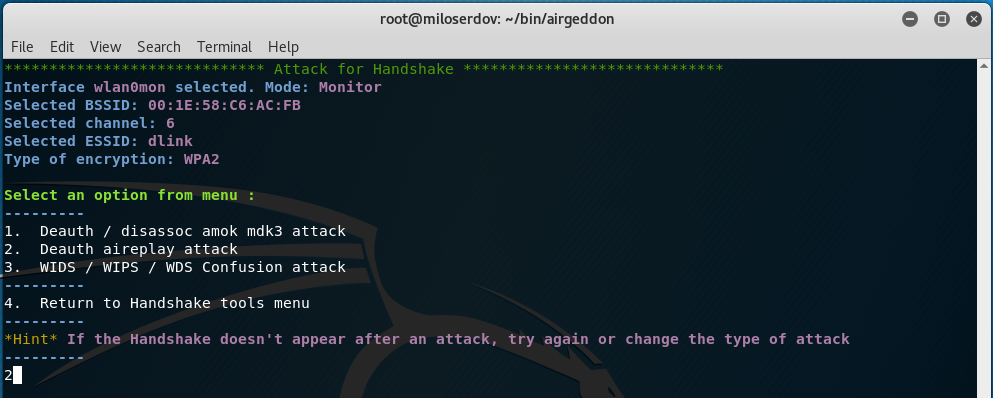
Usually I prefer the second option (Deauth aireplay attack), if it failed I try with ‘1. Deauth / disassoc amok mdk3 attack’.
Two windows will be opened. One with the Handshake capturer and other with the attack to force clients to reconnect.
Don’t close any window manually, script will do when needed. In about 20 seconds maximum you’ll know if you’ve got the Handshake.
I got the Handshake.

Now I ‘7. Return to main menu’ and select ‘6. Offline WPA/WPA2 decrypt menu’:

To launch Dictionary attack against capture file I select the first menu item (‘1. (aircrack) Dictionary attack against capture file’).
The script reports:
As the path of a dictionary file I enter /root/newrockyou.txt.
The Dictionary attack in progress:
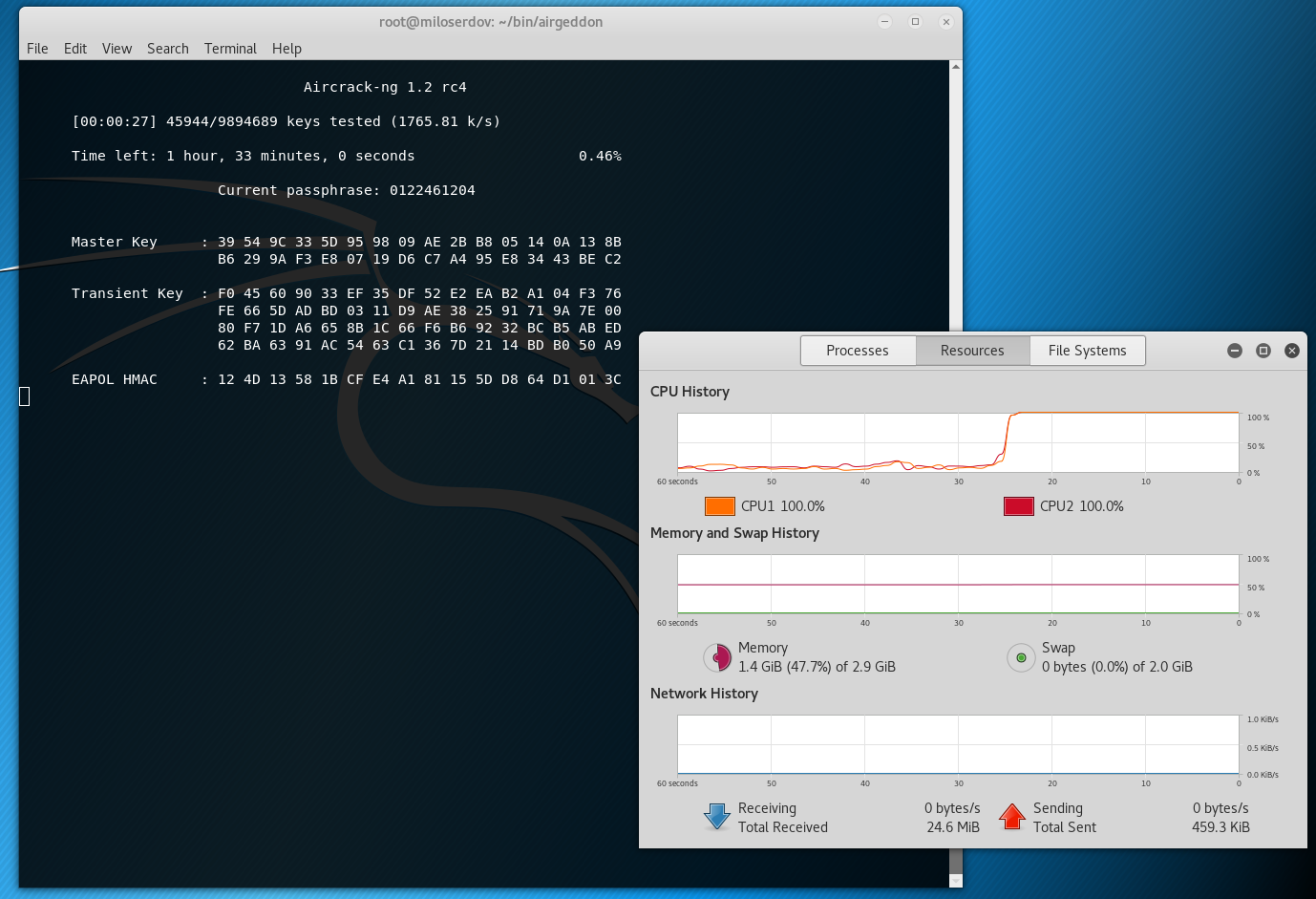
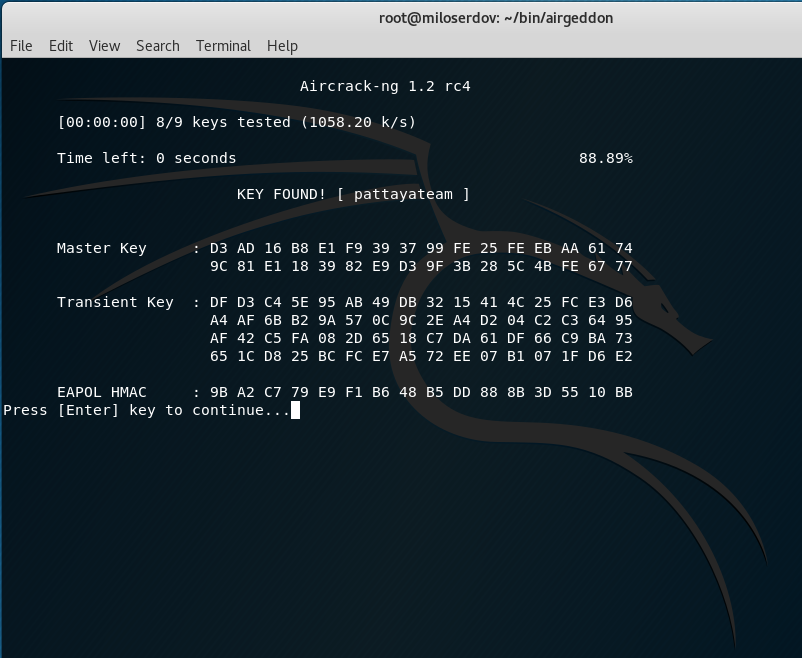
If the attack succeeded the string, containing ‘KEY FOUND!’, will be displayed.
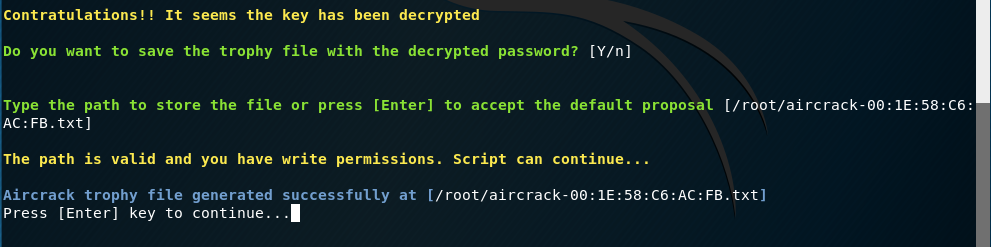
In addition, the script will ask about storing the trophy file:
If the dictionary attack failed, you can try again with another dictionary of use the ‘2. (aircrack + crunch) Bruteforce attack against capture file’.
I recommend you to try eight digits and ten digits passwords (Numeric chars). The first ones are Birthday dates (19990210); the second ones are phone numbers (09341112233).
Conclusion
In this part, we discussed the essential Wi-Fi attacks, which, nevertheless, are commonly used for wireless network audits, for hacking Wi-Fi.
In the next part we will continue to learn airgeddon usage and we will review Evil Twin attack (Captive portal with «DNS blackhole» to capture wifi passwords), Rogue AP (aimed to sniffing) and DoS over wireless networks using different methods.
Also, pay attention to ‘All Airgeddon Hints’, which will help you to understand the wireless attacks better.
Источник



