- How do I configure an EC2 Windows instance to allow file downloads using Internet Explorer?
- Short description
- Resolution
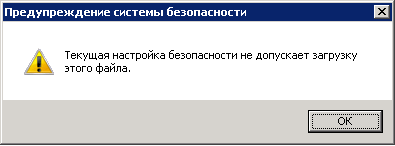
- Internet Explorer: Текущая настройка безопасности не допускает загрузку этого файла
- Oxford SBS Guy
- Office 365, Windows Server, Exchange, PowerShell, Hyper-V and VMware tips and tricks (but no more SBS!)
- Server 2012: Your current security settings do not allow this file to be downloaded
- 11 thoughts on “ Server 2012: Your current security settings do not allow this file to be downloaded ”
- Leave a Reply Cancel reply
- About Me
- @GilesDMiddleton
- Making sense of the technobabble
- Windows Server 2008 “Your current security settings do not allow this file to be downloaded”
- Active Directory Security Groups
- About Active Directory groups
- Distribution groups
- Security groups
- Group scope
- Special identity groups
- Default security groups
- Active Directory default security groups by operating system version
How do I configure an EC2 Windows instance to allow file downloads using Internet Explorer?
Last updated: 2020-09-18
I need to download third-party software from the internet to my Amazon Elastic Compute Cloud (Amazon EC2) Windows instance. The Internet Explorer security configuration is blocking my attempts. How can I enable downloads?
Short description
Amazon Machine Images (AMIs) for Windows Server enable Internet Explorer Enhanced Security Configuration by default, because web browsing isn’t a best practice on a server. Internet Explorer Enhanced Security Configuration disables file downloads using Internet Explorer.
If you want to download and install tools from the internet, you can change the security configuration to enable downloads.
Note: If you enable downloads on your EC2 Windows instance, be sure to download files only from trusted sources. After you download and install the software, it’s a best practice to re-enable Internet Explorer Enhanced Security Configuration.
Resolution
- Connect to your EC2 Windows instance.
- Open the Windows Start menu, and then open Server Manager.
- Follow the instructions for the Windows Server version that your EC2 Windows instance is running:
Windows Server 2012 R2, Windows Server 2016, or Windows Server 2019: Choose Local Server from the left navigation pane. For IE Enhanced Security Configuration, choose On.
Windows Server 2008 R2: Choose Server Manager from the navigation pane. In the Server Summary — Security Information section, choose Configure IE ESC. - For Administrators, select Off.
For Users, select Off.
Choose OK. - Close Server Manager.
Note: The security configuration change takes effect when you open a new Internet Explorer session. If Internet Explorer is already open, open a new tab. Or, close the browser, and then re-open it.
Internet Explorer: Текущая настройка безопасности не допускает загрузку этого файла
Пользователь работает на компьютере с установленной ОС Windows Server 2008 с браузером Internet Explorer 8.0. При попытке скачать любой файл из интернет он получает ошибку: «Текущая настройка безопасности не допускает загрузку этого файла» («Your current security settings do not allow this file to be downloaded»)
Так как человек работает с ограниченными правами (пользователь), в настройках обозревателя на закладке «Безопасность» невозможно изменить/настроить уровень безопасности для зоны «Интернет».
Причина
По умолчанию для снижения риска заражения компьютера вредоносным кодом через интернет на Windows Server 2008 в Internet Explorer заблокирована возможность загрузки файлов.
Решение
Чтобы разрешить скачивание файлов средствами Internet Explorer, необходимо внести изменения в реестр Windows:
1. Нажмите кнопку Пуск, выберите пункт Выполнить и введите в поле Открыть команду regedit.
2. Найдите и выделите следующий раздел реестра: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\3
Изменяем параметр: 1803
Тип: REG_DWORD
Значение: 0 или 3
3: загрузка файлов запрещена (по умолчанию)
0: загрузка файлов разрешена
Oxford SBS Guy
Office 365, Windows Server, Exchange, PowerShell, Hyper-V and VMware tips and tricks (but no more SBS!)
Server 2012: Your current security settings do not allow this file to be downloaded
Ok, you’ve just installed Windows Server 2012, and now want to add a few non MS programs to it to make like a little easier so you open IE and browse to a website, click download and you get the error message “Your current security settings do not allow this file to be downloaded“.

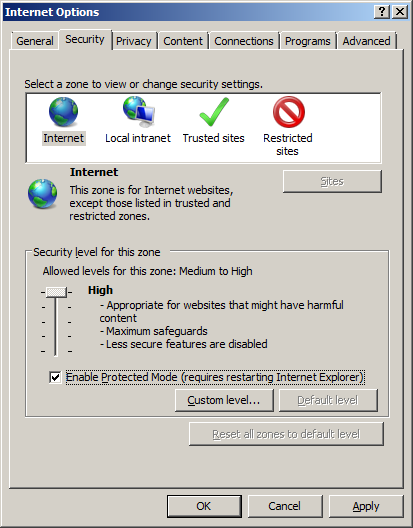
Click the cog in the top right corner of the browser and select Internet Options.
Select the Security tab, and click the Internet zone.
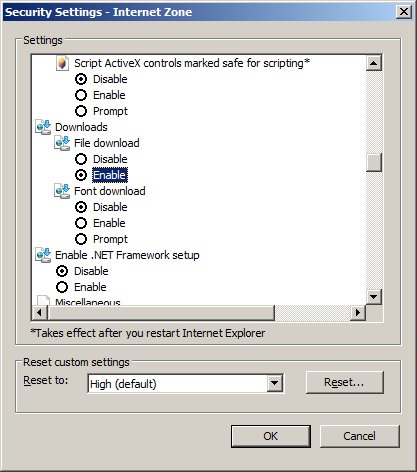
Click Custom level, and then scroll down to Downloads and select Enable.
Click OK and Yes to confirm you want to make the change for the Internet Zone.
Click OK to close the Internet Options.
Downloads are now enabled.
Related Posts:
11 thoughts on “ Server 2012: Your current security settings do not allow this file to be downloaded ”
This also works for fresh Windows Server 2008 installation with IE9
Thank you veryyyyy much man 🙂
thanks .post is exactly wat i was looking for 🙂
downloads are enabled. what now?
Are you still getting an error message?
Had issue on Server2012. Issue was that Microsoft is now using “download.microsoft.com” inside it’s applet. Short answer: Go to trusted sites, click add, add “*.Microsoft.com” (wildcard works). NOW it will work if the other changes were made
city force,, only your solution work with me
thnx
saved me as well!
I’ve tried pretty much everything I know to do in MS Explorer and still I’m not able to download a program to MS Server 2012. I even tried downloading Google Chrome but couldn’t even download it. HELP!
My server 2012 do not install java
keep telling me to add the file to the trust zone
thats sucks!
thanks resolved my issue
Leave a Reply Cancel reply
This site uses Akismet to reduce spam. Learn how your comment data is processed.
About Me
Carl Gray is an IT professional and technology blogger based in the UK.
With 23 years of industry experience, he is currently a Technical Director specialising in PowerShell, Office 365, Windows Server, Exchange Server, SharePoint, Hyper-V, VMware, Veeam and Dell hardware.
@GilesDMiddleton
Making sense of the technobabble
Windows Server 2008 “Your current security settings do not allow this file to be downloaded”
This is, by far, my most popular blog topic. Please leave some feedback if it helped you, or if I can improve it.
Occasionally I have to install a Web server or SQL Server on a fresh Windows Server 2008 R2 operating system, and by far the most annoying bit about it is just getting windows updates and the downloads you need onto the machine. Here’s a reminder (more for myself) how to quickly enable Internet Explorer 9 to act normally, even if it’s just temporarily.
There are a few options to get the job done. – The quickest and least secure method is at the end – via Server Manager.
Option 1 Add the site to your trusted sites
When you try and click a link, you’ll probably see this dialog.
You can simply add the current site to the trusted sites list by the Add… button.
This has the same effect as enabling file downloads manually (Option 2) but will also allow much more than just file downloads to take place, so only use this if you really do trust the site.
Option 2 Enable file downloads for the internet zone
- Open Internet Explorer.
- Click the Cog icon and then click on Internet Options
- Click on the Security tab
- Select the Internet Zone.
- Click on the Custom Level… button
- Scroll to the Download section.
- Enable File download.
- Click OK and .
- Restart Internet Explorer.
Option 3 Use another computer to get the downloads (recommended for maximum security)
- Use whatever mechanism you can to transfer the files (USB, File share, FTP, DVD, ISO mount, the list goes on….)
Option 4 Install Google Chrome
- Yep, them pesky settings only apply to IE!
Option 5 Disable Protection (probably the worst idea and might not help at all)
Because there are many ways in which you can have a file sent to you (not just by clicking a direct link) you may find that the only way to get the download started (other than trusting the site), is to disable protection. I’ve not encountered a situation yet where this has helped, but I’ve not tried hard enough. I’ve seen this suggested on other forums so thought I’d better include it. But see the link at point 3, this option opens up a whole can of worms. If in doubt, choose option 3!
- Click the Cog icon, and select Internet Options
- Go to the Security tab
- Uncheck the Enable protected mode tick box. Want to know what it really does? See here.
- OK the Internet Options page and Restart IE
You will now be nagged about not being protected any more. Try not to catch a cold. If you love screen shots, see this guide.
Option 6 Disable IE Enhanced Security via Server Manager
You can do this quickly through the Server Manager (from the Start Menu). The same implications apply as Option 5 above (no doubt).
Active Directory Security Groups
Applies To: Windows Server 2008, Windows Server 2008 R2, Windows Server 2012 R2, Windows Server 2012
This reference topic for the IT professional describes the default Active Directory security groups.
There are two forms of common security principals in ActiveВ Directory: user accounts and computer accounts. These accounts represent a physical entity (a person or a computer). User accounts can also be used as dedicated service accounts for some applications. Security groups are used to collect user accounts, computer accounts, and other groups into manageable units.
In the WindowsВ Server operating system, there are several built-in accounts and security groups that are preconfigured with the appropriate rights and permissions to perform specific tasks. For ActiveВ Directory, there are two types of administrative responsibilities:
Service administratorsВ В В Responsible for maintaining and delivering Active Directory Domain Services (ADВ DS), including managing domain controllers and configuring the ADВ DS.
Data administratorsВ В В Responsible for maintaining the data that is stored in ADВ DS and on domain member servers and workstations.
About Active Directory groups
Groups are used to collect user accounts, computer accounts, and other groups into manageable units. Working with groups instead of with individual users helps simplify network maintenance and administration.
There are two types of groups in ActiveВ Directory:
Distribution groups Used to create email distribution lists.
Security groups Used to assign permissions to shared resources.
Distribution groups
Distribution groups can be used only with email applications (such as Exchange Server) to send email to collections of users. Distribution groups are not security enabled, which means that they cannot be listed in discretionary access control lists (DACLs).
Security groups
Security groups can provide an efficient way to assign access to resources on your network. By using security groups, you can:
Assign user rights to security groups in ActiveВ Directory.
User rights are assigned to a security group to determine what members of that group can do within the scope of a domain or forest. User rights are automatically assigned to some security groups when Active Directory is installed to help administrators define a person’s administrative role in the domain.
For example, a user who is added to the Backup Operators group in ActiveВ Directory has the ability to back up and restore files and directories that are located on each domain controller in the domain. This is possible because, by default, the user rights Backup files and directories and Restore files and directories are automatically assigned to the Backup Operators group. Therefore, members of this group inherit the user rights that are assigned to that group.
You can use GroupВ Policy to assign user rights to security groups to delegate specific tasks. For more information about using Group Policy, see User Rights Assignment.
Assign permissions to security groups for resources.
Permissions are different than user rights. Permissions are assigned to the security group for the shared resource. Permissions determine who can access the resource and the level of access, such as Full Control. Some permissions that are set on domain objects are automatically assigned to allow various levels of access to default security groups, such as the Account Operators group or the Domain Admins group.
Security groups are listed in DACLs that define permissions on resources and objects. When assigning permissions for resources (file shares, printers, and so on), administrators should assign those permissions to a security group rather than to individual users. The permissions are assigned once to the group, instead of several times to each individual user. Each account that is added to a group receives the rights that are assigned to that group in ActiveВ Directory, and the user receives the permissions that are defined for that group.
Like distribution groups, security groups can be used as an email entity. Sending an email message to the group sends the message to all the members of the group.
Group scope
Groups are characterized by a scope that identifies the extent to which the group is applied in the domain tree or forest. The scope of the group defines where the group can be granted permissions. The following three group scopes are defined by ActiveВ Directory:
In addition to these three scopes, the default groups in the Builtin container have a group scope of Builtin Local. This group scope and group type cannot be changed.
The following table lists the three group scopes and more information about each scope for a security group.
Group scopes
Can Grant Permissions
Possible Member of
Accounts from any domain in the same forest
Global groups from any domain in the same forest
Other Universal groups from any domain in the same forest
Can be converted to Domain Local scope
Can be converted to Global scope if the group does not contain any other Universal groups
On any domain in the same forest or trusting forests
Other Universal groups in the same forest
Domain Local groups in the same forest or trusting forests
Local groups on computers in the same forest or trusting forests
Accounts from the same domain
Other Global groups from the same domain
Can be converted to Universal scope if the group is not a member of any other global group
On any domain in the same forest, or trusting domains or forests
Universal groups from any domain in the same forest
Other Global groups from the same domain
Domain Local groups from any domain in the same forest, or from any trusting domain
Accounts from any domain or any trusted domain
Global groups from any domain or any trusted domain
Universal groups from any domain in the same forest
Other Domain Local groups from the same domain
Accounts, Global groups, and Universal groups from other forests and from external domains
Can be converted to Universal scope if the group does not contain any other Domain Local groups
Within the same domain
Other Domain Local groups from the same domain
Local groups on computers in the same domain, excluding built-in groups that have well-known SIDs
Special identity groups
Special identities are generally referred to as groups. Special identity groups do not have specific memberships that can be modified, but they can represent different users at different times, depending on the circumstances. Some of these groups include Creator Owner, Batch, and Authenticated User.
For information about all the special identity groups, see Special Identities.
Default security groups
Default groups, such as the Domain Admins group, are security groups that are created automatically when you create an ActiveВ Directory domain. You can use these predefined groups to help control access to shared resources and to delegate specific domain-wide administrative roles.
Many default groups are automatically assigned a set of user rights that authorize members of the group to perform specific actions in a domain, such as logging on to a local system or backing up files and folders. For example, a member of the Backup Operators group has the right to perform backup operations for all domain controllers in the domain.
When you add a user to a group, the user receives all the user rights that are assigned to the group and all the permissions that are assigned to the group for any shared resources.
Default groups are located in the Builtin container and in the Users container in ActiveВ Directory Users and Computers. The Builtin container includes groups that are defined with the Domain Local scope. The Users includes contains groups that are defined with Global scope and groups that are defined with Domain Local scope. You can move groups that are located in these containers to other groups or organizational units (OU) within the domain, but you cannot move them to other domains.
Some of the administrative groups that are listed in this topic and all members of these groups are protected by a background process that periodically checks for and applies a specific security descriptor. This descriptor is a data structure that contains security information associated with a protected object. This process ensures that any successful unauthorized attempt to modify the security descriptor on one of the administrative accounts or groups will be overwritten with the protected settings.
The security descriptor is present on the AdminSDHolder object. This means that if you want to modify the permissions on one of the service administrator groups or on any of its member accounts, you must modify the security descriptor on the AdminSDHolder object so that it will be applied consistently. Be careful when you make these modifications because you are also changing the default settings that will be applied to all of your protected administrative accounts.
Active Directory default security groups by operating system version
The following tables provide descriptions of the default groups that are located in the Builtin and Users containers in each operating system.