- Install Cisco AnyConnect Secure Mobility Client on a Mac Computer
- Available Languages
- Download Options
- Objective
- Introduction
- AnyConnect Software Version
- Install AnyConnect Secure Mobility Client
- Prerequisites
- Check these other articles out!
- Applicable Devices | Software Version
- Licensing Information
- Step 1
- Step 2
- Step 3
- Step 4
- Step 5
- Step 6
- Step 7
- Step 8
- Step 9
- Step 10
- Step 11
- Step 12
- Step 13
- Additional Resources
- AnyConnect App
- View a video related to this article.
- Bypass Cisco AnyConnect Hostscan
- What is hostscan?
- How does hostscan work?
- Hostscan Bypass
- No access to the target machine
- Cisco AnyConnect Secure Mobility Client Administrator Guide, Release 4.0
- Book Title
- Chapter Title
- Results
- Chapter: Configure Posture
- Configure Posture
- What ISE Posture Module Provides
- Posture Checks
- Any Necessary Remediation
- Patch Management Checks and Remediation
- Reassessment of Endpoint Compliance
- Automatic Compliance
- VLAN Monitoring and Transitioning
- Troubleshooting
- Operations That Interrupt the AnyConnect ISE Flow
- Status of ISE Posture
- Posture and Multi Homing
- Simultaneous Users on an Endpoint
- Logging for Posture Modules
- Posture Modules’ Log Files and Locations
- ISE Posture Profile Editor
- Advanced Panel
- What VPN Posture (HostScan) Module Provides
- HostScan
- Basic Functionality
- Endpoint Assessment
- Advanced Endpoint Assessment:Antivirus, Antispyware, and Firewall Remediation
- Configure Antivirus Applications for HostScan
- Integration with Dynamic Access Policies
- BIOS Serial Number in a DAP
- Specify the BIOS as a DAP Endpoint Attribute
- How to Obtain BIOS Serial Numbers
- Determine the HostScan Image Enabled on the ASA
- Upgrade HostScan
- OPSWAT Support
- VPN Hostscan Posture OPSWAT Support
- ISE Posture OPSWAT Support
Install Cisco AnyConnect Secure Mobility Client on a Mac Computer
Available Languages
Download Options
Objective
This article shows you how to download and install the Cisco AnyConnect Secure Mobility Client version 4.9.x on a Mac Computer.
This article is only applicable to the RV34x series routers, not Enterprise products.
Introduction
AnyConnect Secure Mobility Client is a modular endpoint software product. It not only provides Virtual Private Network (VPN) access through Secure Sockets Layer (SSL) and Internet Protocol Security (IPsec) Internet Key Exchange version2 (IKEv2) but also offers enhanced security through various built-in modules.
AnyConnect Software Version
Install AnyConnect Secure Mobility Client
This toggled section provides details and tips for beginners.
Prerequisites
- You need to purchase client license(s) from a partner like CDW or through your company’s device procurement. There are options for 1 user (L-AC-PLS-3Y-S5) or packets of licenses including one year for 25 users (AC-PLS-P-25-S). Other license options available as well, including perpetual licenses. For more details on licensing, check out the links in the Licensing Information section below.
- Download the latest version of firmware available for your router.
Check these other articles out!
Applicable Devices | Software Version
- RV340 | 1.0.03.21 (Download latest)
- RV340W | 1.0.03.21 (Download latest)
- RV345 | 1.0.03.21 (Download latest)
- RV345P | 1.0.03.21 (Download latest)
Licensing Information
AnyConnect client licenses allow the use of the AnyConnect desktop clients as well as any of the AnyConnect mobile clients that are available. You will need a client license to download and use the Cisco AnyConnect Secure Mobility Client. A client license enables the VPN functionality and are sold in packs of 25 from partners like CDW or through your company’s device procurement.
Want to know more about AnyConnect licensing? Here are some resources:
Step 1
Open a web browser and navigate to the Cisco Software Downloads webpage.
Step 2
In the search bar, start typing ‘Anyconnect’ and the options will appear. Select AnyConnect Secure Mobility Client v4.x.
Step 3
Download the Cisco AnyConnect VPN Client. Most users will select the AnyConnect Pre-Deployment Package (Mac OS) option.
The images in this article are for AnyConnect v4.9.x, which was latest version at the time of writing this document.
Step 4
Double-click the installer.
Step 5
Step 6
Go over the Supplemental End User License Agreement and then click Continue.
Step 7
Step 8
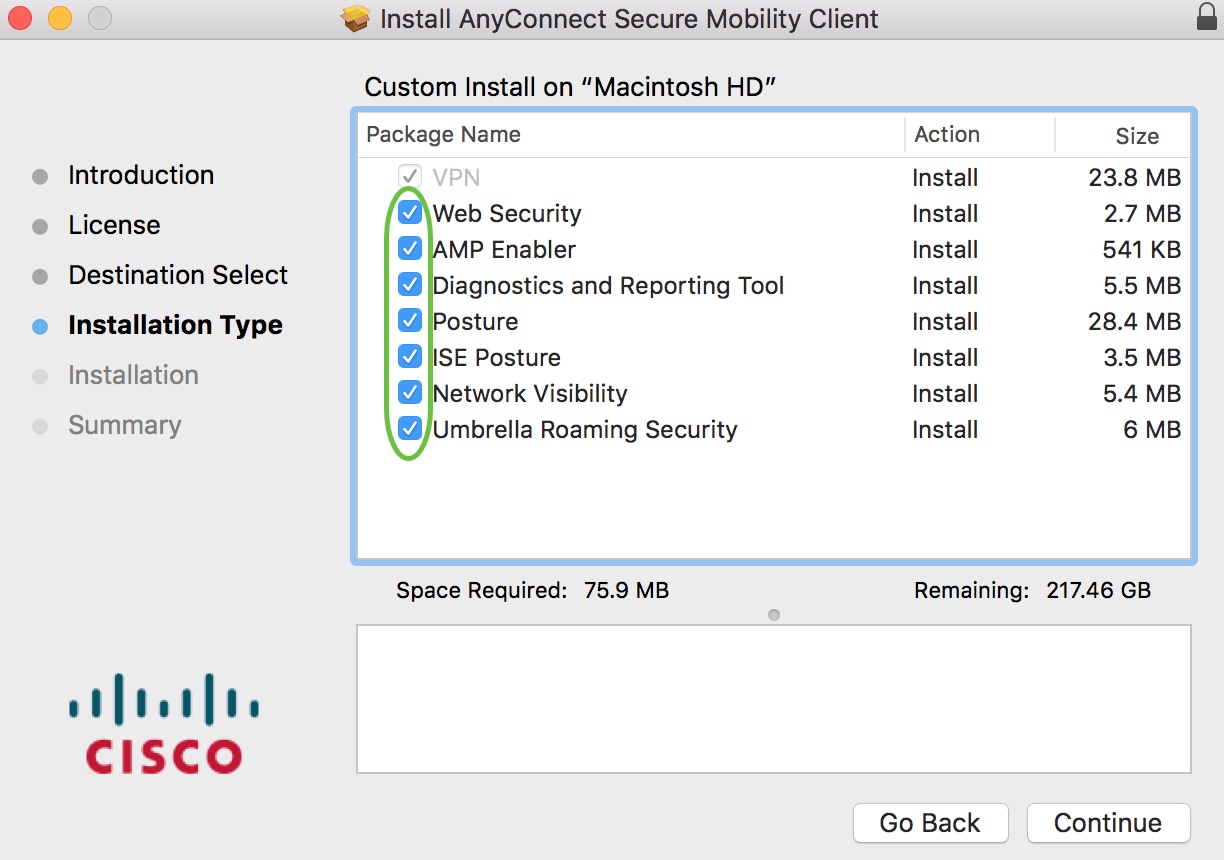
Choose the components to be installed by checking or unchecking the corresponding check boxes. All components are installed by default.
The items you select in this screen will appear as options in AnyConnect. If deploying AnyConnect for end-users, you may want to consider deselecting options.
Step 9
Step 10
Step 11
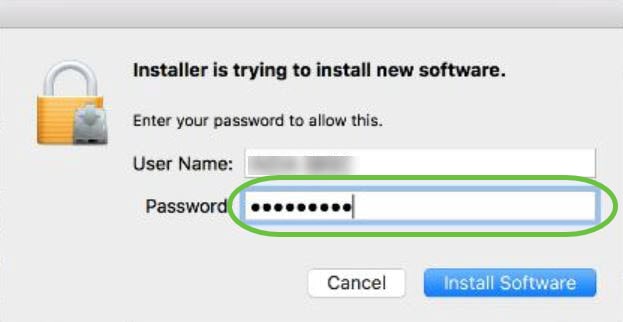
(Optional) Enter your password in the Password field.
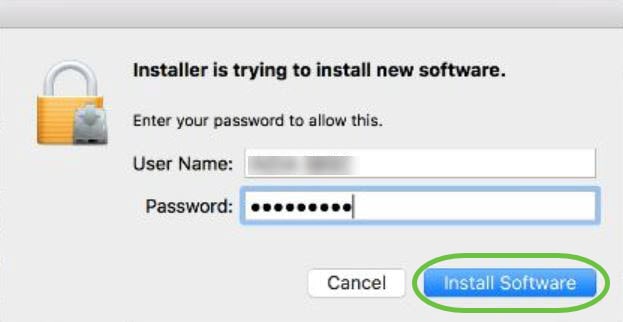
Step 12
Click Install Software.
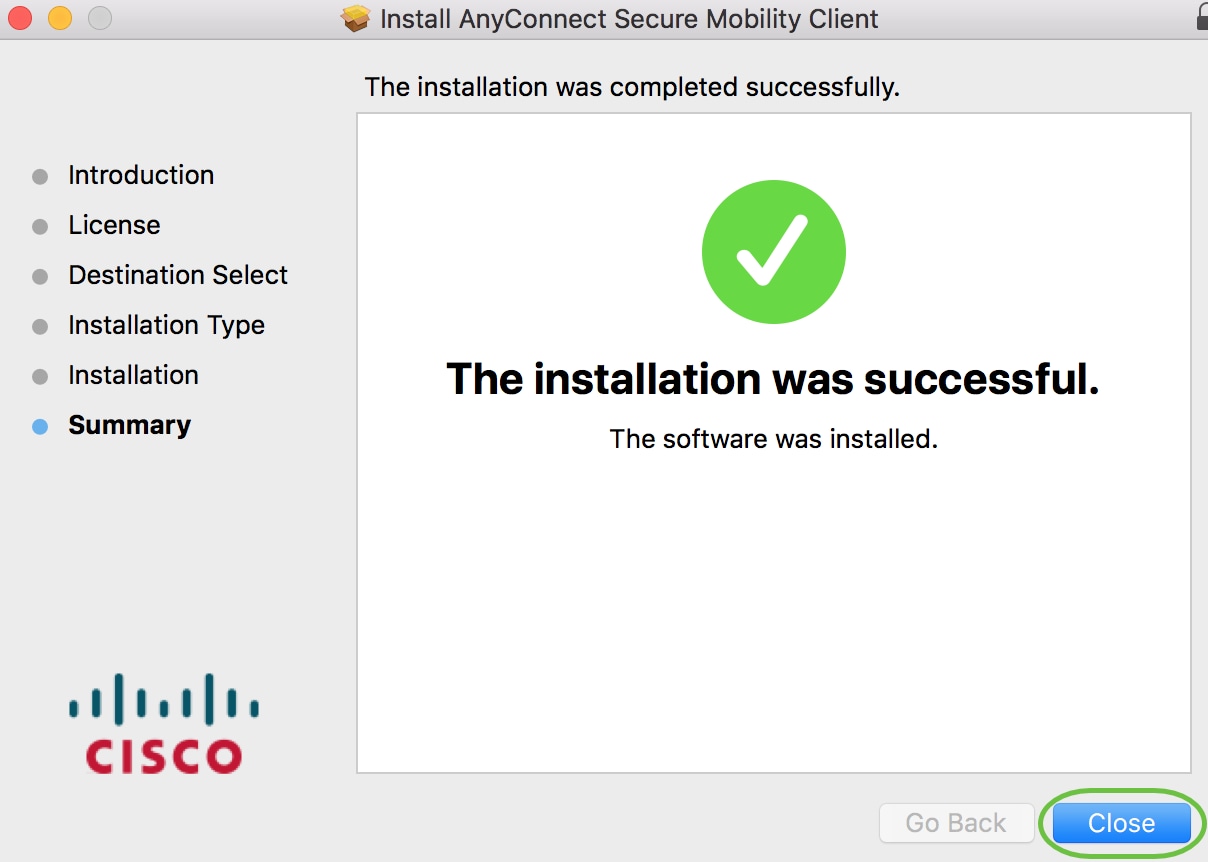
Step 13
You have now successfully installed the AnyConnect Secure Mobility Client Software on your Mac computer.
Additional Resources
AnyConnect App
To try out AnyConnect on mobile devices, the App can be downloaded from Google Play store or Apple store.
View a video related to this article.
Источник
Bypass Cisco AnyConnect Hostscan
What is hostscan?
Hostscan is a feature of Cisco AnyConnect. When a host attempts to VPN into a network, hostscan verifies specific settings are in place. A common example is ensuring Antivirus (AV) is installed. Other examples include looking for specific registry keys, checking for a firewall, etc.
From an attackers stand point, this can be a huge pain. What if I want to VPN in with my Linux box but the environment mandates AV? Or worse.. What if they are not publishing the Linux binaries at all? Let’s dig into hostscan a bit more and try to find a way around this.
How does hostscan work?
Hostscan works by downloading a few binaries (cscan, cnotify and cstub) from the AnyConnect server and executing them locally (. ). If you think about it, this alone is alarming. All it would take is an attacker compromising the ASA and replacing the hostscan binaries with rogue ones and each user that connects to VPN would be infected. But I digress.
When hostscan is done scanning the host, it does a POST to https:// /+CSCOE+/sdesktop/scan.xml?reusebrowser=1 with the scan results. As long as you POST the correct settings, you will be authorized to connect to the network. This is where hostscan-bypass comes into play.
Hostscan Bypass
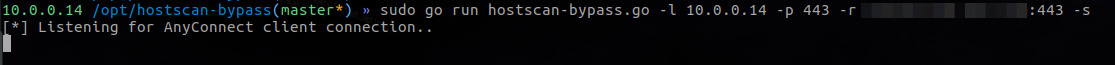
Hostscan-bypass is a hacked version of tcpprox. After playing around with AnyConnect for a while, I was able to figure out how to reliably enumerate the network settings required to connect to a given network.
So, all you have to do is run the script hostscan-bypass.go on your attacking machine and try to connect to it from the AnyConnect client. You’ll essentially setup a Man in the Middle (MITM) attack on yourself in order to get the correct network settings.
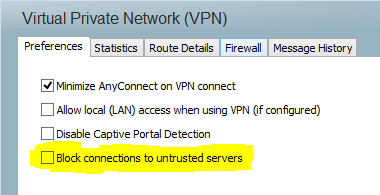
Now with the listener in place, we will initiate a connection from the AnyConnect client on the Windows host that we want to spoof. Before trying to connect, be sure to uncheck the “Block connections to unstrusted servers” box in AnyConnect’s preferences. Our attacking machine is using a self signed cert. If this box is checked, AnyConnect will refuse to connect.
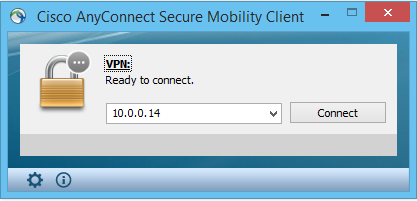
Now initiate the connection to your attacking box. In this case, my IP address was 10.0.0.14.
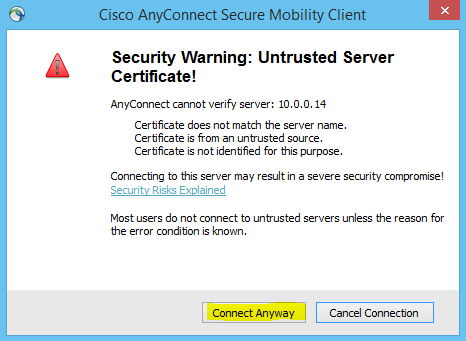
After hitting connect, you will see a prompt like this one. Click “Connect Anyway”.
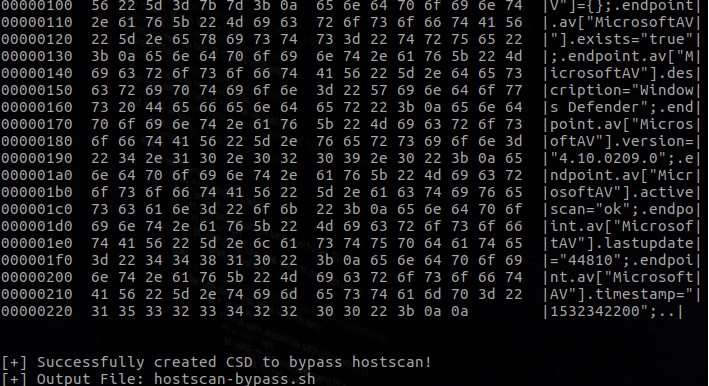
On your attacking machine, you should be seeing a bunch of activity. Now all you do is wait. You don’t need to authenticate in order for the hostscan to take place. Once the endpoint information is sent across the wire, hostscan-bypass has enough information to generate the CSD file.
You need to make hostscan-bypass.sh executable before OpenConnect can use it. Now that you have the CSD file, you can simply connect using OpenConnect:
No access to the target machine
If you have no access to the target machine, you are in unchartered waters. I discovered that AnyConnect actually publishes the requirements to connect to the target VPN, but it will require a lot of trial and error. Since you don’t have the exact endpoint arguments, you will be trying to guess them.
Take a look at the following URL- it will give you a starting point.
Источник
Cisco AnyConnect Secure Mobility Client Administrator Guide, Release 4.0
Book Title
Cisco AnyConnect Secure Mobility Client Administrator Guide, Release 4.0
Chapter Title
View with Adobe Reader on a variety of devices
Results
Chapter: Configure Posture
Configure Posture
The AnyConnect Secure Mobility Client offers an VPN Posture (HostScan) Module and an ISE Posture Module. Both provide the Cisco AnyConnect Secure Mobility Client with the ability to assess an endpoint’s compliance for things like antivirus, antispyware, and firewall software installed on the host. You can then restrict network access until the endpoint is in compliance or can elevate local user privileges so they can establish remediation practices.
VPN Posture is bundled with hostscan_version.pkg, which is the application that gathers what operating system, antivirus, antispyware, and software is installed on the host. ISE Posture deploys one client when accessing ISE-controlled networks, rather than deploying both AnyConnect and the NAC Agent. ISE Posture is a module you can choose to install as an additional security component into the AnyConnect product. HostScan, which was part of the AnyConnect bundle in release 3.x, is now a separate install.
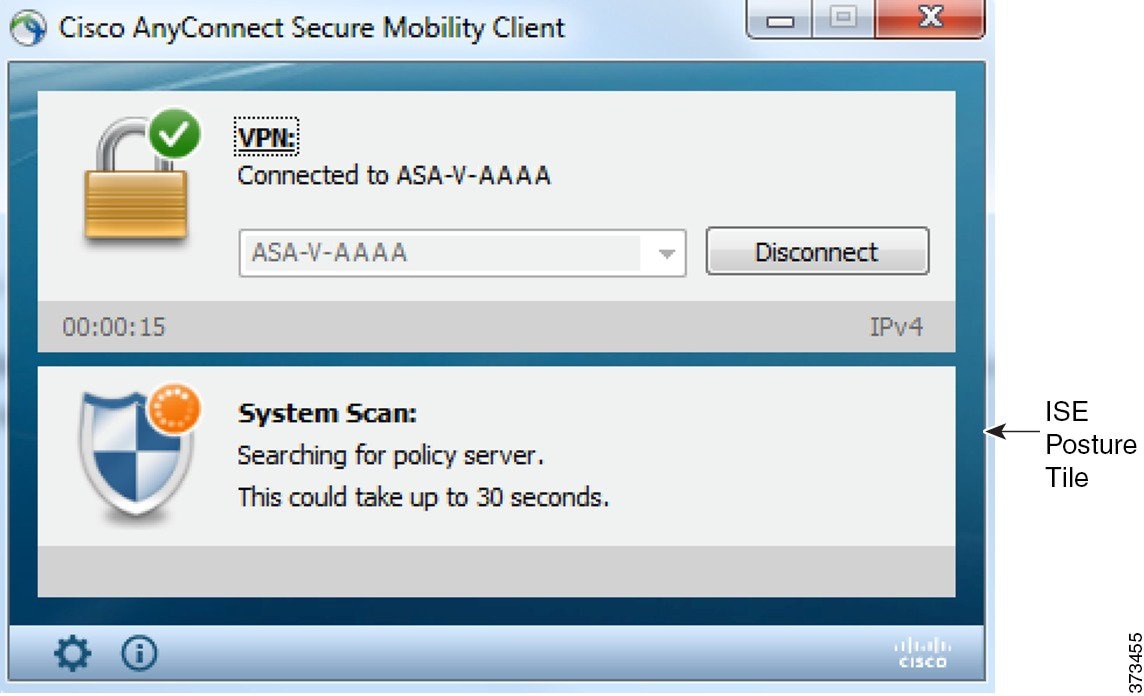
ISE Posture performs a client-side evaluation. The client receives the posture requirement policy from the headend, performs the posture data collection, compares the results against the policy, and sends the assessment results back to the headend. Even though ISE actually determines whether or not the endpoint is compliant, it relies on the endpoint’s own evaluation of the policy.
In contrast, HostScan performs server-side evaluation where the ASA asks only for a list of endpoint attributes (such as operating system, IP address, registry entries, local certificates, and filenames), and they are returned by HostScan. Based on the result of the policy’s evaluation, you can control which hosts are allowed to create a remote access connection to the security appliance.
 Note |
 Note |
 Note | With a posture lease, if the session is valid on ISE, the endpoint is expected to go from posture unknown state to compliant state. |
VLAN Monitoring and Transitioning
Some sites use different VLANs or subnets to partition their network for corporate groups and levels of access. A change of authorization (CoA) from ISE specifies a VLAN change. Changes can also happen due to administrator actions, such as session termination. To support VLAN changes during wired connections, configure the following settings in the ISE Posture profile:
VLAN Detection Interval— Determines the frequency with which the agent detects a VLAN transition and whether monitoring is disabled. VLAN monitoring is enabled when this interval is set to something besides 0. Set this value to at least 5 for macOS.
VLAN monitoring is implemented on both Windows and macOS, although it is only necessary on macOS for the detection of unexpected VLAN changes. If a VPN is connected or an acise (the main AnyConnect ISE process) is not running, it disables automatically. The valid range is 0 to 900 seconds.
Enable Agent IP Refresh—When unchecked, ISE sends the Network Transition Delay value to the agent. When checked, ISE sends DHCP release and renew values to the agent, and the agent does an IP refresh to retrieve the latest IP address.
Network Transition Delay— Used when VLAN monitoring is disabled or enabled by the agent (in the Enable Agent IP Refresh checkbox). This delay adds a buffer when a VLAN is not used, giving the agent an appropriate amount of time to wait for an accurate status from the server. ISE sends this value to the agent. If you also have the Network Transition Delay value set in the global settings on the ISE UI, the value in the ISE Posture Profile Editor overwrites it.
 Note |
 Note |
- Preferences—Allows you to block connections to untrusted servers so that during the downloader process, you receive an «Untrusted Server Blocked» message for any ISE server that has untrusted certification and is unverified. If you disable the blocking, AnyConnect will not block connections to potentially malicious network devices.
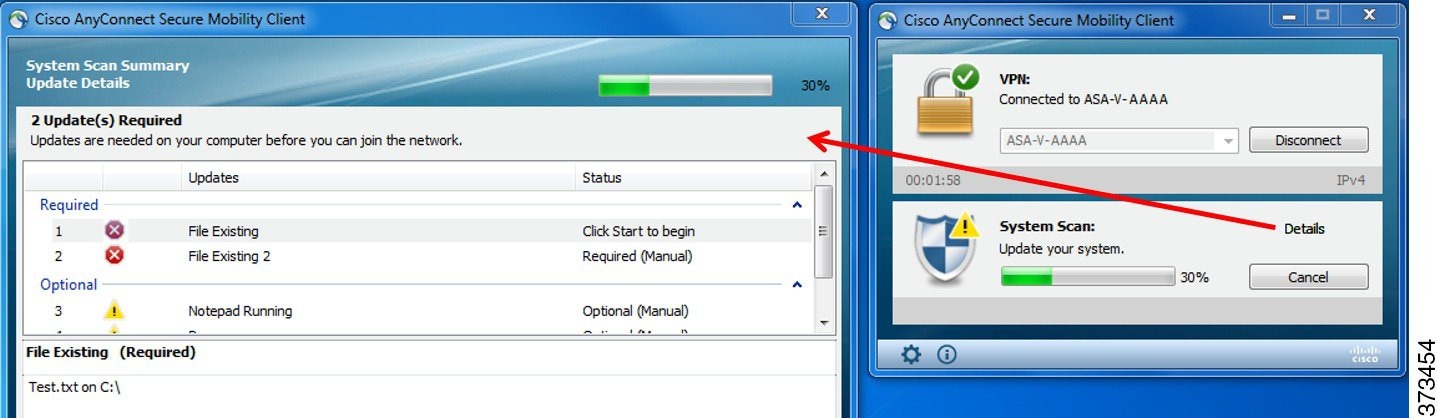
- Statistics—Provides current ISE Posture status (compliant or not), OPSWAT version information, the status of the Acceptable Use Policy, the last running time stamp for posture, any missing requirements, and any other statistics deemed important enough to display for troubleshooting purposes.
- Security Products—Accesses the list of antivirus and antispyware products installed on your system.
- Scan Summary—Allows the users to see whatever posture items the administrator configured for them to see. For example, when configured, they could see all of the items that have been postured on their system or only the ones that failed the posture check and required remediation.
- Message History—Provides a history of every status message sent to the system tray for a component. This history is useful for troubleshooting.
What VPN Posture (HostScan) Module Provides
HostScan
HostScan is a package that installs on the remote device after the user connects to the ASA and before the user logs in. HostScan consists of any combination of the basic module, the endpoint assessment module, and the advanced endpoint assessment module. HostScan is not supported with mobile devices (Android, iOS, Chrome, or UWP).
 Note | In AnyConnect release 3.x, this package was bundled in the hostscan_version.pkg file, which must be updated in ASA under HostScan image and enabled to get HostScan functioning. It is now a separate install. |
Basic Functionality
HostScan automatically identifies operating systems and service packs on any remote device establishing a Cisco clientless SSL VPN or AnyConnect VPN client session.
You can also configure HostScan to inspect the endpoint for specific processes, files, and registry keys. It performs all of these inspections before full tunnel establishment and sends this information to the ASA to distinguish between corporate-owned, personal, and public computers. The information can also be used in assessments.
 Note |
 Note | HostScan gathers service release (GDR) information about Microsoft software updates on a Windows client system. A service release contains multiple hotfixes. The service release endpoint attribute is used in DAP rules, not hotfixes. |
Endpoint Assessment
Endpoint Assessment is a HostScan extension that examines the remote computer for a large collection of antivirus and antispyware applications, associated definitions updates, and firewalls. You can use this feature to combine endpoint criteria to satisfy your requirements before the ASA assigns a specific dynamic access policy (DAP) to the session.
See the Dynamic Access Policies section in the appropriate version of the Cisco ASA Series VPN Configuration Guide for details.
Advanced Endpoint Assessment:Antivirus, Antispyware, and Firewall Remediation
On Windows, Mac OS X, and Linux desktops, Advanced Endpoint Assessment can attempt to begin remediation of various aspects of antivirus, antispyware, and personal firewall protection if that software allows a separate application to begin remediation.
Antivirus—Remediate these components of antivirus software:
Force File System Protection—Enable antivirus software that is disabled.
Force Virus Definitions Update—Begin an update of virus definitions, if the antivirus definitions have not been updated in the number of days defined by the Advanced Endpoint Assessment configuration.
Antispyware—Begin an update of antispyware definitions, if the antispyware definitions have not been updated in the number of days defined by the Advanced Endpoint Assessment configuration.
Personal Firewall—Reconfigure firewall settings and rules that do not meet the requirements defined in the Advanced Endpoint Assessment configuration. For example,
Enable or disable the firewall.
Prevent or allow applications to run.
Block or open ports.
 Note |