- File Security and Access Rights
- How to disable Open File security warning on Windows 10
- How can I disable Open File security warning on Windows 10?
- 1. Change your Internet options
- 2. Disable User Account Control
- 3. Modify your registry
- 4. Edit your Group Policy
- 5. Use Command Prompt
- 6. Unblock the file
- 7. Uncheck Always ask before opening this file option
- 8. Take ownership over the problematic file
- 9. Change Local intranet settings
- 10. Use Command Prompt
- 11. Check Include all network paths options
- 12. Create a bat file that will run the problematic file
- 13. Use the icals command
- 14. Download and use streams utility
- 15. Copy the files to a different location
File Security and Access Rights
Because files are securable objects, access to them is regulated by the access-control model that governs access to all other securable objects in Windows. For a detailed explanation of this model, see Access Control.
You can specify a security descriptor for a file or directory when you call the CreateFile, CreateDirectory, or CreateDirectoryEx function. If you specify NULL for the lpSecurityAttributes parameter, the file or directory gets a default security descriptor. The access control lists (ACL) in the default security descriptor for a file or directory are inherited from its parent directory. Note that a default security descriptor is assigned only when a file or directory is newly created, and not when it is renamed or moved.
To retrieve the security descriptor of a file or directory object, call the GetNamedSecurityInfo or GetSecurityInfo function. To change the security descriptor of a file or directory object, call the SetNamedSecurityInfo or SetSecurityInfo function.
The valid access rights for files and directories include the DELETE, READ_CONTROL, WRITE_DAC, WRITE_OWNER, and SYNCHRONIZE standard access rights. The table in File Access Rights Constants lists the access rights that are specific to files and directories.
Although the SYNCHRONIZE access right is defined within the standard access rights list as the right to specify a file handle in one of the wait functions, when using asynchronous file I/O operations you should wait on the event handle contained in a properly configured OVERLAPPED structure rather than using the file handle with the SYNCHRONIZE access right for synchronization.
The following are the generic access rights for files and directories.
| Access right | Description |
|---|---|
| FILE_GENERIC_EXECUTE | FILE_EXECUTE FILE_READ_ATTRIBUTES STANDARD_RIGHTS_EXECUTE SYNCHRONIZE |
| FILE_GENERIC_READ | FILE_READ_ATTRIBUTES FILE_READ_DATA FILE_READ_EA STANDARD_RIGHTS_READ SYNCHRONIZE |
| FILE_GENERIC_WRITE | FILE_APPEND_DATA FILE_WRITE_ATTRIBUTES FILE_WRITE_DATA FILE_WRITE_EA STANDARD_RIGHTS_WRITE SYNCHRONIZE |
Windows compares the requested access rights and the information in the thread’s access token with the information in the file or directory object’s security descriptor. If the comparison does not prohibit all of the requested access rights from being granted, a handle to the object is returned to the thread and the access rights are granted. For more information about this process, see Interaction between Threads and Securable Objects.
By default, authorization for access to a file or directory is controlled strictly by the ACLs in the security descriptor associated with that file or directory. In particular, the security descriptor of a parent directory is not used to control access to any child file or directory. The FILE_TRAVERSE access right can be enforced by removing the BYPASS_TRAVERSE_CHECKING privilege from users. This is not recommended in the general case, as many programs do not correctly handle directory traversal errors. The primary use for the FILE_TRAVERSE access right on directories is to enable conformance to certain IEEE and ISO POSIX standards when interoperability with Unix systems is a requirement.
The Windows security model provides a way for a child directory to inherit, or to be prevented from inheriting, one or more of the ACEs in the parent directory’s security descriptor. Each ACE contains information that determines how it can be inherited, and whether it will have an effect on the inheriting directory object. For example, some inherited ACEs control access to the inherited directory object, and these are called effective ACEs. All other ACEs are called inherit-only ACEs.
The Windows security model also enforces the automatic inheritance of ACEs to child objects according to the ACE inheritance rules. This automatic inheritance, along with the inheritance information in each ACE, determines how security restrictions are passed down the directory hierarchy.
Note that you cannot use an access-denied ACE to deny only GENERIC_READ or only GENERIC_WRITE access to a file. This is because for file objects, the generic mappings for both GENERIC_READ or GENERIC_WRITE include the SYNCHRONIZE access right. If an ACE denies GENERIC_WRITE access to a trustee, and the trustee requests GENERIC_READ access, the request will fail because the request implicitly includes SYNCHRONIZE access which is implicitly denied by the ACE, and vice versa. Instead of using access-denied ACEs, use access-allowed ACEs to explicitly allow the permitted access rights.
Another means of managing access to storage objects is encryption. The implementation of file system encryption in Windows is the Encrypted File System, or EFS. EFS encrypts only files and not directories. The advantage of encryption is that it provides additional protection to files that is applied on the media and not through the file system and the standard Windows access control architecture. For more information on file encryption, see File Encryption.
In most cases, the ability to read and write the security settings of a file or directory object is restricted to kernel-mode processes. Clearly, you would not want any user process to be able to change the ownership or access restriction on your private file or directory. However, a backup application would not be able to complete its job of backing up your file if the access restrictions you have placed on your file or directory does not allow the application’s user-mode process to read it. Backup applications must be able to override the security settings of file and directory objects to ensure a complete backup. Similarly, if a backup application attempts to write a backup copy of your file over the disk-resident copy, and you explicitly deny write privileges to the backup application process, the restore operation cannot complete. In this case also, the backup application must be able to override the access control settings of your file.
The SE_BACKUP_NAME and SE_RESTORE_NAME access privileges were specifically created to provide this ability to backup applications. If these privileges have been granted and enabled in the access token of the backup application process, it can then call CreateFile to open your file or directory for backup, specifying the standard READ_CONTROL access right as the value of the dwDesiredAccess parameter. However, to identify the calling process as a backup process, the call to CreateFile must include the FILE_FLAG_BACKUP_SEMANTICS flag in the dwFlagsAndAttributes parameter. The full syntax of the function call is the following:
This will allow the backup application process to open your file and override the standard security checking. To restore your file, the backup application would use the following CreateFile call syntax when opening your file to be written.
There are situations when a backup application must be able to change the access control settings of a file or directory. An example is when the access control settings of the disk-resident copy of a file or directory is different from the backup copy. This would happen if these settings were changed after the file or directory was backed up, or if it was corrupted.
The FILE_FLAG_BACKUP_SEMANTICS flag specified in the call to CreateFile gives the backup application process permission to read the access-control settings of the file or directory. With this permission, the backup application process can then call GetKernelObjectSecurity and SetKernelObjectSecurity to read and than reset the access-control settings.
If a backup application must have access to the system-level access control settings, the ACCESS_SYSTEM_SECURITY flag must be specified in the dwDesiredAccess parameter value passed to CreateFile.
Backup applications call BackupRead to read the files and directories specified for the restore operation, and BackupWrite to write them.
How to disable Open File security warning on Windows 10
- Eager to discover a quick way to disable Open File security warning on Windows 10? That’s precisely what we have for you.
- To make that happen, change your Internet options. You may also disable User Account Control.
- Feel free to visit our Windows 10 Settings section to find several easy to understand tips and tricks.
- Don’t forget to bookmark this Tech Tutorials Hub to be one click away from professional assistance at any hour.
Your online security is rather important, so getting a message that states Your Internet security settings prevented one or more files is nothing out of the ordinary.
How many times have you tried to browse freely, only to receive a message like this? You know the answer to that better than anyone else.
Open File security warnings can be a bit annoying, and in this article, we’ll show you how to easily disable them on Windows 10.
How can I disable Open File security warning on Windows 10?
1. Change your Internet options
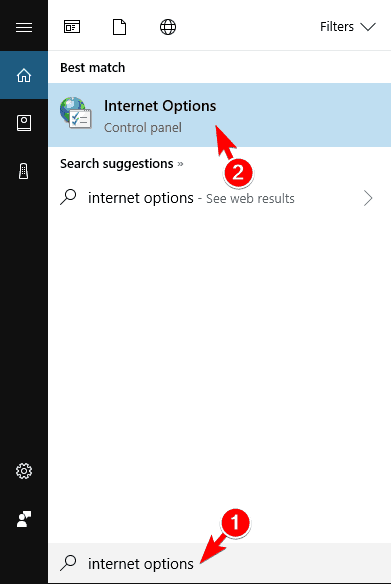
- Press Windows Key+ S and enter Internet options. Select Internet Options from the list of results.
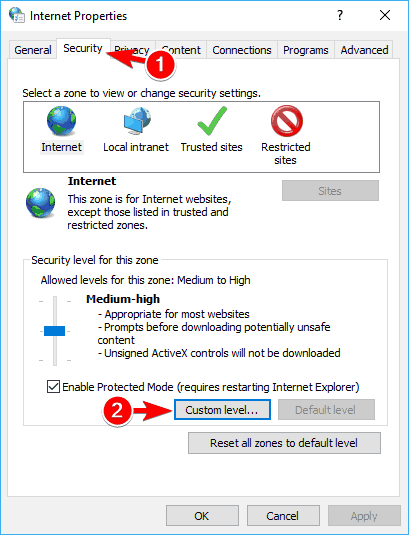
- When the Internet Properties window opens, go to the Security tab and click on the Custom Level button.
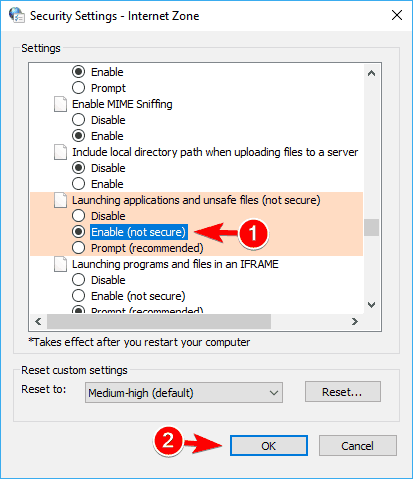
- A list of settings will appear. Locate Launching applications and unsafe files and select Enable. Now click OK to save changes.
Open File security warning usually appears when trying to run downloaded files, but you can fix this problem simply by changing your Internet options.
This is relatively simple and you can do it by following the above steps. After changing these settings you should be able to run downloaded files without any problems.
2. Disable User Account Control
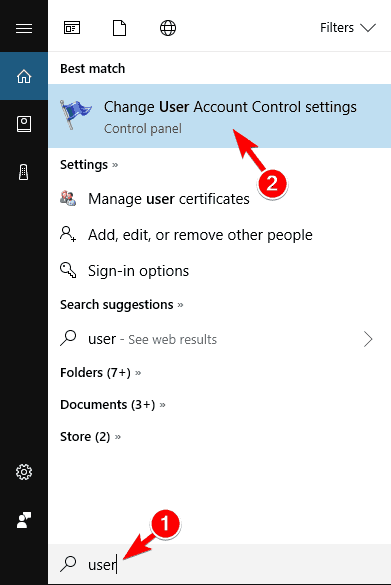
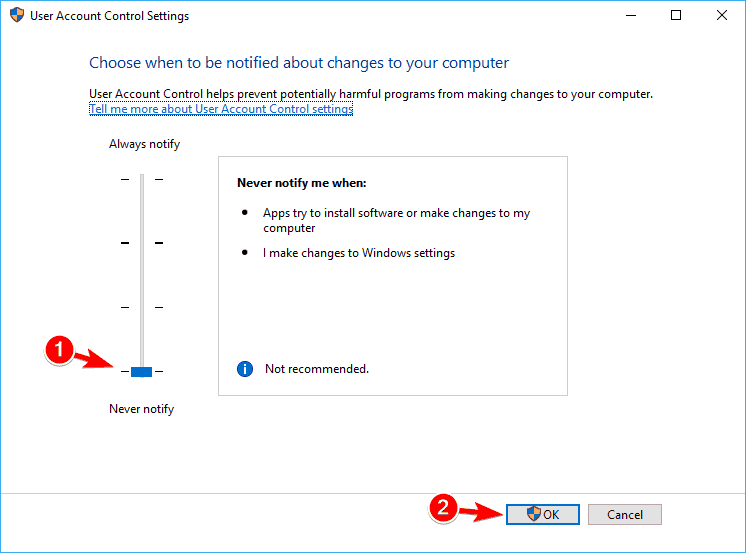
- Press Windows Key + S and enter user. Select Change User Account Control settings from the menu.
- When User Account Control Settings window appears, move the slider all the way down to Never notify. Click on OK to save changes.
Once you disable User Account Control, you should see fewer security warnings on your PC. Disabling User Account Control won’t greatly reduce your security, so you can disable it without fear.
If you’re frequently getting an Open File security warning, you might be able to disable it by turning off User Account Control.
This is a security feature of Windows that notifies you when trying to change a setting or perform an action that requires administrative privileges.
Users claim that this feature is the cause behind this security warning, and if you want to disable it, you need to turn off User Account Control.
3. Modify your registry
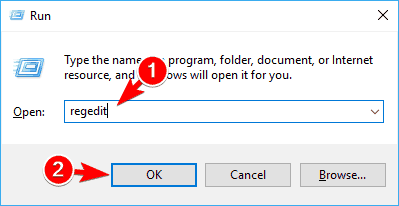
- Press Windows Key + R and enter regedit. Press Enter or click OK.
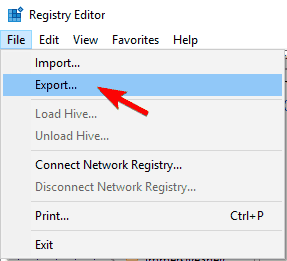
- When Registry Editor opens, go to File > Export.
Select All as Export range, enter the desired File name, choose a safe location and click on Save.
In case anything goes wrong after modifying your registry, you can easily restore it by running the exported file.
- Navigate to the Associations key. If this key isn’t available, you’ll need to create it. To do that, simply right click the Policies key and choose New > Key from the menu.
Now enter Associations as the name of the key and navigate to it.
- Once you navigate to Associations key, look for LowRiskFileTypes in the right pane. If this value isn’t available, you’ll need to create it manually. To do that, right-click the empty space in the right pane and choose New > String Value from the menu.
Enter LowRiskFileTypes as the name of the string. Double click the LowRiskFileTypes to open its properties.
- When the Properties window opens, paste the following into the Value data field: .avi;.bat;.cmd;.exe;.htm;.html;.lnk;.mpg;.mpeg;.mov;.mp3;.mp4;.mkv;.msi;.m3u;.rar;.reg;.txt;.vbs;.wav;.zip;.7z
If needed, you can add more extensions in order to disable the security warning for them. After you’re done, click on OK.
- After making the changes, close Registry Editor and restart your PC.
Your registry holds sensitive system information, and by modifying it you can disable this security warning from appearing.
Modifying the registry can be potentially dangerous if you’re not careful, so we advise you to be extra cautious.
Once your PC restarts, the problem should be fixed and you won’t see the security warning anymore.
If you don’t want to manually edit your registry, you can download Disable_Open-File_Security_Warning.reg file and run it.
By doing that, you’ll disable the security warning for the specified file types. In case you want to enable the security warning, simply download Enable_Open-File_Security_Warning.reg and run it.
4. Edit your Group Policy
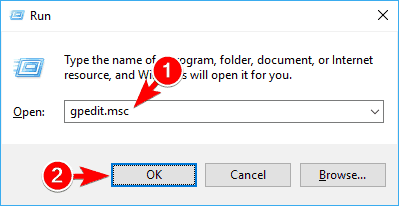
- Press Windows Key + Rkeyboard shortcut and enter gpedit.msc. Press Enter or click OK.
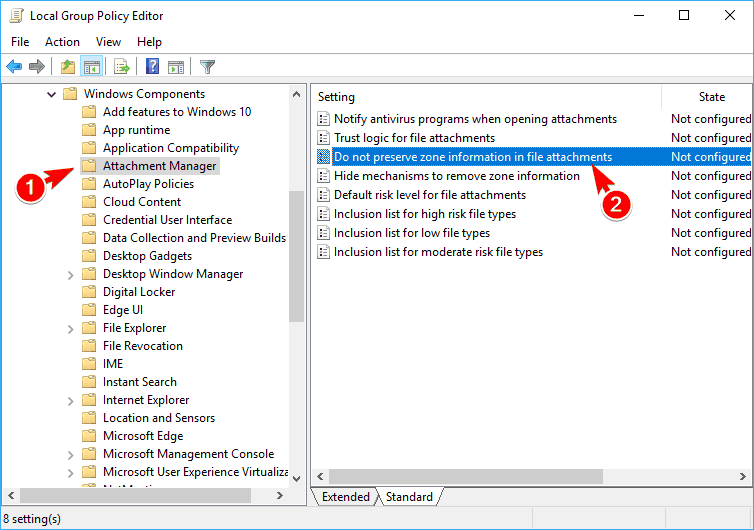
- In the left pane navigate to User Configuration > Administrative Templates > Windows Components > Attachment Manager. In the right pane locate Do not preserve zone information in file attachments.
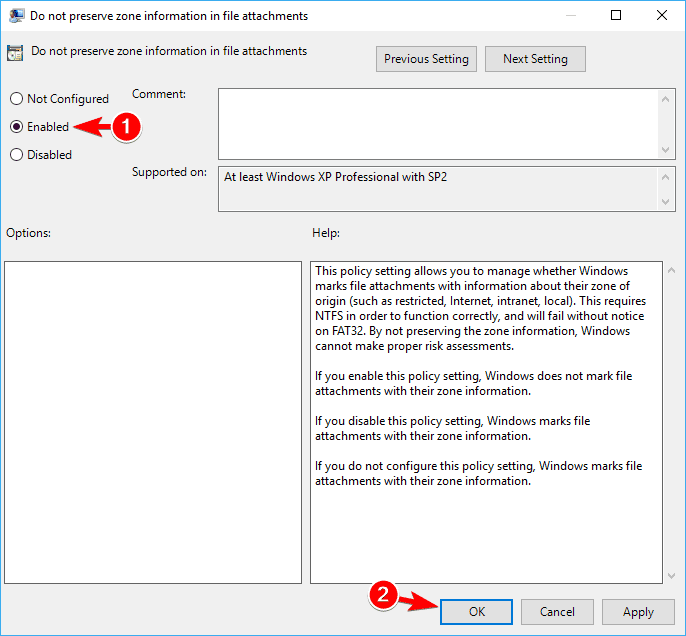
- Select Enabled and click on Apply and OK to save changes.
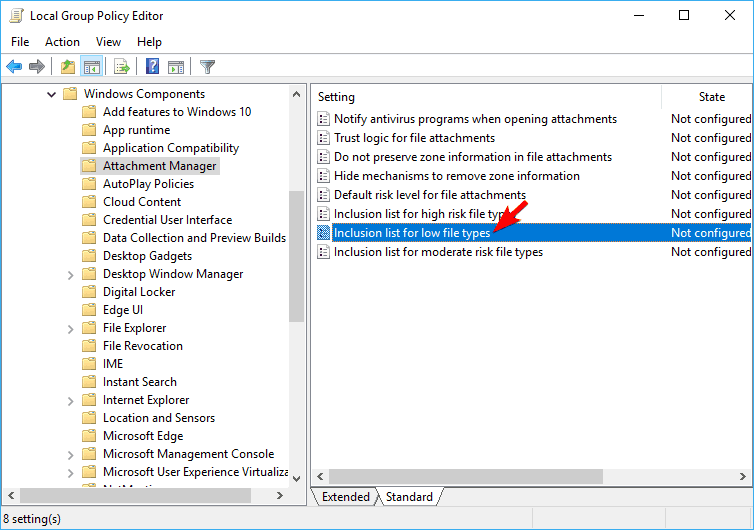
- Now click on the Inclusion list for low file types.
- Select Enabled and paste the following line in Specify low-risk extensions input field: .avi;.bat;.cmd;.exe;.htm;.html;.lnk;.mpg;.mpeg;.mov;.mp3;.mp4;.mkv;.msi;.m3u;.rar;.reg;.txt;.vbs;.wav;.zip;.7z
- Click on Apply and OK to save changes.
You can prevent this security warning from appearing by using Group Policy Editor.
This is a useful application that allows you to change various settings, but unfortunately, it’s available only on Pro and Enterprise versions of Windows.
To use Group Policy, do as described above. Close Group Policy Editor and restart your PC. Once your PC restarts, check if the problem still appears.
Check our handy guide to easily edit the Group Policy like a pro.
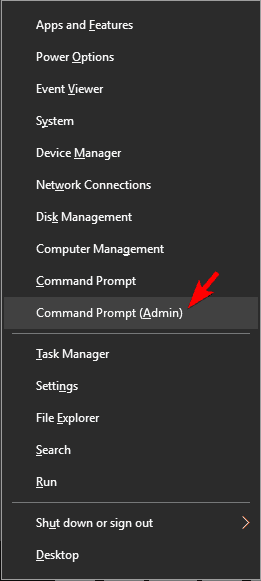
5. Use Command Prompt
- Press Windows Key + X and choose Command Prompt (Admin) from the menu. If Command Prompt isn’t available, you can use PowerShell(Admin) instead.
- When Command Prompt starts, enter the following lines:
- REG ADD «HKCUSoftwareMicrosoftWindowsCurrentVersionInternet SettingsZones3» /V «1806» /T «REG_DWORD» /D «00000000» /F
- REG ADD «HKLMSoftwareMicrosoftWindowsCurrentVersionInternet SettingsZones3» /V «1806» /T «REG_DWORD» /D «00000000» /F
- REG ADD «HKLMSOFTWAREPoliciesMicrosoftInternet ExplorerSecurity» /V «DisableSecuritySettingsCheck» /T «REG_DWORD» /D «00000001» /F
You can also prevent this security message from appearing by using Command Prompt. Many users don’t know this, but you can use Command Prompt to quickly edit your registry.
We have to warn you that modifying the registry can be potentially dangerous, so you’re doing it at your own risk. To fix this problem using Command Prompt, do as described above.
After commands are executed, you might have to restart your PC to apply the changes.
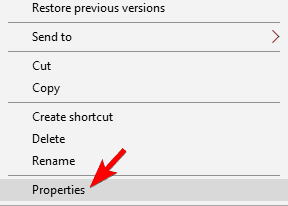
6. Unblock the file
- Right-click the problematic file and choose Properties from the menu.
- When the Properties window opens, go to the General tab and click on the Unblock button.
To stop this security warning from appearing, you might need to unblock your file. Sometimes files can become blocked causing this warning to appear.
To unblock your file, be sure that the file is located in a directory that is associated with your user accounts such as your Desktop or Documents.
If you want to unblock a specific file, complete the above procedure. After doing that, you won’t see the security warning for this file anymore.
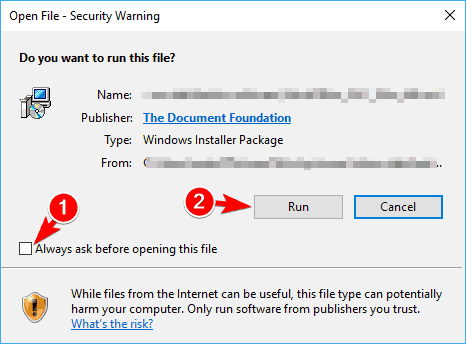
7. Uncheck Always ask before opening this file option
- Run the problematic file.
- You should see an Open File security warning. Uncheck Always ask before opening this file option. Now click on Run to continue.
If you want to disable Open File security warning for a specific file, you can do it simply by unchecking a single option. To do that, follow the above procedure.
After doing that, you should be able to open that file without any security warnings.
This method is simple and straightforward, and it’s rather useful if you want to disable this security warning for a specific file.
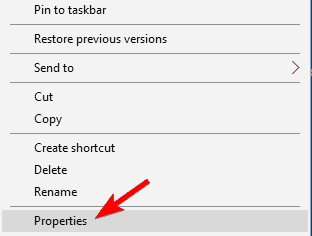
8. Take ownership over the problematic file
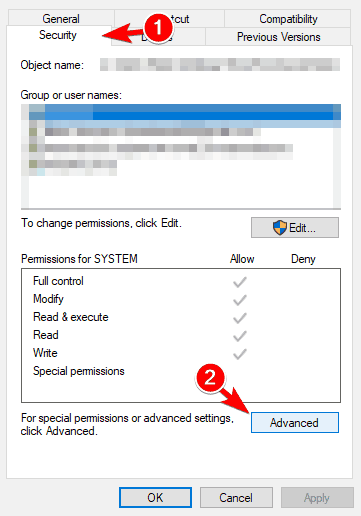
- Locate the file that is giving you this security warning and right-click it. Choose Properties from the menu.
- When the Properties window opens, go to the Security tab and click on Advanced.
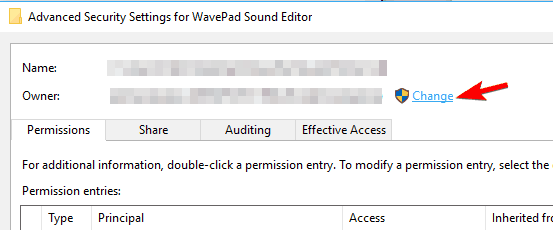
- In the Owner section click on Change.
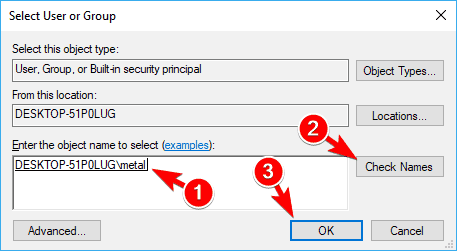
- Select User or Group window will appear. In the Enter the object name to select field enter your user name. Now click on Check Names. If everything is in order, click on OK to save changes.
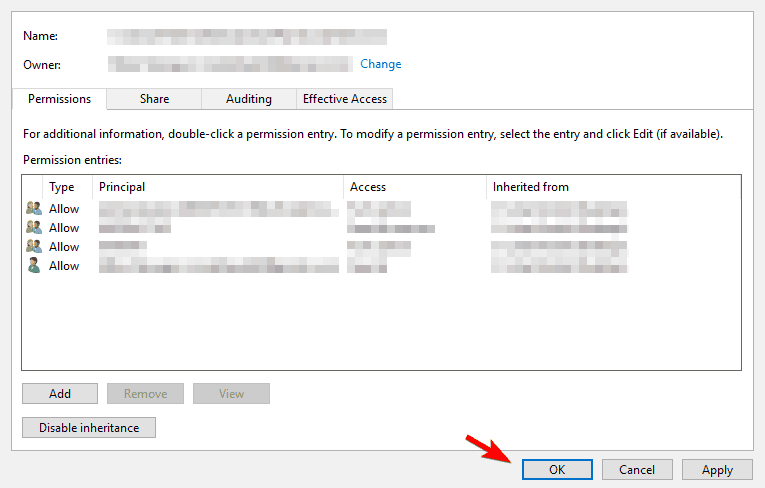
- The owner of the file should now be changed. Now you just have to click on Apply and OK to save changes.
If you’re getting this security warning on your PC, you might be able to disable it for a specific file by taking ownership of that file.
This is relatively simple, and you can do it by following the above procedure.
After taking ownership of the file, you should be able to run it without any security warnings. If you’re an advanced user, you can also use Command Prompt to take ownership of a certain file.
To do that, just follow these steps:
- Start Command Prompt or PowerShell as administrator.
- When Command Prompt opens, enter:
- takeown /F
Of course, be sure to replace the
with an actual path to the problematic file. This method is faster, but it requires you to enter the exact path to the problematic application.
If you’re an advanced user and familiar with Command Prompt, feel free to try this method instead.
9. Change Local intranet settings
- Open InternetOptions. We showed you how to do that in Solution 1, so be sure to check it for detailed instructions.
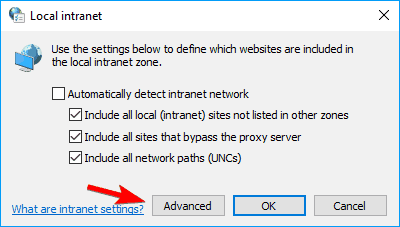
- When the Internet Properties window opens, go to the Security tab and select Local intranet. Now click on the Sites button.
- The local intranet window will now appear. Click on the Advanced button.
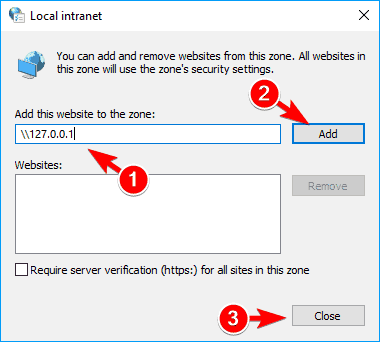
- Now enter the address of the server in the Add this website to the zone field. You can use the server’s domain or you can use its IP address. Just be sure to enter before the server’s address or domain. Now click on the Add button. After you’re done adding servers, click the Close button.
- Save changes and your problem should be resolved completely.
According to users, this security warning can appear if you’re trying to run an application from a network directory.
To fix this problem, you need to add the name or the IP address of the server on which the application is stored in Intranet settings.
This is relatively simple to do, and you can do it by following the above steps.
If you don’t want to use Internet Options, you can make the same changes using the Group Policy Editor. To do that, follow these steps:
- Open Group Policy Editor. To see how to do that, check the first step of Solution 4.
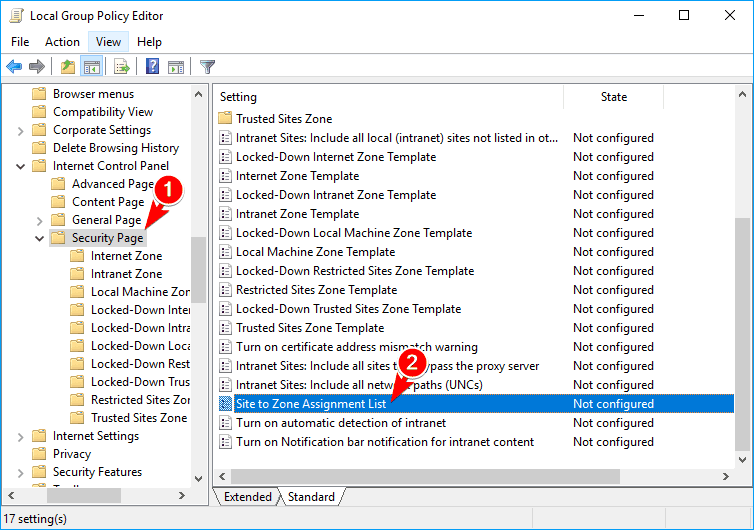
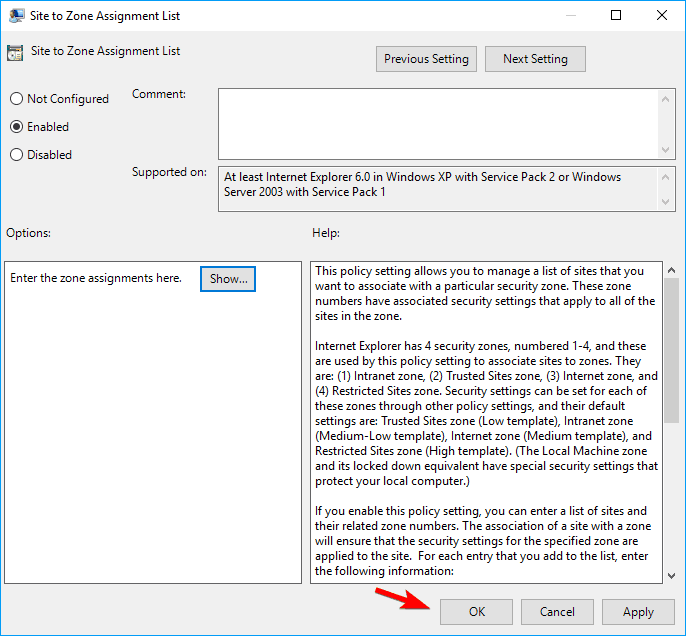
- When Group Policy Editor starts, navigate to ComputerConfiguration > Administrative Templates > Windows Components >Internet Explorer > Internet Control Panel > Security Page in the left pane. In the right pane, locate and double click Site to Zone Assignment List.
- Now select Enabled and click on the Show button.
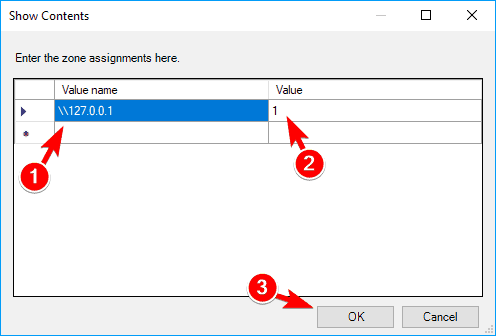
- In the Value name column enter the IP address or domain name of the server. As for Value, enter 1. After you enter all the necessary addresses, click on OK to save changes.
- Now just click on Apply and OK to apply changes.
Both methods will achieve the same results, so you can use any of them. Keep in mind that this solution works only if you’re trying to run an application from a network directory.
10. Use Command Prompt
- Start Command Prompt as administrator.
- Use Command Prompt to navigate to the location of the problematic file.
- Now enter the following commands:
- move your_file_name.exe NewName
- type NewName > your_file_name.exe
If you’re frequently getting this security warning, you might be able to disable it for a specific file by using Command Prompt. To do that you need to follow these above steps.
This is a solid workaround, and it works according to users, so feel free to try it out. Keep in mind that in order to use this solution you need to have a basic understanding of Command Prompt syntax.
11. Check Include all network paths options
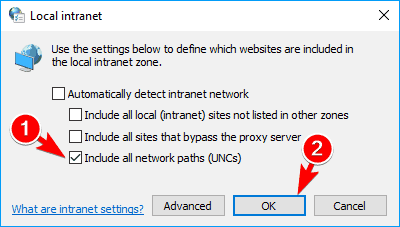
- Open Internet Options. Navigate to the Security tab, select Local intranet, and click on Sites button.
- The local intranet window will appear. Uncheck all options except Include all network paths (UNCs). After doing that, click on OK to save changes.
- Optional: Few users suggest that you should check Include all local (intranet) sites not listed in other zones option as well, so you might want to do that.
Few users claim that you can fix this problem simply by checking a few settings in Internet Options. To do that, follow the above procedure.
After doing that, the problem should be fixed and you’ll be able to run files from network directories without any problems.
12. Create a bat file that will run the problematic file
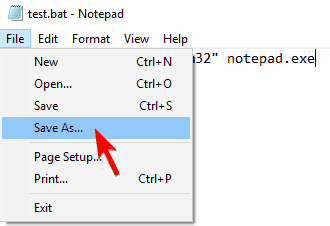
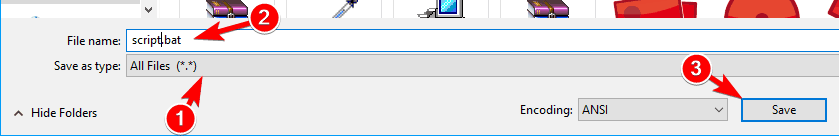
- Open Notepad.
- Now paste the following code:
- start c:windowssystem32 notepad.exe
We used Notepad as an example, but if you want to launch any other application using the bat file, you need to enter the location of the file between the quotes and the file name after it.
According to users, you can avoid this security warning while running a certain application simply by creating a bat file that will start the application for you. To do that, follow these steps:
This is a solid workaround, but it might be a bit complicated since you have to create a bat script for that specific file.
Since this is just a workaround, you’ll have to use the script to start the desired application every time.
13. Use the icals command
- Open Command Prompt as administrator.
- When Command Prompt starts, run the following commands one by one:
- ICACLS «%programdata%MicrosoftWindowsStart MenuPrograms» /Setintegritylevel (OI)(CI)Medium
- ICACLS «%userprofile%FavoritesLinks» /Setintegritylevel (OI)(CI)Medium
- ICACLS «%userprofile%AppDataRoamingMicrosoftInternet ExplorerQuick Launch» /Setintegritylevel (OI)(CI)Medium
- ICACLS «%userprofile%AppDataRoamingMicrosoftInternet ExplorerQuick LaunchUser pinnedTaskbar» /Setintegritylevel (OI)(CI)Medium
Several reported this security warning while trying to run applications from Start Menu or from the Taskbar.
According to them, you can fix this problem simply by using the icals command. This is relatively simple and you can do it by following the above steps.
After running these commands the security warning should disappear and you won’t see it while trying to run applications from Taskbar or Start Menu.
If you’re having this problem with Desktop shortcuts, you might be able to fix it by running Command Prompt and using ICACLS C:Users Desktop /Setintegritylevel (OI)(CI)M command.
After doing that, you should be able to run shortcuts from your Desktop without problems.
14. Download and use streams utility
If you’re getting Open File security warning while opening a specific file, you might be able to fix it by using streams tools. This tool is a part of Sysinternals and you can download it for free from Microsoft’s website.
After you download the tool, you need to start it manually or use Command Prompt to navigate to its directory and enter the following command:
- streams.exe -accepteula -d
After running this command you’ll remove all zone data from that file and you won’t see any security warnings while running it.
15. Copy the files to a different location
According to users, you might be able to fix the problem with the annoying security warning simply by copying the affected files to a new location.
To do that, locate the problematic files and select them. Now copy them to your Desktop.
After doing that, delete the original files from their directory. Now move the files from your Desktop to the original location. After doing that you should be able to run those files without any problems.
Users reported that this workaround works with Internet Explorer favorites, but be sure to try it with other files that are giving you this security warning.
Open File security warning can be rather annoying at times, but you should be able to prevent it from appearing by using one of our solutions.
Moreover, use them when encountering these similar issues too:
- Open file security warning we can’t verify who created this file – Solve this rather common issue shouldn’t be too complicated. Feel free to change your Internet options or set up the file location as a trusted site and see if this makes any difference.
- Open file security warning add trusted locations – Countless users have been constantly trying to solve this issue to absolutely no avail. If you’re one of them too, the above tips are pure gold.


 Select All as Export range, enter the desired File name, choose a safe location and click on Save.
Select All as Export range, enter the desired File name, choose a safe location and click on Save. 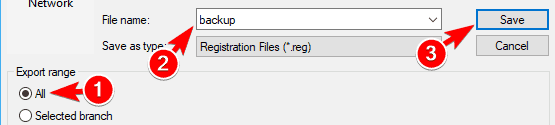 In case anything goes wrong after modifying your registry, you can easily restore it by running the exported file.
In case anything goes wrong after modifying your registry, you can easily restore it by running the exported file. Now enter Associations as the name of the key and navigate to it.
Now enter Associations as the name of the key and navigate to it.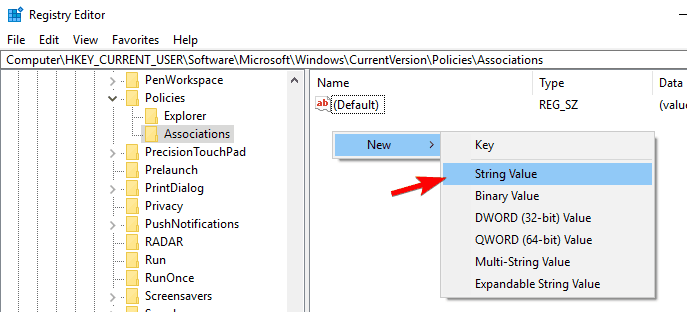 Enter LowRiskFileTypes as the name of the string. Double click the LowRiskFileTypes to open its properties.
Enter LowRiskFileTypes as the name of the string. Double click the LowRiskFileTypes to open its properties.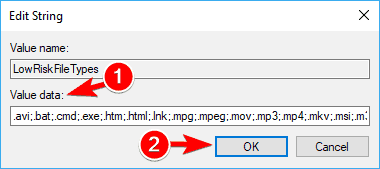 If needed, you can add more extensions in order to disable the security warning for them. After you’re done, click on OK.
If needed, you can add more extensions in order to disable the security warning for them. After you’re done, click on OK.