- Getting Started With Identity Awareness
- Related Topics
- Introduction
- Comparison of Acquisition Sources
- AD Query
- How AD Query Works- Firewall Rule Base
- Browser-Based Authentication
- How Captive Portal Works- Firewall Rule
- How Transparent Kerberos Authentication Works
- Identity Agents
- Downloading Endpoint Identity Agent
Getting Started With Identity Awareness
Related Topics
Introduction
Traditionally, firewalls use IP addresses to monitor traffic and are unaware of the user and computer identities behind those IP addresses. Identity Awareness removes this notion of anonymity since it maps users and computer identities. This lets you enforce access and audit data based on identity.
Identity Awareness is an easy to deploy and scalable solution. It is applicable for both Active Directory and non-Active Directory based networks as well as for employees and guest users. It is currently available on the Firewall blade and Application Control blade and will operate with other blades in the future.
Identity Awareness lets you easily configure network access and auditing based on network location and:
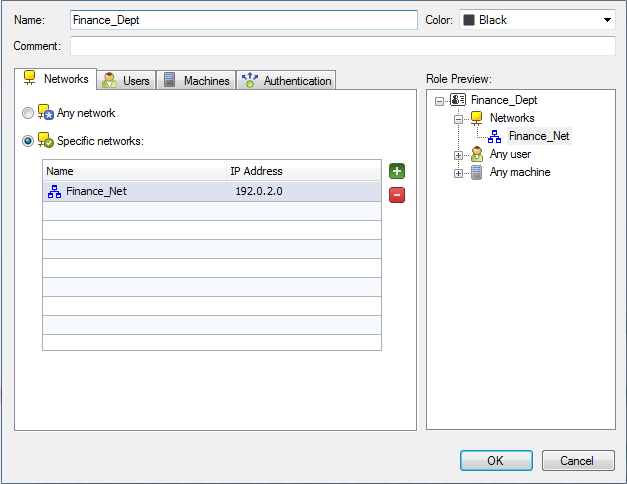
- The identity of a user
- The identity of a computer
When Identity Awareness identifies a source or destination, it shows the IP address of the user or computer with a name. For example, this lets you create firewall rules with any of these properties. You can define a firewall rule for specific users when they send traffic from specific computers or a firewall rule for a specific user regardless of which computer they send traffic from.
In SmartDashboard, you use Access Role objects to define users, computers and network locations as one object.
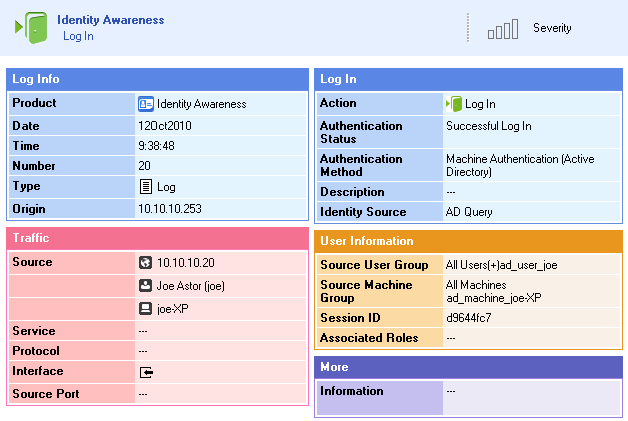
Identity Awareness also lets you see user activity in SmartView Tracker and SmartEvent based on user and computer name and not just IP addresses.
Identity Awareness gets identities from these acquisition sources:
- AD Query
- Browser-Based Authentication
- Endpoint Identity Agent
- Terminal Servers Identity Agent
- Remote Access
Identity Awareness Security Gateways can share the identity information that they acquire with Identity Awareness Security Gateways. In this way, users that need to pass through many Security Gateways are only identified once. See Advanced Deployment for more information.
Comparison of Acquisition Sources
These tables show how identity sources are different in terms of usage and deployment considerations. Depending on those considerations, you can configure Identity Awareness to use one identity source or a combination of identity sources.
Browser-Based Authentication — Captive Portal
Unidentified users log in with a user name and password in a Captive Portal. After authentication, the user clicks a link to go to the destination address.
- Identity based enforcement for non-AD users (non-Windows and guest users)
- You can require deployment of Endpoint Identity Agents
- Used for identity enforcement (not intended for logging purposes).
Gets identity data seamlessly from Active Directory (AD).
- Identity based auditing and logging
- Leveraging identity in Internet applicationR control
- Basic identity enforcement in the internal network
- Easy configuration (requires AD administrator credentials). For organizations that prefer not to allow administrator users to be used as service accounts on third party devices there is an option to configure AD Query without AD administrator privileges, see sk43874.
- Preferred for desktop users
- Only detects AD users and computers
Endpoint Identity Agent
A lightweight Endpoint Identity Agent authenticates users securely with Single Sign-On (SSO).
- Identity enforcement for Data Centers
- Protecting highly sensitive servers
- When accuracy in detecting identity is crucial
- See Choosing Identity Sources.
Terminal Servers Endpoint Identity Agent
Identifies multiple users who connect from one IP address. A terminal Server Endpoint Identity Agent is installed on the application server, which hosts the terminal/Citrix services.
- Identify users who use Terminal Servers or a Citrix environment.
- See Choosing Identity Sources.
Browser-Based Authentication — Transparent Kerberos Authentication
The Transparent Kerberos Authentication Single-Sign On (SSO) solution transparently authenticates users already logged into AD. This means that a user authenticates to the domain one time and has access to all authorized network resources without having to enter credentials again. If Transparent Kerberos Authentication fails, the user is redirected to the Captive Portal for manual authentication.
Note —The Endpoint Identity Agent download link and the keep Alive option are ignored when Transparent Kerberos Authentication SSO is successful. This is so because the user does not see the Captive Portal.
- In AD environments, when known users are already logged in to the domain.
- Used for identity enforcement only (not intended for logging purposes)
- Transparent Kerberos Authentication does not use Endpoint Identity Agents or the Keep Alive feature.
Users who get access using IPsec VPN Office Mode can authenticate seamlessly.
- Identify and apply identity-based security Policy on users that access the organization through VPN.
- See Choosing Identity Sources.
AD Query
AD Query is an easy to deploy, clientless identity acquisition method. It is based on Active Directory integration and it is completely transparent to the user.
The AD Query option operates when:
- An identified asset (user or computer) tries to access an Intranet resource that creates an authentication request. For example, when a user logs in, unlocks a screen, shares a network drive, reads emails through Exchange, or accesses an Intranet portal.
- AD Query is selected as a way to acquire identities.
The technology is based on querying the Active Directory Security Event Logs and extracting the user and computer mapping to the network address from them. It is based on Windows Management Instrumentation (WMI), a standard Microsoft protocol. The Security Gateway communicates directly with the Active Directory domain controllers and does not require a separate server.
No installation is necessary on the clients or on the Active Directory server.
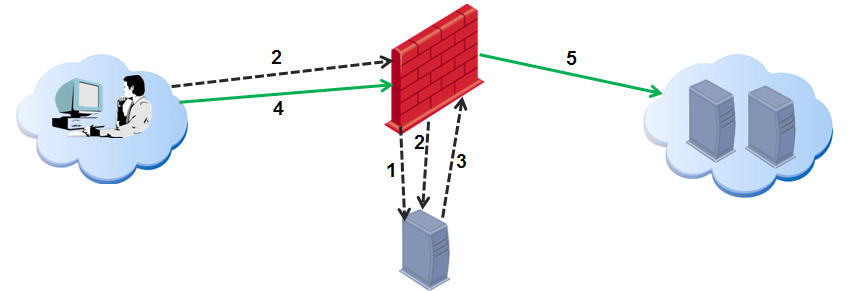
How AD Query Works- Firewall Rule Base
Active Directory domain controller
The Security Gateway is configured to receive security event logs from the Active Directory domain controllers.
A user logs in to a computer with Active Directory credentials.
The Active Directory domain controller sends the security event log to the Security Gateway. The Security Gateway gets the user and IP information (user name@domain, computer name and source IP address).
The user opens a connection to the Internet.
The Security Gateway confirms the user identification and lets him access the Internet based on the policy.
Browser-Based Authentication
Browser-Based Authentication gets identities and authenticates users with one of these acquisition methods:
- Captive Portal
- Transparent Kerberos Authentication
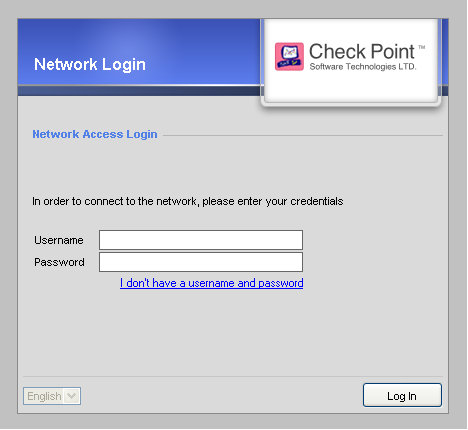
Captive Portal is a simple method that authenticates users with a web interface. When users try to access a protected resource, they enter authentication information in a form that shows in their browser.
Transparent Kerberos Authentication authenticates users by getting authentication data from the browser without any user input. If authentication is successful, the user goes directly to the specified destination. If authentication fails, the user must enter credentials in the Captive Portal.
The Captive Portal shows when a user tries to access a web resource and all of these conditions apply:
- Captive Portal is enabled.
- The redirect option enabled for the applicable rule.
- Firewall or Application and URL Filtering rules block access by unidentified users to resources that would be allowed if they were identified.
The Captive Portal also shows when Transparent Kerberos Authentication is enabled, but authentication fails.
From the Captive Portal, users can:
- Enter their user name and password.
- Enter guest user credentials (Configured in the Portal Settings).
- Click a link to download an Identity Awareness agent (Configured in the Portal Settings).
How Captive Portal Works- Firewall Rule
Security Gateway with Identity Awareness
Active Directory domain controller
A user wants to access the Internal Data Center.
Identity Awareness does not recognize him and redirects the browser to the Captive Portal.
The user enters regular office credentials.
The credentials can be AD or other Check Point supported authentication methods, such as LDAP, Check Point internal credentials, or RADIUS.
The credentials go to the Security Gateway, which finds them in the AD server.
The user can access the requested URL.
How Transparent Kerberos Authentication Works
- A user wants to access the Internal Data Center.
- Identity Awareness does not recognize the user and redirects the browser to the Transparent Authentication page.
- The Transparent Authentication page asks the browser to authenticate itself.
- The browser gets a Kerberos ticket from Active Directory and presents it to the Transparent Authentication page.
- The Transparent Authentication page sends the ticket to the Security Gateway which authenticates the user and redirects it to the originally requested URL.
- If Kerberos authentication fails for some reason, Identity Awareness redirects the browser to the Captive Portal.
Identity Agents
There are two types of Identity Agents:
- Endpoint Identity Agents — dedicated client agents installed on users’ computers that acquire and report identities to the Security Gateway.
- Terminal Servers Endpoint Identity Agent — an Endpoint Identity Agent installed on an application server that hosts Citrix/Terminal services. It identifies individual users whose source is the same IP address.
Using Endpoint Identity Agents gives you:
- User and computer identity
- Minimal user intervention— All necessary configuration steps are done by administrators and does not require user input.
- Seamless connectivity — Transparent authentication using Kerberos Single Sign-On (SSO) when users are logged in to the domain. If you do not want to use SSO, users enter their credentials manually. You can let them save these credentials.
- Connectivity through roaming— Users stay automatically identified when they move between networks, as the client detects the movement and reconnects.
- Added security — You can use the patented packet tagging technology to prevent IP Spoofing. Endpoint Identity Agents also gives you strong (Kerberos based) user and computer authentication.
These are the types of Endpoint Identity Agents you can install:
- Full – Predefined Endpoint Identity Agent includes packet tagging and computer authentication. It applies to all users of the computer that it is installed on. Administrator permissions are required to use the Full Endpoint Identity Agent type.
- Light – Predefined Endpoint Identity Agent that does not include packet tagging and computer authentication. You can install this Endpoint Identity Agent individually for each user on the target computer. Administrator permissions are not required.
- Terminal Servers — Predefined Endpoint Identity Agent that installs MAD services and the Multi-user host driver on Citrix and Terminal Servers. This Endpoint Identity Agent type cannot be used for endpoint computers.
- Custom — Configure custom features for all computers that use this agent, such as MAD services and packet tagging.
Users can download and install Endpoint Identity Agents from the Captive Portal or you can distribute MSI/DMG files to computers with distribution software or any other method (such as telling them where to download the client from).
Downloading Endpoint Identity Agent
This shows how a user downloads the Endpoint Identity Agent from the Captive Portal:
Источник