- Anders.com: Thoughts and commentary on Technology.
- Advertisment
- 1. Open Network Prefrences
- 2. Creating a New VPN Connection
- 3. Set Your Server Address and Account Name
- 4. Find Your PCF File
- 5. Get Your Encrypted Group Password
- 6. Decrypt Your Group Password
- Fancy Schmancy Decoder Ring
- 7. Enter your Shared Secret and Group Name
- 8. Create a New VPN Connection
- 9. Try Starting your VPN
- 10. Bask in the Warm Glow of a Native VPN Connection
- 11. Visit our Sponsor if their Offer Interests You
- The «Other Way Around»
- Troubleshooting
- Disconnects
- Routing Everything Through the VPN
- VPN Clients For Mac OS X FAQ
- Available Languages
- Contents
- Introduction
- General Questions
- Q. What options do I have in order to provide remote access to Mac users?
- Q. How do I uninstall Cisco VPN Client on Mac OS X?
- Q. What are the feature differences between the Cisco Remote Access VPN Client and AnyConnect VPN Client?
- IPsec VPN Questions
- Q. If I want to use IPsec, should I use the built-in Mac VPN Client or the Cisco Remote Access VPN Client?
- Q. How do I configure the Mac built-in VPN Client?
- Q. I tried to use the built-in Mac Client on Lion, but I receive a phase 2 mismatch. What should I do?
- Q. Are there any compatibility issues with the Cisco Remote Access VPN Client?
- Q. Where can I download the Cisco Remote Access VPN Client?
- Q. I tried to use Cisco VPN Client, but received Error 51. What should I do?
- Q. Does the built-in Mac VPN Client support ESP-NULL transforms?
Anders.com: Thoughts and commentary on Technology.
Confirmed working on OS X High Sierra
The proprietary CiscoVPN Mac client is somewhat buggy. It is possible to use the IPSec VPN software included with Mac OS X instead. This tutorial shows you how to migrate from CiscoVPN to the native OS X IPSec VPN by decrypting passwords saved in CiscoVPN PCF files.
Advertisment
Please visit these guys if their offer interests you — they make this site possible.
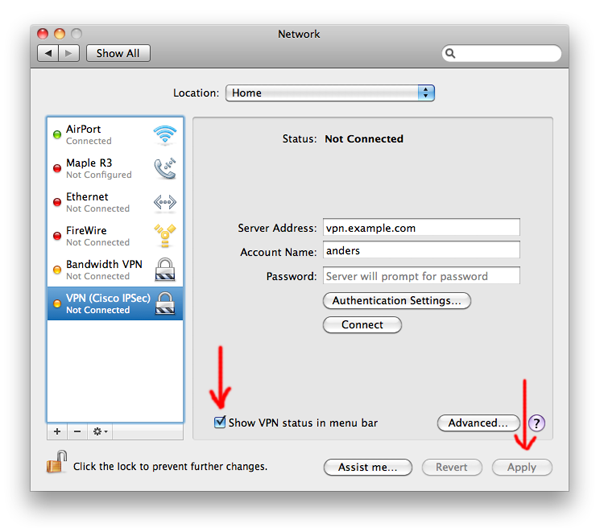
1. Open Network Prefrences
Open up your System Prefrences and select «Network». Click on the little + button at the bottom of the window to create a new connection.
2. Creating a New VPN Connection
Pick «VPN» for the Interface and set its type to «Cisco IPSec». It doesn’t matter what you set as the service name.
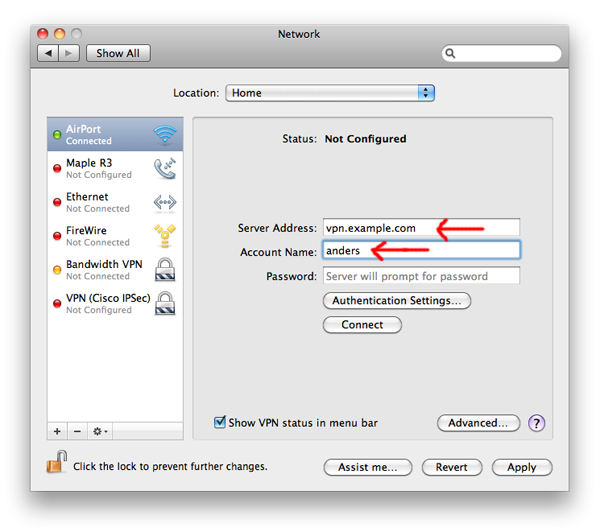
3. Set Your Server Address and Account Name
Copy the «Host» setting from CiscoVPN.
to the «Server Address» setting in your System Prefrences» and enter your username under «Account Name». You probably don’t want to enter your password unless you are OK with the system saving it.
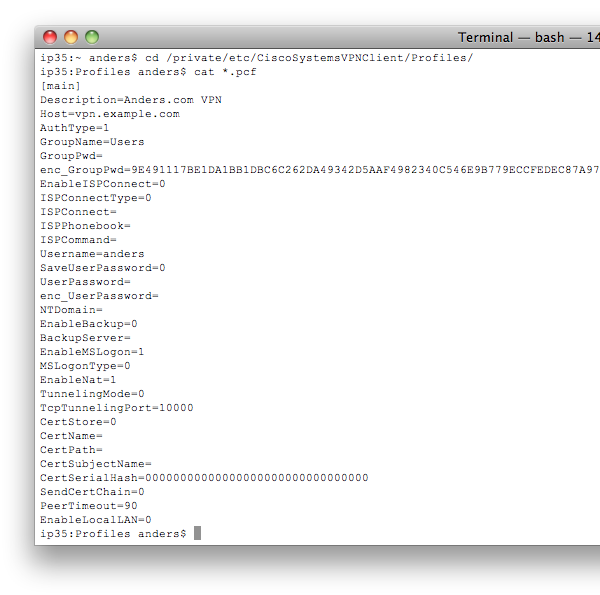
4. Find Your PCF File
On Mac OS X, PCF files are usually found in /private/etc/CiscoSystemsVPNClient/Profiles. Open up /Applications/Terminal and type the following:
You should get something like this:
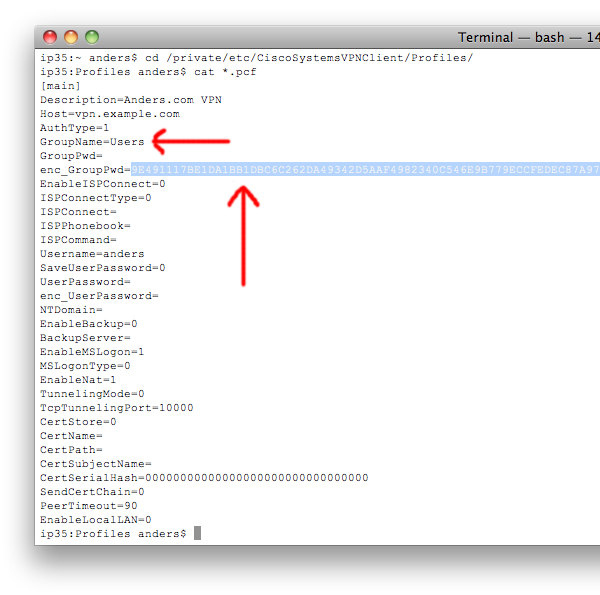
5. Get Your Encrypted Group Password
Find that long list of letters and numbers after enc_GroupPwd= and copy it. Also make note of the GroupName — you’ll need that in a bit as well.
6. Decrypt Your Group Password
Paste that sequence of characters into the fancy schmancy decoder ring below and click «Decode». (pops up a new window)
Fancy Schmancy Decoder Ring
As an example, this should return «letmein» as the password:
Thanks to HAL-9000 at evilscientists.de and Massar’s work on cisco-decrypt.c for the magic here. A JavaScript implementation also exists here: https://github.com/artemkin/cisco-password-decoder.
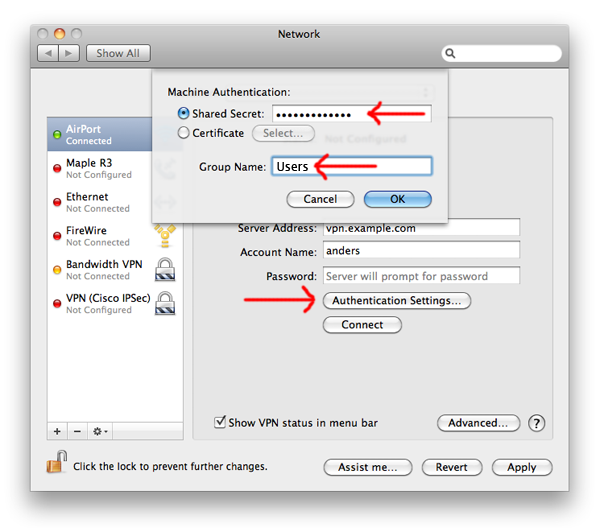
7. Enter your Shared Secret and Group Name
Click «Authentication Settings» back in the Network Prefrences screen. Enter the resulting decoded password into the «Shared Secret» section of the new VPN connection and set the GroupName from above as well.
8. Create a New VPN Connection
Click «OK», make sure «Show VPN status in menu bar» is checked and click «Apply».
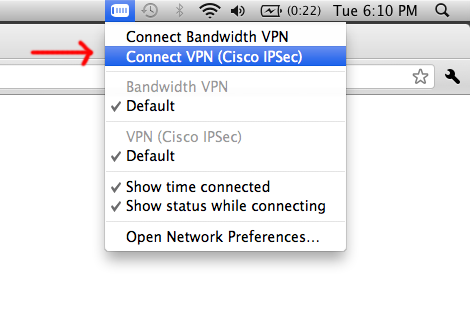
9. Try Starting your VPN
At the top of your screen you should have a little VPN icon. Try connecting to your new VPN.
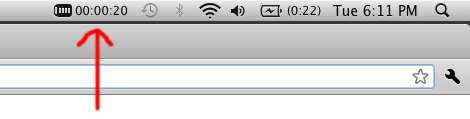
10. Bask in the Warm Glow of a Native VPN Connection
If everything goes as planned, you should see your connection time counting up at the top of your screen.
11. Visit our Sponsor if their Offer Interests You
The «Other Way Around»
How to get your VPN settings out of the built-in mac VPN client.
You don’t need the Fancy Schmancy Decoder Ring to get your settings back out of the built-in Mac VPN client. Just head over to the Keychain Access application (under Applications -> Utilities) and search for «VPN». Double-click your IPSec Shared Secret to open up the window. Clicking «Show Password» will reveal the secret sauce after you authenticate.
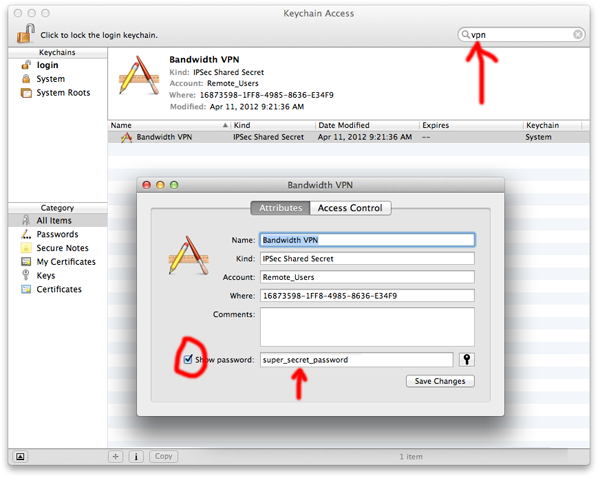
Troubleshooting
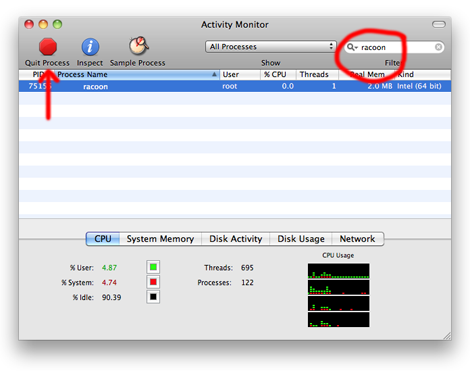
If things seem to get hung-up and you are unable to reconnect your VPN without a reboot, Rick R mentions that you might try killing the «racoon» process.
Racoon is an IPsec key management daemon and is part of the KAME IPsec tools. Kill it by running «Activity Monitor» in the «Utilities» folder, finding it in the process list and clicking «Quit Process» at the upper left of the Activity Monitor window.
Look in your system.log by running the Console app for hints at what might be going wrong. Here’s the system.log from a working VPN setup / take down.
Disconnects
Dave Ma‘s VPN would disconnect after 45 minutes of uptime. Fotos Georgiadis on an Apple forum thread suggested changing the IPSec proposal lifetime within racoon to 24 hours instead of 3600 seconds. (3600 seconds is 1 hour — who knows why people are seeing drops at 45 minutes) Here’s how that is done.
Connect to the VPN (so OSX dynamically generates a racoon configuration file)
Open Terminal on Mac (Applications —> Utilities—> Terminal)
Copy the generated configuration file to /etc/racoon:
sudo cp /var/run/racoon/XXXXXX.conf /etc/racoon
**where: XXXXXX is the name or ip address of your VPN server**
Edit the racoon configuration file with your favorite editor (pico):
sudo pico /etc/racoon/racoon.conf
At the bottom of the racoon.conf file, comment out the line:
(by added the «#» to the beginning of the line)
And instead include the copied file (which we will edit):
(don’t forget to replace XXXXXX with the actual name of your file)
Edit the generated configuration file with your favorite editor (pico):
sudo pico /etc/racoon/XXXXXX.conf
Disable dead peer detection:
Change proposal check to claim from obey:
Change the proposed lifetime in each proposal (24 hours instead of 3600 seconds):
lifetime time 24 hours;
*note: make sure you change all the «proposed lifetime» sections and not just one.
Disconnect and reconnect (this time racoon will use your custom configuration).
Now try using your VPN for more than 45 minutes and it shouldn’t drop.
Routing Everything Through the VPN
So does all your traffic flow through the VPN when you are connected or just traffic to the protected networks? Cisco VPN servers normally send out a list of routes to private networks so you don’t end up sending all of your traffic through the VPN server. The reasoning behind this is why protect it if the traffic is destined for an insecure network anyway? The native OS X Cisco VPN adds these routes automatically and removes them when you disconnect. That’s one of the things that differentiates the Cisco VPN client from the standard IPSec client. Let’s take a look at what gateway is used when sending traffic to apple.com from within the Terminal application:
Notice the «gateway» line there? Traffic to apple.com is going out 192.168.1.1 which is my normal Internet gateway so it is skipping the VPN entirely.
Let’s try an IP on a protected private network: (10.1.2.3)
In this case, the gateway is 172.131.25.12 which is a fake IP on the far end of the VPN which will eventually route traffic to 10.1.2.3. So when sending data to 10.1.2.3, I am going through the VPN and that traffic is encrypted.
So how does it know what gateway to use for different IPs? Let’s take a look at the routing table:
I’ve lopped off a bunch of irrelevant lines but as you can see we have two «default» routes. If a destination isn’t explicitly matched below, the traffic will flow through the first default route from the top. So in this case, if the destination isn’t within 10.1/16 (which means 10.1.*.*) we will go through our default route of 192.168.1.1. If it is, we would go through 172.131.25.12 which is our VPN.
But what if you just wanted to send everything through your VPN connection? We could just delete the first default route and let everything go over the VPN, but this is presumably dangerous because the encrypted traffic probably uses the default route to get to the VPN server in the first place. Let’s see:
Yep, it does. So if we are going to remove the default route to 192.168.1.1, we have to make sure we have an explicit route below to the VPN server. (1.2.3.4) You will notice above that my Cisco VPN server adds this route automatically, but if yours isn’t configured that way you can add it like this:
It is safe to try this if you already have the route because the command will just fail.
The next thing we are going to do is a little dangerous and remove all your network access. A reboot should be your weapon of last resort to get your networking back but you might also want to print these instructions out so you have them. You have been warned!
Now let’s do the dangerous bit and rip the first default route away:
Now let’s check to see if we can still get to our VPN server:
Now let’s look at the wider Internet by seeing how we get to apple.com: (17.172.224.47 — we aren’t using apple.com here because we don’t want to depend on DNS working)
Whoops, something is wrong! That’s because that first route there is a little deceptive. It isn’t a route to the IP of the gateway, just a route to the VPN tunnel device utun0. We’ll need to say what IP to go to. Let’s add a default route to the VPN’s fakenet gateway address: (which we already have as the gateway in most other routes)
OK, let’s see which way packets go to get to apple.com: (17.172.224.47)
Yep, looks like the right way.
Now let’s try pinging google.com: (apple.com doesn’t respond to pings)
Looks like it works. If it doesn’t work, your VPN server likely doesn’t allow general Internet access through VPN connections. If this is the case, you are out of luck. Hopefully you know someone influential in the IT department that can change this for you.
Because we removed the normal default route, when we shut down our VPN we’ll be stuck without a default route. To add that back in after the VPN goes down, do this:
And we should be back to normal.
Ideally we do these things automatically when the VPN comes up. The easiest way to do this is to have your VPN administrator set that up as a policy for you. Alternatively, you can create scripts that run on VPN startup. Create /etc/ppp/ip-up and add whatever lines you came up with above to that and mark that file as executable with:
Similarly, /etc/ppp/ip-down will be run on VPN shutdown. Reverse your commands in that file and you should have a completely automated setup.
Источник
VPN Clients For Mac OS X FAQ
Available Languages
Contents
Introduction
This document answers frequently asked questions about Cisco’s VPN Client solutions available on Mac OS X.
Tip: Cisco recommends that you migrate to the AnyConnect VPN Client for both Secure Sockets Layer (SSL) as well as IPsec. The built-in IPsec client on Mac OS is an Apple product, so any questions/upgrades/bug fixes and other issues on the client side need to be addressed by Apple while the Cisco Remote Access VPN client is EOS. Therefore, no fixes will be put in for this client.
General Questions
Q. What options do I have in order to provide remote access to Mac users?
There are three VPN Client solutions that can be implemented, dependent upon the Mac OS Version.
| VPN Client | Technology/Protocol | Mac OS X 10.10 Yosemite | Mac OS X 10.11 El Capitan | |||||
| Mac Built-in VPN Client | IPsec | X | X | X | X | X | X | |
| Cisco Remote Access IPsec Client | IPsec | X | X | |||||
| Cisco AnyConnect Secure Mobility Client | SSL, IKEv2/IPsec | X* | X | X** | X*** | X | X | X**** |
*Mac OS X 10.5 (Leopard) is no longer supported in AnyConnect Release 3.1. Also, PowerPC support was dropped in Release 3.0 and later.
**Mac OS X 10.7 (Lion) is supported in AnyConnect Releases 2.5.3051 and 3.0.3054 and later.
***Mac OS X 10.8 (Mountain Lion) is supported in AnyConnect Releases 3.0.08057 and 3.1 and later.
****MAC OS X 10.11 (El Capitan) is supported in Anyconnect 4.1.04011 and later. El Capitan support will not be provided in AnyConnect 3.x as new OS support ended in July 2015. Refer to End-of-Sale and End-of-Life Announcement for the Cisco AnyConnect Secure Mobility Client Version 3.x.
Q. How do I uninstall Cisco VPN Client on Mac OS X?
In order to uninstall the Cisco VPN Client, complete these steps:
- Enter these commands in order to clean out the old Cisco VPN kernel extension and reboot the system.
- If you installed the Cisco VPN for Mac version 4.9.01.0180 package, enter these commands in order to delete the misplaced files. The deletion of these files will not affect your system, since applications do not use these misplaced files in their current location.
- Enter these commands if you no longer need the old Cisco VPN Client or Shimo.
Q. What are the feature differences between the Cisco Remote Access VPN Client and AnyConnect VPN Client?
This is beyond the scope of this document, but fundamentally SSL VPN has more features than the Cisco Remote Access Software VPN Client as it is a newer technology and new features are rolled into each new release of AnyConnect. The latest AnyConnect Mobility Client, Version 3.0, includes the same feature-rich support for both SSL VPN and IKEv2.
IPsec VPN Questions
Q. If I want to use IPsec, should I use the built-in Mac VPN Client or the Cisco Remote Access VPN Client?
A. Although it is possible to use either VPN Client, the advantages of each are explained here.
Note: Cisco recommends that you use AnyConnect, which allows you to take advantage of Next Generation Encryption (NGE) ciphers and advancements in the IKEv2 protocol.
Mac VPN Client
- + The Apple built-in client ensures support as the Mac OS evolves.
- + The client is integrated into Mac OS X 10.6 and later.
- + Faster to configure as it does not require installation of another application.
- — Not built into Mac OS X 10.5.
Cisco Remote Access VPN Client
- + Supported in Mac OS X 10.5 and 10.6.
- — Requires installation of another software application on your Mac.
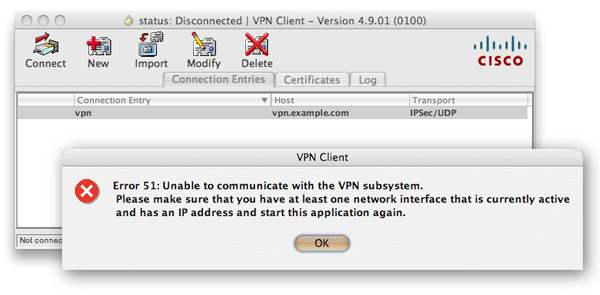
- — In early 2011 Mac began to ship Mac OS X 10.6 with a 64-bit kernel. This is not supported by the Cisco Remote Access VPN Client and results in Error 51 after install. Refer to Cisco IPsec VPN Client on MAC OS X generates the error «Error 51: Unable to communicate with the VPN subsystem».
Q. How do I configure the Mac built-in VPN Client?
In Mac OS X 10.6 and later:
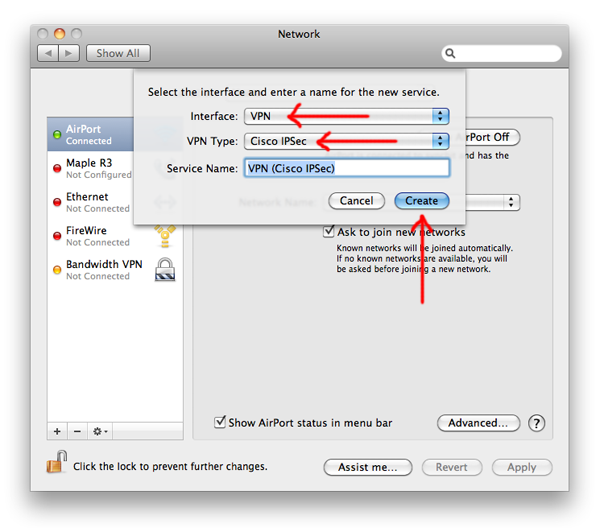
- Choose System Preferences > Network.
- Click the lock button in order to unlock it and make changes.
- Click the plus sign
above the unlocked lock button in order to add an interface.
- From the Interface drop-down list, choose VPN.
- From the VPN Type drop-down list, choose Cisco IPSec.
- In the Service Name text box, type an easy to remember interface name such as ‘Corp IPsec VPN’.
- Click OK and then select this new interface.
- Click the new VPN interface in order to configure the interface.
- Server Address-VPN headend’s outside interface IP address (WAN/publicly routable IP address)
- Account Name-Username
- Account Password-User’s password
- Click Authentication Settings.
- Under Machine Authentication, click the radio button for your respective authentication mechanism (pre-shared-key or certificate authentication).
- If a pre-shared key that matches the pre-shared-key defined on the VPN headend is used, type the key into the Shared Secret dialog box.
- Enter the Group Name that matches the one defined in the EZVPN configuration on the VPN headend device (ASA ‘tunnel-group’, IOS ‘crypto ipsec client ezvpn group’).
Q. I tried to use the built-in Mac Client on Lion, but I receive a phase 2 mismatch. What should I do?
If your Microsoft Windows clients work or your older Macs that use the Cisco Remote Access VPN Clients work, and only the Lion machines do not seem to be able to connect, then it is likely a phase 2 mismatch issue. You see this error message if you enable ‘debug crypto ipsec’ on the ASA. This essentially means the transform sets used probably do not support the encryption used by the Mac built-in client. For Lion, the client uses 3DES or AES. It does not support DES. In order to work around this issue, either switch the transform set to use 3DES completely or add multiple transform sets as shown here:
This issue is usually caused by running an ASA software release earlier than Release 8.4. The later ASA software comes with all transforms sets defined by default, so additional configuration is not required to make it work.
Q. Are there any compatibility issues with the Cisco Remote Access VPN Client?
Refer to the Software Release Notes first for compatibility guidelines. Note the Error 51 compatibility issue between the Cisco Remote Access VPN Client and 64-bit Mac kernel mentioned later in this document.
Q. Where can I download the Cisco Remote Access VPN Client?
- Open the Cisco Support Page.
- Click Download Software.
- Choose Products > Security > Virtual Private Networks (VPN) > Cisco VPN Clients > Cisco VPN Client.
- Choose Cisco VPN Client v4.x.
- Choose Mac OS.
Note: The VPN Client v5.x was only released for Windows PCs. The latest Mac release is v4.9.
Q. I tried to use Cisco VPN Client, but received Error 51. What should I do?
Q. Does the built-in Mac VPN Client support ESP-NULL transforms?
No, the built-in client does not support this transform set.
Источник

 above the unlocked lock button in order to add an interface.
above the unlocked lock button in order to add an interface.


