- Install OpenSSH
- Install OpenSSH using Windows Settings
- Install OpenSSH using PowerShell
- Start and configure SSH Server
- Connect to SSH Server
- Uninstall OpenSSH using Windows Settings
- Uninstall OpenSSH using PowerShell
- Configure SSH Server With Windows 10 Native Way
- Installing and configuring OpenSSH Server
- Apply asymmetric key authentication
- Using $HOME\.ssh\authorized_keys
- Using administrators_authorized_keys
- Setting File Permissions with Authentication Key Information
- Changing the SSH Default Shell
- Staring SSH Server
- How to Secure Remote Desktops
- Set your desired password
- Generate a new password every time
- Try logging in to Remote Desktop with Tunneling
- Using secure file sending and receiving
- Wrap-up
- Credits
- Secure Shell (SSH)
- Using the Windows 10 OpenSSH client
- Using PuTTY
- Download an SSH client
- Connect to your device
- Update account password
- Configure your Windows IoT Core device
- Commonly used utilities
Install OpenSSH
Applies to Windows Server 2019, Windows 10
OpenSSH is a connectivity tool for remote login that uses the SSH protocol. It encrypts all traffic between client and server to eliminate eavesdropping, connection hijacking, and other attacks.
OpenSSH can be used to connect Window 10 clients to Windows Server 2019. OpenSSH Client is available to install on Windows 10 build 1809 and later, while OpenSSH Server is available to install on Windows Server 2019 and later.
If you downloaded OpenSSH from the GitHub repo at PowerShell/openssh-portable, follow the instructions listed there, not the ones in this article.
Install OpenSSH using Windows Settings
Both OpenSSH components can be installed using Windows Settings. OpenSSH Server is installed on Windows Server and OpenSSH Client is installed on Windows 10 devices.
To install the OpenSSH components:
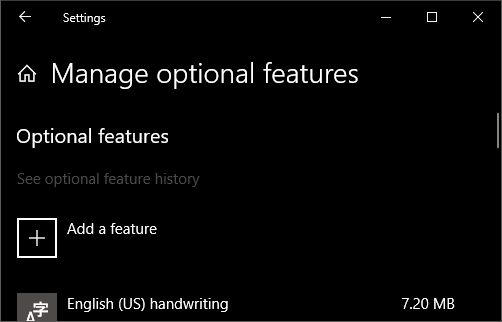
Open Settings, select Apps > Apps & Features, then select Optional Features.
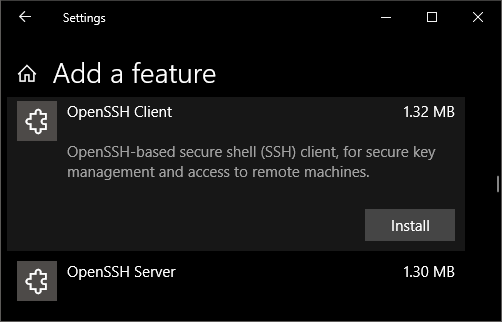
Scan the list to see if the OpenSSH is already installed. If not, at the top of the page, select Add a feature, then:
- On Windows 10, find OpenSSH Client, then click Install
- On Windows Server 2019, find OpenSSH Server, then click Install
Once setup completes, return to Apps > Apps & Features and Optional Features and you should see OpenSSH listed.
Installing OpenSSH Server will create and enable a firewall rule named OpenSSH-Server-In-TCP . This allows inbound SSH traffic on port 22. If this rule is not enabled and this port is not open, connections will be refused or reset.
Install OpenSSH using PowerShell
To install OpenSSH using PowerShell, run PowerShell as an Administrator. To make sure that OpenSSH is available, run the following cmdlet:
This should return the following output:
Then, install the server or client components as needed:
Both of these should return the following output:
Start and configure SSH Server
To start and configure OpenSSH server for initial use, open PowerShell as an administrator, then run the following commands to start the SSHD service :
Connect to SSH Server
Once installed, you can connect to OpenSSH Server from a Windows 10 device with the SSH client installed using PowerShell as follows. Be sure to run PowerShell as an administrator:
Once connected, you get a message similar to the following:
Selecting yes adds that server to the list of known ssh hosts on your Windows client.
You are prompted for the password at this point. As a security precaution, your password will not be displayed as you type.
Once connected, you will see the Windows command shell prompt:
Uninstall OpenSSH using Windows Settings
To uninstall OpenSSH using Windows Settings:
- Open Settings, then go to Apps > Apps & Features.
- Go to Optional Features.
- In the list, select OpenSSH Client or OpenSSH Server.
- Select Uninstall.
Uninstall OpenSSH using PowerShell
To uninstall the OpenSSH components using PowerShell, use the following commands:
You may need to restart Windows afterwards if the service was in use at the time it was uninstalled.
Configure SSH Server With Windows 10 Native Way
C ontinuing from the last post, we’ll look at how to set up a built-in SSH server starting with Windows 10 and Windows Server 1709. This method allows Windows Server to connect remotely using SSH, just like a traditional Linux server. We will also look at how you can use Remote Desktop securely without modifying your firewall settings using SSH port tunneling.
Installing and configuring OpenSSH Server
You can install OpenSSH Server the same way you installed the SSH client in the previous article.
After installing the OpenSSH server program, start and stop the NT service once to create the necessary initial configuration files.
Apply asymmetric key authentication
Using public SSH Key authentication methods and disable the password authentication method highly recommended because it prevents attacks through password assignment. To enable this authentication feature, start PowerShell as an administrator and open the file in the path below with notepad. (Or you can use another text editor of your choice.)
For the following items, uncomment below lines and apply the value as follows:
- PubkeyAuthentication yes
- PasswordAuthentication no
- PermitEmptyPasswords no
Then choose your preferred method of managing SSH public keys. Starting with Windows Server 2019 (or 1809), there are two ways to describe SSH public keys. One of which is the traditional way of creating an authorized_keys file in the user’s home directory.
Using $HOME\.ssh\authorized_keys
To use this method, comment out the following block of code at the bottom of the configuration file:
Then go to the user home directory you want to log in to and create a .ssh directory.
Create an authorized_keys file (without the extension) inside the newly created directory and open it with your favorite text editor.
Add the public SSH key value you are using here.
When you save the file, you must change the file permission settings as described in the section Setting File Permissions with Authentication Key Information. If this setting is missing, the SSH connection will fail.
Using administrators_authorized_keys
This property is the default used by OpenSSH included in Windows Server 2019 (1809). Instead of registering a new SSH key for each user, you can manage your files in one place.
If you use this method, all public keys need to store in the $env: PROGRAMDATA\ssh\administrators_authorized_keys file, except for non-administrative users (that is, users who do not belong to the Administrators group). If you try, this setting will be used instead of your home directory, so if there is no key here, the connection will fail.
The administrators_authorized_keys file does not exist by default and created.
Warning: Run below commands carefully. If you change the other system file or configuration mistakenly, the system can break.
Add the public SSH Key you are using here.
When you save the file, you must change the file permission settings as described in the section Setting File Permissions with Authentication Key Information. If this setting is missing, the SSH connection will fail.
Setting File Permissions with Authentication Key Information
A common and very tough problem that you will face about using the OpenSSH server for Windows is this. SSH Key file permission should have correct and limited file permission. Windows version of SSH also follows this rule, but especially in Windows, configuring file permission can be unintuitive.
Depending on the method you chose in the previous step, you must verify the path of the authorized_keys file or administrators_authorized_keys file and change the permissions so that only the system account can access it using the icacls.exe utility and the Get-Acl and Set-Acl commands.
Warning: Run below commands carefully. If you change the system file’s ACL configuration mistakenly, the system can break.
Changing the SSH Default Shell
Basically, for compatibility reasons, the Windows operating system has provided a shell-based interpreter that recognizes DOS commands for a long time. But now, with more and more features than working with DOS commands, PowerShell is becoming a good alternative.
If necessary, you can specify that PowerShell as the default shell for SSH instead of the DOS interpreter. However, the settings here are specific to SSH sessions, not for the Remote Desktop or console session.
Warning: Run below commands carefully. If you change the registry configuration mistakenly, the system can break.
Staring SSH Server
You are now ready to start your SSH server. The SSH server is set to manual run by default so that you can change the startup mode to automatic. Then begins the service.
Congratulations! From now, you can connect to Windows with SSH-key authentication.
How to Secure Remote Desktops
Unlike Linux, Windows still runs much of the system on a graphical interface rather than on the command line. So if you try to do something with a terminal like this, you may not have much to do as you might expect.
Remote Desktop, however, is a well-known food for many hackers and script kiddies, as is well known. You may encounter the dilemma of choosing between convenience and security.
Fortunately, SSH provides the concept of tunneling, supporting the ability to relay other network connections securely. Remote desktop connections can also be protected in this way so that you can use them with confidence.
Start by blocking the TCP 3389 and UDP 3389 ports. You can do this because you will use Remote Desktop only with SSH tunneling.
Warning: Run below commands carefully. If you change the firewall configuration mistakenly, the system can become vulnerable.
Next, you must change the registry flag value so that the remote desktop server can accept the connection.
Warning: Run below commands carefully. If you change the registry configuration mistakenly, the system can break.
And the part that I’m going to explain right now is cool. As you saw earlier, you will not be asked for your password when you connect to OpenSSH, so you can set up a randomly generated strong password each time you use it. It is handy to have a simple script in the system directory that can do this.
Choose the type of script you want to create a file called ChangePassword.ps1 . We will keep this script in the system directory for your convenience.
Warning: Run below commands carefully. If you change the other system file or configuration mistakenly, the system can break.
Set your desired password
Create the contents of the ChangePassword.ps1 file as follows:
This script allows you to enter your password. However, unless you change the policy, you can only use passwords that pass the Windows Server enhanced default password rules. You must specify a password that must meet all of the following conditions.
- English capital letters (A through Z)
- Lowercase English letters (a through z)
- Arabic numerals (0 to 9)
- Special symbols (e.g. $, #,%)
Generate a new password every time
Create the contents of the ChangePassword.ps1 file as follows:
This way, you can set a strong password every time. If you forget your password, you can rest assured that you can still use public key authentication as a secondary means of authentication.
Try logging in to Remote Desktop with Tunneling
Now enter the following command to run the above script. After that, just set the password and verify that the remote desktop connection is working.
Warning: Run below commands carefully. If you lost the password you specified, you’d be lost access to your system.
To log in to the remote desktop, run SSH as follows:
The first 3389 is the port number on the server-side, and the second address is the port number you want to use locally. If you have changed the remote desktop’s port number from the registry to another port number on the server, you can enter the changed port number instead of 3389.
If you try to connect to a remote desktop using only the part as before, the firewall will block the connection as previously set up. So no one can access the remote desktop directly unless the user has registered a public key that matches the SSH secret key with that server.
Using secure file sending and receiving
Not surprisingly, it is possible to use SSH based SFTP. This feature designed to securely handle large file transfers in place of the remote desktop’s folder sharing feature.
Any client that supports the SFTP feature, such as FileZilla, is compatible and has a management advantage, as there is no need to apply complex firewall open policies like traditional FTP.
Wrap-up
This walkthrough let you through all the new SSH features that added since Windows 10 Version 1709. Both articles are available for Windows 10 and Windows Server 2019, so please take a moment to set them up for even more security.
Credits
The following articles helped me as I wrote this article.
Secure Shell (SSH)
Secure Shell (SSH) allows you to remotely administer and configure your Windows IoT Core device
Using the Windows 10 OpenSSH client
The Windows OpenSSH client requires that your SSH client host OS is Windows 10 version 1803(17134). Also, the Windows 10 IoT Core device must be running RS5 Windows Insider Preview release 17723 or greater.
The OpenSSH Client was added to Windows 10 in 1803 (build 17134) as an optional feature. To install the client, you can search for Manage Optional Features in Windows 10 settings. If the OpenSSH Client is not listed in the list of installed features, then choose Add a feature.
Next select OpenSSH Client in the list and click Install.
To login with a username and password use the following command:
Where host is either the IP address of the Windows IoT Core device or the device name.
The first time you connect you see a message like the following:
Type yes and press enter.
If you need to login as DefaultAccount rather than as administrator, you will need to generate a key and use the key to login. From the desktop that you intend to connect to your IoT Device from, open a PowerShell window and change to your personal data folder (e.g cd
Register the key with ssh-agent (optional, for single sign-on experience). Note that ssh-add must be performed from a folder that is ACL’d to you as the signed-in user (Builtin\Administrators and the NT_AUTHORITY\System user are also ok). By default cd
from PowerShell should be sufficient as shown below.
If you receive a message that the ssh-agent service is disabled you can enable it with sc.exe config ssh-agent start=auto
To enable single sign, append the public key to the Windows IoT Core device authorized_keys file. Or if you only have one key you copy the public key file to the remote authorized_keys file.
If the key is not registered with ssh-agent, it must be specified on the command line to login:
If the private key is registered with ssh-agent, then you only need to specify DefaultAccount@host:
The first time you connect you see a message like the following:
Type yes and press enter.
You should now be connected as DefaultAccount
To use single sign-on with the administrator account, append your public key to c:\data\ProgramData\ssh\administrators_authorized_keys on the Windows IoT Core device.
You will also need to set the ACL for administrators_authorized_keys to match the ACL of ssh_host_dsa_key in the same directory.
To set the ACL using PowerShell
If you see a REMOTE HOST IDENTIFICATION CHANGED message after making changes to the Windows 10 IoT Core device, then edit C:\Users .ssh\known_hosts and remove the host that has changed.
Using PuTTY
Download an SSH client
In order to connect to your device using SSH, you’ll first need to download an SSH client, such as PuTTY.
Connect to your device
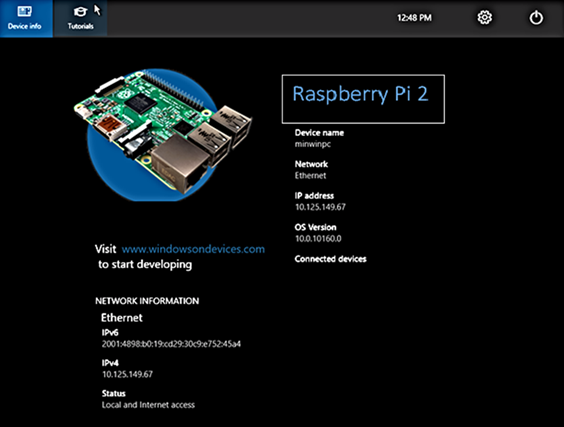
In order to connect to your device, you need to first get the IP address of the device. After booting your Windows IoT Core device, an IP address will be shown on the screen attached to the device:
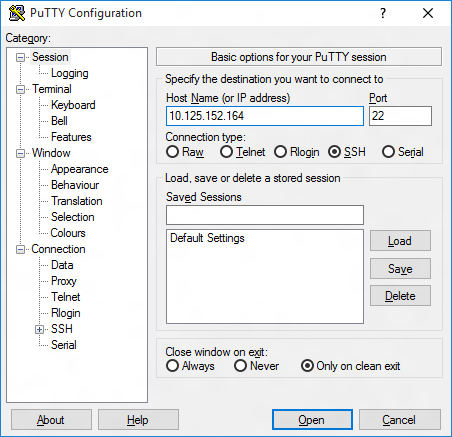
Now launch PuTTY and enter the IP address in the Host Name text box and make sure the SSH radio button is selected. Then click Open .
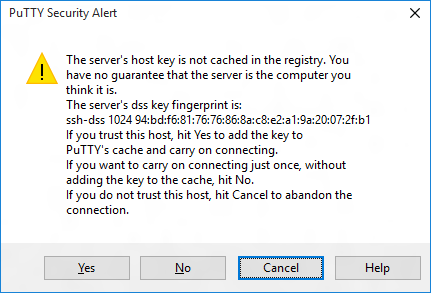
If you’re connecting to your device for the first time from your computer, you may see the following security alert. Just click Yes to continue.
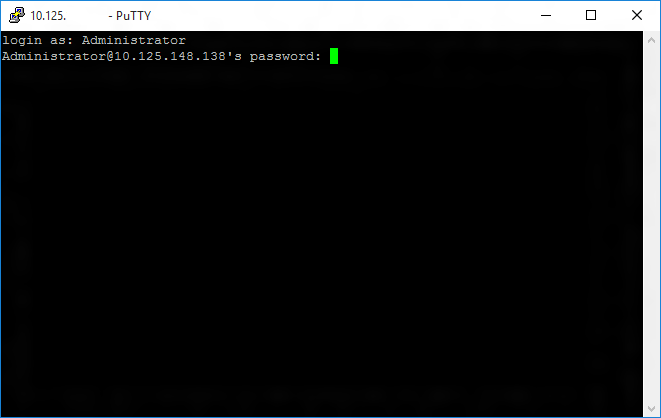
If the connection was successful, you should see login as: on the screen, prompting you to login.
Enter Administrator and press enter. Then enter the default password p@ssw0rd as the password and press enter.
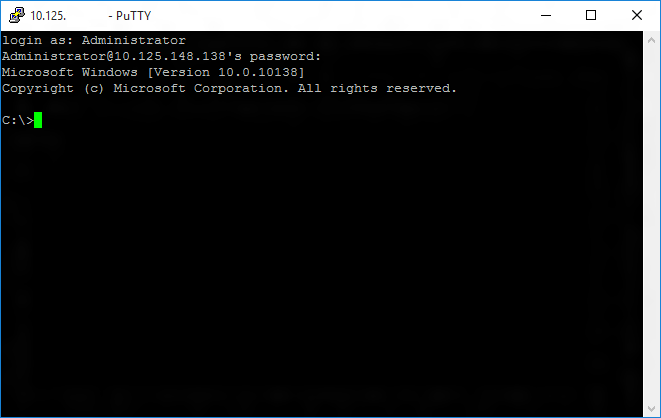
If you were able to login successfully, you should see something like this:
Update account password
It is highly recommended that you update the default password for the Administrator account.
To do this, enter the following command in the PuTTY console, replacing [new password] with a strong password:
Configure your Windows IoT Core device
To be able to deploy applications from Visual Studio 2017, you will need to make sure the Visual Studio Remote Debugger is running on your Windows IoT Core device. The remote debugger should launch automatically at machine boot time. To double check, use the tlist command to list all the running processes from PowerShell. There should be two instances of msvsmon.exe running on the device.
It is possible for the Visual Studio Remote Debugger to time out after long periods of inactivity. If Visual Studio cannot connect to your Windows IoT Core device, try rebooting the device.
If you want, you can also rename your device. To change the ‘computer name’, use the setcomputername utility:
You will need to reboot the device for the change to take effect. You can use the shutdown command as follows:
Commonly used utilities
See the Command Line Utils page for a list of commands and utilities you can use with SSH.