- Manually generating your SSH key in macOS
- About Terminal
- Generating an SSH key
- Importing your SSH key
- Troubleshooting
- What are my next steps?
- 🗝 Как сгенерировать ключи SSH в macOS Mojave
- Откройте приложение терминал
- Генерация ключей SSH
- Скопируйте свой ключ на сервер
- How do I get an SSH Public Key on Mac?
- Step 1 – Open Terminal
- Step 2 – Generate Your SSH Keys
- Step 3 – Save your Private Key, send your Public Key
- Generating a new SSH key and adding it to the ssh-agent
- Help us make these docs great!
Manually generating your SSH key in macOS
You generate an SSH key through macOS by using the Terminal application. Once you upload a valid public SSH key, the Triton Compute Service uses SmartLogin to copy the public key to any new SmartMachine you provision.
Joyent recommends RSA keys because the node-manta CLI programs work with RSA keys both locally and with the ssh agent. DSA keys will work only if the private key is on the same system as the CLI, and not password-protected.
About Terminal
Terminal is the terminal emulator which provides a text-based command line interface to the Unix shell of macOS.
To open the macOS Terminal, follow these steps:
- In Finder, choose Utilities from the Applications folder.
- Find Terminal in the Utilities listw.
- Open Terminal.
The Terminal window opens with the commandline prompt displaying the name of your machine and your username.
Generating an SSH key
An SSH key consists of a pair of files. One is the private key, which should never be shared with anyone. The other is the public key. The other file is a public key which allows you to log into the containers and VMs you provision. When you generate the keys, you will use ssh-keygen to store the keys in a safe location so you can bypass the login prompt when connecting to your instances.
To generate SSH keys in macOS, follow these steps:
Enter the following command in the Terminal window.
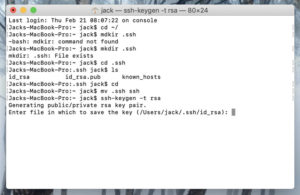
This starts the key generation process. When you execute this command, the ssh-keygen utility prompts you to indicate where to store the key.
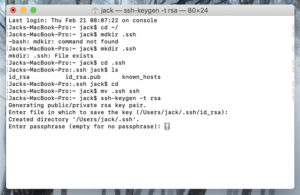
Press the ENTER key to accept the default location. The ssh-keygen utility prompts you for a passphrase.
You will need to enter the passphrase a second time to continue.
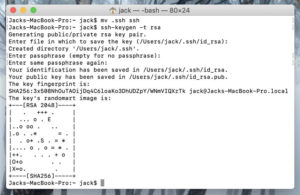
After you confirm the passphrase, the system generates the key pair.
Your private key is saved to the id_rsa file in the .ssh directory and is used to verify the public key you use belongs to the same Triton Compute Service account.
| Never share your private key with anyone! |
|---|
Your public key is saved to the id_rsa.pub ;file and is the key you upload to your Triton Compute Service account. You can save this key to the clipboard by running this:
Importing your SSH key
Now you must import the copied SSH key to the portal.
- After you copy the SSH key to the clipboard, return to your account page.
- Choose to Import Public Key and paste your SSH key into the Public Key field.
- In the Key Name field, provide a name for the key. Note: although providing a key name is optional, it is a best practice for ease of managing multiple SSH keys.
- Add the key. It will now appear in your table of keys under SSH.
Troubleshooting
You may see a password prompt like this:
This is because:
- You did not enter the correct passphrase.
- The private key on your Macintosh ( id_rsa ) does not match the public key stored with your Triton Compute Service account.
- The public key was not entered correctly in your Triton account.
What are my next steps?
In order to use the Terminal to create instances, set up triton and CloudAPI as well as the triton-docker commandline tool.
Источник
🗝 Как сгенерировать ключи SSH в macOS Mojave
macOS может работать с ключами SSH.
Мы покажет вам, как сгенерировать необходимые ключи и скопировать их на сервер.
Аутентификация по ключу SSH – это один из способов повысить безопасность удаленных сеансов между двумя компьютерами.
Этот тип аутентификации зависит от пары ключей, которые генерируются пользователем на клиентском компьютере.
В Linux эта задача невероятно проста.
С macOS процесс такой же простой.
Настолько легко, что с этим может справиться любой человек.
Я хочу провести вас через процесс генерации ключей SSH в macOS Mojave, а затем покажу вам, как скопировать ключ на удаленный сервер для более надежных соединений между двумя компьютерами.
Процесс должен занять у вас всего пару минут.
Откройте приложение терминал
Эта задача будет выполнена через терминальное приложение macOS.
Чтобы открыть это приложение, нажмите значок Launchpad на панели Dock и найдите терминал.
Когда появится это приложение, откройте его одним щелчком мыши.
Генерация ключей SSH
Из окна терминала введите следующую команду:
Примите каталог по умолчанию (рисунок A), используя клавишу Enter на клавиатуре.
Вам будет предложено ввести новую ключевую фразу для ключа (рисунок B).
Обязательно введите надежный и уникальный пароль для ключей.
После того как вы введете и подтвердите свой пароль, SSH сгенерирует случайное ображание для вашего ключа (рисунок C) и вернет вам приглашение.
Этот процесс создаст два ключа в каталоге /Users/USERNAME/.ssh (где USERNAME – ваше имя пользователя macOS).
Файл, заканчивающийся на .pub, является открытым ключом.
Это ключ, которым вы можете поделиться с другими пользователями.
Другой ключ, id_rsa, это ваш личный ключ. Никогда не делитесь этим ключом.
Скопируйте свой ключ на сервер
Теперь, когда у вас есть пара ключей, как вы их должны использовать?
Вот самый простой и часто используемый метод использования ключей SSH.
Вы должны скопировать ключ на удаленный сервер, чтобы использовать аутентификацию по ключу SSH (вместо более слабой аутентификации по паролю).
К счастью, в SSH есть встроенный механизм для копирования этого ключа.
Предположим, что рассматриваемый удаленный сервер имеет IP-адрес 192.168.1.12, а имя пользователя – jack.
Чтобы скопировать ключ на этот сервер, введите команду (из macOS):
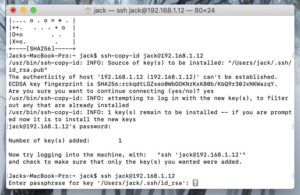
Сначала вам будет предложено ответить, хотите ли вы продолжить соединение.
Введите y и нажмите Enter.
Далее вам будет предложено ввести пароль удаленного пользователя.
После успешной аутентификации ключи будут скопированы, и вы будете готовы войти на удаленный сервер, используя аутентификацию по ключу SSH.
Чтобы войти на удаленный сервер, введите команду (при необходимости подставив имя пользователя и IP-адрес):
Вместо того, чтобы запрашивать пароль пользователя, вам будет предложено ввести пароль для ключа SSH (рисунок D).
Поздравляем, вы не только сгенерировали ключи SSH в macOS, но и скопировали эти ключи на удаленный сервер для более безопасного соединения.
Источник
How do I get an SSH Public Key on Mac?
11th April 2019 by Ricki Larkin
.So you have been to asked for your Public SSH Key? We are here with a quick guide into getting hold of one on your Mac!
Step 1 – Open Terminal
There are many options of running the SSH public key on Macs. However we recommend running this from the terminal command line as this is the easiest.
To get started, you need to open the Terminal application which is found in Applications > Utilities > Directory, but you can also launch this by hitting cmd+spacebar and typing “Terminal” into the search box and then return.
Once open you will be greeted with a window where your cursor is just after a $ symbol. This means you are ready to go!
Step 2 – Generate Your SSH Keys
Now you are ready to type, enter the following command and hit enter:
ssh-keygen -t rsa -b 4096
If this works, you will be asked where to save your keys, the default location is fine so you can just hit enter again. Please be aware that if you enter a location other than default then the code in Step 3 will change to the location you specified.
Next you will be prompted to enter a passphrase. This can be anything you wish but please remember it as you will need to confirm it immediately after.
That’s it! Your keys have been generated, now how to you get hold of them? You’ll still need this Terminal window, so keep it open for now.
Step 3 – Save your Private Key, send your Public Key
Your Private Key will live forever at location you specified in Step 2. You should NEVER share your Private Key, so keep it a secret!
Your Public Key needs to be sent over to us so we can set you up with access. In order to copy your Public Key so you can paste it into an email, simply enter the following command in your Terminal window and hit enter:
You should now have your Public Key on your clipboard. Now head over to your email client, paste into the email content and send it over.
Once we’ve received your Public Key, our server technicians can set you up with access to the server and talk you through how to connect.
If you need any further assistance, please contact your account manager by raising a support ticket or calling the office on 01785 279920.
Источник
Generating a new SSH key and adding it to the ssh-agent
After you’ve checked for existing SSH keys, you can generate a new SSH key to use for authentication, then add it to the ssh-agent.
About SSH key generation
If you don’t already have an SSH key, you must generate a new SSH key to use for authentication. If you’re unsure whether you already have an SSH key, you can check for existing keys. For more information, see «Checking for existing SSH keys.»
If you want to use a hardware security key to authenticate to GitHub, you must generate a new SSH key for your hardware security key. You must connect your hardware security key to your computer when you authenticate with the key pair. For more information, see the OpenSSH 8.2 release notes.
If you don’t want to reenter your passphrase every time you use your SSH key, you can add your key to the SSH agent, which manages your SSH keys and remembers your passphrase.
Generating a new SSH key
Open Terminal Terminal Git Bash .
Paste the text below, substituting in your GitHub email address.
Note: If you are using a legacy system that doesn’t support the Ed25519 algorithm, use:
This creates a new SSH key, using the provided email as a label.
When you’re prompted to «Enter a file in which to save the key,» press Enter. This accepts the default file location.
At the prompt, type a secure passphrase. For more information, see «Working with SSH key passphrases.»
Adding your SSH key to the ssh-agent
Before adding a new SSH key to the ssh-agent to manage your keys, you should have checked for existing SSH keys and generated a new SSH key. When adding your SSH key to the agent, use the default macOS ssh-add command, and not an application installed by macports, homebrew, or some other external source.
Start the ssh-agent in the background.
Depending on your environment, you may need to use a different command. For example, you may need to use root access by running sudo -s -H before starting the ssh-agent, or you may need to use exec ssh-agent bash or exec ssh-agent zsh to run the ssh-agent.
If you’re using macOS Sierra 10.12.2 or later, you will need to modify your
/.ssh/config file to automatically load keys into the ssh-agent and store passphrases in your keychain.
First, check to see if your
/.ssh/config file exists in the default location.
If the file doesn’t exist, create the file.
/.ssh/config file, then modify the file to contain the following lines. If your SSH key file has a different name or path than the example code, modify the filename or path to match your current setup.
Note: If you chose not to add a passphrase to your key, you should omit the UseKeychain line.
Note: If you see an error like this
add an additional config line to your Host * section:
Add your SSH private key to the ssh-agent and store your passphrase in the keychain. If you created your key with a different name, or if you are adding an existing key that has a different name, replace id_ed25519 in the command with the name of your private key file.
Note: The -K option is Apple’s standard version of ssh-add , which stores the passphrase in your keychain for you when you add an SSH key to the ssh-agent. If you chose not to add a passphrase to your key, run the command without the -K option.
If you don’t have Apple’s standard version installed, you may receive an error. For more information on resolving this error, see «Error: ssh-add: illegal option — K.»
Add the SSH key to your account on GitHub. For more information, see «Adding a new SSH key to your GitHub account.»
If you have GitHub Desktop installed, you can use it to clone repositories and not deal with SSH keys.
Ensure the ssh-agent is running. You can use the «Auto-launching the ssh-agent» instructions in «Working with SSH key passphrases», or start it manually:
Add your SSH private key to the ssh-agent. If you created your key with a different name, or if you are adding an existing key that has a different name, replace id_ed25519 in the command with the name of your private key file.
Add the SSH key to your account on GitHub. For more information, see «Adding a new SSH key to your GitHub account.»
Start the ssh-agent in the background.
Depending on your environment, you may need to use a different command. For example, you may need to use root access by running sudo -s -H before starting the ssh-agent, or you may need to use exec ssh-agent bash or exec ssh-agent zsh to run the ssh-agent.
Add your SSH private key to the ssh-agent. If you created your key with a different name, or if you are adding an existing key that has a different name, replace id_ed25519 in the command with the name of your private key file.
Add the SSH key to your account on GitHub. For more information, see «Adding a new SSH key to your GitHub account.»
Generating a new SSH key for a hardware security key
If you are using macOS or Linux, you may need to update your SSH client or install a new SSH client prior to generating a new SSH key. For more information, see «Error: Unknown key type.»
Insert your hardware security key into your computer.
Open Terminal Terminal Git Bash .
Paste the text below, substituting in the email address for your account on GitHub.
Note: If the command fails and you receive the error invalid format or feature not supported, you may be using a hardware security key that does not support the Ed25519 algorithm. Enter the following command instead.
When you are prompted, touch the button on your hardware security key.
When you are prompted to «Enter a file in which to save the key,» press Enter to accept the default file location.
When you are prompted to type a passphrase, press Enter.
Add the SSH key to your account on GitHub. For more information, see «Adding a new SSH key to your GitHub account.»
Help us make these docs great!
All GitHub docs are open source. See something that’s wrong or unclear? Submit a pull request.
Источник