- How to Attack Windows Server 2012 R2 Using Eternalblue
- How To Attack Windows Server 2012 R2 using Eternalblue
- Windows Server 2012 R2 Exploit
- 1 — Prepare the environment
- 2— Create our shellcode
- White Hat Penetration Testing and Ethical Hacking
- Subscribe to this blog
- Follow by Email
- MS17-010 Vulnerability — New EternalRomance / EternalSynergy / EternalChampion SMB modules for Metasploit — Exploit Windows2012R2 and Windows2016
- MS17-010 Vulnerability New EternalRomance / EternalSynergy / EternalChampion SMB modules for Metasploit Exploiting Windows 2012 R2 and Windows 2016
- ИБ-специалист адаптировал эксплоиты АНБ для всех версий Windows
- Xakep #263. Кредитки в опасности
- Exploiting Windows Server 2012 R2
- Summary
- Requirements:
- Overview
- How To : Manually Exploit EternalBlue on Windows Server Using MS17-010 Python Exploit
- Step 1: Set Up the Python-Based Exploit
- Step 2: Find Named Pipe
- Step 3: Run the Exploit File
- Step 4: Serve the Payload
- Step 5: Modify the Code
- Step 6: Run the Finished Exploit
- Wrapping Up
How to Attack Windows Server 2012 R2 Using Eternalblue
How To Attack Windows Server 2012 R2 using Eternalblue
Windows Server 2012 R2 Exploit
Hi Medium! Here we are again with a new article, today we will share a small tutorial where we attack a Windows Server 2012 R2 that it can be in many occasion the AD server of a company, In my last article I shared how we can attack Windows 7, if you want to read the article check this Link
Today we will use two ways the first we get a shell access and in the second we get a Meterpreter access:
1 — Prepare the environment
In this tutorial we need a Kali linux and a Windows Server 2012 R2, before we begin we need to run those command to update our kali OS
We need to power on the Windows Server and get his IP@. If you are in a Pentesting mission and you don’t have the IP target address you just need to run a network scan using nmap :
2— Create our shellcode
+ First we need to download the shell code developed by Sleepya from this link then we assemble it using nasm (you can download nasm from this link) with this command :
White Hat Penetration Testing and Ethical Hacking
A practical approach to computer security, vulnerability checking, penetration testing techniques and ethical hacking. Kali Linux and Metasploit are usually used in my lab scenarios.
Subscribe to this blog
Follow by Email
MS17-010 Vulnerability — New EternalRomance / EternalSynergy / EternalChampion SMB modules for Metasploit — Exploit Windows2012R2 and Windows2016
- Get link
- Other Apps
In the previous post, we covered the two new MS17-010 EternalRomance / EternalSynergy / EternalChampion SMB Remote Windows Command/Code Execution modules that Metasploit released last month:
auxiliary/admin/smb/ms17_010_command and
exploit/windows/smb/ms17_010_psexec
One of the cool features for the new modules is that they are supposed to work with all Microsoft OS versions post-Windows 2000. Check this message on Twitter from zerosum0x0 — one of the modules’ authors.
Therefore, I wanted to test the new modules with newer Microsoft OS Server versions like Windows 2012 R2 and Windows 2016.
As you will see in the video below, exploiting Windows 2012 R2 and Windows 2016 is similar to exploiting Windows 10. We will need non-admin user credentials in order to exploit successfully, because by default no named pipes are available when connecting anonymously.
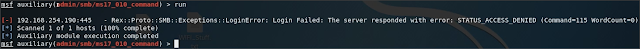
For learning purposes, I attempted to use the modules without specifying the credentials and I got the following error:
:445 — Rex::Proto::SMB::Exceptions::LoginError: Login Failed: undefined method `force_encoding’ for nil:NilClass
The details for my LAB are as in the picture below:
MS17-010 Vulnerability
New EternalRomance / EternalSynergy / EternalChampion SMB modules for Metasploit
Exploiting Windows 2012 R2 and Windows 2016
ИБ-специалист адаптировал эксплоиты АНБ для всех версий Windows
Xakep #263. Кредитки в опасности
Весной 2017 года хакерская группа The Shadow Brokers опубликовала в открытом доступе «арсенал кибероружия», похищенный у американских спецслужб. Тогда хакеры обнародовали различные эксплоиты и инструменты, украденные у Equation Group – группировки, за которой стоят «правительственные хакеры» из АНБ. В результате достоянием широкой общественности стали такие опасные вещи, как эксплоит EternalBlue, направленный на эксплуатацию уязвимости в протоколе SMB (именно он использовался для распространения шифровальщика WannaCry в мае 2017 года, а затем во время атак NotPetya и Bad Rabbit).
Еще летом 2017 года специалисты компании RiskSense, Шон Диллон (Sean Dillon) и Дилан Девис (Dylan Davis) сообщили, что им удалось адаптировать эксплоит EternalBlue для работы с Windows 10. Напомню, что на тот момент инструмент для использования багов в SMB уже мог применяться для атак на Windows XP, Windows Vista, Windows 7, Windows Server 2003 и Windows Server 2008, хотя в некоторых случаях добиться заражения было весьма непросто. Также исследователям удалось модифицировать EternalBlue для работы с Windows 8, Windows 8.1 и Windows Server 2012.
Однако в опубликованном The Shadow Brokers дампе содержались и другие эксплоиты, чьи названия не столь известны, но потенциал тоже обширен. Все прошедшие месяцы Шон Диллон продолжал начатую в 2017 году работу и теперь сообщил об очередном успехе. Исследователю удалось скорректировать исходный код эксплоитов EternalChampion, EternalRomance и EternalSynergy таким образом, что теперь эти инструменты могут использоваться против любых версий Windows, 32-разрядных и 64-разрядных, вышедших за последние 18 лет (начиная с Windows 2000 и далее).
Диллон уже адаптировал результат своей работы для Metasploit и опубликовал исходные коды на GitHub. Так, CVE-2017-0146 (EternalChampion, EternalSynergy) позволяет спровоцировать состояние гонки через transaction-запросы, а CVE-2017-0143 (EternalRomance, EternalSynergy) эксплуатирует проблему типа type confusion между WriteAndX и transaction-запросами.
Диллон пишет, что эксплоиты работают против следующих, непропатченных версий Windows:
- Windows 2000 SP0 x86
- Windows 2000 Professional SP4 x86
- Windows 2000 Advanced Server SP4 x86
- Windows XP SP0 x86
- Windows XP SP1 x86
- Windows XP SP2 x86
- Windows XP SP3 x86
- Windows XP SP2 x64
- Windows Server 2003 SP0 x86
- Windows Server 2003 SP1 x86
- Windows Server 2003 Enterprise SP 2 x86
- Windows Server 2003 SP1 x64
- Windows Server 2003 R2 SP1 x86
- Windows Server 2003 R2 SP2 x86
- Windows Vista Home Premium x86
- Windows Vista x64
- Windows Server 2008 SP1 x86
- Windows Server 2008 x64
- Windows 7 x86
- Windows 7 Ultimate SP1 x86
- Windows 7 Enterprise SP1 x86
- Windows 7 SP0 x64
- Windows 7 SP1 x64
- Windows Server 2008 R2 x64
- Windows Server 2008 R2 SP1 x64
- Windows 8 x86
- Windows 8 x64
- Windows Server 2012 x64
- Windows 8.1 Enterprise Evaluation 9600 x86
- Windows 8.1 SP1 x86
- Windows 8.1 x64
- Windows 8.1 SP1 x64
- Windows Server 2012 R2 x86
- Windows Server 2012 R2 Standard 9600 x64
- Windows Server 2012 R2 SP1 x64
- Windows 10 Enterprise 10.10240 x86
- Windows 10 Enterprise 10.10240 x64
- Windows 10 10.10586 x86
- Windows 10 10.10586 x64
- Windows Server 2016 10.10586 x64
- Windows 10 10.0.14393 x86
- Windows 10 Enterprise Evaluation 10.14393 x64
- Windows Server 2016 Data Center 10.14393 x64
Эксперт подчеркивает, что данные инструменты были созданы исключительно в рамках научного исследования и предназначены для специалистов и разработки эффективных защитных практик. Использование этих эксплоитов для атак без явного согласия третьей стороны – противозаконно, и автор не несет никакой ответственности за подобные инциденты.
Exploiting Windows Server 2012 R2
Summary
For some reason, you ran into a windows server 2012 on a virtual machine and do not know the administrator password or simply forgot the password and need to gain access this is for you.
Requirements:
Windows 2012 Server Iso image booted on some device or into your virtual machine.
Overview
Boot on your Windows Server Image and go to repair setting
Go to Troubleshoot and open the CMD
Make a Backup of Utilman
command: move D:/Windows/System32/Utilman.exe D:/Windows/System32/Utilman0.exe
Replace Utilman.exe with CMD with
coomand: copy D:/Windows/System32/cmd.exe D:/Windows/System32/Utilman.exe
Now reboot on your machine and go to the login page on Windows Server 2012
press Wi n dows + U and will open the CMD on login page
Now write: net user *Username* *password* wihtout this quote and press enter and the password have been replaced
How To : Manually Exploit EternalBlue on Windows Server Using MS17-010 Python Exploit
EternalBlue was a devastating exploit that targeted Microsoft’s implementation of the SMB protocol. Metasploit contains a useful module that will automatically exploit a target, as long as it’s vulnerable. But what if we wanted to exploit this vulnerability without Metasploit holding our hand? It can be done using a Python file to exploit EternalBlue manually.
I won’t go into the whole spiel about what EternalBlue is, where the exploit came from, or how SMB works since I already did that in the previous guide on exploiting EternalBlue on Windows Server with Metasploit. So for more background information on what EternalBlue and SMB are and how to figure out if a target is vulnerable or not, make sure to check that out before continuing.
In this guide, we’ll tackle the manual route of exploiting EternalBlue on Windows Server. I’ll be using an unpatched copy of Windows Server 2016 Datacenter as the target, and evaluation copies can be downloaded from Microsoft if you want to follow along as we perform each step below.
Step 1: Set Up the Python-Based Exploit
The first thing we need to do is locate the exploit file. On Kali, we can use searchsploit in the terminal to search the database for a match.
The exploit we want is labeled 42315.py. In order to keep things tidy, let’s create a directory to work out of.
Now we can copy the exploit file to our newly created directory.
Then, change into the directory and verify the file is present.
Now we can take a look at the source code for more information about this particular exploit. This is quite a long file, so we can use the less command to view it from the top.
This exploit requires a valid named pipe (we’ll get to this soon) and a valid set of credentials. These can be any other credentials from a user that has logged onto the target in the past, including guest accounts. The exploit will automatically upgrade us to a privileged account when it’s run.
Before we go any further, it is a good idea to make a copy of this file so we have access to the original source code. We can rename it exploit.py to keep it simple.
Now we can edit the Python file and enter a valid username and password to use.
Save it, and now we can try to run the exploit.
It looks like it is trying to import a module named mysmb, so in order for this to work, we need to download it. We can easily do that using wget.
Try running the file again and we get different output.
It looks like usage information now, which is a good sign. We need to plug in the IP address of our target and a pipe name as parameters.
Step 2: Find Named Pipe
Named pipes are a way for running processes to communicate with each other with very little overhead. Pipes usually appear as files for other processes to attach to. Metasploit has a scanner that will find any named pipes on a host. In a new terminal, type msfconsole to fire it up, then we can search for the scanner.
The one we want is the pipe_auditor. Load the module with the use command.
You should see the «auxiliary(scanner/smb/pipe_auditor) > options» prompt. Now we can take a look at the options.
All we really need to do is specify the IP address of our target.
And then we can run the scanner.
It looks like it found a few named pipes. Awesome.
Step 3: Run the Exploit File
Now we should be able to run the exploit file. Back in the first terminal from Step 1, where we’re still in the exploit directory, use the target’s IP address and one of the named pipes we found as parameters.
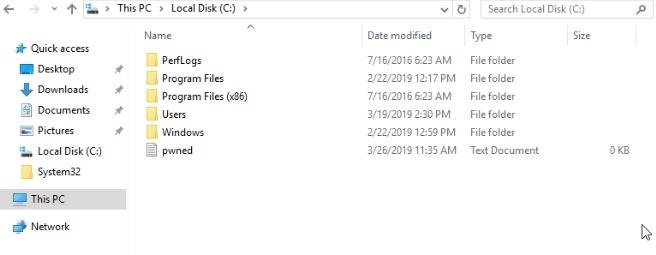
We can see some data spit out on the screen, and at the bottom, it says it created a text file on the target. If we take a peek at the target, we can see this was successful.
But we want to do more than just create a text file on the target. This is just a proof of concept, after all, so we will need to do a few more things to get this exploit fully functional.
Step 4: Serve the Payload
We’re going to need a payload and a way for the exploit to get it and execute. For that, we can use MSFvenom to generate some shellcode, and we can serve it from our machine using Apache.
In a new terminal, use the following command to generate the payload and save it to a file named sc.exe in the default web root for the Apache server.
This is a long command, so let’s break it down:
- The -a flag specifies the architecture as 64-bit.
- The —platform option sets the platform as Windows.
- The -p flag specifies the payload.
- lhost is our local machine to connect back to.
- lport is the local port to connect to.
- The -e flag specifies the encoder to use.
- The -i flag sets the number of iterations the encoder uses.
- The -f flag sets the format.
- The -o flag specifies the output file.
Now we can start the Apache server so the exploit can connect to our machine from the target to reach the payload. Next, we will tweak the code to fit our needs.
Step 5: Modify the Code
Back in exploit.py, find the section of code near the bottom that looks like this:
Here we can see the code that is responsible for connecting to the target and creating the text file. We can also see an interesting looking function called service_exec() which is commented out. That will connect to the target and issue a command to copy the previously created text file into a new text file named pwned_exec.txt on the C drive. We can use this function to grab our payload and execute it on the target.
First, uncomment the function and replace everything after cmd /c with the following command:
BITSAdmin (Background Intelligent Transfer Service) is a Windows command-line tool used to upload or download files. The /transfer switch initializes a transfer (with the name pwn in this case) and /download specifies that it is a download. Then we enter the name of the remote file (being hosted on our machine) and the name of the local file once it’s transferred.
Next, add another service_exec() function and have it execute the file we just transferred. The code will look like this:
Finally, we can comment out the section that creates a text file, since we really don’t need it anymore. The final code should look like this:
Now, all we have left to do now is run the exploit.
Step 6: Run the Finished Exploit
To complete the exploit, we need something to catch the shell once the payload executes. We can use the multipurpose handler in Metasploit for this. In a new terminal, use the following commands.
You should see the «exploit(multi/handler)» prompt. We just need to set the payload to match whatever we specified when we created the shellcode earlier, which in this case is a reverse TCP shell.
Next, set the appropriate listening host.
And the listening port.
And we can start the handler.
It will listen for any incoming connections, and if everything goes smoothly, we’ll get a Meterpreter session once our exploit completes.
At last, we should have everything in place and ready to go. We can launch the exploit just like we did earlier in our test run from within the exploit directory.
This time we should see different results. Ignore the errors, and if it doesn’t work the first time, just try again. Once the exploit successfully completes, we should see a session open up back on our listener.
We can verify we have compromised the target with the sysinfo command.
And the getuid command.
And there we have it — a full Meterpreter session from manually exploiting EternalBlue.
Wrapping Up
In this tutorial, we covered how to manually exploit EternalBlue on Windows Server. We began by setting up a few things in order to get the proof of concept to work. Next, we generated some shellcode and hosted the payload on our machine. After that, we modified the code, launched the exploit, and successfully got a Meterpreter session on the target. Even though Metasploit contains a module to do all this automatically, it’s beneficial to know how to do things the hard way, just in case something needs tweaking for a specific target or scenario.
Want to start making money as a white hat hacker? Jump-start your hacking career with our 2020 Premium Ethical Hacking Certification Training Bundle from the new Null Byte Shop and get over 60 hours of training from cybersecurity professionals.