- How to export Certificates with Private Key in Windows 7
- How do I export a Windows Certificate with the Private Key?
- Экспорт части сертификата аутентификации сервера с закрытым ключом Export the Private Key Portion of a Server Authentication Certificate
- Экспорт части сертификата аутентификации сервера с закрытым ключом To export the private key portion of a server authentication certificate
- Export certificates and private key from Windows 10 certificate store which is deployed through Active Directory
- Know someone who can answer? Share a link to this question via email, Twitter, or Facebook.
- Browse other questions tagged windows powershell active-directory windows-10 windows-server or ask your own question.
- Related
- Hot Network Questions
- Subscribe to RSS
- How to export private key from Windows Certificate Manager?
- 4 Answers 4
- Recovering a certificate where the private key is marked as non-exportable
How to export Certificates with Private Key in Windows 7
As you most probably know, Microsoft has stopped updating Windows 7, and now users are left with the choice of either getting the Extended Support or upgrading to Windows 10.
While some users may choose the Extended Support, they need to keep in mind that this is a temporary and costly solution. Thus, they will have to upgrade to Windows 10 at some point.
Their biggest concern with upgrading to a newer OS is how they will migrate their data since not all of it can be simply copied and pasted from one computer to another.
One good example is how some users may want to export their Windows Certificates with the Private Key.
That is precisely why we’ve compiled this step-by-step guide that will show you how you can export your Windows Certificates with the Private Key, and maybe make it usable in Windows 10.
How do I export a Windows Certificate with the Private Key?
Before starting, you need to remember several things regarding the process:
- A private key is exportable only when it is specified in the certificate request or certificate template that was used to create the certificate.
- You should clear the Enable strong protection checkbox if you will use the private key with any program that does not support strong protection
- You need to be a User or local Administrator to complete this procedure
Once you’ve taken this situation into account, you can proceed with the steps:
- Open the Certificates snap-in for a user, computer, or service. This involves using the Microsoft Management Console
- To view the certificates for a certain device
- Select Run from the Start menu, and then enter certlm.msc.
- To view the certificates for the current user
- Select Run from the Start menu, and then enter certmgr.msc.
- To view the certificates for a certain device
- Look in the console tree under the logical store that contains the certificate to export
- Click Certificates
- Look in the Details pane
- Click the certificate that you want to export
- On the Action menu, point to All Tasks
- Click Export
- When the Certificate Export Wizard appears, click Yes, export the private key
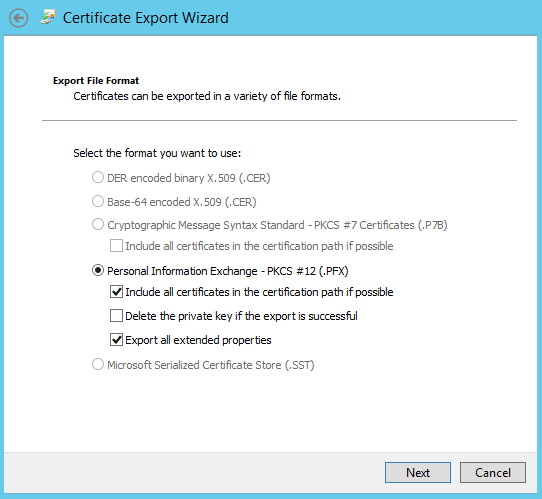
- Under Export File Format, you will need to choose one of the following:
- Include all certificates in the certification path if possible
- This will include all certificates in the certification path
- Delete the private key if the export is successful
- This will delete the private key if the export is successful
- Export all extended properties
- This will export the certificate’s extended properties
- This will export the certificate’s extended properties
- Include all certificates in the certification path if possible
- Choose a password to encrypt the key that you are exporting
- Give the file a name, and select a file path for it to be exported
By following these steps, the certificate will remain in the certificate store in addition to being in the newly created file .
Did you find this article useful? Let us know in the comments section below.
RELATED ARTICLES YOU SHOULD CHECK OUT:
Экспорт части сертификата аутентификации сервера с закрытым ключом Export the Private Key Portion of a Server Authentication Certificate
Каждый сервер федерации в ферме службы федерации Active Directory (AD FS) ( AD FS ) должен иметь доступ к закрытому ключу сертификата проверки подлинности сервера. Every federation server in an Active Directory Federation Services (AD FS) farm must have access to the private key of the server authentication certificate. При реализации фермы серверов или веб-серверов федерации необходимо иметь один сертификат проверки подлинности. If you are implementing a server farm of federation servers or Web servers, you must have a single authentication certificate. Этот сертификат должен быть выдан ЦС центра сертификации предприятия ( ) и должен иметь экспортируемый закрытый ключ. This certificate must be issued by an enterprise certification authority (CA), and it must have an exportable private key. Закрытый ключ сертификата аутентификации сервера должен быть экспортируемым, чтобы его можно было предоставить всем серверам на ферме. The private key of the server authentication certificate must be exportable so that it can be made available to all the servers in the farm.
Эта же концепция относится к фермам прокси-серверов федерации в том смысле, что все прокси сервера федерации в ферме должны совместно использовать частную часть одного сертификата проверки подлинности сервера. This same concept is true of federation server proxy farms in the sense that all federation server proxies in a farm must share the private key portion of the same server authentication certificate.
Оснастка управления AD FS — в относится к сертификатам проверки подлинности сервера для серверов федерации в качестве сертификатов связи служб. The AD FS Management snap-in refers to server authentication certificates for federation servers as service communication certificates.
В зависимости от роли, которую будет воспроизводить этот компьютер, используйте эту процедуру на компьютере сервера федерации или прокси-сервера федерации, где установлен сертификат проверки подлинности сервера с закрытым ключом. Depending on which role this computer will play, use this procedure on the federation server computer or federation server proxy computer where you installed the server authentication certificate with the private key. По окончании процедуры можно импортировать этот сертификат на веб-сайт по умолчанию каждого сервера на ферме. When you finish the procedure, you can then import this certificate on the Default Web Site of each server in the farm. Дополнительные сведения см. в разделе Импорт сертификата проверки подлинности сервера на веб-сайт по умолчанию. For more information, see Import a Server Authentication Certificate to the Default Web Site.
Для выполнения этой процедуры требуется членство в группе Администраторы или в эквивалентной группе на локальном компьютере. Membership in Administrators, or equivalent, on the local computer is the minimum required to complete this procedure. Просмотрите сведения об использовании соответствующих учетных записей и членстве в группах в локальной среде и группах домена по умолчанию. Review details about using the appropriate accounts and group memberships at Local and Domain Default Groups.
Экспорт части сертификата аутентификации сервера с закрытым ключом To export the private key portion of a server authentication certificate
На начальном экране введите службы IIS ( ) Диспетчер IIS и нажмите клавишу ВВОД. On the Start screen, type Internet Information Services (IIS) Manager, and then press ENTER.
В дереве консоли щелкните ComputerName. In the console tree, click ComputerName.
В центральной области дважды — щелкните Сертификаты сервера. In the center pane, double-click Server Certificates.
В центральной области щелкните правой кнопкой мыши — сертификат, который необходимо экспортировать, и выберите пункт Экспорт. In the center pane, right-click the certificate that you want to export, and then click Export.
В диалоговом окне Экспорт сертификатов нажмите кнопку … In the Export Certificate dialog box, click the … . button.
В окне имя файла введите C: \намеофцертификате, а затем нажмите кнопку Открыть. In File name, type C:\NameofCertificate, and then click Open.
Введите пароль для сертификата, подтвердите его и нажмите кнопку ОК. Type a password for the certificate, confirm it, and then click OK.
Проверьте, успешно ли выполнен экспорт, убедившись, что заданный файл создан в заданном расположении. Validate the success of your export by confirming that the file you specified is created at the specified location.
Для того чтобы этот сертификат можно было импортировать в локальное хранилище сертификатов на новом сервере, необходимо переместить файл на физический носитель и обеспечить его безопасность во время переноса на новый сервер. So that this certificate can be imported to the local certificate store on the new server, you must transfer the file to physical media and protect its security during transport to the new server. Очень важно обеспечить безопасность закрытого ключа. It is extremely important to guard the security of the private key. Если этот ключ скомпрометирован, безопасность всего развертывания AD FS, ( включая ресурсы в Организации и организации партнера по ресурсам, ) скомпрометирована. If this key is compromised, the security of your entire AD FS deployment (including resources within your organization and in resource partner organizations) is compromised.
Export certificates and private key from Windows 10 certificate store which is deployed through Active Directory
I have deployed certificate and private key using AD group policy which deployed certificate and private key to the client machine. When I tried to export the certificate and private key from the client machine, the private key export option was disabled. I have enabled the private key export option when imported to the AD group policy. But that didn’t help me to export the private key from the client machine. Certificates export worked well from the client machine without the key.
I would like to export this certificate and key from the client machine (export in any format). Can anyone help to do this?
Thanks in Advance.
Know someone who can answer? Share a link to this question via email, Twitter, or Facebook.
Browse other questions tagged windows powershell active-directory windows-10 windows-server or ask your own question.
Related
Hot Network Questions
Subscribe to RSS
To subscribe to this RSS feed, copy and paste this URL into your RSS reader.
site design / logo © 2021 Stack Exchange Inc; user contributions licensed under cc by-sa. rev 2021.4.16.39093
By clicking “Accept all cookies”, you agree Stack Exchange can store cookies on your device and disclose information in accordance with our Cookie Policy.
How to export private key from Windows Certificate Manager?
I’m developing in a Windows environment.
My company functions as it’s own certificate authority for internal-use https applications, and I’ve been issued a certificate from our system (for an internal-use only web server I’ve built).
Using certificate manager I am able to export the certificate. But, when exporting the certificate from certificate manager, the ‘export private key’ radio button is greyed out. Follow
4 Answers 4
Recovering a certificate where the private key is marked as non-exportable
We needed to export the private key of our IIS7 SSL certificate in order to import it in a node.js HTTPS project operating on a different port under the same domain.
We realized that the certificate had lost its ability to export the private key. The certificate had recently been re-issued using the old CSR but somehow the new certificate’s private key was marked as non-exportable, while past certificates had exportable private keys. Luckily we had a previous certificate available with exportable private key to work with. There are guides on the internet that the following process might work without the old certificate but in our case it did not, possibly because the certificate was re-issued.
DISCLAIMER: the following process is not intrusive on your computer and requires a VM to work with. If it succeeds then your will get your private key exported. If it fails, then your only option would be to create a CSR with exportable private key and re-issue your certificate and re-configure your domains.
Using mmc we imported both certificates in Local Computer\Personal.
NOTE: THE PLACE THAT YOU IMPORT CERTIFICATES IS IMPORTANT!
We located the Thumbprint of the certificate with the non-exportable private key:
In this sample the thumb is 693867F321B5764E324F3FB8C5CBCE03CDA3C2A3.
IMPORTANT: THUMB MUST BE UPPERCASE .
At this point, depending on the root cause of your problem, we suggest starting a command prompt and enter the following command, as it might cure your problem:
If the problem is not cured and the private key remains non-exportable, continue.
Using PowerShell we identified the private key store and copied to C:\
This command revealed the private key store to be:
Then using NirSoft PsExec64 we started an Elevated Command Prompt on System account and copied / decrypted the keystore to C:\ using /G and /H.
We create a VMware and copied both certificates and the private key store:
Using MMC we imported both certificates into Local Computer\Personal:
During import, we made sure that for the certificate with the private key, we marked the private key as exportable:
So, both certificates were imported but as expected only one had the lock icon indicating it had a private key:
Using Power Shell on the VM, we got the Machine’s GUID from Microsoft Cryptography and used this GUID in order to copy the private key store to the proper location.
This returned: a73d2e44-7a45-486a-97d3-b9d97bf556fa. In the following command you need to replace the old computer’s GUID with the new, the GUID is after the first dash (-). The command syntax is this:
So, according to the identifiers derived in previous steps, it should look like this:
Then we run certutil using the thumb of the problematic certificate to repair it!
You should see something like this:
After refreshing MMC you will that both certificates have a private key icon:
So, go ahead and export the certificate with the private key:
SOS: MAKE SURE YOU MARK THE PRIVATE KEY AS EXPORTABLE .
Next copy the PFX file back to your node.js server computer and import it ON-TOP of the existing problematic certificate.
Once you import the new certificate you can delete the old.
Next re-export the certificate from your server, just for sanity check. You should see the Export Private Key that is not grayed out any more!
SOS: MAKE SURE YOU MARK THE PRIVATE KEY AS EXPORTABLE .
To export the private key for node.js we used DigiCert Utility tool:
To convert the PFX to PEM for node.js we used OpenSSL:
To use the certificate is node.js create an SLL folder in your node.exe path and copy the following items in it:
- Private Key file (.key)
- Certificate file (.pem)
- Authority Certificate file (.crt)
NOTE: the authority certificate file is provided along with your certificate from your certificate provider.
Finally you may load the certificate and private key using the following code: