- How to hack Facebook with Kali Linux and SET(Social Engineering Toolkit)
- Table of contents
- What is Social Engineering Toolkit (SET)??
- How to hack Facebook using Kali Linux
- Fake Facebook Phishing Page made by Kali Linux
- Commonly Asked Questions
- Q1. Is hacking facebook with kali Linux legal to use on anyone?
- Q2. Can I hack Account Using Mobile phone?
- Facebook Account Hacking — The Best 9 Methods
- 1. Phishing
- 2. Keylogger
- 3. Reset The Password/Recover Account
- 4. Hacking the Email
- 5. Easy Passwords
- 6. Man in the Middle
- 7. Looking for Passwords
- 8. Low Security Websites
- 9. Viruses or Malware
- You may like these posts
- Comments
How to hack Facebook with Kali Linux and SET(Social Engineering Toolkit)
Welcome to another Facebook Hacking tutorial. If you want to know how to hack Facebook with Kali Linux, you have come to the right place. In this article, we will be showing you how you can hack Facebook with Kali Linux and social engineering toolkit.
Do note you need Kali Linux installed on your system for this hack to work. You can also install Kali Linux via Virtual Machine as well.
Table of contents
What is Social Engineering Toolkit (SET)??
The Social-Engineer Toolkit (SET) is intended to perform very targetted against the human attack vector. SET was made by David Kennedy and his team. The attacks included within the toolbox are intended to be used for testing purposes. Even though we can hack Facebook with Kali Linux know that it is illegal to do so without proper permission from the parties involved.
We will be using the SET toolkit, which is preinstalled in Kali Linux to hack Facebook account.
If you want to install on any other Linux distribution use the following commands:
How to hack Facebook using Kali Linux
Step 1: Open a Kali Linux.
Step 2: Search for setoolkit and run the Toolkit via the shortcut as shown below:
Step 3: Press “Y” to accept social engineering toolkit terms and conditions.
Step (4) As you can see from the image below the following options will be shown to you:
1) Social-Engineering Attacks
2) Penetration Testing (Fast-Track)
3) Third-Party Modules
Step 5: Select social engineering attacks option by selecting the appropriate option, which in our case is “1.”
Type “1.”
Step 6: Now, you will see more options, as shown. Select the correct option in our case; its option “2.”
Type “2.”
1) Spear-Phishing Attack Vectors
2) Website Attack Vectors
3) Infectious Media Generator
4) Create a Payload and Listener
5) Mass Mailer Attack
6) Arduino-Based Attack Vector
7) Wireless Access Point Attack Vector
8) QRCode Generator Attack Vector
9) Powershell Attack Vectors
10) Third-Party Modules
Step 7: Now select the Credential Harvester Attack Method
Type “3.”
1) Java Applet Attack Method
2) Metasploit Browser Exploit Method
3) Credential Harvester Attack Method
4) Tabnabbing Attack Method
5) Web Jacking Attack Method
6) Multi-Attack Web Method
7) HTA Attack Method
Step 8: Select the site cloner option by selecting the appropriate option
Type “2.”
1) Web Templates
2) Site Cloner
3) Custom Import
Step 9: Give your IP address to set up and start the attack
set:webattack> IP address for the POST back in Harvester/Tabnabbing [192.168.x.xxx]:(your IP address)
You can find your IP address by using the ifconfig command
Step 10: Select the URL to clone. In our case it is www.facebook.com
set:webattack>Enter the URL to clone: www.facebook.com
Step 11: Go to other location > Computer > VAR > WWW and move every one of the files from www folder to HTML folder.
Step 12: Using tinyurl.com, make your IP address shorter and send it to the victim. When he logs in through your phishing link you will get his/her credentials in a file which is located at other location> Computer > VAR > WWW.
Fake Facebook Phishing Page made by Kali Linux
That’s it you have successfully hacked facebook using Kali Linux and social engineering g toolkit.
Commonly Asked Questions
Below are some of the questions that might come in your mind while learning how to hack facebook with Kali Linux and social engineering tool
Q1. Is hacking facebook with kali Linux legal to use on anyone?
No, It is not legal Kali Linux to Hack facebook accounts of people. If you use it to hack someone’s account without their permission then it is a criminal offence. You are only supposed to use this for learning and testing purposes
Q2. Can I hack Account Using Mobile phone?
Yes, you can use your mobile phone to hack facebook account. But you will need to install Kali Linux Nethunter on your android device. Not all mobile devices are fully compatible. You can also use termux app and install Linux on your android phone.
If your account was hacked then you can recover the account by using the following article:
In the recover facebook article, we have given numerous ways to recover your hacked facebook account.
If you liked our content then support our website via donations and by sharing our content
Источник
Facebook Account Hacking — The Best 9 Methods
So, we have searched for Facebook account hacking. Almost all new comer in hacking field wants to hack Facebook or Instagram account or Instagram or others Wi-Fi password, this is the main priority of every noobies. After ending this tutorial we will have a clear idea on Facebook hacking in depth. Not only just about Facebook, this tutorial applies on social media accounts like Instagram, Facebook, Twitter, Snapchat etc.
First off all we have to clear the truth that we simply can’t hack Facebook or Instagram. But when we search on Google there have a lots of free tools that giving us password of any Facebook user by just typing user’s email address. If you tried this kind of tools, then you are not on the general level of stupidity. Congratulations, you have achieved a higher level of stupidity. Come on, if this was so easy then Facebook needs to shut down their business.
When some sites or tool says it can hack Facebook passwords by just typing username or e-mail id you should understand that it is fake. They all have some common things which are following :
- All have very user-friendly interface. We just need to type user-id and click on hack.
- Then it will show that the password is successfully cracked, but they will not revel the password.
- All have links which will lead you to a survey or some annoying ads even may be say to download malicious software.
- All are 100% not working.
Then what does actually meaning of Facebook hacking. Many of us are mislead by the term of hacking. They think hacking means steal someone’s password and gaining unauthorized access but hacking is so much more.
When we try to learn hacking Facebook we need to understand some things how Facebook works means understand the functioning of the website, find about Facebook’s database management systems, scripts used, use of cookies, language use to build the website.
Then need to find out vulnerabilities in the the website in our case that is Facebook or Instagram.
Then need to code exploits to break through the obstacles and gain privileges into Facebook’s system, using suitable payloads. Then we need to check their database and the passwords will be encrypted in Facebook’s own way, we need to decrypt the passwords, then the last step is to set a backdoor for easy access next time, and we must need to clear our traces so that we don’t get caught.
Believe us, not everyone can do this, means we read some blogs and learned much things on hacking and Kali Linux, that is not enough for Facebook Hacking. So, the conclusion is that hacking Facebook is a real big deal , not everyone’s cup of tea. Even elite level hackers can’t do it. Nothing is impossible but hacking Facebook in above way is practically very close to impossible.
Humans are the weakest point in any security system.
1. Phishing
 |
| Check the URL please. It’s not real Facebook |
If the victim logs in, the credentials (id and password) will be sent to attacker not in real Facebook. This process is a bit difficult because we need to host a website and create a login page. But some tools really made it kids play. We have some tutorials which makes phishing very easy. Tools like Modlishka can even bypass two factor authentication on a phishing attack. Check following :
How to be safe from Phishing?
- We should not click on any link through email/website/chatroom or text messages etc.
- we need to check the link is driving to original Facebook, mean to say check the links is https://www.facebook.com/ or not. If not and the page is looking like Facebook like the above picture, then this is a phishing page.
- Sometimes phishing links hided with normal looking genuine links. To know more read our hide phishing URL article.
- Windows user should use anti-virus and web-security software , like norton or McAfee . Linux user should take care before clicking unknown links.
2. Keylogger
Keyloggers works can be simply understand by it’s name. Yes it logs all the key strokes on the keyboard that user makes, without their knowledge. When user types their username and password keyloggers capture it.
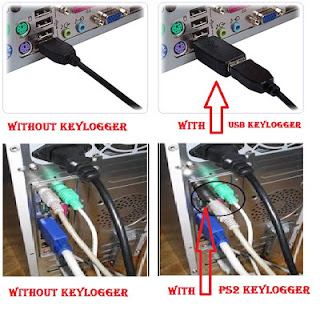 |
| Hardware Keylogger |
Keylogger are generally two types «software keylogger» and «hardware keylogger».
- Software Keylogger:- Software keylogger is a program has to be download (or send by any way) and install on the the victim’s computer or mobile phone. It will automatically start capturing the keystrokes of keyboard. After device turned on this program starts it’s work, and runs in background to be undetected. Software keyloggers sends the details of key strokes to the attacker by email.
- Hardware Keylogger:- The work is same as software keylogger but method is different. Hardware keylogger is a USB/ps2 tool that connects between USB keyboard and the computer. The USB port of keyboard is plugged with this hardware and then it connects to the computer. It capture and saves the keystrokes in it’s inbuilt memory, and attacker need physical access to victim’s computer. Some premium hardware keyloggers have Wi-Fi enabled which can email captured keystrokes or can be accessed remotely over Wi-Fi.
How to be safe from Keyloggers ?
- Use a firewall. Software keyloggers usually send information through the internet, so a firewall will monitor our computer’s online activity and find out if anything suspicious.
- Installing anti-virus or anti-malware is good for windows users to detect software keyloggers.
- Shouldn’t use or download third party programs or apps. It may be embed with malicious apps like keylogger or any other payload.
- Now this is very easy to be safe from hardware keylogger. We need to be aware for it, that someone could not plant a USB hardware on our computer.
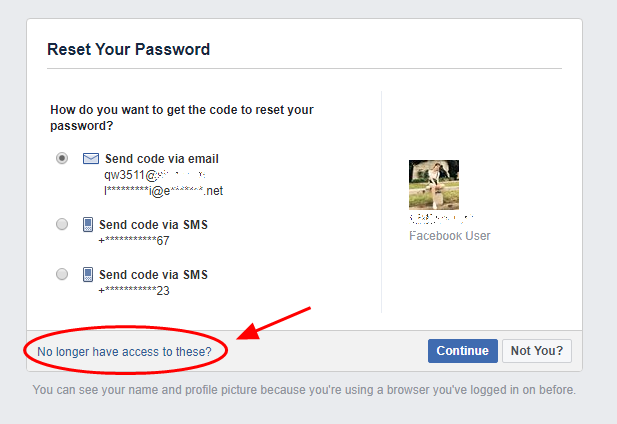
3. Reset The Password/Recover Account
Then if it asks to reset the password by the email. This will not work for the attacker. The attacker need to choose «No longer have access to these ?«
How to be safe from recover account?
- we should use an fresh email address specially for Facebook account and we never show that email id on Facebook profile. We never publish that email id.
- When we choose the security question and answer we need to make it difficult that no one can figure it out by know us personally or checking our Facebook posts. No pet names neither anniversaries, not even the names of best teacher. These questions are very easy for guessing and known personalities.
4. Hacking the Email
How to be safe from E-mail hacking ?
- We need a special care at mail id like Facebook accounts.
- Using a special email for Facebook would be batter. We shouldn’t tell anyone our that email id.
5. Easy Passwords
How to be safe from easy passwords?
- First we should choose an uncommon password. A perfect password will be 13 characters long or more, it must contains some upper case and lower case letters and some numbers and one or more special character like @, *, #, ? etc. Here is a beautiful guidance on choosing secure passwords Click Here.
- We should not write down our password or any personal information anywhere, some hackers check dustbins for personal information.
6. Man in the Middle
If attacker get close to his target, he can use man in the middle attack (MITM) by creating a free fake Wi-Fi network, When target connects with his network attacker can steal credentials. Tools like Wi-Fi Pumpkin makes easy to creating rouge Wi-Fi access point.
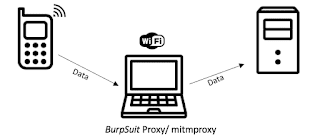 |
| Man-In-The-Middle Image Copyright researchgate.net |
How to be safe from MITM ?
- Don’t connect to any open and unsecured Wi-Fi networks.
- Don’t connect to any network that are out of place. May be we can see «Google Starbucks» when there is no Starbucks near. Attacker knows that our devices will connects automatically to our used same named networks.
- If we got trouble connecting ton our own Wi-Fi, then we need to look at our Wi-Fi list of nearby, If there are any copy of our Wi-Fi network, it might be the attacker using Evil-Twin or any other same types of attacks.
- If our router asks to enter password for firmware upgrade then it might be someone trying to get our credentials. How attackers are able to do it ? Read our this tutorial.
7. Looking for Passwords
How to be safe from this?
- Be careful while typing passwords, is anyone looking at our keyboard or is there any camera behind ?
- If we are saving our credentials in browser then we need to make our personal computer personal, for better result we recommend to not save password in browser because they also can be stolen remotely by using malicious web apps.
- Stay away from typing our password on public place or logging our social media account on public device (like cybercafe etc).
8. Low Security Websites
How to be safe from low security websites?
- Choose different passwords for different websites.
- Must choose an unique long password for e-mail, Facebook and other social media.
9. Viruses or Malware
How to be safe from viruses?
- We should not download 3rd party applications, because hackers can bind a malicious application in a normal looking application. We should always download from the official app store.
- We should not click on any suspicious link.
- If we are using Windows PC then we should buy a good antivirus, anti-spyware, antimalware for our computer, and keep updating it.
So, this is how our Facebook account got hacked. From this tutorial we learned how to be safe, and Facebook hacking is very easy if the user is careless. There are some zero day hacking. Great hackers able to find vulnerabilities in Facebook or Instagram but we don’t need care for this. Facebook developers will fix it as soon as possible. Zero day attackers normally targets the celebrates because zero day attacks is the code exploit attacks that we talked on the starting of this tutorial. This type of hacks needs high end skills and hard works, for this they normally don’t choose normal users they targets well known personalities or celebs.
We need to make our Facebook stronger. Follow our provided steps and be safe from Facebook hacking.
This tutorial is for new learners who is new in this field. Everyone should have an clear idea how Facebook, Instagram and other social media account can be hacked and how to be safe. This tutorial is for educational purpose only. Hacking Facebook, Instagram or any other account is a serious crime. If anyone do any illegal activity then we are not responsible for that.
To join our family, join our Telegram Group . We are trying to build a community for Linux and Cybersecurity.
For anything we always happy to help everyone on the comment section . As we know our comment section is always open to everyone. We read each and every comment and we always reply .
You may like these posts
Comments
perfect writing. all in one THANKS. this will save my life.
perfect writing. all in one THANKS. this will save my life.
Thanks for the detailed post. I read every article of KaliLinux.In. This tutorial will save my Facebook account and me
I always wait for your article. You are very knowledgeable in your field. Thanks for your this detailed post. This will save me and my Facebook account.
hi can you come in facebook
what an post sir. Other hacking blogs is not for beginners. Your language is very simple, easy to understand. Keep going.
Sir, I am not a spammer. Seriously talking that your post is awesome.
Yah everything is 100% true
i want to ask admin whether he is from bengal or not?
Yah bro! I’m Bengal. Tell me
Grate!! you can mail me from the given mail address in the about section.
Nice article boss
Have readed all your posts.. Such nice articles
Is it possible to intercept cell phone transmissions via an unmanned aerial vehicle or UAV, carefully rerouting the call to a centralized system without the individual cell phone user or smart phone user realizing what is going on? this link
This comment has been removed by a blog administrator.
I want to hack someone Facebook accounts plzz help me
Wenn Sie einen qualifizierten professionellen Hacker brauchen, der wird
Ihre Arbeit effizient erledigt Mit einer schnellen und schnellen Antwort haben Sie sich getroffen
die richtigen Hacker WEBDARK115@GMAIL.COM. Wir sind eine Gruppe deutscher Hacker aus dem Dark Web.
ANONYMITÄT: Es ist uns egal, wer du bist. Der Grund, warum wir eingestellt werden, ist zu
Erledige einfach deine Arbeit. Wir engagieren uns diskret, um das Ziel anzugreifen
Halten Sie sie von dem Hack unbewusst.
UNSERE HACKING-FÄHIGKEITEN: Kein Job ist zu groß oder zu klein oder zu schwierig.
Es gibt eine Reihe von Personen, die ihre Ziel-E-Mail-ID knacken müssen
aus vielen Gründen wie Ehemann betrügt Frau oder Frau betrügt weiter
Ehemann, Freundin betrügt Freund oder umgekehrt. Oder wichtig
Informationen mussten von der Ziel-E-Mail-Adresse oder für
aus welchem Grund auch immer Sie Ihre Ziel-E-Mail hacken möchten (Google Mail, Hotmail,
Ausblick, yahoomail usw.). Oder wenn Sie eine private Domain hacken möchten
E-Mail-Konto (geschäftliche E-Mail), Facebook, Twitter, kontaktieren Sie uns. Wirklich
Wir geben immer eine 100% ige Garantie auf jeden Job, den wir eingestellt haben
denn weil wir in der Vergangenheit in all meinen Jobs immer erfolgreich waren
Jahre und unsere Kunden können das bezeugen. Um etwas zu hacken, braucht es Zeit
Wir können jedoch schnell auf Ihren Job reagieren, je nachdem, wie
schnell und dringend brauchen Sie. Die Zeit hängt auch davon ab, was genau Sie wollen
zu hacken und wie ernst du bist. Genug Zeit mit Social Engineering
wird zum Hacken benötigt. Also, wenn Sie mich in kurzer Zeit binden wollen,
dann kontaktiere mich einfach nicht, weil ich nicht in einem hacken kann
Stunde, * sorry *. Grundsätzlich hängt die Zeit von Ihrem Glück ab. Wenn es viel Glück ist,
dann ist es möglich innerhalb einer stunde zu hacken aber wenn es in der anderen ist
Umher würde es einige Stunden dauern. Ich habe FAKE HACKERS behaupten sehen
Sie können in einer Stunde hacken, aber es gibt keinen REAL HACKER, der das sagen kann
dies (VERMEIDEN SIE SIE). Wenn Ihr Zielkonto Facebook, MySpace,
Twitter, sexuelle Konten oder andere soziale Konten usw., oder Sie möchten
Hacken Sie sich in ein Smartphone, damit Sie dessen Anrufe überwachen und lesen können
ihre Nachrichten, Chats und Aktivitäten in sozialen Konten ohne ihre
Beachten Sie, zögern Sie nicht, uns zu kontaktieren und wir hätten ein gutes Angebot! ich werde
Erkläre dir, wie ich die Arbeit erledigen werde. HACKEN EINER WEBSITE
Vielleicht möchten viele Leute ihre Zielwebsite für ihre hacken
persönliche Gründe oder Interesse. Wir sind mehr als erfahren und
erfahren darin, Websites zu hacken und Zugriff auf die Datenbank zu erhalten. Es kann sein
für Datenbankzugriff, Datenbankspeicherauszug, Zugriff auf eine bestimmte
Informationen, Verunstaltung, möchten Sie vielleicht, dass ich mich in die Gerichtsdatenbank hacke
und Löschen Sie Ihre Strafregister, vielleicht aus politischen Gründen oder
Konkurrenzunternehmen usw. Es ist uns egal, welche Art von Website Sie geben
mich zum Pen-Test. Ist es hoch oder niedrig oder mittel, ich
werde mein Möglichstes tun. Sie können uns für jede andere Art von kontaktieren
«Entführung und Angriffe». Unsere Hacking-Services sind unbegrenzt. Kontaktieren Sie uns
jetzt unter WEBDARK115@GMAIL.COM, z
Ihre endlosen Möglichkeiten.
PlPlease help me I can’t access my old account because I have lost my recovery email as well as number and I have forget it’s password please hack it
I’m pleased to recommend BILL, a private hacker for any hacking related issues of your interest. I got in contact with him when i was having problems with my cheating husband and needed help in getting evidence against him in court, Bill helped me hack into my husband’s phone and in no time i started seeing his chats and messages, call records including access to his recently deleted conversations. I»m so glad i got in contact with Bill, He is also into various jobs such as Facebook hacking, whats-app hacking, phone hacking, snapchat, Instagram, we-chat, phone text messages, hangouts and so on.. You can contact him by email: billhackwizard @ gmail .com, text him on: +1(314) 230-8385, you can also chat him up on whats-app:- +1(314) 635 7319., you should contact him today and see for yourself, remember to tell him Sofia referred you.
Источник