- Как сгенерировать SSH-ключ для доступа на сервер
- Введение
- SSH-ключ для Linux/MacOS
- SSH-ключ для Windows
- Заключение
- What is an SSH KEY?
- How to Create an SSH Key
- Generate an SSH Key on Mac and Linux
- Generate an SSH Key on Windows
- Windows Linux Subsystem
- Summary
- Manually generating your SSH key in macOS
- About Terminal
- Generating an SSH key
- Importing your SSH key
- Troubleshooting
- What are my next steps?
- RTFM.WIKI
- Инструменты пользователя
- Инструменты сайта
- Боковая панель
- Навигация
- Линкшэринг
- ALARM!
- Добавить новую страницу
- Реклама
- Содержание
- SSH: подключение по ключу без пароля на примере macOS
- Шаг 1. Создать пару ключей
- Шаг 2. Скопировать открытый ключ на удаленный хост
- Долгий путь
- ssh-copy-id
- cat + ssh
- Шаг 3. Локальный конфиг SSH и тест подключение
- Generating a new SSH key and adding it to the ssh-agent
- Help us make these docs great!
Как сгенерировать SSH-ключ для доступа на сервер
Введение
Использование SSH-ключей — простой и надежный способ обеспечения безопасности соединения с сервером. В отличие от пароля, взломать SSH-ключ практически невозможно. Сгенерировать SSH-ключ очень просто.
SSH-ключ для Linux/MacOS
Откройте терминал и выполните команду:
На консоль будет выведен следующий диалог:
Нажмите на клавишу Enter. Далее система предложит ввести кодовую фразу для дополнительной защиты SSH-подключения:
Этот шаг можно пропустить. При ответе на этот и следующий вопрос просто нажмите клавишу Enter.
После этого ключ будет создан, а на консоль будет выведено следующее сообщение:
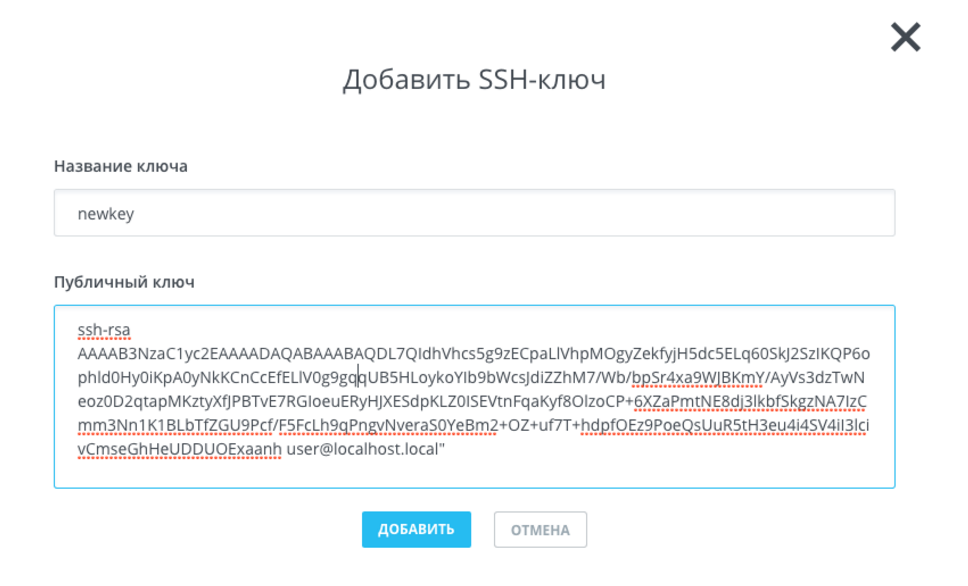
Далее выполните в терминале команду:
На консоль будет выведен ключ. Скопируйте его и вставьте в соответствующее поле:
Нажмите на кнопку «Добавить».
Добавив ключ, выполните в терминале команду:
После этого соединение с сервером будет установлено. Вводить пароль при этом не потребуется.
SSH-ключ для Windows
В OC Windows подключение к удаленным серверам по SSH возможно, например, с помощью клиента Putty. Скачать его можно здесь (ссылка взята с официального сайта). Putty не требует установки — чтобы начать с ним работать, достаточно просто распаковать скачанный архив.
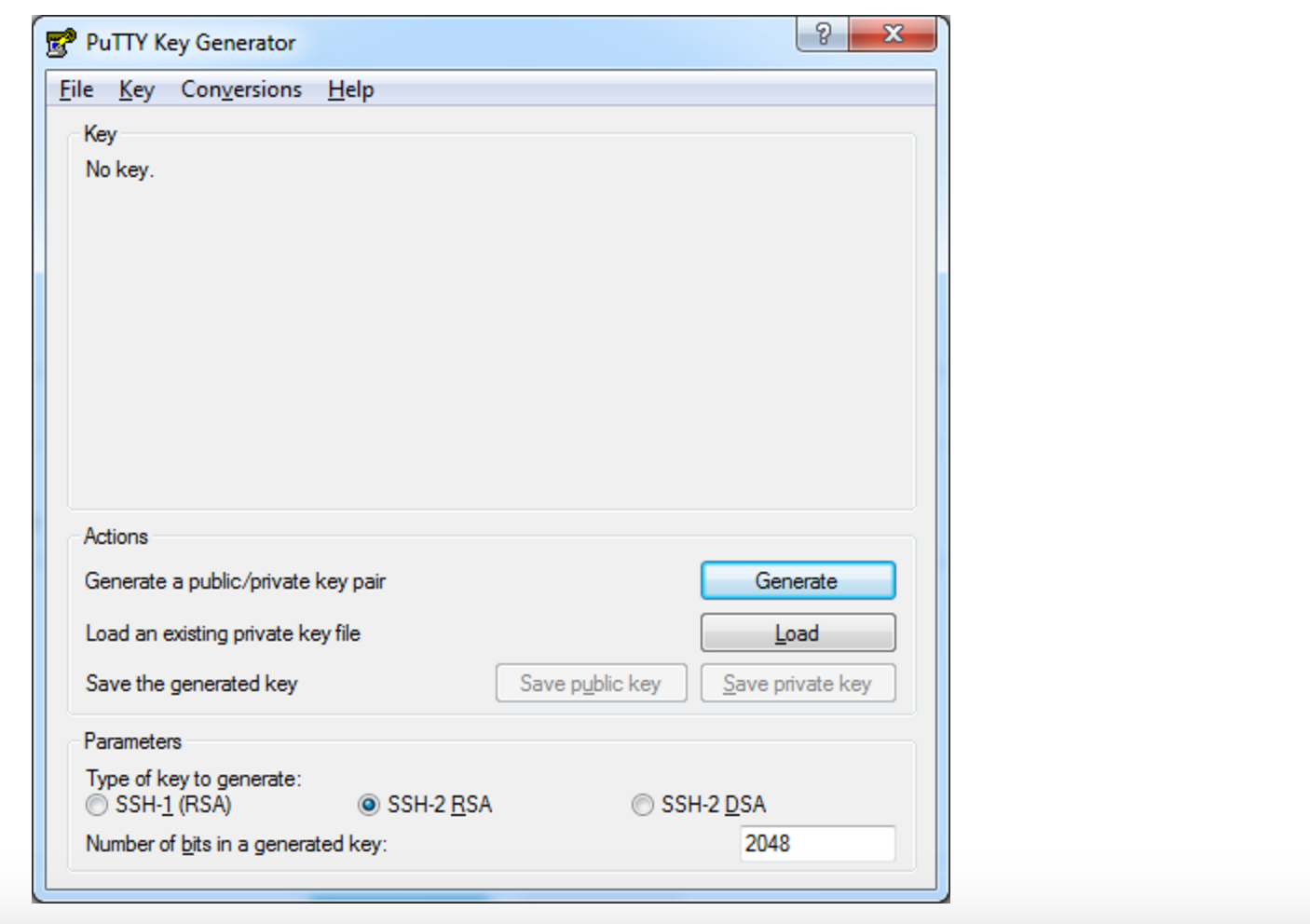
По завершении распаковки запустите файл puttygen.exe.
Выберите тип ключа SSH-2 RSA и длину 2048 бит, а затем нажмите на кнопку Generate:
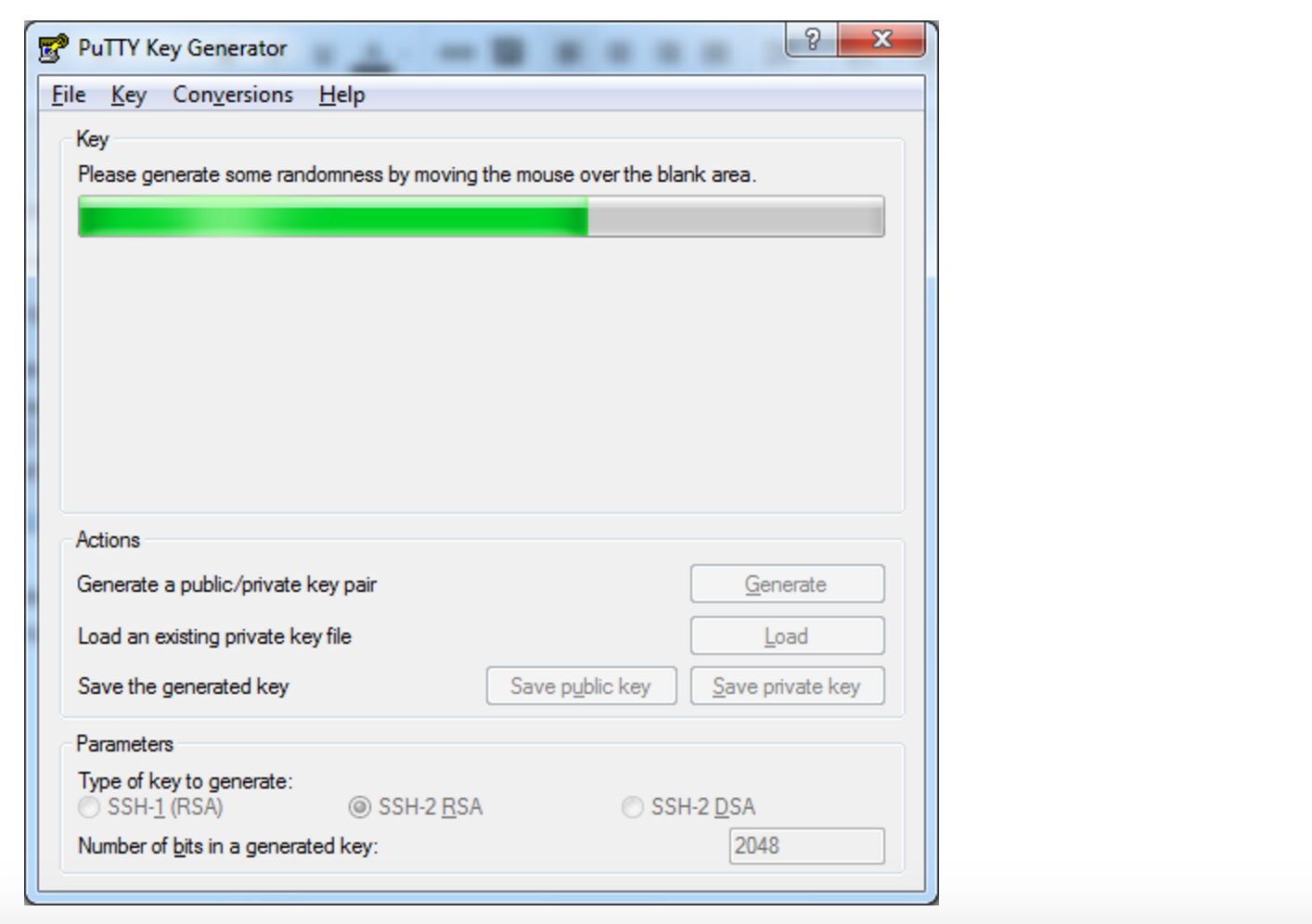
Во время генерации водите курсором в пустой области окна (это нужно для создания псевдослучайности):
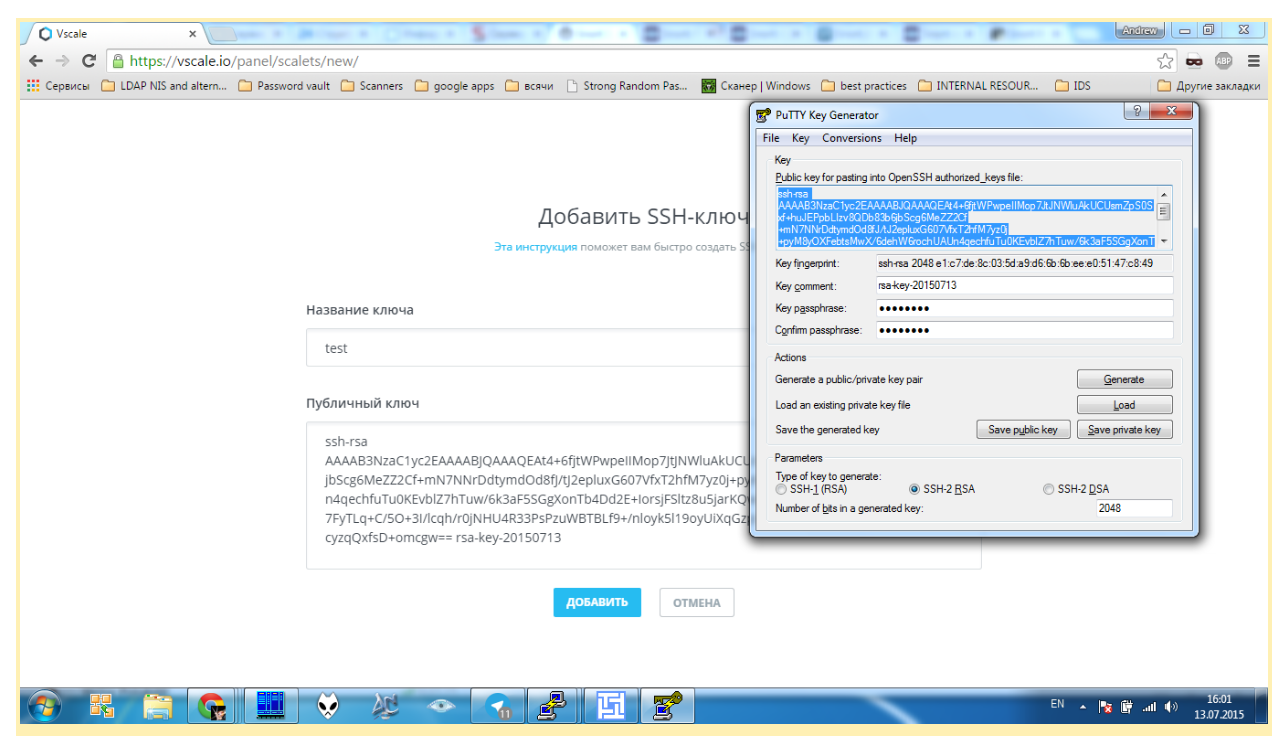
Сохраните сгенерированную пару ключей на локальной машине (кнопки Save public key и Save private key).
Скопируйте сгененированный ключ и вставьте его в соответствующее поле:
Заключение
В этой инструкции мы рассмотрели, как создать шифрованный протокол для связи с сервером: сгенерировали SSH-ключ для Linux/MacOS и Windows. Теперь вы можете входить в систему без пароля учетной записи.
Источник
What is an SSH KEY?
An SSH key is an access credential for the SSH (secure shell) network protocol. This authenticated and encrypted secure network protocol is used for remote communication between machines on an unsecured open network. SSH is used for remote file transfer, network management, and remote operating system access. The SSH acronym is also used to describe a set of tools used to interact with the SSH protocol.
SSH uses a pair of keys to initiate a secure handshake between remote parties. The key pair contains a public and private key. The private vs public nomenclature can be confusing as they are both called keys. It is more helpful to think of the public key as a «lock» and the private key as the «key». You give the public ‘lock’ to remote parties to encrypt or ‘lock’ data. This data is then opened with the ‘private’ key which you hold in a secure place.
How to Create an SSH Key
SSH keys are generated through a public key cryptographic algorithm, the most common being RSA or DSA. At a very high level SSH keys are generated through a mathematical formula that takes 2 prime numbers and a random seed variable to output the public and private key. This is a one-way formula that ensures the public key can be derived from the private key but the private key cannot be derived from the public key.
SSH keys are created using a key generation tool. The SSH command line tool suite includes a keygen tool. Most git hosting providers offer guides on how to create an SSH Key.
Generate an SSH Key on Mac and Linux
Both OsX and Linux operating systems have comprehensive modern terminal applications that ship with the SSH suite installed. The process for creating an SSH key is the same between them.
1. execute the following to begin the key creation
This command will create a new SSH key using the email as a label
2. You will then be prompted to «Enter a file in which to save the key.»
You can specify a file location or press “Enter” to accept the default file location.
3. The next prompt will ask for a secure passphrase.
A passphrase will add an additional layer of security to the SSH and will be required anytime the SSH key is used. If someone gains access to the computer that private keys are stored on, they could also gain access to any system that uses that key. Adding a passphrase to keys will prevent this scenario.
At this point, a new SSH key will have been generated at the previously specified file path.
4. Add the new SSH key to the ssh-agent
The ssh-agent is another program that is part of the SSH toolsuite. The ssh-agent is responsible for holding private keys. Think of it like a keychain. In addition to holding private keys it also brokers requests to sign SSH requests with the private keys so that private keys are never passed around unsecurly.
Before adding the new SSH key to the ssh-agent first ensure the ssh-agent is running by executing:
Once the ssh-agent is running the following command will add the new SSH key to the local SSH agent.
The new SSH key is now registered and ready to use!
Generate an SSH Key on Windows
Windows environments do not have a standard default unix shell. External shell programs will need to be installed for to have a complete keygen experience. The most straight forward option is to utilize Git Bash. Once Git Bash is installed the same steps for Linux and Mac can be followed within the Git Bash shell.
Windows Linux Subsystem
Modern windows environments offer a windows linux subsystem. The windows linux subsystem offers a full linux shell within a traditional windows environment. If a linux subsystem is available the same steps previously discussed for Linux and Mac can be followed with in the windows linux subsystem.
Summary
SSH keys are used to authenticate secure connections. Following this guide, you will be able to create and start using an SSH key. Git is capable of using SSH keys instead of traditional password authentication when pushing or pulling to remote repositories. Modern hosted git solutions like Bitbucket support SSH key authentication.
Источник
Manually generating your SSH key in macOS
You generate an SSH key through macOS by using the Terminal application. Once you upload a valid public SSH key, the Triton Compute Service uses SmartLogin to copy the public key to any new SmartMachine you provision.
Joyent recommends RSA keys because the node-manta CLI programs work with RSA keys both locally and with the ssh agent. DSA keys will work only if the private key is on the same system as the CLI, and not password-protected.
About Terminal
Terminal is the terminal emulator which provides a text-based command line interface to the Unix shell of macOS.
To open the macOS Terminal, follow these steps:
- In Finder, choose Utilities from the Applications folder.
- Find Terminal in the Utilities listw.
- Open Terminal.
The Terminal window opens with the commandline prompt displaying the name of your machine and your username.
Generating an SSH key
An SSH key consists of a pair of files. One is the private key, which should never be shared with anyone. The other is the public key. The other file is a public key which allows you to log into the containers and VMs you provision. When you generate the keys, you will use ssh-keygen to store the keys in a safe location so you can bypass the login prompt when connecting to your instances.
To generate SSH keys in macOS, follow these steps:
Enter the following command in the Terminal window.
This starts the key generation process. When you execute this command, the ssh-keygen utility prompts you to indicate where to store the key.
Press the ENTER key to accept the default location. The ssh-keygen utility prompts you for a passphrase.
You will need to enter the passphrase a second time to continue.
After you confirm the passphrase, the system generates the key pair.
Your private key is saved to the id_rsa file in the .ssh directory and is used to verify the public key you use belongs to the same Triton Compute Service account.
| Never share your private key with anyone! |
|---|
Your public key is saved to the id_rsa.pub ;file and is the key you upload to your Triton Compute Service account. You can save this key to the clipboard by running this:
Importing your SSH key
Now you must import the copied SSH key to the portal.
- After you copy the SSH key to the clipboard, return to your account page.
- Choose to Import Public Key and paste your SSH key into the Public Key field.
- In the Key Name field, provide a name for the key. Note: although providing a key name is optional, it is a best practice for ease of managing multiple SSH keys.
- Add the key. It will now appear in your table of keys under SSH.
Troubleshooting
You may see a password prompt like this:
This is because:
- You did not enter the correct passphrase.
- The private key on your Macintosh ( id_rsa ) does not match the public key stored with your Triton Compute Service account.
- The public key was not entered correctly in your Triton account.
What are my next steps?
In order to use the Terminal to create instances, set up triton and CloudAPI as well as the triton-docker commandline tool.
Источник
RTFM.WIKI
Ordnung muß sein. Ordnung über alles (18+)
Инструменты пользователя
Инструменты сайта
Боковая панель
Навигация
Линкшэринг
socialite Display:icon facebook twitter
ALARM!
Добавить новую страницу
Реклама
Содержание
SSH: подключение по ключу без пароля на примере macOS
Минимум теории и максимум хауту. За теорией лучше обратиться на сайт wikipedia или на ssh.com
Шаг 1. Создать пару ключей
Нужно создать пару ключей: приватный (закрытый) ключ и публичный (открытый) ключ. Приватный ключ никогда никуда никому не передавать. Публичный ключ можно показывать всем.
Пр желании можно дать ключу другое имя (ключ -f ), например id_rsa_server_vps13.
Следующий пункт passphrase. Это парольная фраза или проще говоря пароль для ключа.
Минусы. Его нужно будет вводить каждый раз, когда используется ключ.
Очевидный плюс. Если файл окажется в чужих руках без парольной фразы использовать его не получится. Ну и не стоит использовать пароли admin111 или qwerty123.
Шаг 2. Скопировать открытый ключ на удаленный хост
Как всегда в unix есть множество вариантов для этого.
Долгий путь
В macOS можно скопировать содержимое файла в буфер обмена с помощью pbcopy
Подключаемся к удаленному серверу, переходим в директорию .ssh и открываем (или создаем) файл authorized_keys.
Добавляем ключ из буфера обмена.
Кстати каждый ключ должен быть на отдельной строке. И никаких пустых строк между ключами.
ssh-copy-id
Начиная с Sierra утилита уже есть в составе системы и не нужно ставить с github или через homebrew.
или с указанием имени ключа
cat + ssh
Шаг 3. Локальный конфиг SSH и тест подключение
Добавим локальный файл конфигурации для SSH клиента в файл
Особый интерес представляют опции UseKeychain и AddKeysToAgent.
Пароль приватного ключа можно хранить в «Связке ключей» (Apple KeyChain). Один раз добавили и всё — больше никогда не надо вводить никаких паролей для подключения по ssh.
В каком-то релизе (Sierra? у меня не Linux, чтобы отслеживать это) всё сломали и Terminal теперь по-умолчанию не использует keychain.
Опция AddKeysToAgent вышла в OpenSSH 7.2 еще в 2016 году, но я узнал про нее только сейчас.
В клиент ssh добавлена опция AddKeysToAgent, управляющая передачей в ssh-agent закрытого ключа, используемого в процессе аутентификации. Опция может принимать значения ‘yes’, ‘no’, ‘ask’, и ‘confirm’ (по умолчанию ‘no’)
Что еще важного в ссылках выше?
Буду рад если кто-то более подробно разобрался в данном вопросе и дополнит заметку.
Источник
Generating a new SSH key and adding it to the ssh-agent
After you’ve checked for existing SSH keys, you can generate a new SSH key to use for authentication, then add it to the ssh-agent.
About SSH key generation
If you don’t already have an SSH key, you must generate a new SSH key to use for authentication. If you’re unsure whether you already have an SSH key, you can check for existing keys. For more information, see «Checking for existing SSH keys.»
If you want to use a hardware security key to authenticate to GitHub, you must generate a new SSH key for your hardware security key. You must connect your hardware security key to your computer when you authenticate with the key pair. For more information, see the OpenSSH 8.2 release notes.
If you don’t want to reenter your passphrase every time you use your SSH key, you can add your key to the SSH agent, which manages your SSH keys and remembers your passphrase.
Generating a new SSH key
Open Terminal Terminal Git Bash .
Paste the text below, substituting in your GitHub email address.
Note: If you are using a legacy system that doesn’t support the Ed25519 algorithm, use:
This creates a new SSH key, using the provided email as a label.
When you’re prompted to «Enter a file in which to save the key,» press Enter. This accepts the default file location.
At the prompt, type a secure passphrase. For more information, see «Working with SSH key passphrases.»
Adding your SSH key to the ssh-agent
Before adding a new SSH key to the ssh-agent to manage your keys, you should have checked for existing SSH keys and generated a new SSH key. When adding your SSH key to the agent, use the default macOS ssh-add command, and not an application installed by macports, homebrew, or some other external source.
Start the ssh-agent in the background.
Depending on your environment, you may need to use a different command. For example, you may need to use root access by running sudo -s -H before starting the ssh-agent, or you may need to use exec ssh-agent bash or exec ssh-agent zsh to run the ssh-agent.
If you’re using macOS Sierra 10.12.2 or later, you will need to modify your
/.ssh/config file to automatically load keys into the ssh-agent and store passphrases in your keychain.
First, check to see if your
/.ssh/config file exists in the default location.
If the file doesn’t exist, create the file.
/.ssh/config file, then modify the file to contain the following lines. If your SSH key file has a different name or path than the example code, modify the filename or path to match your current setup.
Note: If you chose not to add a passphrase to your key, you should omit the UseKeychain line.
Note: If you see an error like this
add an additional config line to your Host * section:
Add your SSH private key to the ssh-agent and store your passphrase in the keychain. If you created your key with a different name, or if you are adding an existing key that has a different name, replace id_ed25519 in the command with the name of your private key file.
Note: The -K option is Apple’s standard version of ssh-add , which stores the passphrase in your keychain for you when you add an SSH key to the ssh-agent. If you chose not to add a passphrase to your key, run the command without the -K option.
If you don’t have Apple’s standard version installed, you may receive an error. For more information on resolving this error, see «Error: ssh-add: illegal option — K.»
Add the SSH key to your account on GitHub. For more information, see «Adding a new SSH key to your GitHub account.»
If you have GitHub Desktop installed, you can use it to clone repositories and not deal with SSH keys.
Ensure the ssh-agent is running. You can use the «Auto-launching the ssh-agent» instructions in «Working with SSH key passphrases», or start it manually:
Add your SSH private key to the ssh-agent. If you created your key with a different name, or if you are adding an existing key that has a different name, replace id_ed25519 in the command with the name of your private key file.
Add the SSH key to your account on GitHub. For more information, see «Adding a new SSH key to your GitHub account.»
Start the ssh-agent in the background.
Depending on your environment, you may need to use a different command. For example, you may need to use root access by running sudo -s -H before starting the ssh-agent, or you may need to use exec ssh-agent bash or exec ssh-agent zsh to run the ssh-agent.
Add your SSH private key to the ssh-agent. If you created your key with a different name, or if you are adding an existing key that has a different name, replace id_ed25519 in the command with the name of your private key file.
Add the SSH key to your account on GitHub. For more information, see «Adding a new SSH key to your GitHub account.»
Generating a new SSH key for a hardware security key
If you are using macOS or Linux, you may need to update your SSH client or install a new SSH client prior to generating a new SSH key. For more information, see «Error: Unknown key type.»
Insert your hardware security key into your computer.
Open Terminal Terminal Git Bash .
Paste the text below, substituting in the email address for your account on GitHub.
Note: If the command fails and you receive the error invalid format or feature not supported, you may be using a hardware security key that does not support the Ed25519 algorithm. Enter the following command instead.
When you are prompted, touch the button on your hardware security key.
When you are prompted to «Enter a file in which to save the key,» press Enter to accept the default file location.
When you are prompted to type a passphrase, press Enter.
Add the SSH key to your account on GitHub. For more information, see «Adding a new SSH key to your GitHub account.»
Help us make these docs great!
All GitHub docs are open source. See something that’s wrong or unclear? Submit a pull request.
Источник