- how2: Using GPG on macOS without GPGTools
- GPG Setup
- Connecting to GitHub
- Troubleshooting
- GPGTools
- One simple package with everything you need, to protect your emails and files.
- GPG Mail
- GPG Keychain
- GPG Services
- MacGPG
- GPG Suite at a glance
- It’s all about the keys
- Create your own key
- Upload your key to a key server so your friends can find it
- Already an expert?
- See all your keys
- The toolbar
- More options
- Add additional email addresses
- Write secure messages with Mail
- The lock button
- The sign button
- Choose between PGP and S/MIME
- Receive secure messages with Mail
- Signed messages
- Encrypted or signed attachments
- Sometimes things go wrong
- Find out what went wrong
- How to use GnuPG for encrypting files on MacOS
- Configuration Files
- Gpg для mac os
- Download
- Source code releases
- GnuPG binary releases
- End-of-life announcements
how2: Using GPG on macOS without GPGTools
I don’t like GPGTools. I want GPG on macOS. Every tutorial has some obsolete part. Here’s what I did.
GPGTools installs a lot of things that I don’t want to use. I just want to sign my commits on GitHub and save my GPG key in macOS keychain.
There are two main dependencies to achieve that, gnupg contains the GPG tools to generate keys and sign things, as well as an agent to do agent things; and pinentry-mac which is the part of GPGTools that prompts for your key password and stores it on the OS keychain.
GPG Setup
Before anything, install homebrew.
After that, install the dependencies:
Then, let’s generate your first key. I recommend using RSA and RSA, a key size of 4096, and not having the key expire. Remember to choose a strong password.
Now you need to configure gpg-agent to use pinentry-mac by creating a file
Then, sign a test message so pinentry-mac can store your password in the keychain:
This should open a dialog prompting your password. Remember to check “Save in Keychain”.
Connecting to GitHub
First, copy your private key to add to GitHub:
Second, configure your git environment to use signed commits. I’ve done it globally. First obtain your public GPG keys:
Then configure git:
And finally, commit something with the-S argument to make sure it’s signed:
Troubleshooting
Things you can try if things are not working:
Источник
GPGTools
One simple package
with everything you need,
to protect your emails and files.
By downloading, you agree to our Terms of Distribution
Use GPG Suite to encrypt, decrypt, sign and verify files or messages. Manage your GPG Keychain with a few simple clicks and experience the full power of GPG easier than ever before.
GPG Mail
integrates the full power of GPG seamlessly into macOS Mail. Protecting your emails has never been so simple.
GPG Keychain
allows you to manage your OpenPGP keys. Create new keys, modify existing ones and import your colleagues’ keys from a key server.
GPG Services
integrates the power of GPG into almost any application via the macOS Services context menu. It allows you to encrypt/decrypt, sign/verify text selections, files, folders and much more.
MacGPG
is the underlying encryption engine of GPG Suite. If you are familiar with the command line, you can use its raw powers. Based on the latest version of GnuPG.
GPG Suite at a glance
It’s all about the keys
To use GPG to encrypt and verify mails or files you and your friends need GPG keys.
GPG Keychain lets you manage your own keys and find and import keys of your friends.
Create your own key
Enter your name and the email address you want to use your key with and you are ready to go.
You don’t have to bother with more advanced settings, we set good defaults for you.
Upload your key to a key server so your friends can find it
When creating a key, you have the option to upload it to a key server, which makes it very easy for your friends to find and import it.
Already an expert?
When creating a key, you can enable the advanced view, which lets you choose key size, expiration date and algorithm to use for your keys. Have full control over your keys.
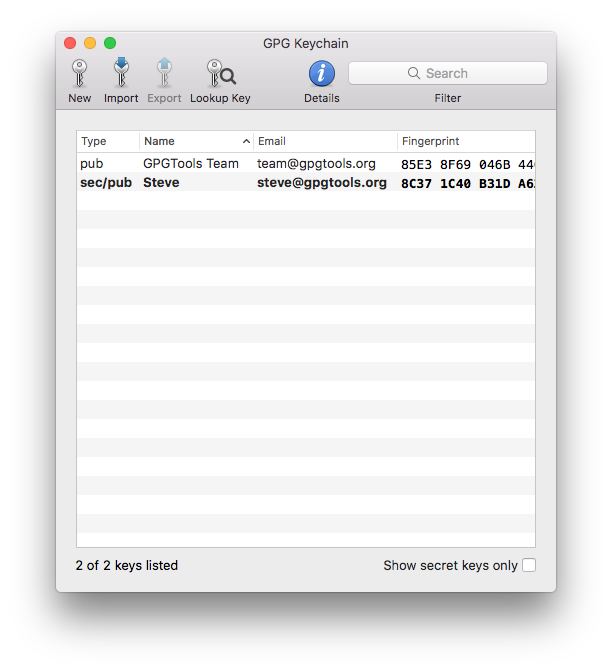
See all your keys
The main window of GPG Keychain shows you all your keys and the keys of your friends.
Enable the «Show secret keys only» checkbox, to see only the keys you created.
The toolbar
gives you quick access to the most important actions. Create a new key, import or export an existing key, or search for a specific key using the search field.
More options
Select a key and right-click on it to bring up a context menu, letting you send your key to a key server, update or manage the details of your key.
Add additional email addresses
Select your key and press the info button in the toolbar to add additional email addresses.
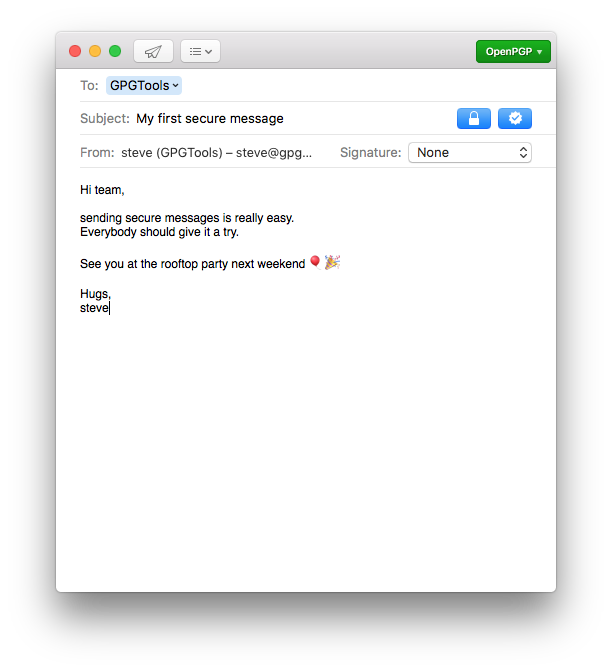
Write secure messages with Mail
After installing GPG Suite, you’ll see two new buttons when writing a new email: the lock button and the sign button next to it.
The lock button
Activate the lock button to encrypt an email. Only you and the recipient will be able to read the contents of your message. Toggle between encrypting and not encrypting your email pressing ⌥ ⌘ Y.
The sign button
Activate the sign button to sign an email. The recipient will be able to tell, that the email came from you and whether or not it was tampered with in any way.
Toggle between signing and not signing your email pressing ⌥ ⌘ X.
Choose between PGP and S/MIME
Using the security method indicator in the upper right corner, you can quickly switch between PGP and S/MIME. This is very handy if you use both.
Press ⌥ ⌘ P to activate PGP or ⌥ ⌘ S to activate S/MIME.
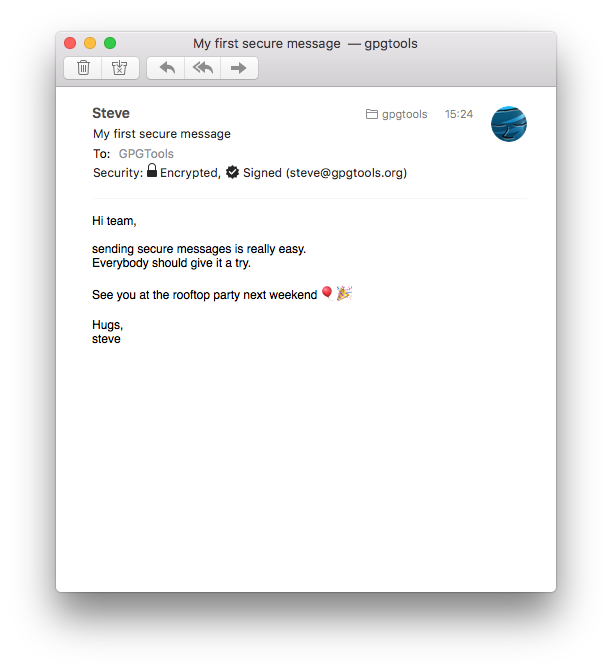
Receive secure messages with Mail
The «Security:» header will tell you, if the message you’ve received was signed or encrypted.
If the message was successfully decrypted, you’ll see an open lock. If the signature of the message is valid, you’ll see a star icon with a checkmark.
Make sure to click «Details» to see the security header.
Signed messages
will show the email address associated with your friend’s key that was used to sign this message.
Click on the signature icon to see more infos regarding the key and signature.
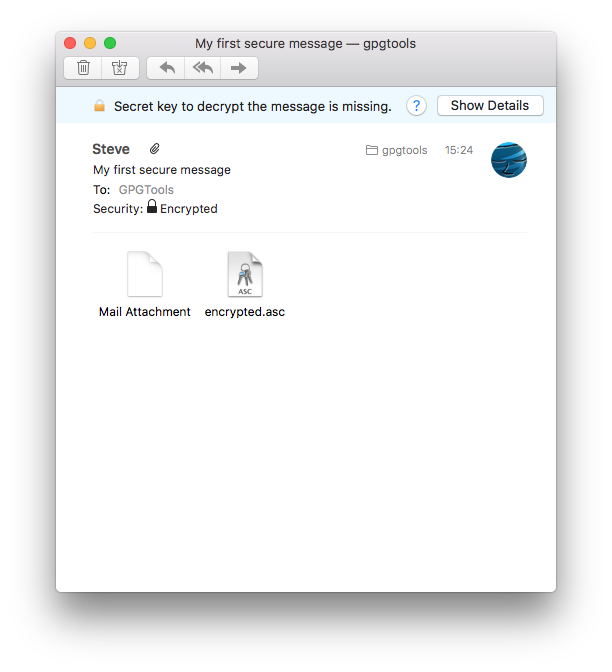
Encrypted or signed attachments
If the message contains encrypted or signed attachments, they will be automatically decrypted and verified. The attachments will look like any other non-encrypted attachments to you, while still being protected.
Sometimes things go wrong
It might happen that someone encrypted a mail for another recipient but mistakenly sent it to you and so you’re not able to read it. Or a signed message you’re receiving was modified without your knowledge. Or anything else could have gone wrong. In these cases we’re trying to be as helpful as possible by providing good explanations of what happened.
Find out what went wrong
Whenever we detect that something’s not right, you’ll see a banner with an error message, letting you know what the problem is.
To get detailed information about a problem, click on «Show Details» which contains a better description of the problem and possible solutions to it.
Источник
How to use GnuPG for encrypting files on MacOS
GnuPG is an implementation of OpenPGP standard.
People use it for public-private key encryption.
It is one of the tools that Edward Snowden used to uncover the secrets of the NSA.
GnuPG is a complex tool.
I will only show you how to use it for file encryption without using keys.
And i will show some configuration files to make commands more simple.
I assume you know how to use a Unix console and have Homebrew package manager installed.
First you should install GnuPG with Homebrew:
Exit fullscreen mode
This will install GnuPG version 2.2.19
Exit fullscreen mode
You should be able to see something like this:
Exit fullscreen mode
Now we can use GnuPG.
I have a text file named test.txt .
It contains this text:
Exit fullscreen mode
To encrypt test.txt file i will use this command:
Exit fullscreen mode
This command will ask you a password and create an encrypted version of test.txt file and save as test.asc file.
-c means use symmetric cipher so you will enter a password for that file.
—armor is for a readable ascii output so you can easily copy/paste it.
—cipher-algo AES256 is for using AES-256 cipher. (U.S. government using it so why not)
—no-symkey-cache means GnuPG will not remember password. If you don’t enter this —decrypt command won’t ask your passphrase.
—output test.asc means save encrypted file as test.asc
Now i have test.asc (encrypted test.txt ).
It contains this text:
Exit fullscreen mode
As you can see it is readable but meaningless.
This is because of the —armor option we added to the command.
To decrypt test.asc file i will use this command:
Exit fullscreen mode
This command will ask you the password you used and if it is correct it will create a decrypted file as test1.txt .
Now i have test1.txt .
It contains this text:
Exit fullscreen mode
Configuration Files
There are some configuration files im using.
I will show you how to create these files.
These configuration files are not neccessary but they are shortening the commands i use everyday.
GnuPG creates a folder for itself.
It is normally in your $HOME folder named .gnupg .
It contains caches, your keyrings, your configuration files.
So go there and create a file named gpg.conf .(if it doesn’t exists)
Write these in gpg.conf :
Exit fullscreen mode
Now create another configuration file named gpg-agent.conf .(gpg-agent comes with gnupg installation)
Write these in gpg-agent.conf :
Exit fullscreen mode
Now actually you should restart your pgp-agent program.
Kill it with this command:
Exit fullscreen mode
It will launch automatically when you call gpg .
If it doesn’t you can run this command to launch it:
Exit fullscreen mode
But i think you won’t need it.
Anyway now we don’t need to add any options. We can simply run our command like this:
Exit fullscreen mode
This command will automatically create a file named test.txt.asc with cipher aes-256 , also in ascii format and won’t remember the password .
To decrypt it simply enter this command:
Exit fullscreen mode
It will create a decrypted file as text.txt .
This is one of the ways to use GnuPG.
As i said before it does so much more.
You can look for more info here at GnuPG
Источник
Gpg для mac os
Download
Note that you may also download the GNU Privacy Guard from a mirror site close to you. See our list of mirrors. The table below provides links to the location of the files on the primary server only.
Source code releases
These are the canonical release forms of GnuPG. To use them you need to build the binary version from the provided source code. For Unix systems this is the standard way of installing software. For GNU/Linux distributions are commonly used (e.g. Debian, Fedora, RedHat, or Ubuntu) which may already come with a directly installable packages. However, these version may be older so that building from the source is often also a good choice. Some knowledge on how to compile and install software is required.
The table lists the different GnuPG packages, followed by required libraries, required tools, optional software, and legacy versions of GnuPG. For end-of-life dates see further down.
| Name | Version | Date | Size | Tarball | Signature |
|---|---|---|---|---|---|
| GnuPG | 2.3.2 | 2021-08-24 | 7411k | download | download |
| GnuPG (LTS) | 2.2.32 | 2021-10-06 | 7043k | download | download |
| Libgpg-error | 1.42 | 2021-03-22 | 951k | download | download |
| Libgcrypt | 1.9.4 | 2021-08-22 | 3163k | download | download |
| Libgcrypt (LTS) | 1.8.8 | 2021-06-02 | 2917k | download | download |
| Libksba | 1.6.0 | 2021-06-10 | 646k | download | download |
| Libassuan | 2.5.5 | 2021-03-22 | 558k | download | download |
| ntbTLS | 0.2.0 | 2020-08-27 | 340k | download | download |
| nPth | 1.6 | 2018-07-16 | 293k | download | download |
| Pinentry | 1.2.0 | 2021-08-25 | 486k | download | download |
| GPGME | 1.16.0 | 2021-06-24 | 1678k | download | download |
| Scute | 1.7.0 | 2021-01-07 | 831k | download | download |
| GPA | 0.10.0 | 2018-10-16 | 745k | download | download |
| GnuPG 1.4 | 1.4.23 | 2018-06-11 | 3661k | download | download |
GnuPG distributions are signed. It is wise and more secure to check out for their integrity.
- Pinentry is a collection of passphrase entry dialogs which is required for almost all usages of GnuPG.
- GPGME is the standard library to access GnuPG functions from programming languages.
- Scute is a PKCS#11 provider on top of GnuPG.
- GPA is a graphical frontend to GnuPG.
- GnuPG 1.4 is the old, single binary version which still support the unsafe PGP-2 keys. This branch has no dependencies on the above listed libraries or the Pinentry. However, it lacks many modern features and will receive only important updates.
GnuPG binary releases
In general we do not distribute binary releases but leave that to the common Linux distributions. However, for some operating systems we list pointers to readily installable releases. We cannot guarantee that the versions offered there are current. Note also that some of them apply security patches on top of the standard versions but keep the original version number.
| OS | Where | Description |
|---|---|---|
| Windows | Gpg4win | Full featured Windows version of GnuPG |
| download sig | Simple installer for the current GnuPG | |
| download sig | Simple installer for GnuPG 1.4 | |
| OS X | Mac GPG | Installer from the gpgtools project |
| GnuPG for OS X | Installer for GnuPG | |
| Debian | Debian site | GnuPG is part of Debian |
| RPM | rpmfind | RPM packages for different OS |
| Android | Guardian project | Provides a GnuPG framework |
| VMS | antinode.info | A port of GnuPG 1.4 to OpenVMS |
| RISC OS | home page | A port of GnuPG to RISC OS |
End-of-life announcements
We announce the end-of-life date for a current stable version at the time a new stable version is released. We maintain old branches for at least two years. For GnuPG 2.2 we consider 2.1.0 as the birth of this new stable branch. For most other packages we don’t maintain branches and thus there is no end-of-life; always use the latest version.
Источник