- Top 21 Operating Systems for Ethical Hacking and Pen Testing (2021 List)
- Favourite Operating Systems of hackers :
- 1. Kali Linux
- 2. BackBox
- 3. Parrot Security OS
- 4. Live Hacking OS
- 5. DEFT Linux
- 6. Samurai Web Testing Framework
- 7. Network Security Toolkit
- 8. Bugtraq-II
- 9. NodeZero
- 10. Pentoo
- 11. BlackBuntu
- 12. Cyborg Hawk Linux
- 13. Knoppix STD
- 14. Weakerthan
- 15. BlackArch Linux
- 16. Matriux Linux
- 17. Dracos Linux
- 18. Fedora Security Lab
- 19. Caine
- 20. ArchStrike
- 21. URIX OS
- 13 Best Hacking Tools Of 2019 For Windows, Linux, macOS
- 13 Best Hacking Software for Windows, Linux, and Mac
- 1. Metasploit | Best collection of exploit tools
- Supported platforms and download:
- 2. Acunetix WVS | Vulnerability Scanner
- Supported platforms and download:
- 3. Nmap | Port scanner tool
- Supported platforms and download:
- 4. Wireshark | Packet analyzer
- Supported platforms and download:
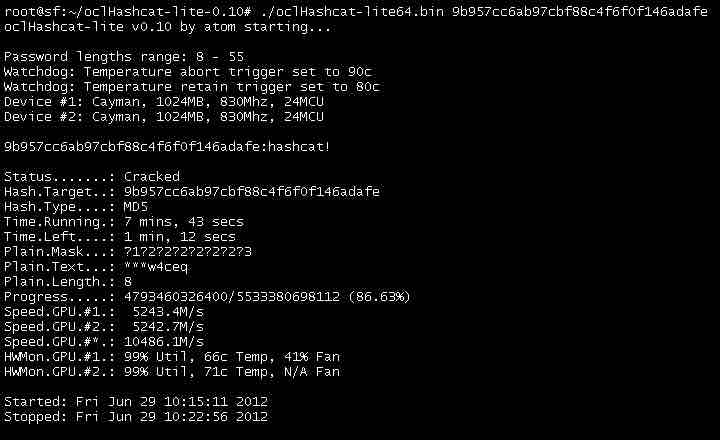
- 5. oclHashcat | Password cracking tool
- Supported platforms and download:
- 6. Nessus | Vulnerability Scanner
- Supported platforms and download:
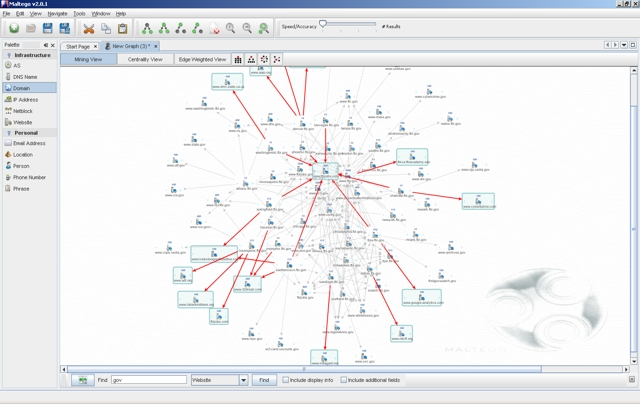
- 7. Maltego | Forensics platform
- Supported platforms and download:
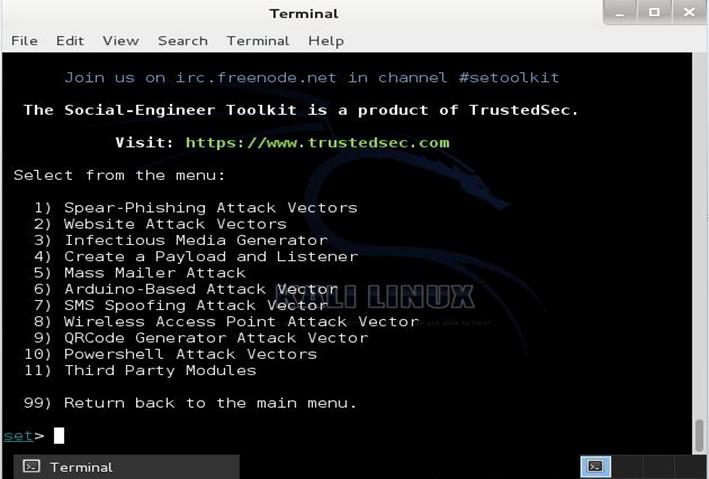
- 8. Social-Engineer Toolkit
- Supported platforms and download:
- 9. Netsparker | Web app scanner
- Supported platforms and download:
- 10. w3af | Web app scanner
- Supported platforms and download:
- 11. John The Ripper
- Supported platforms and download:
- 12. Aircrack-ng | Password cracking tool
- Supported platforms and download:
- 13. Ghidra | Reverse Engineering Tool
- Supported platforms and download:
- Other top hacking and security tools of 2019 in multiple categories:
Top 21 Operating Systems for Ethical Hacking and Pen Testing (2021 List)
Best Operating Systems For Ethical Hacking And Penetration Testing
Like to learn about computer and network security or to find vulnerabilities in your network or are you searching for best-operating systems for ethical hacking and pen testing or like to know which is the favorite operating system of hackers? — then stop! Here is the list of most widely using infamous ethical hacking operating systems or we can say digital forensic tools.
Almost all the best ethical hacking operating systems for security experts are based on Linux kernel, so favorite operating systems of all types of hackers are always Linux — though security-focused operating system is a security analyst’s best friend. But also keep in mind that, simply having these operating systems doesn’t make anyone a security expert or hacker — you should also learn some essential programming languages to enrich your knowledge in this field.
Favourite Operating Systems of hackers :
So check out 21 best Linux hacking os using for pen testing and other security measures.
1. Kali Linux
Kali Linux maintained and funded by Offensive Security Ltd. is one of the well-known and favorite ethical hacking operating systems used by hackers and security professionals. Kali is a Debian-derived Linux distribution designed fReal hackers or digital forensics and penetration testing. It was developed by Mati Aharoni and Devon Kearns of Offensive Security through the rewrite of BackTrack, their previous forensics Linux distribution based on Ubuntu.
Apart from desktop support, Kali Linux also has a dedicated project set-aside for compatibility and porting to specific Android devices, called Kali Linux NetHunter. When comes to security tools, this top ethical hacking operating system is equipped with 600+ preinstalled pen testing tools and they are frequently updated and are offered for different platforms like ARM and VMware. Now Kali Linux is based on a rolling release model.
2. BackBox
BackBox is an Ubuntu-based penetration testing Linux distribution. It provides penetration test and security assessment oriented providing a network and informatics systems analysis toolkit along with a complete set of other tools required for ethical hacking and security testing.
It includes some of the most used security and analysis Linux tools to help out security experts from stress tests to sniffing including vulnerability assessment, computer forensic analysis, and exploitation.
3. Parrot Security OS
Parrot Security OS (or ParrotSec) is a GNU/LINUX distribution based on Debian. This Linux distribution for hackers is built in order to perform penetration testing, vulnerability assessment and mitigation, computer forensics and anonymous surfing. It has been developed by Frozenbox’s Team.
Parrot is cloud-friendly Linux distribution and unlike other ethical hacking operating systems, Parrot OS is a lightweight Linux distro — runs over machines which have minimum 265Mb of RAM and it is suitable for both 32bit (i386) and 64bit (amd64), with a special edition it works on old 32bit machines (486).
4. Live Hacking OS
Live Hacking OS is a Linux distribution packed with tools and utilities for ethical hacking, penetration testing and countermeasure verification. It includes the graphical user interface GNOME inbuilt. There is a second variation available that has command line only, and it requires very fewer hardware requirements.
5. DEFT Linux
DEFT stands for Digital Evidence and Forensic Toolkit and it’s an open-source distribution of Linux built around the DART (Digital Advanced Response Toolkit) software and based on the Ubuntu operating system. It has been designed from the ground up to offer some of the best open-source computer forensics and incident response tools that can be used by individuals, IT auditors, investigators, military, and police.
6. Samurai Web Testing Framework
The Samurai Web Testing Framework is a live Linux environment that has been pre-configured to function as a web pen-testing environment. The CD contains the best of the open-source and free tools that focus on testing and attacking websites. In developing this environment, we have based our tool selection on the tools we use in our security practice. We have included the tools used in all four steps of a web pen-test.
7. Network Security Toolkit
The Network Security Toolkit (NST) is a Linux-based Live CD that provides a set of open-source computer security and networking tools to perform routine security and networking diagnostic and monitoring tasks. The distribution can be used as a network security analysis, validation and monitoring tool on servers hosting virtual machines. The majority of tools published in the article “Top 125 security tools” by Insecure.org are available in the toolkit.
8. Bugtraq-II
Bugtraq-II is a GNU/Linux distribution focused on digital forensics, penetration testing, malware laboratories, and GSM forensics. Bugtraq-II is available in 11 languages with more than 500 ethical security hacking tools installed and configured. Depending on your desktop environment, the features vary. The minimum requirements are based on XFCE and KDE, this ethical hacking os needs 1GHz x86 processor & 512 MB of system memory 15 GB of disk space for installation.
9. NodeZero
NodeZero is an open-source Linux kernel-based ethical hacking operating system derived from Ubuntu and designed to be used for penetration testing operations. Besides the fact that it allows you to start the live system, the boot menu contains various advanced options, such as the ability to perform a system memory diagnostic test, boot from a local drive, start the installer directly, as well as to boot in safe graphics mode, text mode or debug mode.
With NodeZero you will have instant access to over 300 penetration testing tools, as well as a set of basic services that are needed in penetration testing operations.
10. Pentoo
Pentoo is a Live CD and Live USB designed for penetration testing and security assessment. Based on Gentoo Linux, Pentoo is provided both as 32 and 64 bit installable LiveCD. Pentoo is also available as an overlay for an existing Gentoo installation. The Pentoo kernel includes grsecurity and PAX hardening and extra patches – with binaries compiled from a hardened toolchain with the latest nightly versions of some tools available.
11. BlackBuntu
BlackBuntu is penetration testing distribution with GNOME Desktop Environment which was specially designed for security training students and practitioners of information security. It’s currently being built using the Ubuntu 10.10 and work on reference BackTrack.
12. Cyborg Hawk Linux
CYBORG HAWK LINUX is a Ubuntu-based hacking operating system created by the team of Ztrela Knowledge Solutions Pvt. Ltd. Cyborg Hawk penetration testing distro can be used for network security and assessment and also for digital forensics. It has various tools also fit for the Mobile Security and Wireless testing. It has 700+ tools while other penetration distros has 300+ and also dedicated tools for and menu for mobile security and malware analysis.
13. Knoppix STD
STD is a Linux-based Security Tool used by hackers. Actually, it is a collection of hundreds if not thousands of open source security tools. It’s a Live Linux distro and its sole purpose in life is to put as many security tools at your disposal with as slick an interface as it can. STD is meant to be used by both novice and professional security personnel but is not ideal for the Linux uninitiated.
14. Weakerthan
Weakerthan is another hacking distribution which is built from Debian Squeeze. For the desktop environment, it uses Fluxbox. This ethical hacking OS is ideal for WiFi hacking as it contains plenty of Wireless tools. It has a very well maintained website and a devoted community.
15. BlackArch Linux
BlackArch Linux -an Arch Linux-based ethical hacking operating system for penetration testers and security researchers. The new version also has a total of 1400 penetration testing tools with the old ones updated and the new ones added, making it a must-have download for hackers and security researchers.
16. Matriux Linux
Matriux Linux – a Debian-based security distribution designed for penetration testing and hacking. Although suited best for hackers, it can also be used by any Linux user as a desktop system for day-to-day computing. Matriux has more than 300 open source tools for penetration testing and hacking. Since its the new one, many security researchers claims that it is a better alternative to Kali Linux.
17. Dracos Linux
Dracos Linux — another favourite operating system of hackers that surfaced from Indonesia built based on the Linux from scratch. Dracos is built to be fast, strong, and powerful OS which is used to perform security testing (penetration testing). Powered by hundreds of pentest tools including information gathering, forensics, malware analysis, maintaining access, and reverse engineering, Dracos Linux is one of the best choices of hacker’s operating system.
18. Fedora Security Lab
Fedora Security Lab comes with the clean and fast Xfce Desktop Environment and essential set of tools like — Wireshark, Sqlninja, Yersinia, Medusa, etc — to follow a proper test path for security and pen-testing. Fedora Security Lab is maintained by a community of security testers and developers.
19. Caine
Caine — Computer-Aided Investigation Environment — is an Ubuntu-based GNU/Linux live distribution created for ethical hackers and digital forensics experts. It provides a complete forensic environment with a friendly graphical interface.
20. ArchStrike
ArchStrike is one of the perfect Arch Linux based ethical hacking operating systems for security experts. ArchStrike provides a live desktop environment based on the Openbox window manager along with an extra repository of security software of 32-bit and 64-bit builds.
21. URIX OS
URIX OS is a security-focused ethical hacking distribution based on openSUSE. In URIX OS security is strengthened by removing servers and closing incoming ports. The distro also provides several penetration tools for testing purposes.
That’s all!! If you think we forget to add some other favourite operating systems of hackers, please comment below. And also soon we will add more ethical hacking operating systems to the list.
13 Best Hacking Tools Of 2019 For Windows, Linux, macOS
W e have compiled a list of top hacking software and tools of 2019 with their best features and download links. This list is based on industry reviews, your feedback, and our own experience. This list will tell you about the best software used for hacking purposes featuring port scanners, web vulnerability scanner, password crackers, forensics tools, traffic analysis, and social engineering tools.
Read about them, learn how to use them and share your reviews to make this list better. If you’re interested in ethical hacking, you can also check our dedicated article on operating systems for ethical hacking and pentesting.
13 Best Hacking Software for Windows, Linux, and Mac
1. Metasploit | Best collection of exploit tools
Rather than calling Metasploit a collection of exploit tools, I’ll call it an infrastructure that you can utilize to build your own custom tools. This free software is one of the most popular cybersecurity tool that allows you to locate vulnerabilities at different platforms. Metasploit is backed by more than 200,000 users and contributors that help you to get insights and uncover the weaknesses in your system.
This top hacking tool package of 2019 lets you simulate real-world attacks to tell you about the weak points and finds them. As a penetration tester, it pin points the vulnerabilities with Nexpose closed–loop integration using Top Remediation reports. Using the open source Metasploit framework, users can build their own tools and take the best out of this multi-purpose hacking tool.
Supported platforms and download:
Metasploit is available for all major platforms including Windows, Linux, and OS X.
2. Acunetix WVS | Vulnerability Scanner
Acunetix is a web vulnerability scanner (WVS) that scans and finds out the flaws in a website that could prove fatal. This multi-threaded tool crawls a website and finds out malicious Cross-site Scripting, SQL injection, and other vulnerabilities. This fast and easy to use tool scans WordPress websites from more than 1200 vulnerabilities in WordPress.
Acunetix comes with a Login Sequence Recorder that allows one to access the password protected areas of websites. The new AcuSensor technology used in this tool allows you to reduce the false positive rate. Such features have made Acunetix WVS a preferred hacking tools that you need to check out in 2019.
Supported platforms and download:
Acunetix is available for Windows XP and higher.
3. Nmap | Port scanner tool
Nmap – also known as Network Mapper – falls in the category of a port scanner tool. This free and open source hacking tool is the most popular port scanning tool around that allows efficient network discovery and security auditing. Used for a wide range of services, Nmap uses raw IP packets to determine the hosts available on a network, their services along with details, operating systems used by hosts, the type of firewall used, and other information.
Last year, Nmap won multiple security products of the year awards and was featured in multiple movies including The Matrix Reloaded, Die Hard 4, and others. Available in the command line, Nmap executable also comes in an advanced GUI avatar.
Supported platforms and download:
Nmap is available for all major platforms including Windows, Linux, and OS X.
4. Wireshark | Packet analyzer
Wireshark is a well-known packet crafting tool that discovers vulnerability within a network and probes firewall rule-sets. Used by thousands of security professionals to analyze networks and live pocket capturing and deep scanning of hundreds of protocols. Wireshark helps you to read live data from Ethernet, IEEE 802.11, PPP/HDLC, ATM, Bluetooth, USB, Token Ring, Frame Relay, FDDI, and others.
This free and open source tool was originally named Ethereal. Wireshark also comes in a command-line version called TShark. You can also read our dedicated article on the newly released Wireshark 3.0.0.
Supported platforms and download:
This Qt-based network protocol analyzer runs with ease on Linux, Windows, and OS X.
5. oclHashcat | Password cracking tool
If password cracking is something you do on daily basis, you might be aware of the free password cracking tool Hashcat. While Hashcat is a CPU-based password cracking tool, oclHashcat is its advanced version that uses the power of your GPU.
oclHashcat calls itself world’s fastest password cracking tool with world’s first and only GPGPU based engine. For using the tool, NVIDIA users require ForceWare 346.59 or later and AMD users require Catalyst 15.7 or later.
This tool employs following attack modes for cracking:
- Straight
- Combination
- Brute-force
- Hybrid dictionary + mask
- Hybrid mask + dictionary
Mentioning another major feature, oclHashcat is an open source tool under MIT license that allows an easy integration or packaging of the common Linux distros.
Supported platforms and download:
This useful password cracking tool can be downloaded in different versions for Linux, OSX, and Windows.
6. Nessus | Vulnerability Scanner
This top free security tool of 2019 works with the help of a client-server framework. Developed by Tenable Network Security, the tool is one of the most popular vulnerability scanners we have. Nessus serves different purposes to different types of users – Nessus Home, Nessus Professional, Nessus Manager and Nessus Cloud.
Using Nessus, one can scan multiple types of vulnerabilities that include remote access flaw detection, misconfiguration alert, denial of services against TCP/IP stack, preparation of PCI DSS audits, malware detection, sensitive data searches etc. To launch a dictionary attack, Nessus can also call a popular tool Hydra externally.
Apart from the above mentioned basic functionalities, Nessus could be used to scan multiple networks on IPv4, IPv6, and hybrid networks. You can set the scheduled scan to run at your chosen time and re-scan all or a subsection of previously scanned hosts using selective host re-scanning.
Supported platforms and download:
Nessus is supported by a variety of platforms including Windows 7 and 8, Mac OS X, and popular Linux distros like Debian, Ubuntu, Kali Linux etc.
7. Maltego | Forensics platform
Maltego is an open source forensics platform that offers rigorous mining and information gathering to paint a picture of cyber threats around you. Maltego excels in showing the complexity and severity of points of failure in your infrastructure and the surrounding environment.
Maltego is a great hacker tool that analyzes the real world links between people, companies, websites, domains, DNS names, IP addresses, documents and whatnot. Based on Java, this tool runs in an easy-to-use graphical interface with lost customization options while scanning.
Supported platforms and download:
Maltego security tool is available for Windows, Mac, and Linux.
8. Social-Engineer Toolkit
Also featured on Mr. Robot, TrustedSec’s Social-Engineer Toolkit is an advanced framework for simulating multiple types of social engineering attacks like credential harvestings, phishing attacks, and more. On the show, Elliot is seen using the SMS spoofing tool from the Social-Engineer Toolkit.
This Python-driven tool is the standard tool for social engineering penetration tests with more than two million downloads. It automates the attacks and generates disguising emails, malicious web pages and more.
Supported platforms and download:
To download SET on Linux, type the following command:
Apart from Linux, Social-Engineer Toolkit is partially supported on Mac OS X and Windows.
9. Netsparker | Web app scanner
Netsparker is a popular web application scanner that finds flaws like SQL injection and local file induction, suggesting remedial actions in a read-only and safe way. As this hacking tool produces a produces a proof of exploitation, you don’t need to verify the vulnerability on your own. Just in case it can’t verify a flaw automatically, it’ll alert you. This hacking tool is very easy to get started with. Simply enter the URL and let it perform a scan. Netsparker supports JavaScript and AJAX-based applications. So, you don’t need to configure the scanner or rely on some complex scanning settings to scan different types of web applications.
If you don’t wish to pay money for the professional version of Netsparker, they’ve also got a demo version that you can use.
Supported platforms and download:
Netsparker web app scanner is available for Windows
10. w3af | Web app scanner
w3af is a free and open source web application security scanner that’s widely used by hackers and penetration testers. w3af stands for web application attack and audit framework. Using this hacking tool, one can get security vulnerability information that can be further used in penetration testing engagements. w3af claims to identify more than 200 vulnerabilities (including the likes of cross-site scripting, SQL Injection, PHP misconfigurations, guessable credentials, and unhandled application errors) and make a web application (and website) more secure.
w3af comes both in command line and graphical user interface to suit the needs of a hacker. In less than 5 clicks and using the predefined profile for the beginners, one can audit the security of a web application. As it’s well documented, the new users can easily find their way. Being an open source hacking tool, an experienced developer can play with the code, add new features, and create something new.
Supported platforms and download:
w3af is available for Linux, BSD, and OS X. On Windows, its older versions are supported.
11. John The Ripper
When it comes to the password cracking tools, John The Ripper turns out to be the top-most choice of most of the ethical hackers. This free and open source software is distributed in the form of source code.
John The Ripper is primarily written in C programming language. It has been able to achieve the status of a great companion due to the fact that it’s a combination of many password crackers into one. Different modules grant it the ability to crack the passwords using different encryption techniques
Supported platforms and download:
John The Ripper hacking software is available on a variety of platforms, including Windows, Linux, DOS, OpenVMS, and Unix.
12. Aircrack-ng | Password cracking tool
When it comes to password cracking, Aircrack-ng is another option that you can explore. This network suite consists of a detector, traffic sniffer, and password cracker tool. All these tools are command line based and allow heavy scripting.
Using Aircrack-ng hacking software, you can capture the packets, export data to text files, perform different attacks, check WiFi cards and drivers capabilities, cracking WEP and WPA PSK, etc.
Supported platforms and download:
Aircrack-ng is available for different platforms like macOS, Linux, FreeBSD, Windows. The Linux version has also been ported to Android as well.
13. Ghidra | Reverse Engineering Tool
Ghidra is NSA’s home-grown reverse engineering tool that has been recently open sourced by the American agency. As per NSA, the tool is internally used to dig deep into malware and software to spot vulnerabilities that can be exploited.
One of the most important features of this hacking software is the feature of multi-user support that lets researchers collaborate and reverse engineer a single binary. One can also use the exposed API and create own Ghidra plugin and add-ons for extra functionality.
Supported platforms and download:
Ghidra hacking software is available for Linux, Windows, and macOS.
Other top hacking and security tools of 2019 in multiple categories:
Web Vulnerability Scanners – Burp Suite, Firebug, AppScan, OWASP Zed, Paros Proxy, Nikto, Grendel-Scan
Vulnerability Exploitation Tools – Netsparker, sqlmap, Core Impact, WebGoat, BeEF
Forensic Tools – Helix3 Pro, EnCase, Autopsy
Port Scanners – Unicornscan, NetScanTools, Angry IP Scanner
Traffic Monitoring Tools – Nagios, Ntop, Splunk, Ngrep, Argus
Debuggers – IDA Pro, WinDbg, Immunity Debugger, GDB
Rootkit Detectors – DumpSec, Tripwire, HijackThis
Encryption Tools – KeePass, OpenSSL, OpenSSH/PuTTY/SSH, Tor
Password Crackers – John the Ripper, Hydra, ophcrack
We hope that you found this list helpful. Share your reviews in the comments below and help us improve this list.
Get the best deals on these hacking certification courses: