- Ethical hacking and penetration testing
- InfoSec, IT, Kali Linux, BlackArch
- How to start with HackRF and gqrx
- How to Install Driver, HackRF Tools and SDR Utilities
- Linux
- Assembly from source
- Where to buy HackRF
- How to check HackRF
- Step-by-step instructions for updating the HackRF One firmware
- How to receive a signal with HackRF
- How to listen to FM radio with HackRF
- when update to new firmware >>hackrf_open() failed: Access denied #366
- Comments
- stackprogramer commented Apr 4, 2017 •
- when i update firmware hackrf_one :
- Expected behaviour
- Actual behaviour
- Version information
- when update to new firmware >>hackrf_open() failed: Access denied #366
- Comments
- stackprogramer commented Apr 4, 2017 •
- when i update firmware hackrf_one :
- Expected behaviour
- Actual behaviour
- Version information
Ethical hacking and penetration testing
InfoSec, IT, Kali Linux, BlackArch
How to start with HackRF and gqrx
This is the first introduction to HackRF and gqrx.
The issues of analysis of radio broadcasting, beyond Wi-Fi, Bluetooth and BLE, are quite new to me. Therefore, when I received my HackRF in the mail, I had a question – what should I do with it? This article focuses on exactly this – how to test and receive radio signal with HackRF for the first time. For clarity, we will just listen to the FM radio. Something more serious will be in the following tutorials.
If you are also a beginner, then HackRF is a radio (Software-defined radio), a device that can send and receive radio waves in a very wide range. And gqrx is one of the programs for working with data received through HackRF (or other similar devices). This program has a graphical interface and is very suitable for the very first acquaintance with SDR.
Remember that HackRF should not be turned on, and especially being used to transmit or receive data if no antenna is connected to it!
How to Install Driver, HackRF Tools and SDR Utilities
This section contains software installation tips for specific Linux operating systems and distributions.
Most users are strongly advised, if you do not pursue the goal of developing or testing new features for HackRF, use the packages built for your system and install them using the package manager available for your operating system.
Linux
Kali Linux, Ubuntu, Debian, Linux Mint
Fedora / Red Hat
Arch linux, BlackArch
OS X (10.5+)
Windows
Executables are provided as part of the PothosSDR project, which can be downloaded here: https://downloads.myriadrf.org/builds/PothosSDR/
Freebsd
You can use the binary package:
You can build and install with ports:
Assembly from source
Linux / OS X / *BSD
First, make sure that your system is updated using the update method provided on your operating system.
- Installation using PyBOMBS
The GNU Radio project has an assembly system that covers key libraries, drivers for SDR hardware, and many of the tree modules. PyBOMBs take care for you in installing dependencies.
- Building HackRF tools from source
Get the source code for the HackRF tools from either the release archive or git:
After downloading the source code, the host tools can be compiled as follows:
If you have HackRF, then you may need to update the firmware to match the version of the host tools.
Where to buy HackRF
I bought from this seller. The peculiarity of buying a HackRF is that there are many configuration options:
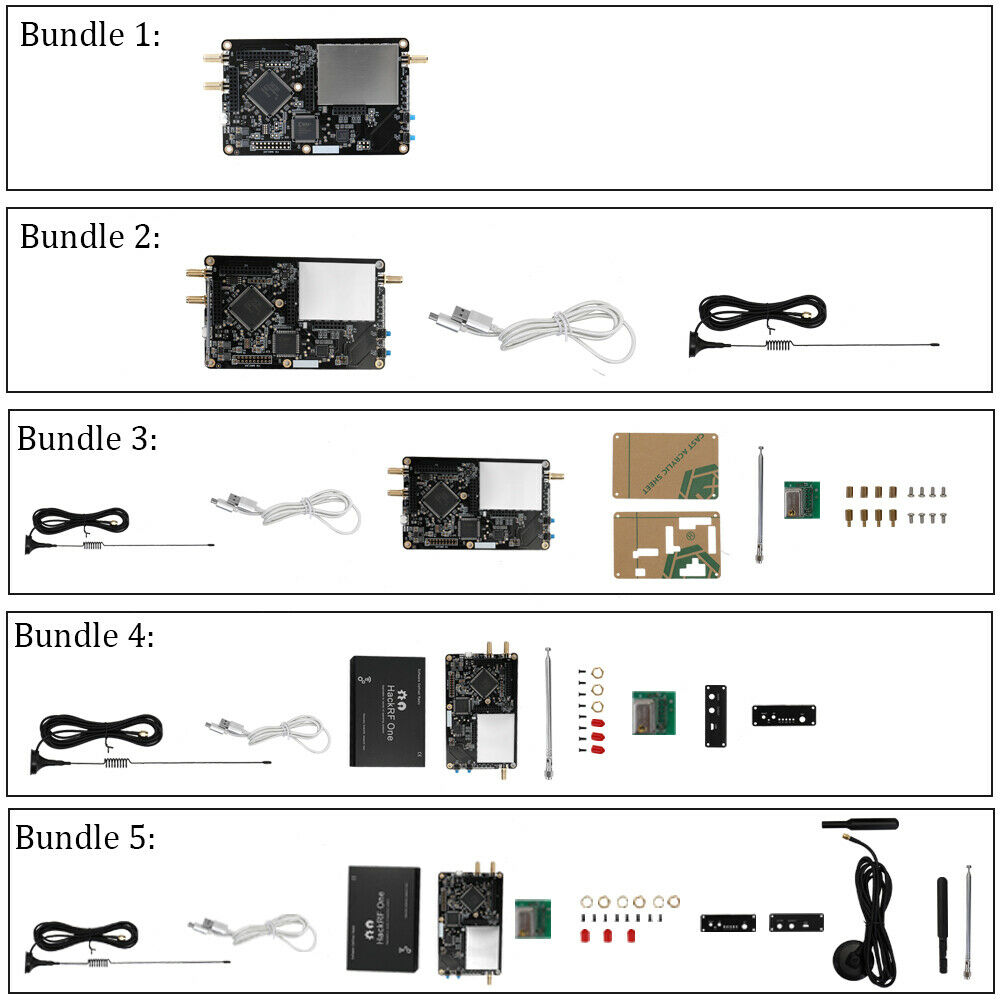
You can buy a board, even without a USB power cable, or you can buy it with a case (Alloy Shell) and several antennas. The types of shells also vary. You also need to be careful, and not confuse the case without a board with the board itself – some cases (with a screen and a built-in battery) can cost as much as the board itself.

- 1 x HackRF One Software Defined Radio with Aluminum Alloy Shell
- 4 x HackRF SMA Antennas (40MHz-6GHz antenna;2.4G/5/5.8G antenna;70MHz-2700MHz antenna;40MHz-860MHz antenna)
- 1 x HackRF One special Shield cover(welded on the board)
- 1 x HackRF TCXO PPM0.1 GPS Clock module
- 1 x LG Micro USB cable
I liked that because there are several antennas for different needs.
The box came to me very crumpled form and while I was coming from the post office I was quite worried for the board:

Fortunately, the board was already in the case, and the case is quite strong and there was not a scratch on it.

The antennas look very fragile, but they turned out to be in perfect order – not bent or broken. Only the HackRF TCXO PPM0.1 GPS Clock module was unlucky, when the box was deformed, the legs pierced the package:
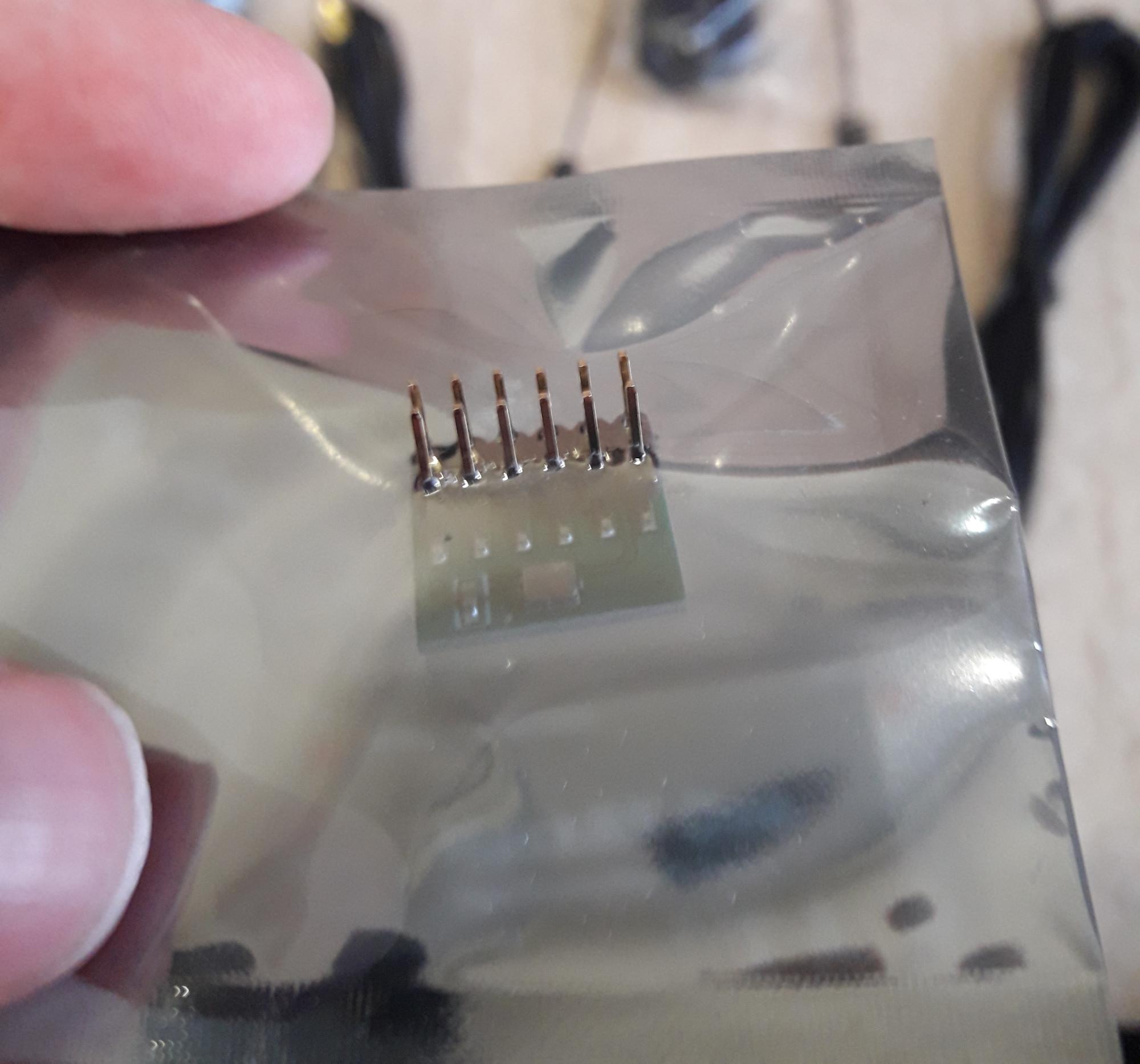
The legs themselves were also bent.

I straightened the legs with a flat screwdriver and installed this module on the HackRF board. I forgot to take a photo (and I’m too lazy to take it apart), and besides, I’m not sure I installed it correctly. Therefore, about the HackRF TCXO PPM0.1 GPS Clock module, why it is needed and how to use it will be in some subsequent article.
How to check HackRF
When HackRF is connected to a Linux computer, practically nothing happens – only the indicators on the board light up. The system itself does not have any built-in applets for connecting to HackRF.
Let’s see the information:
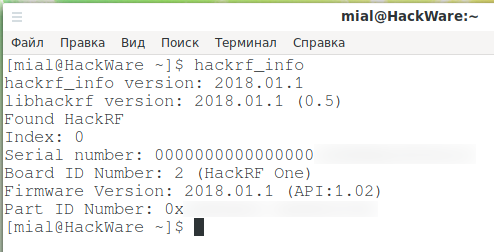
Firstly, the device is detected, and the firmware 2018.01.1 is installed on it. The latest firmware version can be checked here: https://github.com/mossmann/hackrf/releases/. There is the same version, that is, an update is not required (how to update HackRF is written here).
Let’s try to get data at maximum speed:

Let’s try to send the data:
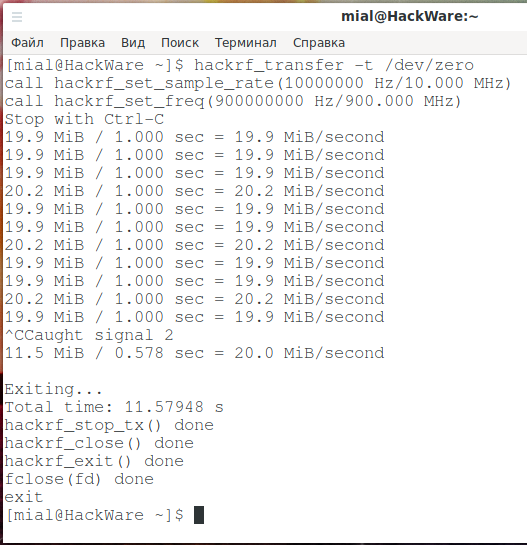
At least the basic tests passed – despite the crumpled box, the device was not damaged.
Step-by-step instructions for updating the HackRF One firmware
Since this writing, there has been a software update for HackRF One, including a firmware update for HackRF.
To check the version of the installed software and HackRF firmware, run the command:
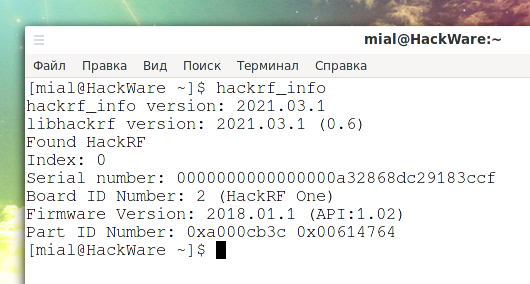
As you can see, the version of the software installed on this computer is now 2021.03.1:
And firmware version 2018.01.1:
You can make sure that this is the latest software version on this page: https://github.com/mossmann/hackrf/releases/
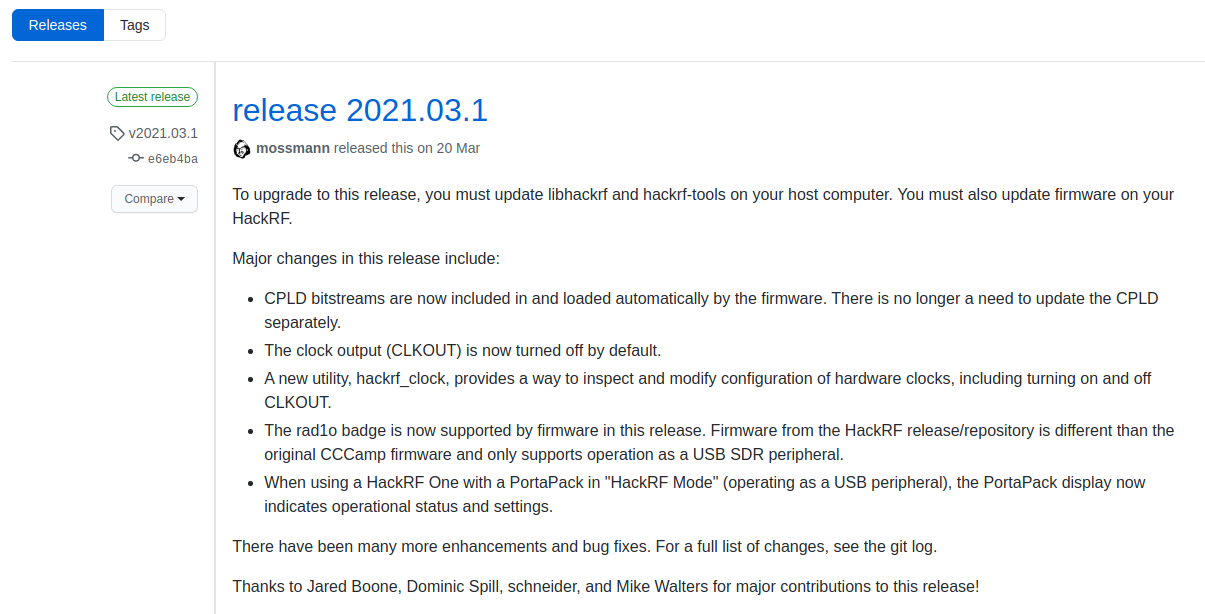
In the same place, we learn that starting with release 2021.03.1, CPLD bitstreams are now included in the firmware and are automatically loaded with it during an update. You no longer need to update the CPLD separately.
This section will show you step by step how to upload the new firmware to the HackRF.
The firmware file comes with libhackrf and hackrf-tools. The name of specific packages can be different on different Linux distributions. See above How to Install Driver, HackRF Tools and SDR Utilities for details.
That is, you need to wait for these packages to be updated in the repositories of your distribution, or you can compile them yourself.
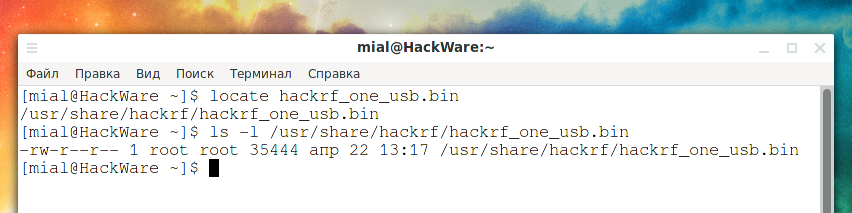
The file with the firmware is called hackrf_one_usb.bin, let’s find the path to it in the system:
In my case, this is /usr/share/hackrf/hackrf_one_usb.bin.
Although the updated libhackrf and hackrf-tools should mean that the firmware file is also new, check that the file has a fresh creation date.
To start the update process, use a command of the form:

Turn HackRF off and on for changes to take effect (disconnect from USB cable).
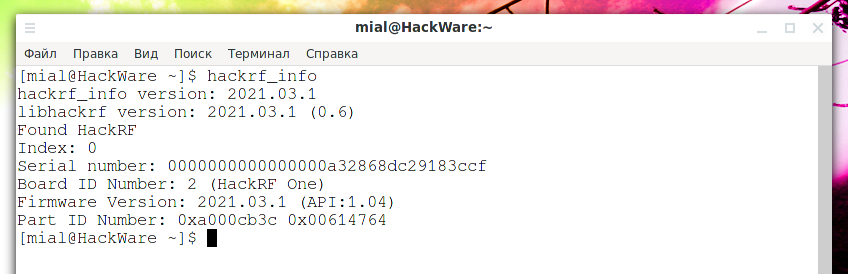
Let’s check the software version again:
The HackRF firmware is now updated!
How to receive a signal with HackRF
Install the gqrx program; for this, in Kali Linux, Debian, Linux Mint, Ubuntu and their derivatives, run the command:
On BlackArch and Arch Linux, run the command:
When you first start the setup window will appear, in it you can select the source of the received data and the sound output device. As a Device, I selected HackRF, and also increased the Input rate to a maximum value of 20000000.
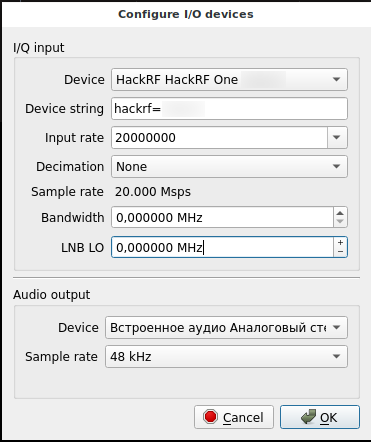
Gqrx main window:
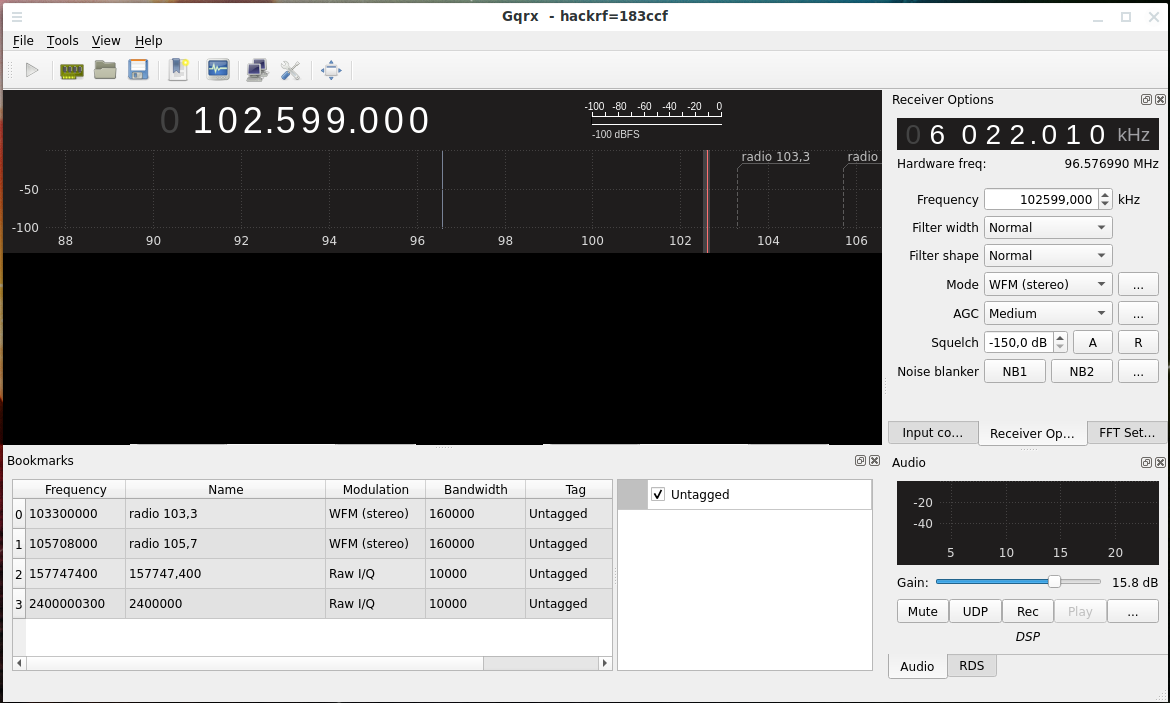
To start receiving a signal, click the “Start DSP processing” button, and to change the frequency, you can specify it in the “Frequency” window, or set it on the panel with numbers. The panel can be moved, for this grab the bottom row of numbers:
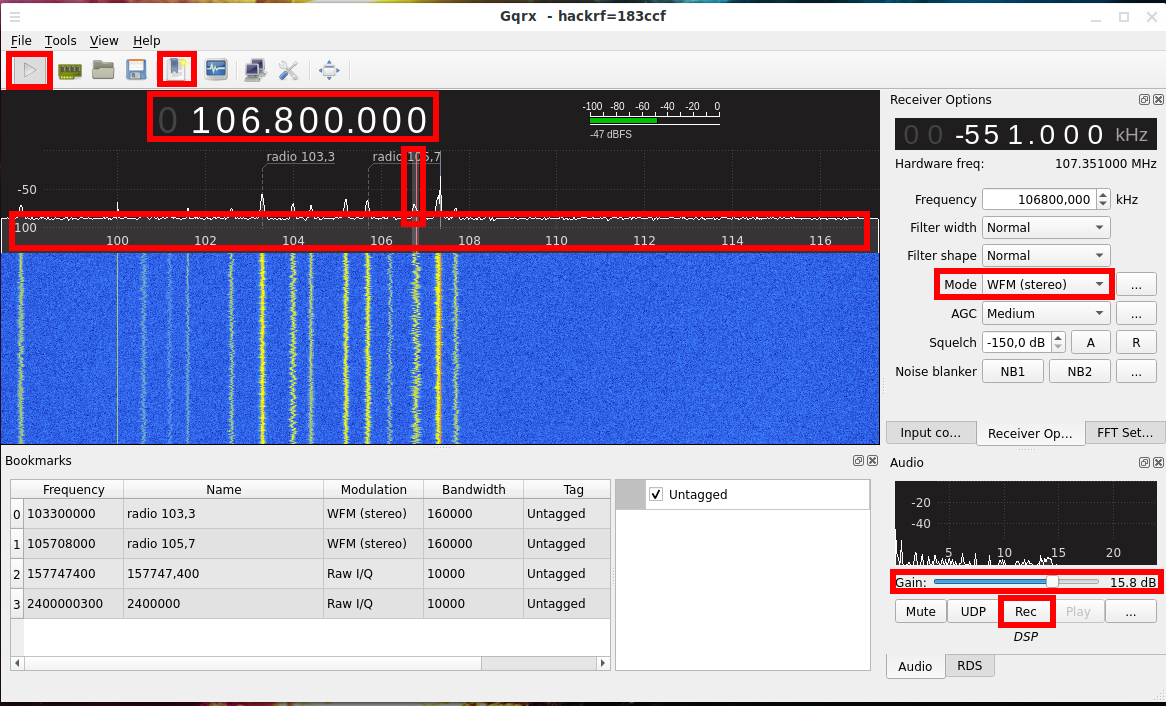
To stop receiving a signal, press the “Stop DSP processing” button (formerly the “Start DSP processing” button). If you want to unplug HackRF (for example, to change the antenna), then it is better to exit gqrx, because I had this program freeze after reconnecting HackRF.
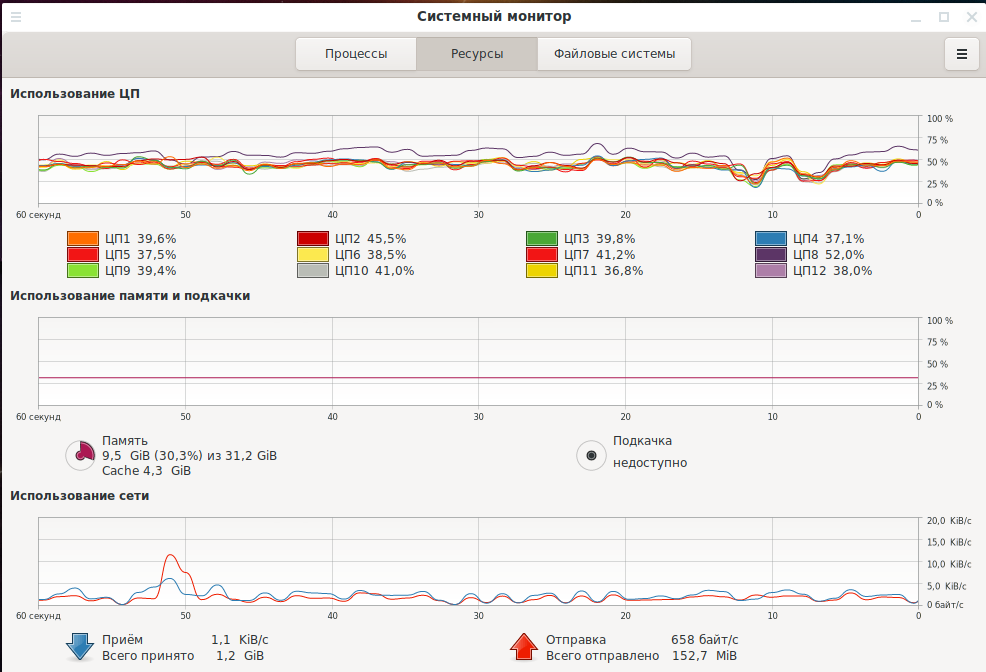
While receiving the signal, the CPU load is rather high, probably due to the fact that I chose a high Input rate:
How to listen to FM radio with HackRF
The FM bands are 92.1-107.1 MHz. Since the frequency in the “Frequency” window is indicated in kHz (kilohertz), then we need to go to about 100000 kHz:
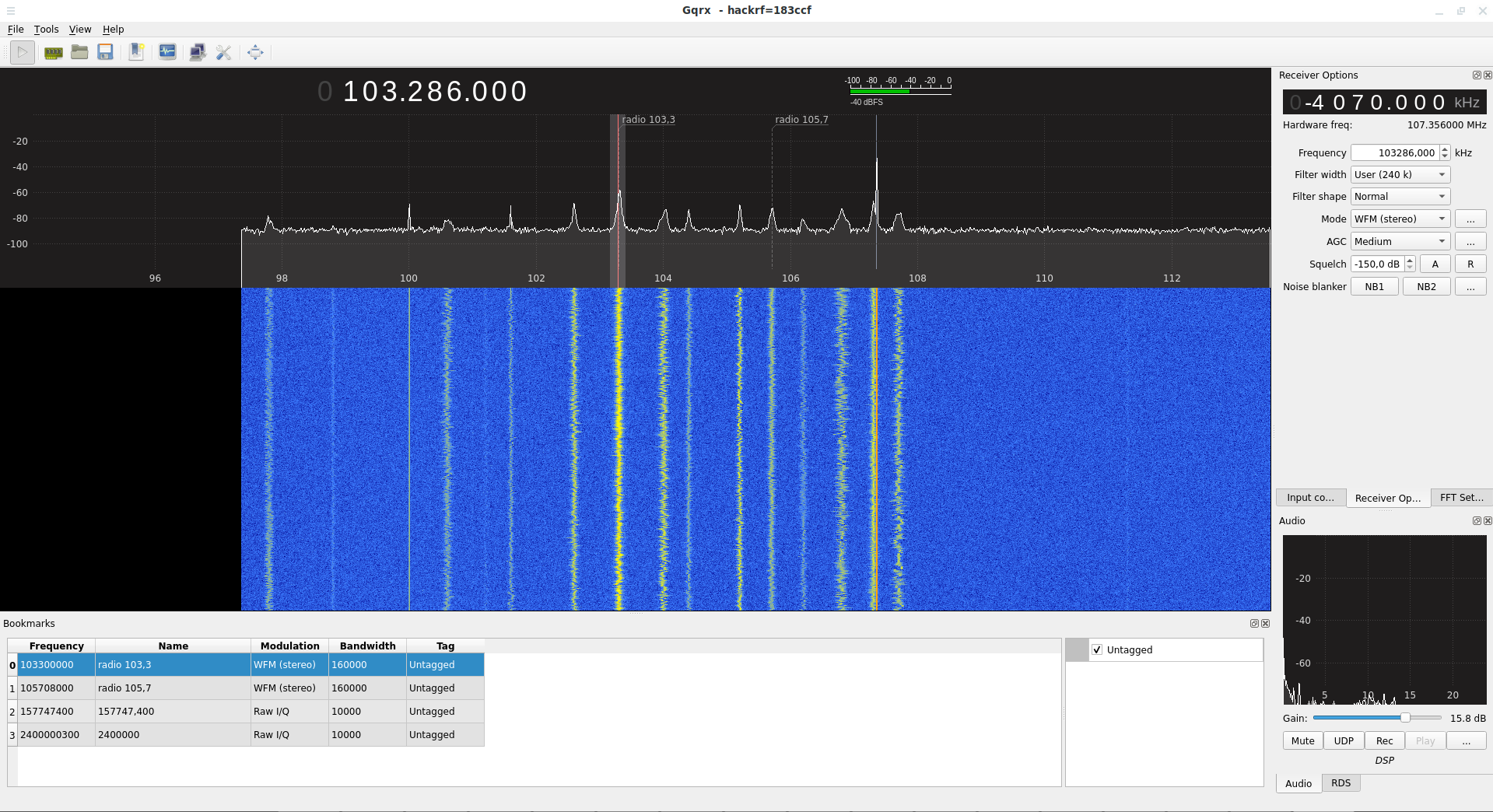
You can see that in this range there are many peaks – this is the broadcasts of radio stations.
For “Mode”, select “WFM (stereo)”.
Increase the “Gain” value, otherwise it will be too quiet.
By clicking on the “Bookmark” button, you can save frequencies to bookmarks.
If you click on the “Rec” button, then you can record audio.
A short video where I learn the gqrx interface:
This is just the beginning! Next, we will deal with signal sources and methods for decoding them. With HackRF, you can detect a variety of devices: from wireless doorbells to bugs, hidden cameras and radars. Some types of signals can be decrypted: walkie-talkies, outdated telephone standards, etc. Some types of signals can only be traced: Wi-Fi, modern telephone standards, etc. In any case, the world of radio waves is very vast and interesting!
Источник
when update to new firmware >>hackrf_open() failed: Access denied #366
Comments
stackprogramer commented Apr 4, 2017 •
when i update firmware hackrf_one :
1.i used this link for update firmware https://github.com/mossmann/hackrf/releases/tag/v2017.02.1
2.product id and vendor id is change?? /\00/\
root@debian:/home/admin# hackrf_info
hackrf_info version: 2017.02.1
libhackrf version: 2017.02.1 (0.5)
Found HackRF
Index: 0
Serial number: 0000000000000000406464c823846d4b
Board ID Number: 2 (HackRF One)
Firmware Version: 2017.02.1 (API:1.02)
Part ID Number: 0xa000cb3c 0x00534f4b
3.rule usb that i set is not worked.
Expected behaviour
when i am not in root user i set rule group that i can’t access hackrfone.
Actual behaviour
but in ordinary user mode it returns
$ hackrf_info
hackrf_info version: 2017.02.1
libhackrf version: 2017.02.1 (0.5)
Found HackRF
Index: 0
hackrf_open() failed: Access denied (insufficient permissions) (-1000)
Version information
debian os > libhackrf version: 2017.02.1 (0.5)
for settig rule i used different modes:
i use lsusb for determine my id vendor /product
admin@debian:/etc/udev/rules.d$ lsusb
Bus 002 Device 002: ID 1d50:6089 OpenMoko, Inc.
Bus 002 Device 001: ID 1d6b:0002 Linux Foundation 2.0 root hub
Bus 001 Device 004: ID 0e0f:0008 VMware, Inc.
Bus 001 Device 003: ID 0e0f:0002 VMware, Inc. Virtual USB Hub
Bus 001 Device 002: ID 0e0f:0003 VMware, Inc. Virtual Mouse
Bus 001 Device 001: ID 1d6b:0001 Linux Foundation 1.1 root hub
idvendor:idproduct=1d50:6089
idvendor:idproduct= a000cb3c :00534f4b
idvendor:idproduct= cb3c :00534f4b
idvendor:idproduct= cb3c:534f4b
i too set group to my group user.
i saw too this link
http://wiki.openmoko.org/wiki/USB_Product_IDs
my question why product /vendor id is changed
why rule in past worked now that i set doesn’t work.
thanks in advance best regards stackprogramer
The text was updated successfully, but these errors were encountered:
Источник
when update to new firmware >>hackrf_open() failed: Access denied #366
Comments
stackprogramer commented Apr 4, 2017 •
when i update firmware hackrf_one :
1.i used this link for update firmware https://github.com/mossmann/hackrf/releases/tag/v2017.02.1
2.product id and vendor id is change?? /\00/\
root@debian:/home/admin# hackrf_info
hackrf_info version: 2017.02.1
libhackrf version: 2017.02.1 (0.5)
Found HackRF
Index: 0
Serial number: 0000000000000000406464c823846d4b
Board ID Number: 2 (HackRF One)
Firmware Version: 2017.02.1 (API:1.02)
Part ID Number: 0xa000cb3c 0x00534f4b
3.rule usb that i set is not worked.
Expected behaviour
when i am not in root user i set rule group that i can’t access hackrfone.
Actual behaviour
but in ordinary user mode it returns
$ hackrf_info
hackrf_info version: 2017.02.1
libhackrf version: 2017.02.1 (0.5)
Found HackRF
Index: 0
hackrf_open() failed: Access denied (insufficient permissions) (-1000)
Version information
debian os > libhackrf version: 2017.02.1 (0.5)
for settig rule i used different modes:
i use lsusb for determine my id vendor /product
admin@debian:/etc/udev/rules.d$ lsusb
Bus 002 Device 002: ID 1d50:6089 OpenMoko, Inc.
Bus 002 Device 001: ID 1d6b:0002 Linux Foundation 2.0 root hub
Bus 001 Device 004: ID 0e0f:0008 VMware, Inc.
Bus 001 Device 003: ID 0e0f:0002 VMware, Inc. Virtual USB Hub
Bus 001 Device 002: ID 0e0f:0003 VMware, Inc. Virtual Mouse
Bus 001 Device 001: ID 1d6b:0001 Linux Foundation 1.1 root hub
idvendor:idproduct=1d50:6089
idvendor:idproduct= a000cb3c :00534f4b
idvendor:idproduct= cb3c :00534f4b
idvendor:idproduct= cb3c:534f4b
i too set group to my group user.
i saw too this link
http://wiki.openmoko.org/wiki/USB_Product_IDs
my question why product /vendor id is changed
why rule in past worked now that i set doesn’t work.
thanks in advance best regards stackprogramer
The text was updated successfully, but these errors were encountered:
Источник



