- Kali Linux — Password Cracking Tools
- Hydra
- Johnny
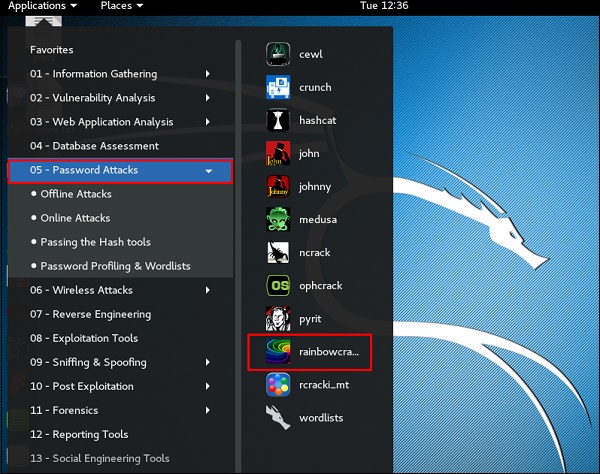
- Rainbowcrack
- SQLdict
- hash-identifier
- How to Crack Linux Password Hash
- Dictionary Based Cracking
- Key-space Brute-forcing
- Other Methods
- Disclaimer:
- Linux Password Cracking: Explain unshadow and john Commands ( John the Ripper Tool )
- John cracking modes
- Install John the Ripper Password Cracking Tool
- How do I use John the ripper to check weak passwords or crack passwords?
- Related:
- Kali Linux – Password Cracking Tool
Kali Linux — Password Cracking Tools
In this chapter, we will learn about the important password cracking tools used in Kali Linux.
Hydra
Hydra is a login cracker that supports many protocols to attack ( Cisco AAA, Cisco auth, Cisco enable, CVS, FTP, HTTP(S)-FORM-GET, HTTP(S)-FORM-POST, HTTP(S)-GET, HTTP(S)-HEAD, HTTP-Proxy, ICQ, IMAP, IRC, LDAP, MS-SQL, MySQL, NNTP, Oracle Listener, Oracle SID, PC-Anywhere, PC-NFS, POP3, PostgreSQL, RDP, Rexec, Rlogin, Rsh, SIP, SMB(NT), SMTP, SMTP Enum, SNMP v1+v2+v3, SOCKS5, SSH (v1 and v2), SSHKEY, Subversion, Teamspeak (TS2), Telnet, VMware-Auth, VNC and XMPP).
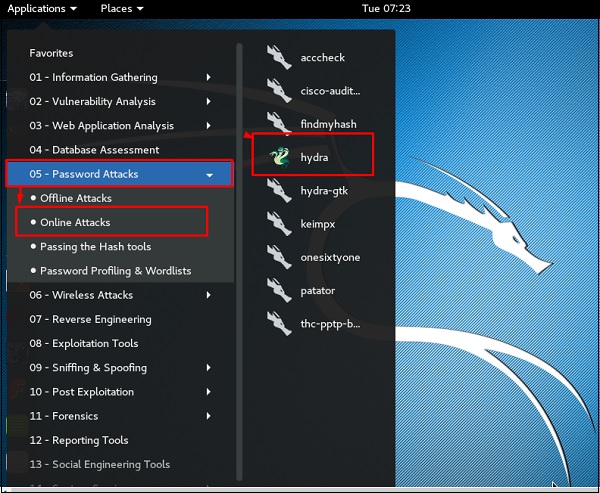
To open it, go to Applications → Password Attacks → Online Attacks → hydra.
It will open the terminal console, as shown in the following screenshot.
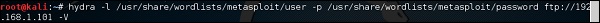
In this case, we will brute force FTP service of metasploitable machine, which has IP 192.168.1.101
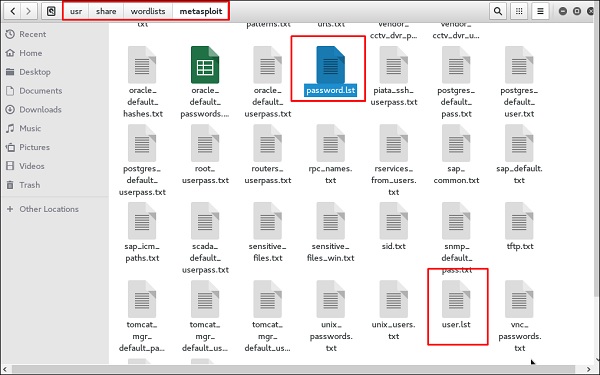
We have created in Kali a word list with extension ‘lst’ in the path usr\share\wordlist\metasploit.
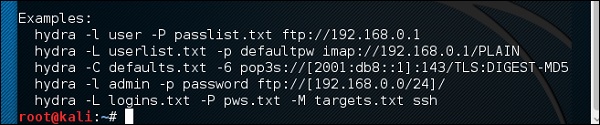
The command will be as follows −
where –V is the username and password while trying
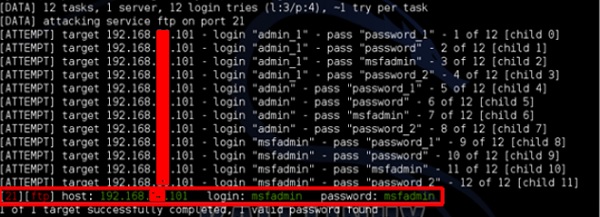
As shown in the following screenshot, the username and password are found which are msfadmin:msfadmin
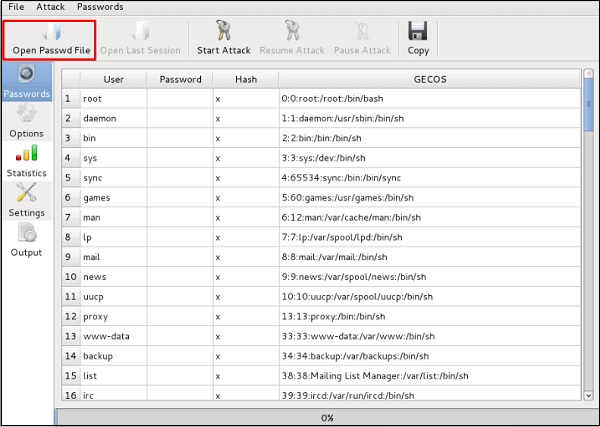
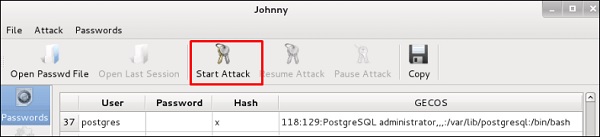
Johnny
Johnny is a GUI for the John the Ripper password cracking tool. Generally, it is used for weak passwords.
To open it, go to Applications → Password Attacks → johnny.
In this case, we will get the password of Kali machine with the following command and a file will be created on the desktop.
Click “Open Passwd File” → OK and all the files will be shown as in the following screenshot.
Click “Start Attack”.
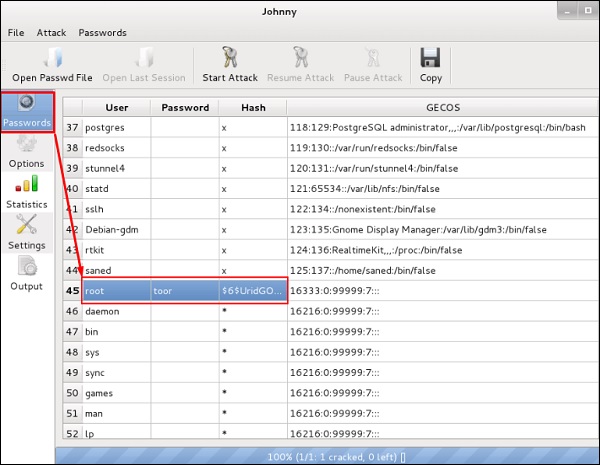
After the attack is complete, click the left panel at “Passwords” and the password will be unshaded.
john is a command line version of Johnny GUI. To start it, open the Terminal and type “john”.
In case of unshadowing the password, we need to write the following command −
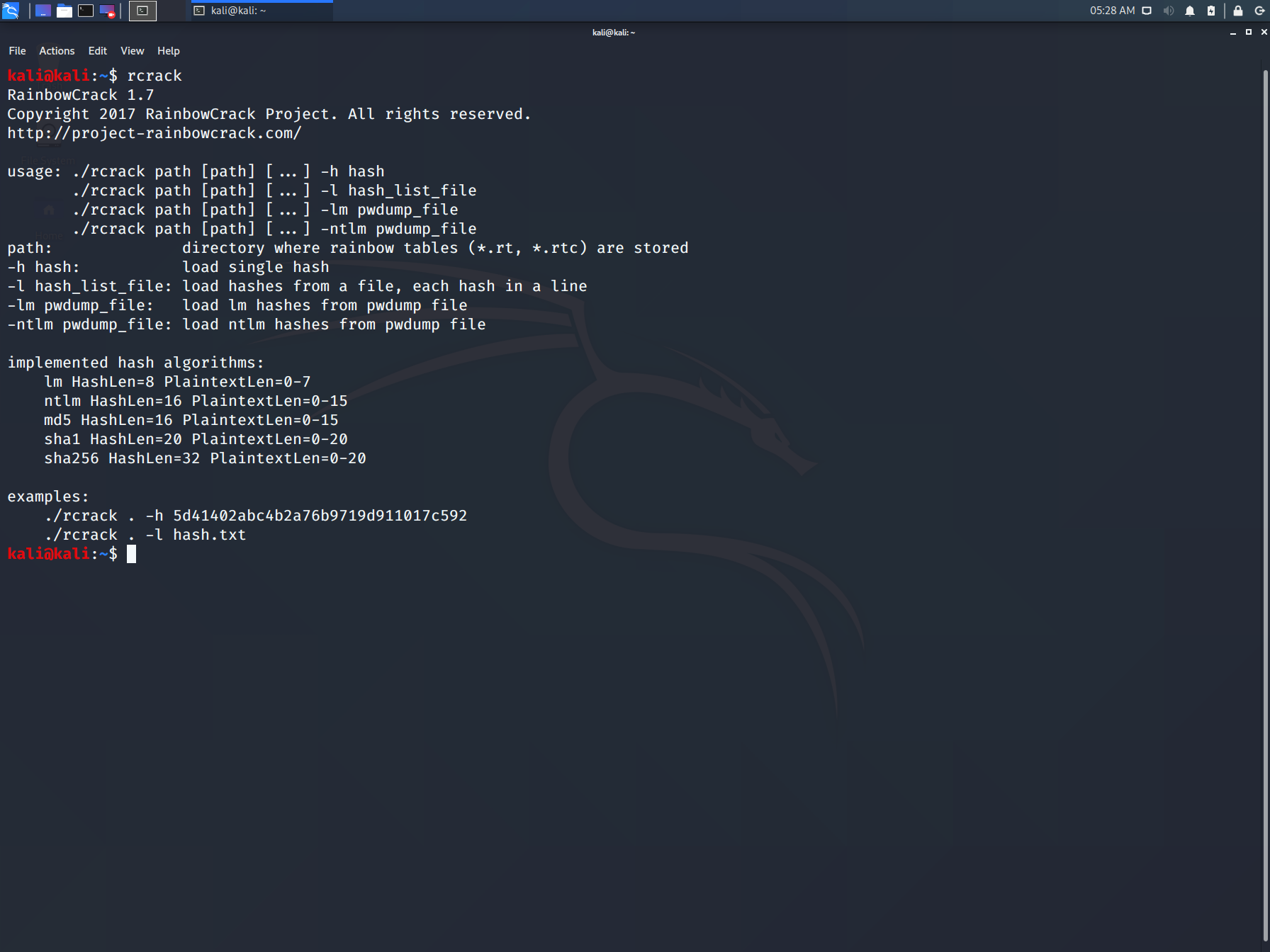
Rainbowcrack
The RainbowCrack software cracks hashes by rainbow table lookup. Rainbow tables are ordinary files stored on the hard disk. Generally, Rainbow tables are bought online or can be compiled with different tools.
To open it, go to Applications → Password Attacks → click “rainbowcrack”.
The command to crack a hash password is −
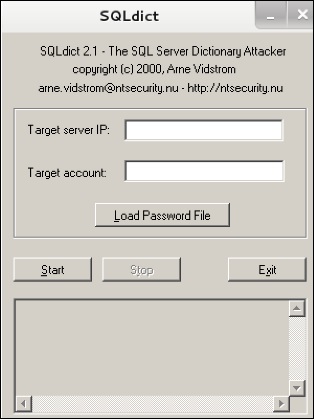
SQLdict
It is a dictionary attack tool for SQL server and is very easy and basic to be used. To open it, open the terminal and type “sqldict”. It will open the following view.
Under “Target IP Server”, enter the IP of the server holding the SQL. Under “Target Account”, enter the username. Then load the file with the password and click “start” until it finishes.
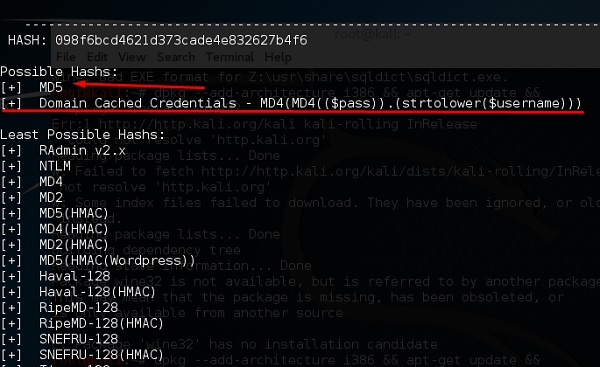
hash-identifier
It is a tool that is used to identify types of hashes, meaning what they are being used for. For example, if I have a HASH, it can tell me if it is a Linux or windows HASH.
The above screen shows that it can be a MD5 hash and it seems a Domain cached credential.
Источник
How to Crack Linux Password Hash
Apr 14, 2020 · 2 min read
Example of Linux Password Hash: $1$e7NfNpNi$A6nCwOTqrNR2oDuIKirRZ
- $1 = MD5 hashing algorithm.
- $2 =Blowfish Algorithm is in use.
- $2a=eksblowfish Algorithm
- $5 =SHA-256 Algorithm
- $6 =SHA-512 Algorithm
So this is MD5 hash
The second field is salt value so e7NfNpNi is the salt
The last field is the hash value of salt+user password i.e A6nCwOTqrNR2oDuIKirRZ
Now comes the cracking part. But unless this is a common hash which it isn’t you can’t decrypt it.
You can use Johntheripper to crack the password. This might take a long time if you are keyspace bruteforcing. If you want you can use a dictionary based attack to crack it. To do this first you need to setup the hash file.
Afte r this you can do one of the following
Dictionary Based Cracking
- john -w /path/to/wordlist — format=md5crypt hashes
Key-space Brute-forcing
Other Methods
If you have access to a GPU, you can harness its power for your cracking process. For this you can use hash-cat.
- hashcat -m 1800 -a 0 [Path-to-Hashes] [Path-to-Word-list] -o [Path-to-Output-Cracked-Hashes]
you can set m to either 500 or 1800, depending on your setup.
To solve this Common Password problems use a Complex Password:
Disclaimer:
The information published in this article is only for educational purposes. The content of this article is based on my personal learning and experience. Any misuse of information will not be the responsibility of the author.
Feel free to point out any mistakes or let me know if there is anything I should add!
Источник
Linux Password Cracking: Explain unshadow and john Commands ( John the Ripper Tool )
John cracking modes
[donotprint]
| Tutorial details | |
|---|---|
| Difficulty level | Easy |
| Root privileges | Yes |
| Requirements | John the Ripper |
| Est. reading time | N/A |
[/donotprint] John the Ripper can work in the following modes:
[a] Wordlist : John will simply use a file with a list of words that will be checked against the passwords. See RULES for the format of wordlist files. [b] Single crack : In this mode, john will try to crack the password using the login/GECOS information as passwords. [c] Incremental : This is the most powerful mode. John will try any character combination to resolve the password. Details about these modes can be found in the MODES file in john’s documentation, including how to define your own cracking methods.
Install John the Ripper Password Cracking Tool
John the ripper is not installed by default. If you are using Debian / Ubuntu Linux, enter:
$ sudo apt-get install john
- No ads and tracking
- In-depth guides for developers and sysadmins at Opensourceflare✨
- Join my Patreon to support independent content creators and start reading latest guides:
- How to set up Redis sentinel cluster on Ubuntu or Debian Linux
- How To Set Up SSH Keys With YubiKey as two-factor authentication (U2F/FIDO2)
- How to set up Mariadb Galera cluster on Ubuntu or Debian Linux
- A podman tutorial for beginners – part I (run Linux containers without Docker and in daemonless mode)
- How to protect Linux against rogue USB devices using USBGuard
Join Patreon ➔
RHEL, CentOS, Fedora, Redhat Linux user can grab john the ripper here. Once downloaded use the rpm command as follows to install the same:
# rpm -ivh john*
How do I use John the ripper to check weak passwords or crack passwords?
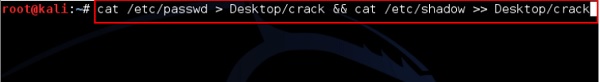
First use the unshadow command to combines the /etc/passwd and /etc/shadow files so John can use them. You might need this since if you only used your shadow file, the GECOS information wouldn’t be used by the “single crack” mode, and also you wouldn’t be able to use the -shells option. On a normal system you’ll need to run unshadow as root to be able to read the shadow file. So login as root or use old good sudo / su command under Debian / Ubuntu Linux :
$ sudo /usr/sbin/unshadow /etc/passwd /etc/shadow > /tmp/crack.password.db
RHEL / CentOS / Fedora Linux user type the following command:
# /usr/bin/unshadow /etc/passwd /etc/shadow > /tmp/crack.password.db
To check weak password (crack password), enter the following command:
CPU-time consuming password cracking techniques.
To use John, you just need to supply it a password file created using unshadow command along with desired options. If no mode is specified, john will try “single” first, then “wordlist” and finally “incremental” password cracking methods.
$ john /tmp/crack.password.db
Output:
This procedure will take its own time. To see the cracked passwords, enter:
$ john -show /tmp/crack.password.db
Above output clearly indicates that user test has 123456 and didi has abc123 password.
Related:
Further readings:
- John the ripper project home page.
- See john and unshadow command man pages.
- John the ripper examples text file
- John configuration file /etc/john/john.conf
- Rainbow table – Rainbow Cracking uses differs from brute force crackers in that it uses large pre-computed tables called rainbow tables to reduce the length of time needed to crack a password drastically. See Ophcrack Live CD.
🐧 Get the latest tutorials on Linux, Open Source & DevOps via
Источник
Kali Linux – Password Cracking Tool
Password cracking is a mechanism that is used in most of the parts of hacking. Exploitation uses it to exploit the applications by cracking their administrator or other account passwords, Information Gathering uses it when we have to get the social media or other accounts of the C.E.O. or other employees of the target organization, Wifi Hacking uses it when we have to crack the hash from the captured wifi password hash file, etc.
So to be a good Ethical hacker one must be aware of password cracking techniques. Though it is easy to crack passwords by just using guessing techniques, it is very time consuming and less efficient so in order to automate the task, we have a lot of tools. When it comes to tools Kali Linux is the Operating System that stands first, So here we have a list of tools in Kali Linux that may be used for Password Cracking.
1. Crunch
In order to hack a password, we have to try a lot of passwords to get the right one. When an attacker uses thousands or millions of words or character combinations to crack a password there is no surety that any one of those millions of combinations will work or not. This collection of a different combination of characters is called a wordlist. And in order to crack a password or a hash, we need to have a good wordlist which could break the password. So to do so we have a tool in Kali Linux called crunch.
crunch is a wordlist generating tool that comes pre-installed with Kali Linux. It is used to generate custom keywords based on wordlists. It generates a wordlist with permutation and combination. We could use some specific patterns and symbols to generate a wordlist.
To use crunch, enter the following command in the terminal.
2. RainbowCrack
Rainbow crack is a tool that uses the time-memory trade-off technique in order to crack hashes of passwords. It uses rainbow tables in order to crack hashes of passwords. It doesn’t use the traditional brute force method for cracking passwords. It generates all the possible plaintexts and computes the hashes respectively. After that, it matches hash with the hashes of all the words in a wordlist. And when it finds the matching hashes, it results in the cracked password.
To use RainbowCrack, enter the following command in the terminal.
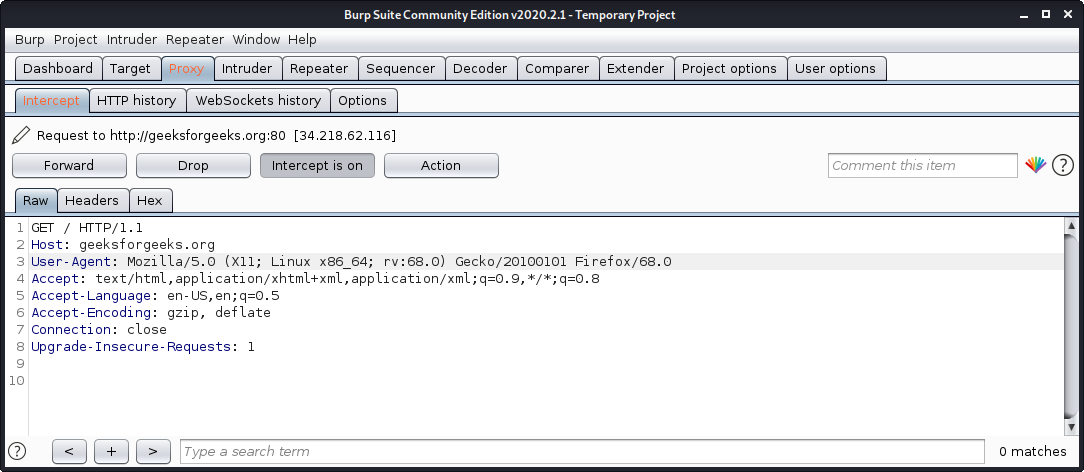
3. Burp Suite
Burp Suite is one of the most popular web application security testing software. It is used as a proxy, so all the requests from the browser with the proxy pass through it. And as the request passes through the burp suite, it allows us to make changes to those requests as per our need which is good for testing vulnerabilities like XSS or SQLi or even any vulnerability related to the web. Kali Linux comes with burp suite community edition which is free but there is a paid edition of this tool known as burp suite professional which has a lot many functions as compared to burp suite community edition. It comes with an intruder tool that automates the process of password cracking through wordlists.
To use burp suite:
- Read this to learn how to setup burp suite.
- Open terminal and type “burpsuite” there.
- Go to the Proxy tab and turn the interceptor switch to on.
- Now visit any URL and it could be seen that the request is captured.
4. Maltego
Maltego is a platform developed to convey and put forward a clear picture of the environment that an organization owns and operates. Maltego offers a unique perspective to both network and resource-based entities which is the aggregation of information delivered all over the internet – whether it’s the current configuration of a router poised on the edge of our network or any other information, Maltego can locate, aggregate and visualize this information. It offers the user with unprecedented information which is leverage and power.
Maltego’s Uses:
- It is used to exhibit the complexity and severity of single points of failure as well as trust relationships that exist currently within the scope of the infrastructure.
- It is used in the collection of information on all security-related work. It will save time and will allow us to work more accurately and in a smarter way.
- It aids us in thinking process by visually demonstrating interconnected links between searched items.
- It provides a much more powerful search, giving smarter results.
- It helps to discover “hidden” information.
To use Maltego: Go to applications menu and then select “maltego” tool to execute it.
5. John the Ripper
John the Ripper is a great tool for cracking passwords using some famous brute for attacks like dictionary attack or custom wordlist attack etc. It is even used to crack the hashes or passwords for the zipped or compressed files and even locked files as well. It has many available options to crack hashes or passwords.
To use John the Ripper
- John the ripper comes pre-installed in Kali Linux.
- Just type “john” in the terminal to use the tool.
Источник