- Freeing up a TCP/IP port?
- 11 Answers 11
- How to free port linux
- This distribution contains preinstalled service UFW(Uncomplicated Firewall) by default. It simplifies the whole configuration and it is user-friendly for every person.
- Firewalld is more advanced tool which uses zones in its configuration. They are responsible for taking care of some area, or one “attached” network interface.
- That’s the quick tutorial for firewalld.
- Ubuntu: How To Free Up Port 53, Used By systemd-resolved
- How to stop systemd-resolved from using port 53 on Ubuntu
- How to undo the changes
- How to close an open port in Ubuntu?
- 7 Answers 7
- What’s the easiest way to find an unused local port?
- 17 Answers 17
- One-liner
- Line by line
- Example
Freeing up a TCP/IP port?
netstat -tulnap shows me what ports are in use. How to free up a port in Linux?
11 Answers 11
As the others have said, you’ll have to kill all processes that are listening on that port. The easiest way to do that would be to use the fuser(1) command. For example, to see all of the processes listening for http requests on port 80 (run as root or use sudo):
If you want to kill them, then just add the -k option.
To a kill a specific port in Linux use below command
replace Port_Number with your occupied port.
In terminal type :
netstat -anp|grep «port_number»
It will show the port details. Go to last column. It will be in this format . For example :- PID/java
kill -9 PID. Worked on Centos5
and then execute :
Worked on Macbook
You can use tcpkill (part of the dsniff package) to kill the connection that’s on the port you need:
To check all ports:
To close an open port:
In both cases you can use the sudo command if needed.
The «netstat —programs» command will give you the process information, assuming you’re the root user. Then you will have to kill the «offending» process which may well start up again just to annoy you.
Depending on what you’re actually trying to achieve, solutions to that problem will vary based on the processes holding those ports. For example, you may need to disable services (assuming they’re unneeded) or configure them to use a different port (if you do need them but you need that port more).
Kill the process that is listening to the port in question. I believe netstat shows you process ids.
the last column has the process
If you really want to kill a process immediately, you send it a KILL signal instead of a TERM signal (the latter a request to stop, the first will take effect immediately without any cleanup). It is easy to do:
Be aware however that depending on the program you are stopping, its state may get badly corrupted when doing so. You normally only want to send a KILL signal when normal termination does not work. I’m wondering what the underlying problem is that you try to solve and whether killing is the right solution.
I think the only way will be to stop the process which has opened the port.
sudo killall -9 «process name»
Shutting down the computer always kills the process for me.
Источник
How to free port linux
We might try to start with the firewall definition which is needed to fulfil understanding of «port-vocabulary». Firewall is software or firmware that enforces a set of rules about what data packets will be allowed to enter or leave a network. It is in charge of managing Allow and Deny rules for ports.
Accordingly to the topic of this guide we would like to open ports in Linux distributions such as Ubuntu or CentOS. Both distros allow to configure it with different set of tools (firewalls packages) but with the same results.
Tools that we will be using:
Let’s have a look at the Ubuntu scenario first:
This distribution contains preinstalled service UFW(Uncomplicated Firewall) by default. It simplifies the whole configuration and it is user-friendly for every person.
Check the service status with standard systemctl command:
Enable UFW with enable command:
Syntax to open specific TCP port:
Syntax supports also names which reffer to specific ports:
To allow incoming tcp and udp packet on port 21, enter:
Example for specific IP Address:
Let’s check the configuration:
Command displays a provisional table with three columns:
Explanations:
• To – describes the particular protocol
• Action – tells us whether it is allowed or denied
• From – It says about the source e.g anywhere or one ip address like presented above
It’s time for CentOS already:
Firewalld is more advanced tool which uses zones in its configuration. They are responsible for taking care of some area, or one “attached” network interface.
Firewalld is frontend controller for iptables used to implement persistent network traffic rules.
Let’s take a look for a bunch of commands that elaborate with firewalld.
1. Start our service with stardand systemctl command:
This command informs us about state of service. It may only display two sentences: “running” or “no running”
Default zone is public. In this short tutorial we will not be changing it, but if you would like to then use this commands:
Let’s try to add tcp traffic on port 1112:
TO reload and get those changes applied instantly we have to reload the firewalld state.
We may obtain a readable review of our new rule with listing command:
To allow a ssh connection on specific Ipv4 we have to use syntax with “rich rule”
That’s the quick tutorial for firewalld.
Hint:
Firewall is the default package for CentOS to manage incoming and outcoming traffic. If the UFW seems more preferable for you may install those packages too.
Источник
Ubuntu: How To Free Up Port 53, Used By systemd-resolved
Ubuntu has systemd-resolved listening on port 53 by default. In case you want to run your own DNS server, you can’t because port 53 is already in use, so you’ll get an error similar to this: «listen tcp 0.0.0.0:53: bind: address already in use».
This article explains how to stop systemd-resolved from using port 53 on Ubuntu. The instructions were tested on Ubuntu 20.04, but they should also work on other Ubuntu versions, e.g. Ubuntu 18.04, the upcoming Ubuntu 20.10, as well as Ubuntu-based Linux distributions like Pop!_OS, Zorin OS, Elementary OS, Linux Mint, and so on. Basically, this works on any system having systemd version 232 or newer.
To see if port 53 is in use on your system, use:
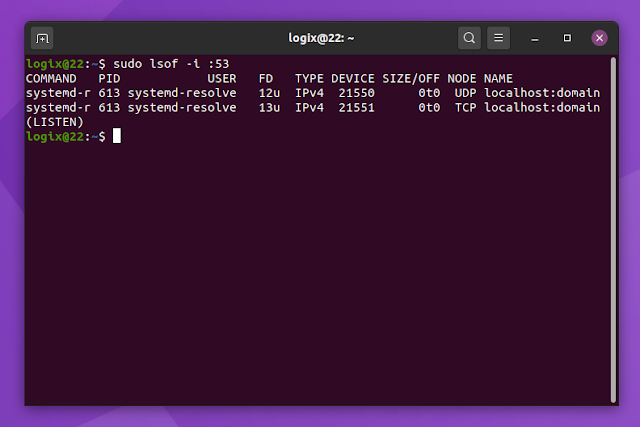
Example with output, showing that systemd-resolved is using port 53 on a default Ubuntu 20.04 system:
In case you don’t get any output, it means that port 53 is not in use.
How to stop systemd-resolved from using port 53 on Ubuntu
It’s worth noting that you can free up port 53 by simply uncommenting DNSStubListener and setting it to no in /etc/systemd/resolved.conf . The other steps are for enabling a DNS server — without it, your system will not be able to resolve any domain names, so you won’t be able to visit websites in web browser, etc.
1. Edit /etc/systemd/resolved.conf with a text editor (as root), e.g. open it with Nano console text editor:
And uncomment (remove # from the front of the line) the DNS= line and the DNSStubListener= line. Next, change the DNS= value in this file to the DNS server you want to use (e.g. 127.0.0.1 to use a local proxy, 1.1.1.1 to use the Cloudflare DNS, etc.), and also change the DNSStubListener= value from yes to no .
This is how the file should look after you’ve made these changes (I’m using 1.1.1.1 as the DNS server here, which is the Cloudflare DNS):
To save the file using Nano text editor, press Ctrl + x , then type y and press Enter .
2. Create a symbolic link for /run/systemd/resolve/resolv.conf with /etc/resolv.conf as the destination:
Here, -s is for creating a symbolic and not hard link, and -f is for removing any existing destination files (so it removes /etc/resolv.conf if it exists).
3. Reboot your system.
Port 53 should now be free on your Ubuntu system, and you shouldn’t be getting errors like «listen tcp 127.0.0.1:53: bind: address already in use» anymore.
You can check to see if port 53 is in use or not by running sudo lsof -i :53 — if port 53 is not in use, this command shouldn’t show any output.
How to undo the changes
Do you want to undo the changes made by following the instructions in this article? This is what you must do.
1. Start by editing /etc/systemd/resolved.conf with a text editor (as root), e.g. open it with Nano console text editor:
And comment out (add # in front of the line) DNS= and DNSStubListener=no , then save the file. To save the file using Nano text editor, press Ctrl + x , then type y and press Enter .
Источник
How to close an open port in Ubuntu?
I need a command to list all open ports in my PC, and another command to close a port.
I need to close some applications’ port.
7 Answers 7
netstat can be used to see the ports stat.
To list all Listening ports Numbers with the Process responsible on each one. Terminate or kill the process to close port. ( kill , pkill . )
Without process termination, It is not possible! . See Manually closing a port from command line. Other way you may look for a firewall solution (as isolating that port from network)
for closing open port in ubuntu you can use below command
in place of 3000 you can specify your port number
lsof command will give information about file opened by process
-t : This flag specifies that lsof should produce terse output with process identifiers only and no header — e.g., so that the output may be piped to kill(1). This option selects the -w option.
-i : This flag selects the listing of files any of whose Internet address matches the address specified in i. If no address is specified, this option selects the listing of all Internet and x.25 (HP-UX) network files.
Источник
What’s the easiest way to find an unused local port?
What’s the easiest way to find an unused local port?
Currently I’m using something similar to this:
It feels awfully roundabout, so I’m wondering if there’s a more simple path such as a builtin that I’ve missed.
17 Answers 17
My solution is to bind to port 0, which asks the kernel to allocate a port from it’s ip_local_port_range. Then, close the socket and use that port number in your configuration.
This works because the kernel doesn’t seem to reuse port numbers until it absolutely has to. Subsequent binds to port 0 will allocate a different port number. Python code:
This gives just a number of a port, eg. 60123 .
Run this program 10 000 times (you should run these concurrently), and you’ll get 10 000 different port numbers. Therefore, I think it’s pretty safe to use the ports.
If your application supports it, you can try passing port 0 to the application. If your application passes this to the kernel, the port will be dynamically allocated at request time, and is guaranteed not to be in use (allocation will fail if all ports are already in use).
Otherwise, you can do this manually. The script in your answer has a race condition, the only way to avoid it is to atomically check if it is open by trying to open it. If the port is in use, the program should quit with a failure to open the port.
For example, say you’re trying to listen with GNU netcat.
One-liner
I’ve put together a nice one-liner that quickly serves the purpose, allowing to grab an arbitrary number of ports in an arbitrary range (here it’s divided in 4 lines for readability):
Line by line
comm is a utility that compares lines in two files that must appear sorted alphabetically. It outputs three columns: lines that appear only in the first file, lines that only appear in the second one and common lines. By specifying -23 we suppress the latter columns and only keep the first one. We can use this to obtain the difference of two sets, expressed as a sequence of text lines. I learned about comm here.
The first file is the range of ports that we can select from. seq produces a sorted sequence of numbers from $FROM to $TO . The result is sorted alphabetically (instead of numerically, in order to comply with comm s requirement) and piped to comm as the first file using process substitution.
The second file is the sorted list of ports, that we obtain by calling the ss command (with -t meaning TCP ports, -a meaning all — established and listening — and -n numeric — don’t try to resolve, say, 22 to ssh ). We then pick only the fourth column with awk , which contains the local address and port. We use cut to split address and port with the : delimiter and keep only the latter ( -f2 ). We then comply with comm ‘s requirement by sort ing without duplicates -u .
Now we have a sorted list of open ports, that we can shuf fle to then grab the first «$HOWMANY» ones with head -n .
Example
Grab the three random open ports in the private range (49152-65535)
Источник