- Гостевая статья BeEF 101 — Фреймворк для браузера
- Hacking with BeEF
- Installing the BeEF Framework
- Welcome to BeEF
- Using BeEF
- Hooking a Browser
- Conclusion
- About the author
- Younis Said
- My script to Install Beef-xss in kali-linux from github and resolving all Problem’s with kali beef #1356
- Comments
- ziflar commented Feb 8, 2017 •
- step’s to Install it
- kalifan commented Feb 9, 2017 •
- ziflar commented Feb 10, 2017 •
- any time you want an update of beef from github just open a terminal and tape:
- kalifan commented Feb 10, 2017
- InnerSoul commented Mar 24, 2017
- kalifan commented Mar 26, 2017
- KewL-1 commented Sep 26, 2017
- BeEF — Control Any Browser Remotely
Гостевая статья BeEF 101 — Фреймворк для браузера
В этом посте я объясню BeEF, как его установить и протестировать установку, выполнив небольшую атаку на мою систему.
BeEf или Browser Exploitation Framework — один из самых мощных арсеналов Kali Linux, который позволяет осуществлять атаку на стороне клиента против веб-браузеров. JavaScript может быть очень мощным и опасным. Эта инфраструктура может использовать преимущества XSS или межсайтовых сценариев, которые являются критической уязвимостью (как упоминается OWASP), обнаруженной на веб-страницах, для внедрения Java-скрипта и получения контроля над браузером, а иногда и всей системой.
Как установить BeEF?
Установка BeEF довольно проста. Все, что вам нужно, это компьютер Kali Linux с активным подключением к Интернету. Сначала убедитесь, что у вас есть нужные репозитории, добавленные в файл /etc/apt/sources file. После добавления мы можем установить этот фреймворк, выполнив две команды.
Запустите терминал и выполните
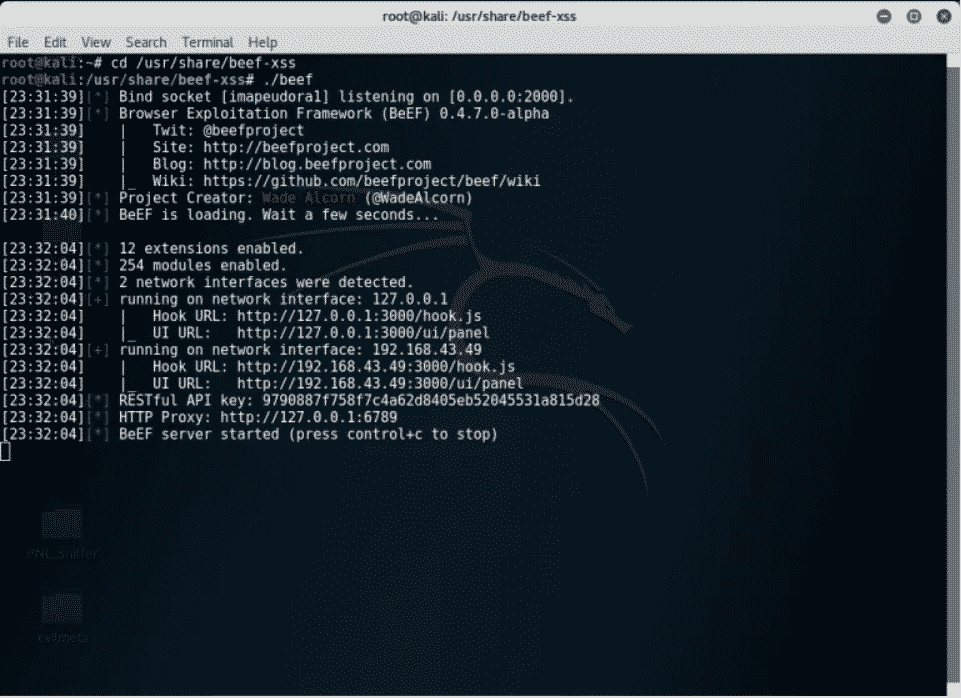
Запуск BeEF
Как только он установлен, вы можете запустить говядину, просто набрав beef-xss в терминале
Здесь мы увидим кое-что, что мы будем использовать в будущем. При запуске фреймворка вы увидите слово hook.js несколько раз. Прежде чем идти дальше, вы должны знать, что такое «крючок BeEF», который является источником атаки.
Что такое BeEF?
BeEF hook — это тщательно разработанный java-скрипт, который хранится на компьютере (сервере) злоумышленников, который должен выполняться в целевом веб-браузере, чтобы успешно скомпрометировать его. Когда этот код будет выполнен на целевой машине, он отправит обратно столько ценной информации о машине и браузере жертвы. Это также позволяет другим модулям в BeEF работать с машиной жертвы.
Вот так выглядит hook.js.
Доступ к интерфейсу
В большинстве случаев он автоматически запускает браузер для вас, но если это не так, вам просто нужно открыть браузер и перейти к
http://:3000/ui/panel
Или, если вы используете тот же компьютер, вы можете получить к нему доступ с помощью:
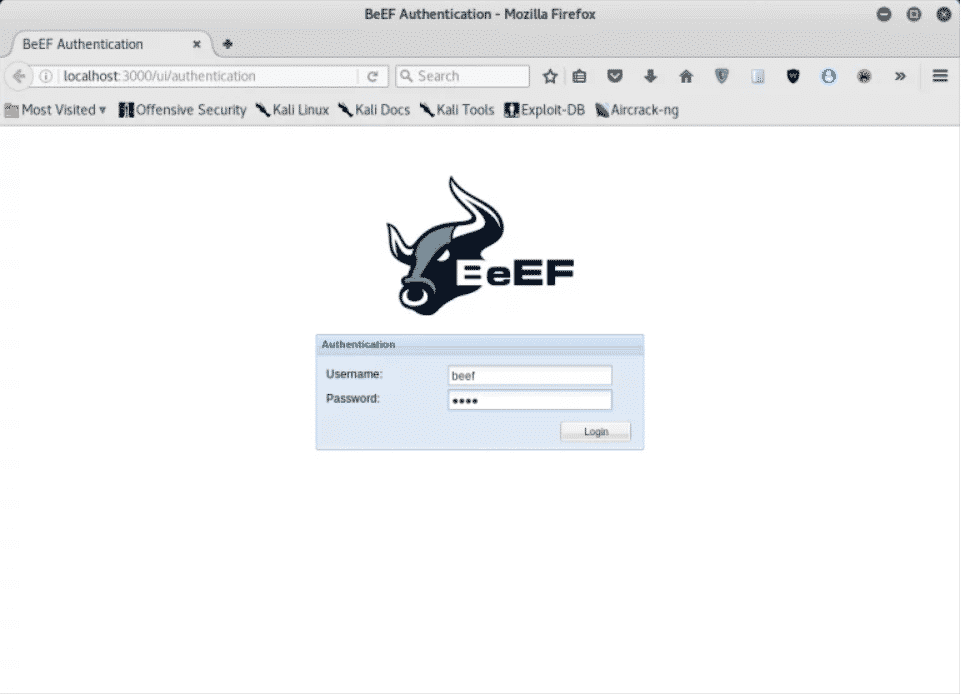
http://localhost:3000/ui/panel or http://127.0.0.1:3000/ui/panel
Имя пользователя по умолчанию: beef и Пароль по умолчанию: beef
После успешной отправки учетных данных вы будете перенаправлены на панель инструментов.
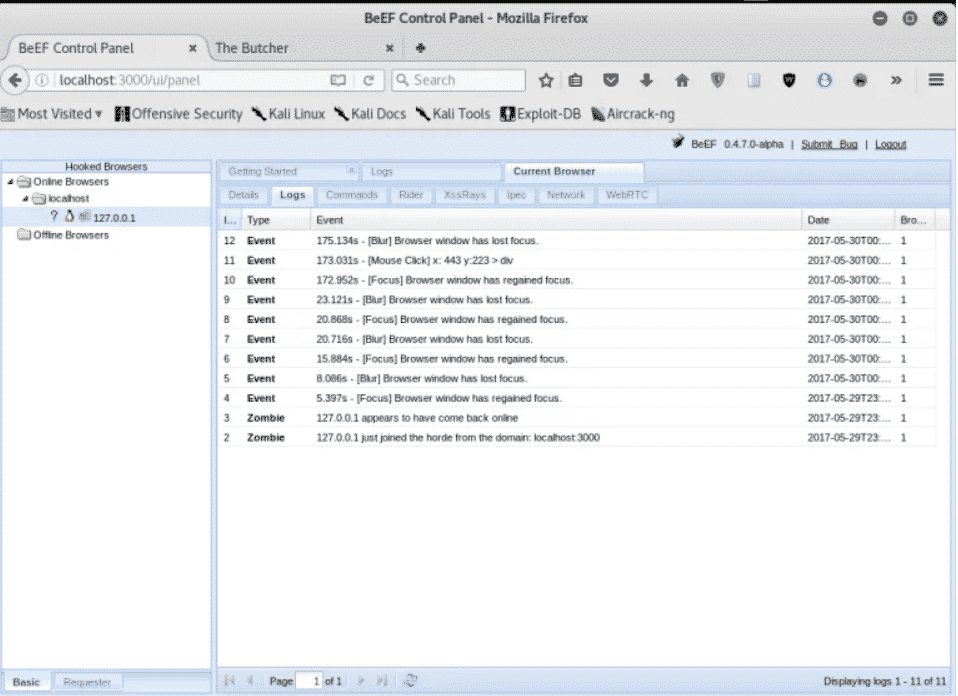
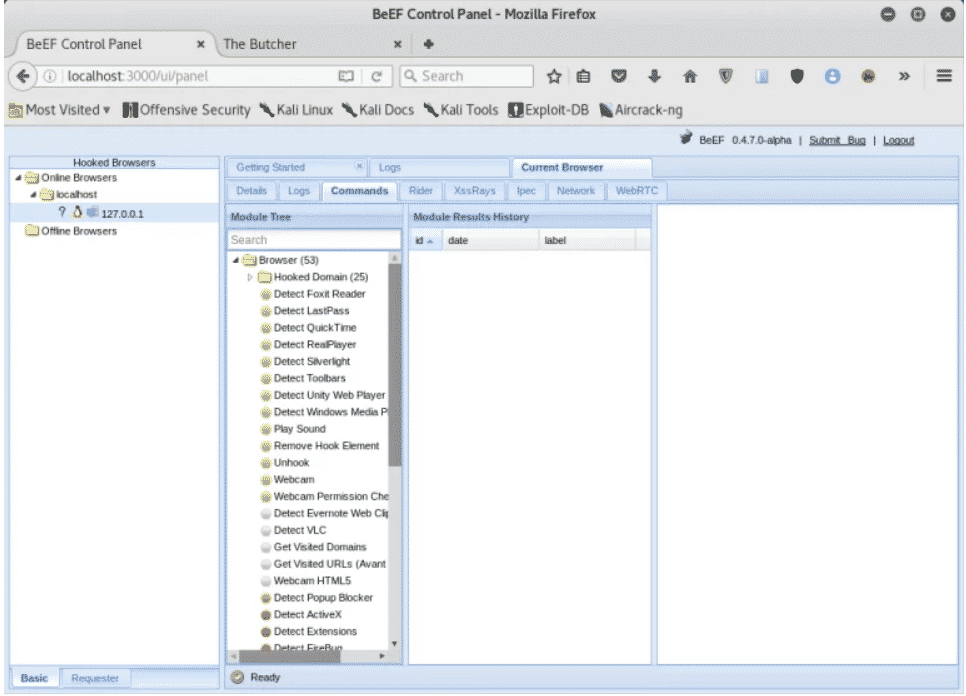
Это основная панель управления. Здесь вы можете увидеть все подробности обо всех подключенных браузерах, его IP-адресе, версии, доступности, возможных атаках и т. Д. Отсюда вы можете запускать атаки на различные цели, которые находятся в режиме онлайн.
Тестирование — наша первая атака
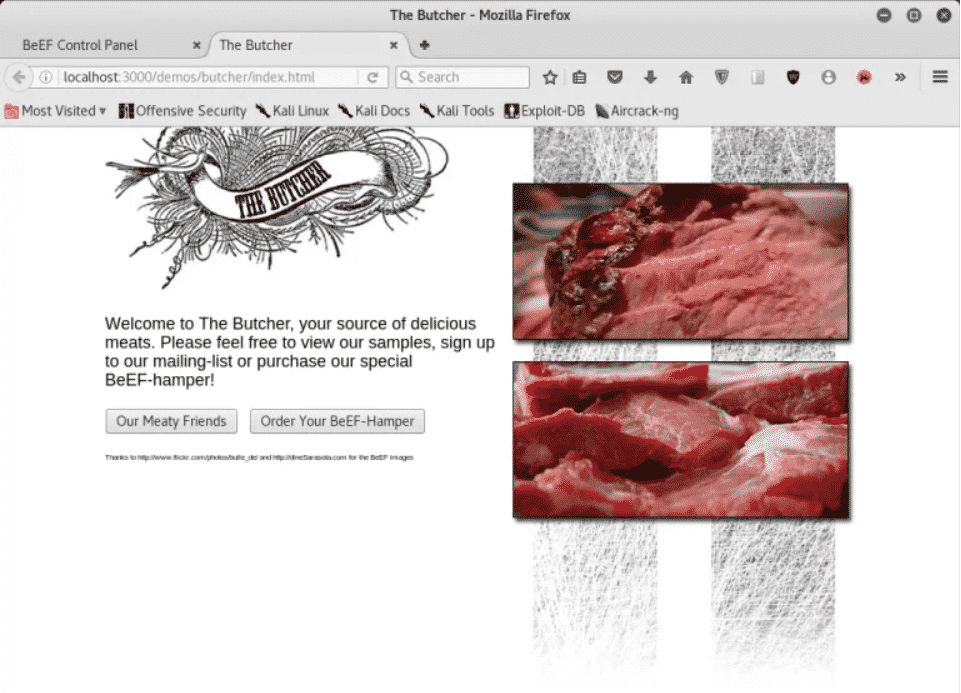
Все отлично сработало, теперь пришло время проверить, как это работает. Для этого я открою демонстрационную веб-страницу, в которую уже встроен hook.js, и посмотрю, не перехватывает ли он мой браузер и не запускает ли небольшую фишинговую атаку.
Я открыл демонстрационную страницу, и, как вы видите на этом изображении, она уже подключила мой браузер.
На вкладке команд я собираюсь выбрать модуль Google Phishing из категории «Социальная инженерия». Как только это выбрано, нажмите выполнить.
Как вы можете видеть, демонстрационная страница изменилась на поддельную страницу входа в Google.
Когда пользователь пытается войти в систему из браузера, учетные данные будут отправлены обратно на сервер, и пользователь будет перенаправлен на страницу реального входа в Gmail.
Это всего лишь представление о том, что вы можете сделать с помощью этой платформы. Как упоминалось ранее, это структура с бесконечными возможностями. Все ограничено вашей фантазией.
Источник
Hacking with BeEF
BeEF has a very capable, yet straightforward, API that serves as the pivot upon which its efficiency stands and grows out into an imitation of a full-fledged cyber attack.
This short tutorial will take a look at several ways that this flexible and versatile tool can be of use in pen-testing.
Installing the BeEF Framework
A Linux OS such as Kali Linux, Parrot OS, BlackArch, Backbox, or Cyborg OS is required to install BeEF on your local machine.
Although BeEF comes pre-installed in various pen-testing operating systems, it might be possible that it is not installed in your case. To check if whether BeEF is installed, look for BeEF in your Kali Linux directory. To do so, go to applications>Kali Linux>System Services>beef start.
Alternatively, you can fire up BeEF from a new terminal emulator by entering the following code:
To install BeEF on your Kali Linux machine, open the command interface and type in the following command:
BeEF should now be installed under /usr/share/beef-xss.
You can start using BeEF using the address described previously in this section.
Welcome to BeEF
Now, you can see the BeEF GUI in its full glory. Access the BeEF server by launching your web browser and looking up the localhost (127.0.0.1).
You can access the BeEF web GUI by typing the following URL in your web browser:
The default user credentials, both the username and password, are “beef:”
Now that you have logged into the BeEF web GUI, proceed to the “Hooked Browsers” section. Online Browsers and Offline Browsers. This section shows the victim’s hooked status.
Using BeEF
This walkthrough will demonstrate how to use BeEF in your local network using the localhost.
For the connections to be made outside the network, we will need to open ports and forward them to the users waiting to connect. In this article, we will stick to our home network. We will discuss port forwarding in future articles.
Hooking a Browser
To get to the core of what BeEF is about, first, you will need to understand what a BeEF hook is. It is a JavaScript file, used to latch on to a target’s browser to exploit it while acting as a C&C between it and the attacker. This is what is meant by a “hook” in the context of using BeEF. Once a web browser is hooked by BeEF, you can proceed to inject further payloads and begin with post-exploitation.
To find your local IP address, you open a new terminal and enter the following:
Follow the steps below to perform the attack:
- To target a web browser, you will first need to identify a webpage that the victim to-be likes to visit often, and then attach a BeEF hook to it.
- Deliver a javascript payload, preferably by including the javascript hook into the web page’s header. The target browser will become hooked once they visit this site.
If you have been able to follow these steps without any problems, you should be able to see the hooked IP address and OS platform in the BeEF GUI. You can find out more about the compromised system by clicking on the hooked browser listed in the window.
Also, there are several generic webpage templates they have made available for your use.
You can glean all sorts of information from here, such as the plugins and extensions that the browser is using, and various information about the hardware and software specs of the target.
The BeEF framework goes so far as to create complete logs of mouse movements, double-clicks, and other actions performed by the victim.
Here is a list of available modules that can be used to breach a designated system. These modules include keyloggers and spyware, including the ones that use the webcams and microphones of the target browser.
Note that certain commands have a colored icon. These icons all have different connotations that you can find out by taking the ‘getting started’ introductory tour, which introduces various aspects of the BeEF interface. Also, notice how each module has a traffic light icon associated with it. These traffic symbols are used to indicate any of the following:
- The command module works against the target and should be invisible to the user
- The command module works against the target but may be visible to the user
- The command module has yet to be verified against this target
- The command module does not work against this target
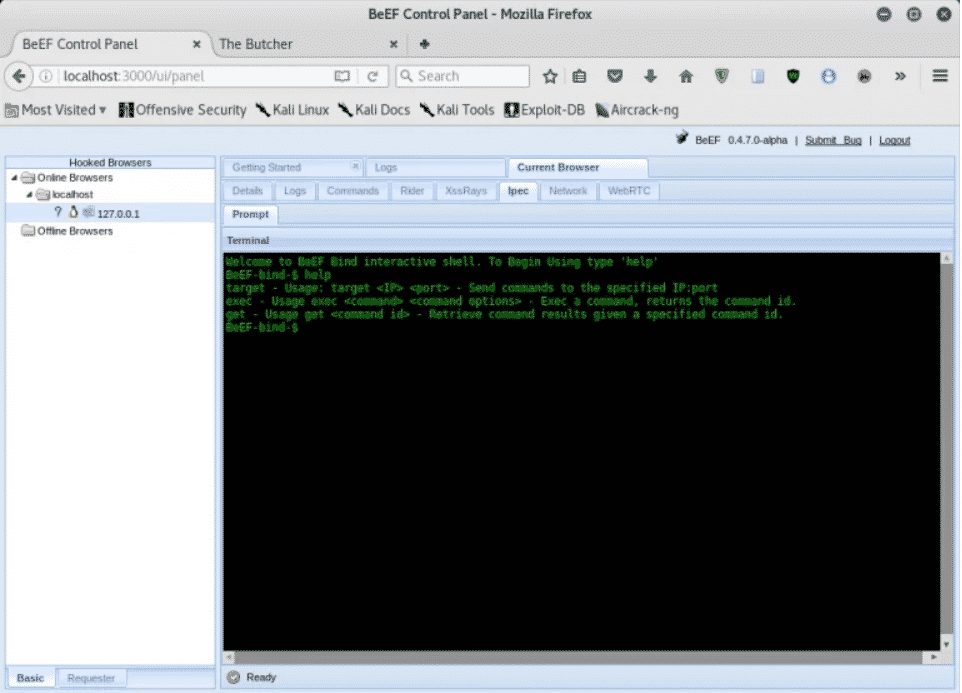
You can also send shell commands to the target system, as shown below:
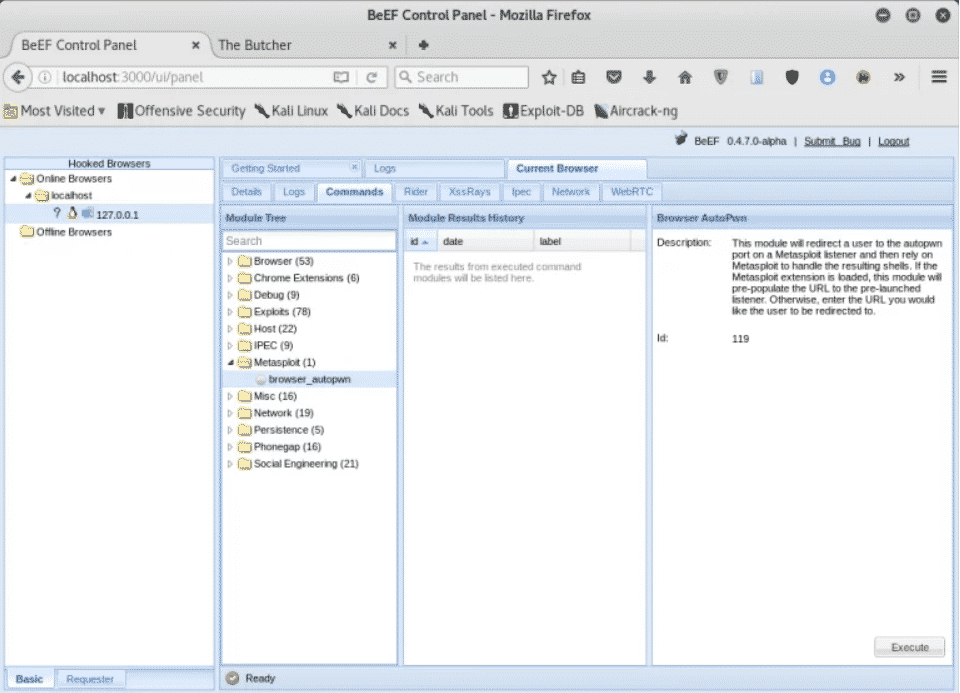
Coupled with Metasploit, BeEF can be used to perform quite varied and intricate system exploitation using modules, such as browser_auto_pwn.
Conclusion
BeEF is an incredibly powerful tool that you can use to fortify systems against cyberattacks. From providing spyware modules to tracking mouse movement on the targeted system, BeEF can do it all. It is a good idea, therefore, to test your system using this security forensics tool.
Hopefully, you found this tutorial useful to get you started with this tool with such diverse, useful functionality.
About the author
Younis Said
I am a freelancing software project developer, a software engineering graduate and a content writer. I love working with Linux and open-source software.
Источник
My script to Install Beef-xss in kali-linux from github and resolving all Problem’s with kali beef #1356
Comments
ziflar commented Feb 8, 2017 •
To resolve all problem’s with beef-xss in kali linux :
i’ve edited a script to install it from github :
step’s to Install it
let’s the script delete beef insalled in kali and it’s clone the new one from github
The text was updated successfully, but these errors were encountered:
kalifan commented Feb 9, 2017 •
what do you mean when you say resolve all problems? what are these problems or what do you fix thank you..
ziflar commented Feb 10, 2017 •
@kalifan
My script was edited 6 months before to fix beef problem’s on kali rolling as hocked browser and login panel:
On kali linux beef and metasploit are late for their upgrade not as on github.
The update on kali may take months to go from one version to another new one .
Then my script can simply install beef from github and proceed to its update any time we want and keep on use as beef kali
any time you want an update of beef from github just open a terminal and tape:
cd /usr/share/beef-xss/ && ./update-beef
thx @+
kalifan commented Feb 10, 2017
@ziflar thanks my friend.
InnerSoul commented Mar 24, 2017
@ziflar @beefproject still it is not loading with metasploit modules 🙁 i kept metasploit extension to true and changed the host and callback host to my ip, and loaded msgrpc plugin in metasploit, but still beef is not loading with metasploit modules. can you say the steps for making it work?
kalifan commented Mar 26, 2017
@InnerSoul Hi maybe here is the solution for your problem:
#1322
KewL-1 commented Sep 26, 2017
Awesome script bro keep up the good work and thanks!
Источник
BeEF — Control Any Browser Remotely
The Browser Exploitation Framework (BeEF) is a penetration testing tool focused on client-side attacks executed within a browser. Oh, Yes it includes lots of exploits.
Previously BeEF comes pre-installed with Kali Linux, but now it doesn’t comes pre-installed. But it is available in Kali Linux repository. We can install it on Kali Linux or other similar Linux distribution by applying following command:
The following screenshot shows the output of the preceding command:
It may consume our time depending on our internet speed and processing speed.
BeEF can be opened from the terminal using beef-xss command:
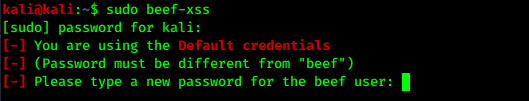
If we are opening for the first time we need to set a new password to log in BeEF control panel.
After setting up a new password for default user beef the tool will be started as we can see in the following screenshot:
Now we can access the web based user interface (Web UI) in our browser. We don’t know why but BeEF tries to open our browser automatically but failed (Hey BeEF, don’t worry we can open it manually). We need to open our browser and navigate to http://127.0.0.1:3000/ui/panel and we are in the BeEF’s login page.
Now here we type beef as default user and our chosen password and press login.
We are logged in in our BeEF control panel.
Now we need to «hook» a browser.
BeEF is providing us a basic demo page and a advanced page to hook a browser as we can see in the above screenshot.
Let’s check it by clicking on the advanced version.
We can see in the above picture this is the advanced page to hook browser. Which browser opens this will be hooked (even own browsers also) and we got control of the browser.
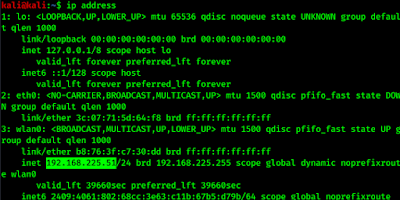
But this runs on localhost to send it another person in our local network we need to use 192.168.XX.XXX (Local IP address) in the place of 127.0.0.1. Local IP address can be found by typing ip address command in terminal.
Now we need to send this to anyone in our local network with some juicy social engineering techniques. Whenever our target opens this link with a browser the browser will be hooked.
We have send our this hooking url http://192.168.225.51:3000/demos/butcher/index.html to our another PC and open this link their.
In our attacker machine we got one online hooked browser.
We need to click over the hooked browser’s ip address.
Now we are on current browser section. Here we can see all the details about our browser and we can run exploits.
To run exploit commands we need to navigate on the commands tab.
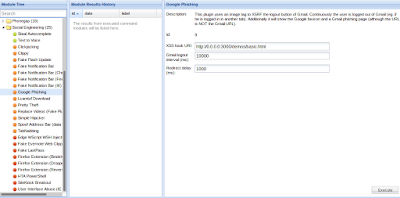
For an example in this tutorial we run a basic exploit command on our hooked browser. We go social engineering menu and select the Google phishing and click on execute.
Now if we enter credentials on targeted PC we got them on our attacker machine.
Not only creating phishing page crating BeEF have lots of advanced exploits. It can take snaps from webcam, it is dangerous when attacker integrated BeEF with metasploit.
Browser Exploitation Framework hooks the browser by a JavaScript inside a normal HTML page, it exposes restful API that allow BeEF to be scripted through HTTP/JSON requests.
To use BeEF over internet we need to use our external ip in the place of our internal ip address. We also need to forward default 3000 port.
Источник