- How to prevent and remove viruses and other malware
- How to Use CMD to Remove Virus from Any Drive in Windows 10
- What Damage Could Viruses Do
- Why Can You Remove a Virus Using CMD
- How to Remove Virus Using CMD
- 3 Other Ways to Remove Virus
- Method 1. Run Antivirus
- Method 2. Run Windows Defender Antivirus
- Method 3. Format the Infected Device
- How to Recover Files Deleted/Hidden by Viruses
- How to Prevent Virus or Malware Infections
- The Bottom Line
How to prevent and remove viruses and other malware
What is a computer virus?
A computer virus is a small software program that spreads from one computer to another and interferes with computer operation. A computer virus might corrupt or delete data on a computer, use an email program to spread the virus to other computers, or even delete everything on the hard disk.
Computer viruses are frequently spread by attachments in email messages or by instant messaging messages. Therefore, you must never open an email attachment unless you know who sent the message or you are expecting the email attachment. Viruses can be disguised as attachments of funny images, greeting cards, or audio and video files. Computer viruses also spread through downloads on the Internet. They can be hidden in pirated software or in other files or programs that you might download.
Symptoms of a computer virus
For information about the symptoms of a computer virus, go to the
Microsoft PC Security website.
A worm is computer code that spreads without user interaction. Most worms begin as email attachments that infect a computer when they’re opened. The worm scans the infected computer for files, such as address books or temporary webpages, that contain email addresses. The worm uses the addresses to send infected email messages, and frequently mimics (or spoofs) the «From» addresses in later email messages so that those infected messages seem to be from someone you know. Worms then spread automatically through email messages, networks, or operating system vulnerabilities, frequently overwhelming those systems before the cause is known. Worms aren’t always destructive to computers, but they usually cause computer and network performance and stability problems.
What is a trojan horse?
A trojan horse is a malicious software program that hides inside other programs. It enters a computer hidden inside a legitimate program, such as a screen saver. Then it puts code into the operating system that enables a hacker to access the infected computer. Trojan horses do not usually spread by themselves. They are spread by viruses, worms, or downloaded software.
What is spyware?
Spyware can install on your computer without your knowledge. These programs can change your computer’s configuration or collect advertising data and personal information. Spyware can track Internet search habits and can also redirect your web browser to a different website than you intend to go to.
What is rogue security software?
A rogue security software program tries to make you think that your computer is infected by a virus and usually prompts you to download or buy a product that removes the virus. The names of these products frequently contain words like Antivirus, Shield, Security, Protection, or Fixer. This makes them sound legitimate. They frequently run right after you download them, or the next time that your computer starts. Rogue security software can prevent applications, such as Internet Explorer, from opening. Rogue security software might also display legitimate and important Windows files as infections. Typical error messages or pop-up messages might contain the following phrases:
Warning!
Your computer is infected!
This computer is infected by spyware and adware.
Note If you receive a message in a popup dialog box that resembles this warning, press ALT + F4 on your keyboard to close the dialog box. Do not click anything inside the dialog box. If a warning, such as the one here, keeps appearing when you try to close the dialog box, it’s a good indication that the message is malicious.
Are you sure you want to navigate from this page?
Your computer is infected! They can cause data lost and file corruption and need to be treated as soon as possible. Press CANCEL to prevent it. Return to System Security and download it to secure your PC.
Press OK to Continue or Cancel to stay on the current page.
If you see this kind of message, then don’t download or buy the software.
What is malware?
Malware is a term that is used for malicious software that is designed to do damage or unwanted actions to a computer system. Examples of malware include the following:
Rogue security software
How to remove malware such as a virus, spyware, or rogue security software
Removing a computer virus or spyware can be difficult without the help of malicious software removal tools. Some computer viruses and other unwanted software reinstall themselves after the viruses and spyware are detected and removed. Fortunately, by updating the computer and by using malicious software removal tools, you can help permanently remove unwanted software.
For more information about how to remove a computer virus and spyware, see the following article in the Microsoft Knowledge Base:
2671662 — Microsoft resources and guidance for removal of malware and viruses Note If you cannot access the Internet on your computer, use another computer to help you follow the steps in the “How to reset your Internet Explorer proxy settings” section on the computer that may be infected.
To remove a computer virus and other malicious software, follow these steps in order.
Install the latest updates from Microsoft Update
Note A computer virus may prevent you from accessing the Microsoft Update website to install the latest updates. We recommend that you set the Automatic Updates service to run automatically so that a computer is not missing any important updates. For more information, see the following article in the Microsoft Knowledge Base:
Click Start, and then type Windows Update in the search box.
In the results area, click Windows Update.
Click Check for Updates.
Follow the instructions to download and install the latest Windows Updates.
Use the free Microsoft Safety Scanner
Microsoft offers a free online tool that scans and helps remove potential threats from your computer. To perform the scan, go to the Microsoft Safety Scanner website.
Use the Windows Malicious Software Removal Tool
For more information about the Microsoft Malicious Software Removal Tool, see the following article in the Microsoft Knowledge Base:
890830 — Remove specific prevalent malware with Windows Malicious Software Removal Tool
Manually remove the rogue security software
If the rogue security software can’t be detected or removed by using Microsoft Safety Scanner or the Windows Malicious Software Removal Tool, try the following steps:
Note the name of the rogue security software. For this example, we’ll call it XP Security Agent 2010.
Restart your computer.
When you see the computer’s manufacturer’s logo, repeatedly press the F8 key.
When you are prompted, use the arrow keys to highlight Safe Mode with Networking, and then press Enter.
Click the Start button and check whether the rogue security software appears on the Start menu. If it’s not listed there, click All Programs and scroll to find the rogue security software’s name.
Right-click the name of the rogue security software program, and then click Properties.
Click the Shortcut tab.
In the Properties dialog box, check the path of the rogue security software program that is listed in Target. For example, C:\Program Files\XP Security Agent 2010.
Note The folder name frequently is a random number.
Click Open File Location.
In the Program Files window, click Program Files in the address bar.
Scroll until you find the rogue security software program folder. For example, XP Security Agent 2010.
Right-click the folder, and then click Delete.
Restart your computer.
Click the Download Now button, and then click Run.
Follow the instructions to scan your computer and help remove the rogue security software.
If you suspect that your computer is infected with rogue security software that was not detected by using Microsoft security solutions, you can submit samples by using the Microsoft Malware Protection Center submission form.
For more information about rogue security software, go to the Watch out for fake virus alerts website.
Install and run Microsoft Security Essentials or Windows Defender
Microsoft offers a free malicious removal program called Microsoft Security Essentials that helps protect your computer from becoming infected. To install Microsoft Security Essentials, follow these steps:
Click Free Download.
Click Run, and then follow the instructions to install Microsoft Security Essentials.
After installation, restart your computer.
Click Start, click All Programs, and then click Microsoft Security Essentials.
On the Home tab, select the Full scan option, and then click Scan now.
Install Windows Defender Offline
Windows Defender Offline is a malware tool that helps remove difficult to eliminate viruses that start before Windows starts. To use Windows Defender Offline, follow these steps:
On an uninfected computer, go to the What is Windows Defender Offline website.
Click Download the 32 bit version or Download the 64 bit version, depending on which operating system that you are running. If you’re unsure of which operating system that you are running, go to the Is my PC running the 32-bit or 64-bit version of Windows website.
When you are prompted, click Save As, and then save the file to a DVD, CD, or USB flash drive.
On the infected computer, insert the DVD, CD, or USB flash drive, and then restart the computer.
When you are prompted, press a key to select an option to use to start your computer, such as F12, F5, or F8, depending on the kind of computer that you are using.
Use the arrow key to scroll to the drive where you installed Windows Defender Offline file. Windows Defender Offline starts and immediately scans for malware.
For more information about how to remove a computer virus, go to the How do I remove a computer virus website.
How to protect your computer against malware
There are actions that you can take to help protect your computer against malware.
Turn on the firewall
Click the Start button, and then click Control Panel.
In the Search box, type firewall, and then click Windows Firewall.
In the left pane, click Turn Windows Firewall on or off (you may be prompted to enter your administrator password).
Under each network location, click On (recommended) (Windows Vista) or Turn on Windows Firewall (Windows 7), and then click OK.
For more information about how to turn on your firewall in Windows 7, go to the Turn Windows 7 Firewall on or off website.
Keep your computer up to date
For more information about how to set Automatic Updates in Windows, see the following article in the Microsoft Knowledge Base:
306525 — How to configure and use Automatic Updates in Windows
Install Microsoft Security Essentials and keep it up to date
For more information about how to install and use Microsoft Security Essentials, go to the Microsoft Security Essentials website.
Don’t be tricked into downloading malware
Here are some tips that can help protect you from downloading software that you don’t want:
Only download programs from websites that you trust. If you’re not sure whether to trust a program that you want to download, enter the name of the program into your favorite search engine to see whether anyone else has reported that it contains spyware.
Read all security warnings, license agreements, and privacy statements that are associated with any software that you download.
Never click «Agree» or «OK» to close a window that you suspect might be spyware. Instead, click the red «x» in the corner of the window or press Alt + F4 on your keyboard to close a window.
Be wary of popular «free» music and movie file-sharing programs, and make sure that you understand all the software packaged with those programs.
Use a standard user account instead of an administrator account. For more information, go to the Why use a standard account instead of an administrator account website.
For more information about how to protect a computer against viruses, go to the How to boost your malware defense and protect your PC website.
How to reset your Internet Explorer proxy settings
Malicious software might change Internet Explorer proxy settings, and these changes can prevent you from accessing Windows Update or any Microsoft Security sites.
To have us change your Internet Explorer proxy settings for you, click the Fix it button or link. Click Run in the File Download dialog box, and follow the steps in the Fix it wizard:
This wizard may be in English only. However, the automatic fix also works for other language versions of Windows.
If you are not using the computer that has the problem, save the Fix it solution to a flash drive or a CD and then run it on the computer that has the problem.
To change your Internet Explorer proxy settings yourself, follow these steps:
Click Start and then click Run.
In the Run box, copy and paste the following:
reg add «HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings» /v ProxyEnable /t REG_DWORD /d 0 /f
Click Start, and then click Run.
In the Run box, copy and paste the following:
reg delete «HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings» /v ProxyServer /f
For more information about how to reset your Internet Explorer proxy settings, visit the following Microsoft Knowledge Base article:
2289942 — How to reset your Internet Explorer proxy settings
How to obtain computer virus and security-related support
For United States
Want to chat with a live person? Our Answer Tech trained professionals are ready to help:
For United States and Canada
Help protect your computer from viruses and malware:
Get help with installing updates:
Security solutions for IT Professionals:
Support by country:
If you are using a PC running Windows 8, click here for more information about how to help protect your PC from viruses, or click here for more information about how to find and remove viruses.
For locations outside North America
For computer virus and security-related support for locations outside North America, go to the Microsoft Support website.
How to Use CMD to Remove Virus from Any Drive in Windows 10
Viruses may attack files/folders, storage devices, or Windows operating systems. To remove a virus from an infected USB drive, SD card, pen drive and more on a Windows 10 computer, you can use CMD to get things done. If the virus delete or hide your files, don’t hesitate to use EaseUS Data Recovery Wizard to recover them with ease.
Table of Contents
About the Author
Reviews and Awards
On this page, we include four practical methods to help you remove viruses and help you restore virus removed or deleted files with powerful EaseUS file recovery software. If you are in this dilemma, follow fixes here to clean up virus and bring your files back:В
| Workable Solutions | Step-by-step Troubleshooting |
|---|---|
| Fix 1. Remove Virus with CMD | Run Command Prompt as Administrator or EaseUS M Tool > Clear virus with attrib -s -h -r /s /d *.*В command. Full steps |
| Fix 2. Run Antivirus | Run installed antivirus software, execute clean operation if virus is detected. Full steps |
| Fix 3. Run Windows Defender | Go to Settings > «Update & Security» > «Windows Security» > «Virus & threat protection» . Full steps |
| Fix 4. Format Infected Device | If the hard drive partition or external storage device was infected by virus, formatting it can help. Full steps |
| Bonus Tip. Recover Files | If files get hidden or deleted by the virus, run EaseUS Data Recovery Wizard > Scan device and recover. Full steps |
What Damage Could Viruses Do
We loathe computer viruses, undoubtedly. But do you know exactly how viruses can damage your computer? There are many types of viruses, and they behave in different ways. To sum it up, a computer virus is simply a type of program that causes your computer to act in an undesirable way. It can be a dangerous infiltration designed to drag your computer down, erase important files, track your habits, or gives hackers access to your personal information. A virus is a great nuisance. Some viruses like the Locky virus and CryptoLocker, also known as ransomware, delete computer files, encrypt them, even change the file extension to .locky or .encypt. Other viruses hide files and leave users with nowhere to unhide them.
It’s certainly true that aВ virus is something you will want to remove once you find it. Among the multiple choices, many users attempt to remove viruses using CMD.
Why Can You Remove a Virus Using CMD
In fact, using command lines doesn’t directly check and remove viruses from your computer or external storage device. CMD helps to achieve your goal of removing viruses by showing the hidden viruses on a partition or drive. Afterward, you can delete the suspicious files. Since viruses always conceal themselves, you need to make them appear and then delete the virus files. Then how can you show the potentially hidden virus files using CMD? All you need is the attrib command.
The attrib command is a Command Prompt command used to display, set, or remove the attributes of the files or folders in the selected location. By canceling the «hidden» attribute of the virus, you can see it appearing in the folder. And then you will know where to find and remove it.
How to Remove Virus Using CMD
Now, follow the steps below to delete viruses from your computer or storage device using CMD.
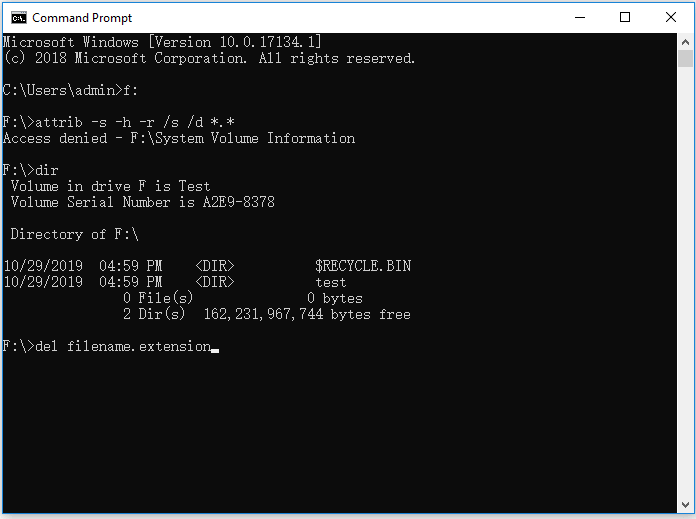
Step 1.В Type cmd in the search bar, right-click «Command Prompt» and choose «Run as an administrator».
Step 2.В TypeВ F:В and press «Enter». (Replace «F» with the drive letter of the infected partition or device.)
Step 3.В Type attrib -s -h -r /s /d *.* and hit «Enter».
Step 4. Type dir and hit «Enter». Now you will see all the files under the assigned drive. (The dir command displays a list of a directory’s files and subdirectories.)
Step 5. For your information, a virus name may contain words like «autorun» and with «.inf» as the extension. Thus, if you find such suspicious files, type del autorun.inf to remove the virus.
Here are the basic attributes of the ‘attrib’ command:
R – represents the «Read-only» attribute of a file or folder. Read-only means the file cannot be written on or executed.
H – the «Hidden» attribute.
A – stands for «Archiving» which prepares a file for archiving.
S – the «System» attribute changes the selected files or folders from user files into system files.
I — «not content indexed file» attribute.
The «attrib» Syntax:
ATTRIB [+ attribute | – attribute] [pathname] [/S [/D]]
In the above command, let’s see what the different parameters and switches are:
‘+ / –’: To enact or to cancel the specified attribute.
‘attribute’: As explained above.
‘/S’: Searching throughout the entire path including subfolders.
‘/D’: В Include any process folder.
‘pathname’: Path where the target file or folder is located.
Here is the proper syntax order for attrib command:
ATTRIB [+R | -R] [+A | -A ] [+S | -S] [+H | -H] [+I | -I] [drive:][path][filename] [/S [/D] [/L]]
If you receive the message «Access denied», you should:
- Make sure you have run Command Prompt as an administrator
- Make sure the file/folder is not in use
- Check the permission of the current account and make sure you have full control over the file/folder (right-click the file/folder/partition and go to «Security»)
- Use CHKDSK command to check for file system errors (run Command prompt and enter chkdsk /f [drive letter]:)
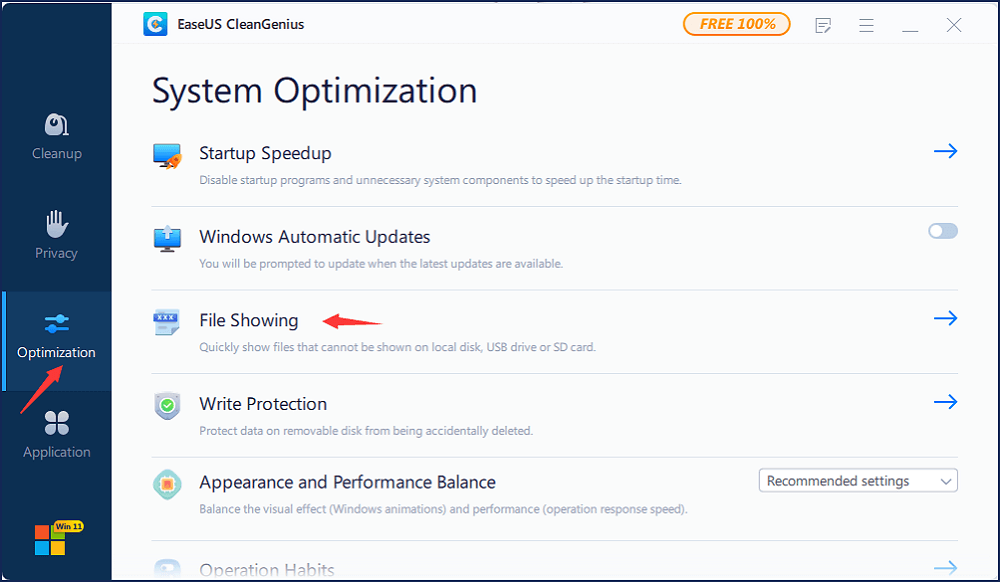
Manual input of the command line is suitable for computer professionals since wrong commands can cause more severe problems. Therefore, for security and usability, we strongly recommend you try an automatic command line alternative. EaseUS Tools M is a practical tool that enables you to check and fix files system error, enable/disable write protection and system update with one-click instead of typing intricate command lines.
Follow the simple steps below to show hidden files with this 1-click-fix software.В
Step 1.В оњљ DOWNLOAD EaseUS Tools M for Free.
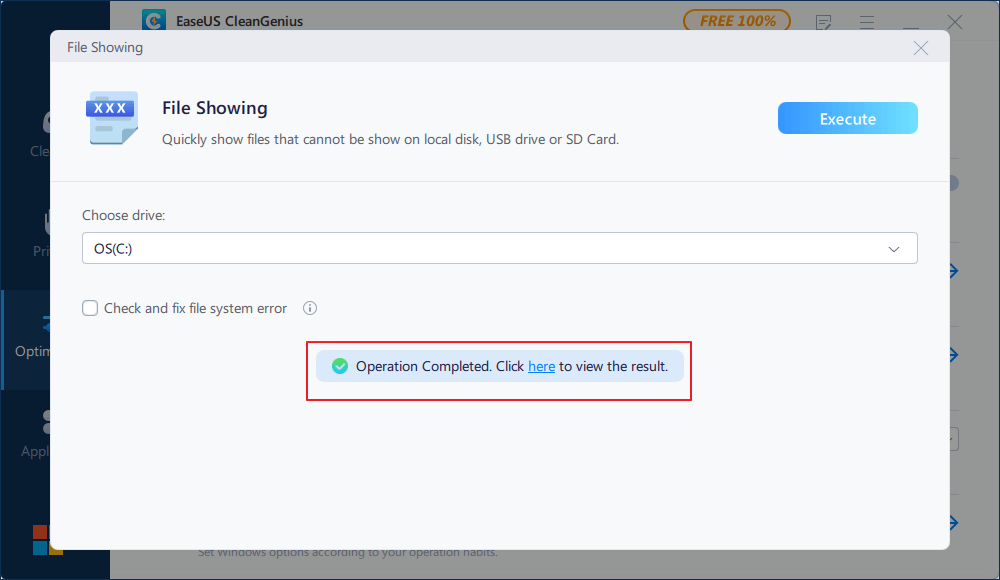
Step 2. Start EaseUS Tools M, choose «File Showing» on the left pane. Next, choose the target drive for scanning.
Step 3. After the operation completes, click the View button to check the hidden files.В
3 Other Ways to Remove Virus
In addition to using CMD, there are other methods available to remove a virus from your computer or storage device, like using antivirus software, Windows Defender, and formatting the storage device.
Method 1. Run Antivirus
Almost every computer has antivirus software installed. Whenever you find your computer is infected by a virus, running the antivirus software may help.
Method 2. Run Windows Defender Antivirus
Windows Defender Antivirus is the built-in antivirus protection in Windows 10. It provides protection against viruses, malware, and spyware for your computer and connected devices. If you don’t have third-party antivirus software, using the built-in utility is advisable.
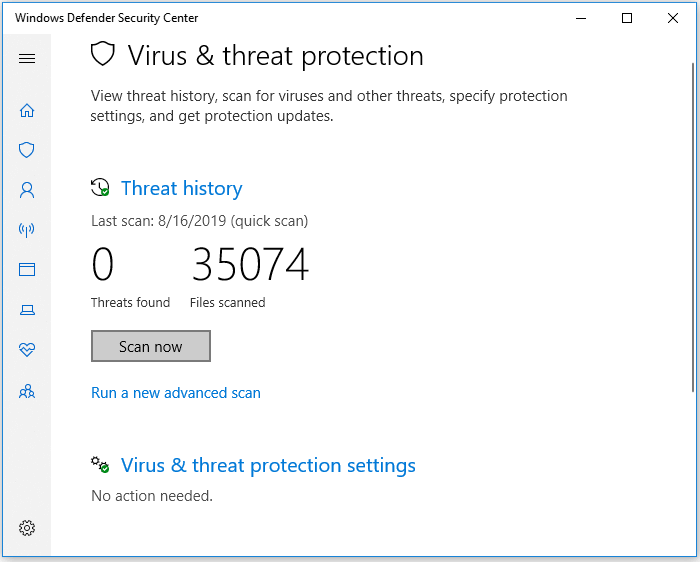
Step 1. Go to «Settings» > «Update & Security» > «Windows Security».
Step 2. Click «Virus & threat protection».
Step 3. In the «Threat history» section, click «Scan now» to scan for viruses on your computer.
Method 3. Format the Infected Device
The format is the process of erasing the existing files on the selected partition or drive. It will certainly remove the virus, too. Since formatting a partition/drive will cause data loss, make sure you don’t have any important files stored on the device.
How to Recover Files Deleted/Hidden by Viruses
Don’t forget to use aВ data recovery tool in case the virus deleted or hid your important files on USB and other drives. Using commands can only help remove the virus but can do nothing to restore damaged and lost files. EaseUS file recovery software is able to complete virus file recovery in just three steps.
Learn the 3-step file recovery in this video guide.
How to Prevent Virus or Malware Infections
Except for knowing how to cope with a virus attack, you should also know how to prevent virus infection on your computer or external storage device. For you to protect your computer or USB drives better, here are some feasible tips on virus prevention for you:
Install professional antivirus software on your computer and keep it updated
Be cautious with the origins of the programs you want to install
Avoid suspicious websites and think before you make a click
Make sure the network connection is safe
Besides, regularly making backups of your files with free backup software is also recommended to avoid complete data loss that may be caused by a virus infection.
The Bottom Line
Removing a virus using CMD is a roundabout solution. Yet it works in some cases. If the attrib command fails, try the three more tips provided to get rid of the malicious file. Besides, virus attacks are always accompanied by data loss. In that case, use the hard drive recovery software — EaseUS Data Recovery Software to rescue the lost files as soon as possible.