- Kali linux all download
- Kali Linux Metapackages
- Kali Linux 2021.3
- Kali Linux is an advanced penetration testing Linux distribution used for penetration testing, ethical hacking and network security assessments. Official images hosted by us for faster downloads.
- Download
- What’s New
- Specs
- Similar to 5
- Kali linux all download
- Where to Get Official Kali Linux Images
- Verifying Your Downloaded Kali Image
- How Do I Verify My Downloaded Image?
Kali linux all download
We release fresh images of Kali Linux every few months as a result of accumulative fixes, major security updates, installer updates, etc.
Please see bugs.kali.org/changelog_page.php for the most up-to-date log of changes.
- Kali 2021.3 – 14th September, 2021 – The third 2021 Kali Rolling release. Kernel 5.10.0, Xfce 4.16.3.
- Kali 2021.2 – 1st June, 2021 – The second 2021 Kali Rolling release. Kernel 5.10.0, Xfce 4.16.2.
- Kali 2021.1 – 24th February, 2021 – The first 2021 Kali Rolling release. Kernel 5.10.0, Xfce 4.16.1.
- Kali 2020.4 – 18th November, 2020 – The fourth 2020 Kali Rolling release. Kernel 5.9.0, Xfce 4.14.4.
- Kali 2020.3 – 18th August, 2020 – The third 2020 Kali Rolling release. Kernel 5.7.0, Xfce 4.14.4.
- Kali 2020.2 – 12th May, 2020 – The second 2020 Kali Rolling release. Kernel 5.5.0, Xfce 4.14.4.
- Kali 2020.1b – 18th March, 2020 – Minor bug fix release (Offline setup issue).
- Kali 2020.1a – 13th February, 2020 – Minor bug fix release (xserver-xorg issue).
- Kali 2020.1 – 28th January, 2020 – The first 2020 Kali Rolling release. Kernel 5.4.0, Xfce 4.14.2.
- Kali 2019.4 – 26th November, 2019 – The fourth 2019 Kali Rolling release. Kernel 5.3.9, Xfce 4.14.1.
- Kali 2019.3 – 2nd September, 2019 – The third 2019 Kali Rolling release. Kernel 5.2.9, GNOME 3.30.2.
- Kali 2019.2 – 21st May, 2019 – The second 2019 Kali Rolling release. Kernel 4.19.28, GNOME 3.30.2.
- Kali 2019.1a – 4th March, 2019 – Minor bug fix release (VMware Installer).
- Kali 2019.1 – 18th February, 2019 – The first 2019 Kali Rolling release. Kernel 4.19.13, GNOME 3.30.2.
- Kali 2018.4 – 29th October, 2018 – The fourth 2018 Kali Rolling release. Kernel 4.18.0, GNOME 3.30.1.
- Kali 2018.3 – 27th August, 2018 – The third 2018 Kali Rolling release. Kernel 4.17.0, GNOME 3.28.2.
- Kali 2018.2 – 30th April, 2018 – The second 2018 Kali Rolling release. Kernel 4.15.0, GNOME 3.28.0.
- Kali 2018.1 – 6th February, 2018 – The first 2018 Kali Rolling release. Kernel 4.14.12, GNOME 3.26.2.
- Kali 2017.3 – 21st November, 2017 – The third 2017 Kali Rolling release. Kernel 4.13, GNOME 3.26.
- Kali 2017.2 – 20th September, 2017 – The second 2017 Kali Rolling release. Kernel 4.12, GNOME 3.25.
- Kali 2017.1 – 25th April, 2017 – The first 2017 Kali Rolling release. Kernel 4.9, GNOME 3.22.
- Kali 2016.2 – 31st August, 2016 – The second 2016 Kali Rolling release. Kernel 4.6, GNOME 3.20.2.
- Kali 2016.1 – 21st January, 2016 – The first Kali Rolling release. Kernel 4.3, GNOME 3.18.
- Kali 2.0 – 11th August, 2015 – Major release, “safi«, now a rolling distribution, major UI changes.
- Kali 1.1.0a – 13th March, 2015 – No fanfare release fixing kernel ABI inconsistencies in the installers.
- Kali 1.1.0 — 9th Febuary, 2015 — First dot release in 2 years. New kernel, new tools and updates.
- Kali 1.0.9a — 6th October, 2014 — Security bug fix release covering shellshock and Debian apt vulnerabilities.
- Kali 1.0.9 — 25th August, 2014 — Bug fix release including installer and a set of tool updates and package fixes.
- Kali 1.0.8 — 22nd July, 2014 — EFI Support for our) and package fixes.
- Kali 1.0.7 — 27th May, 2014 — Kernel 3.14, tool updates, package fixes, Kali Live Encrypted USB Persistence.
- Kali 1.0.6 — 9th January, 2014 — Kernel 3.12, cryptsetup nuke option, Amazon AMI, ARM build scripts.
- Kali 1.0.5 — 5th September, 2013 — Bug fix rollup. LVM Encrypted installs, Software Defined Radio (SDR) tools.
- Kali 1.0.4 — 25th July, 2013 — Bug fix rollup. Penetration testing tool additions and updates.
- Kali 1.0.3 — 26th April, 2013 — Bug fix rollup. New accessibility features. Added live Desktop installer.
- Kali 1.0.2 — 27th March, 2013 — Minor Bug fix release and update roll-up.
- Kali 1.0.1 — 14th March, 2013 — Minor Bug fix release (USB Keyboard).
- Kali 1.0.0 — 13th March, 2013 — Initial release, “moto«.
- Legacy Operating Systems releases.
Источник
Kali Linux Metapackages
One of our goals when developing Kali Linux was to provide multiple metapackages that would allow us to easily install subsets of tools based on their particular needs. Until recently, we only had a handful of these meta packages but we have since expanded the metapackage list to include far more options:
- kali-linux
- kali-linux-all
- kali-linux-forensic
- kali-linux-full
- kali-linux-gpu
- kali-linux-pwtools
- kali-linux-rfid
- kali-linux-sdr
- kali-linux-top10
- kali-linux-voip
- kali-linux-web
- kali-linux-wireless
These metapackages allow for easy installation of certain tools in a specific field, or alternatively, for the installation of a full Kali suite. All of the Kali metapackages follow a particular naming convention, starting with “kali-linux” so if you want to see which metapackages are available, you can search for them as follows:
Although we tried to make the metapackage names self-explanatory, we are limited in the practical length we can use, so let’s take a brief look at each of them and see how much disk space is used by each one:
kali-linux
The kali-linux metapackage is a completely bare-bones installation of Kali Linux and includes various network services such as Apache and SSH, the Kali kernel, and a number of version control applications like git, svn, etc. All of the other metapackages listed below also contain kali-linux. Installation Size: 1.5 GB
kali-linux-full
When you download a Kali Linux ISO, you are essentially downloading an installation that has the kali-linux-full metapackage installed. This package includes all of the tools you are familiar with in Kali. Installation Size: 9.0 GB
kali-linux-all
In order to keep our ISO sizes reasonable, we are unable to include every single tool that we package for Kali and there are a number of tools that are not able to be used depending on hardware, such as various GPU tools. If you want to install every available Kali Linux package, you can install the kali-linux-all metapackage. Installation Size: 15 GB
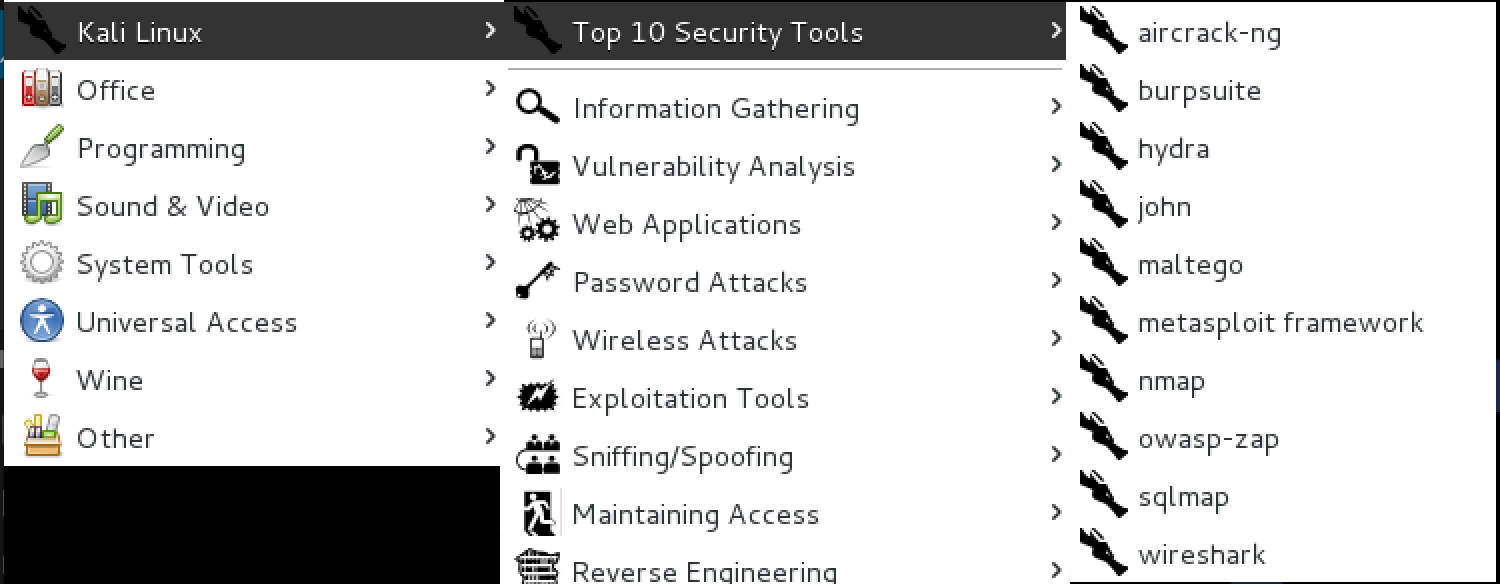
kali-linux-top10
In Kali Linux, we have a sub-menu called “Top 10 Security Tools”. The kali-linux-top10 metapackage will install all of these tools for you in one fell swoop. Installation Size: 3.5 GB
kali-linux-forensic
If you are doing forensics work, you don’t want your analysis system to contain a bunch of unnecessary tools. To the rescue comes the kali-linux-forensic metapackage, which only contains the forensics tools in Kali. Installation Size: 3.1 GB
kali-linux-gpu
GPU utilities are very powerful but need special hardware in order to function correctly. For this reason, they are not included in the default Kali Linux installation but you can install them all at once with kali-linux-gpu and get cracking. Installation Size: 4.8 GB
kali-linux-pwtools
The kali-linux-pwtools metapackage contains over 40 different password cracking utilities as well as the GPU tools contained in kali-linux-gpu. Installation Size: 6.0 GB
kali-linux-rfid
For our users who are doing RFID research and exploitation, we have the kali-linux-rfid metapackage containing all of the RFID tools available in Kali Linux. Installation Size: 1.5 GB
kali-linux-sdr
The kali-linux-sdr metapackage contains a large selection of tools for your Software Defined Radio hacking needs. Installation Size: 2.4 GB
kali-linux-voip
Many people have told us they use Kali Linux to conduct VoIP testing and research so they will be happy to know we now have a dedicated kali-linux-voip metapackage with 20+ tools. Installation Size: 1.8 GB
kali-linux-web
Web application assessments are very common in the field of penetration testing and for this reason, Kali includes the kali-linux-web metapackage containing dozens of tools related to web application hacking. Installation Size: 4.9 GB
kali-linux-wireless
Like web applications, many penetration testing assessments are targeted towards wireless networks. The kali-linux-wireless metapackage contains all the tools you’ll need in one easy to install package. Installation Size: 6.6 GB
To see the list of tools included in a metapackage, you can use simple apt commands. For example, to list all the tools included in the kali-linux-web metapackage, we could:
Источник
Kali Linux 2021.3
Kali Linux is an advanced penetration testing Linux distribution used for penetration testing, ethical hacking and network security assessments. Official images hosted by us for faster downloads.
Download
What’s New
Specs
Similar to 5
Kali Linux is preinstalled with over 600 penetration-testing programs, including nmap (a port scanner), Wireshark (a packet analyzer), John the Ripper (a password cracker), Aircrack-ng (a software suite for penetration-testing wireless LANs), Burp suite and OWASP ZAP (both web application security scanners). Kali Linux can run natively when installed on a computer’s hard disk, can be booted from a live CD or live USB, or it can run within a virtual machine. It is a supported platform of the Metasploit Project’s Metasploit Framework, a tool for developing and executing security exploits.
It was developed by Mati Aharoni and Devon Kearns of Offensive Security through the rewrite of BackTrack, their previous forensics Linux distribution based on Ubuntu. The third core developer Raphaël Hertzog joined them as Debian expert.
Kali Linux is based on Debian Wheezy. Most packages Kali uses are imported from the Debian repositories.
Kali Linux is developed in a secure location with only a small number of trusted people that are allowed to commit packages, with each package being signed by the developer. Kali also has a custom built kernel tha is patched for injection. This was primarily added because the development team found they needed to do a lot of wireless assessments.
Today we have released the newest version of Kali Linux, 2021.3 (quarter #3), which is now ready for download or updating.
A summary of the changes since the 2021.2 release from June are:
- OpenSSL — Wide compatibility by default — Keep reading for what that means
- New Kali-Tools site — Following the footsteps of Kali-Docs, Kali-Tools has had a complete refresh
- Better VM support in the Live image session — Copy & paste and drag & drop from your machine into a Kali VM by default
- New tools — From adversary emulation, to subdomain takeover to Wi-Fi attacks
- Kali NetHunter smartwatch — first of its kind, for TicHunter Pro
- KDE 5.21 — Plasma desktop received a version bump
OpenSSL: wide compatibility by default
Going forwards from Kali Linux 2021.3, OpenSSL has now been configured for wider compatibility to allow Kali to talk to as many services as possible. This means that legacy protocols (such as TLS 1.0 and TLS 1.1) and older ciphers are enabled by default. This is done to help increase Kali’s ability to talk to older, obsolete systems and servers that are still using these older protocols. This may potentially increase your options on available attack surfaces (if your target has these End of Life (EoL) services running, having then forgotten about them, what else could this uncover?). While this is not a configuration that would be good for a general purpose operating systems, this setting makes sense for Kali as it enables the user to engage and talk with more potential targets.
This setting is easy to modify via the command-line tool kali-tweaks though. Enter the Hardening section, and from there you can configure OpenSSL for Strong Security mode instead, which uses today’s current modern standard allowing for secure communication.
Virtualization: improvements all over the place
The Kali Live image received some love during this release cycle! We worked hard to make the experience smoother for those who run the Live image in virtualized environments. Basic features like copy’n’paste and drag’n’drop between the host and the guest should now work out of the box. And this is really for everyone: VMware, VirtualBox, Hyper-V and QEMU+Spice. Did we forget anyone? Drop us a word on the Kali bug tracker!
On the same line: it’s now very easy to configure Kali for Hyper-V Enhanced Session Mode. Open kali-tweaks in a terminal, select Virtualization, and if Kali is running under Hyper-V, you’ll see a setting to turn on Hyper-V Enhanced Session Mode. It’s now as simple as hitting Enter!
If you use this feature, make sure to visit kali.org/docs/virtualization/install-hyper-v-guest-enhanced-session-mode/, as there are a few additional things to be aware of.
Many thanks to @Shane Bennett, who spent a tremendous amount of time testing this feature, provided extremely detailed feedback all along, and even helped us with the documentation. Kudos Shane!
Источник
Kali linux all download
IMPORTANT! Never download Kali Linux images from anywhere other than the official sources.
Always be sure to verify the SHA256 checksums of the file you’ve downloaded against our official values.
It would be easy for a malicious entity to modify a Kali installation to contain exploits or malware and host it unofficially.
Where to Get Official Kali Linux Images
ISO Files for Intel-based PCs
In order to run Kali “Live” from a USB drive on standard Windows and Apple PCs, you’ll need a Kali Linux bootable ISO image, in either 32-bit or 64-bit format.
If you’re not sure of the architecture of the system you want to run Kali on, on Linux or macOS, you can run the command uname -m at the command line. If you get the response, “x86_64”, use the 64-bit ISO image (the one containing “amd64” in the file name); if you get “i386”, use the 32-bit image (the one containing “i386” in the file name). If you’re on a Windows system, the procedure for determining whether your architecture is detailed on Microsoft’s website.
The Kali Linux images are available both as directly downloadable “.iso/.img” files or via “.torrent” files.
Building your own Kali Linux ISO, standard or customized, is a very simple process.
Virtual Machines Images
If you want to run Kali Linux as a “guest” under VMware or VirtualBox, Kali Linux is available as a pre-built virtual machines with any guest tools already installed. These image are available in a 64-bit (amd64), and 32-bit PAE (i*86) formats.
ARM Images
The hardware architectures of ARM-based devices vary considerably, so it is not possible to have a single image that will work across all of them. Pre-built Kali Linux images for the ARM architecture are available for a wide range of devices.
Scripts for building your own ARM images locally are also available on GitLab. For more details, see the articles on setting up an ARM cross-compilation environment and building a custom Kali Linux ARM chroot.
Verifying Your Downloaded Kali Image
Why do I need to do this?
Before you run Kali Linux Live, or install it to your hard disk, you want to be very sure that what you’ve got actually is Kali Linux, and not an imposter. Kali Linux is a professional penetration testing and forensics toolkit. As a professional penetration tester, having absolute confidence in the integrity of your tools is critical: if your tools are not trustworthy, your investigations will not be trustworthy, either.
Moreover, as the leading penetration testing distribution, Kali’s strengths mean that a bogus version of Kali Linux could do a tremendous amount of damage if it were deployed unwittingly. There are plenty of people with plenty of reason to want to stick very sketchy stuff into something that looks like Kali, and you absolutely do not want to find yourself running something like that.
Avoiding this is simple:
- Only download Kali Linux via the official download pages at kali.org/downloads/ or offensive-security.com/kali-linux-vmware-arm-image-download/ — you will not be able to browse to these pages without SSL; encrypting the connection makes it much harder for an attacker to use a “man-in-the-middle” attack to modify your download. There are a few potential weaknesses to even these sources — see the sections on verifying the download with the SHA256SUMS file and its signature against the official Kali Development team private key for something much closer to absolute assurance.
- Once you’ve downloaded an image, and before you run it, always validate that it really is what it’s supposed to be by verifying its checksum using one of the procedures detailed below.
There are several methods for verifying your download. Each provides a certain level of assurance, and involves a corresponding level of effort on your part.
- You can download an ISO image from an official Kali Linux “Downloads” mirror, calculate the ISO’s SHA256 hash and compare it by inspection with the value listed on the Kali Linux site. This is quick and easy, but potentially susceptible to subversion via a DNS poisoning: it assumes that the site to which, for example, the domain “kali.org” resolves is in fact the actual Kali Linux site. If it somehow were not, an attacker could present a “loaded” image and a matching SHA256 signature on the fake web page. See the section “Manually Verify the Signature on the ISO (Direct Download)”, below.
- You can download an ISO image through the torrents, and it will also pull down a file — unsigned — containing the calculated SHA256 signature. You can then use the shasum command (on Linux and macOS) or a utility (on Windows) to automatically verify that the file’s computed signature matches the signature in the secondary file. This is even easier than the “manual” method, but suffers from the same weakness: if the torrent you pulled down is not really Kali Linux, it could still have a good signature. See the section “Verify the Signature on the ISO Using the Included Signature File (Torrent Download)”, below.
- To be as close to absolutely certain as possible that the Kali Linux download you’ve obtained is the real thing, you can download both a cleartext signature file and and version of the same file that has been signed with the official Kali Linux private key and use GNU Privacy Guard (GPG) to first, verify that the computed SHA256 signature and the signature in the cleartext file match and second, verify that the signed version of the file containing the SHA256 hash has been correctly signed with the official key.
If you use this more complicated process and successfully validate your downloaded ISO, you can proceed with pretty complete assurance that what you’ve got is the official image and that it has not been tampered with in any way. This method, while the most complex, has the advantage of providing independent assurance of the integrity of the image. The only way this method can fail is if the official Kali Linux private key is not only subverted by an attacker, but also not subsequently revoked by the Kali Linux development team. For this method, see the section on verification using the SHA256SUMS file.
What do I need to do this?
If you’re running on Linux, you probably already have GPG (GNU Privacy Guard) installed. If you’re on Windows or macOS, you’ll need to install the appropriate version for your platform.
- If you’re on a PC running Windows, download and install GPG4Win from here. Certain versions of Windows do not have the native ability to calculate SHA256 checksums. To check this, you can open the command prompt and run certutil -? . If you do have this installed, you can run certutil -hashfile kali-linux-2021.3-live-amd64.iso sha256 to verify your download. If you do not have certutil installed, you will also need a utility such as Microsoft File Checksum Integrity Verifier or Hashtab to verify your download.
- If you’re on a Macintosh running macOS, download and install GPGTools from here. Alternatively, if you have Homebrew installed, just run brew install gnupg
Once you’ve installed GPG, you’ll need to download and import a copy of the Kali Linux official key. Do this with the following command:
Your output should look like this:
Verify that the key is properly installed with the command:
The output will look like this:
You’re now set up to validate your Kali Linux download.
How Do I Verify My Downloaded Image?
Manually Verify the Signature on the ISO (Direct Download)
If you downloaded the ISO directly from the downloads page, verify it using the following procedure.
On Linux, or macOS, you can generate the SHA256 checksum from the ISO image you’ve downloaded with the following command (assuming that the ISO image is named “kali-linux-2021.3-live-amd64.iso”, and is in your current directory):
The output should look like this:
The resulting SHA256 signature, “e316b27025922e9f6bca0cacee6dde83dbfd4a549ad18026526f5824af639fc1”, can be seen to match the signature displayed in the “sha256sum” column on the official download page for the 64-bit Intel architecture Kali Linux 2021.3 ISO image:
Verify the Signature on the ISO Using the Included Signature File (Torrent Download)
If you downloaded your copy of the Kali Linux ISO image via the torrents, in addition to the ISO file (e.g. kali-linux-2021.3-live-amd64.iso), there will be a second file containing the computed SHA256 signature for the ISO, with the extension “.txt.sha256sum” (e.g. kali-linux-2021.3-live-amd64.txt.sha256sum). You can use this file to verify the authenticity of your download on Linux or macOS with the following command:
If the image is successfully authenticated, the response will look like this:
IMPORTANT! If you are unable to verify the authenticity of the Kali Linux image you have downloaded as described in the preceding section, do NOT use it! Using it could endanger not only your own system, but any network you connect to as well as the other systems on that network. Stop, and ensure that you have downloaded the images from a legitimate Kali Linux mirror.
Verify the ISO Using the SHA256SUMS File
This is a more complex procedure, but offers a much higher level of validation: it does not rely on the integrity of the web site you downloaded the image from, only the official Kali Linux development team key that you install independently. To verify your image this way for an Intel architecture version of Kali, you will need to download three files from the Kali “Live CD Image” site for the current release (v2021.3, as of this writing):
- The ISO image itself (e.g. kali-linux-2021.3-live-amd64.iso)
- The file containing the calculated SHA256 hash for the ISO, SHA256SUMS
- The signed version of that file, SHA256SUMS.gpg
Before verifying the checksums of the image, you must ensure that the SHA256SUMS file is the one generated by Kali Linux. That’s why the file is signed by Kali’s official key with a detached signature in SHA256SUMS.gpg. If you have not already done so, Kali’s official key can be downloaded and imported into your keychain with this command:
or this command
Your output should look like this:
You should verify that the key is properly installed with the command:
The output will look like this:
Once you have downloaded both SHA256SUMS and SHA256SUMS.gpg, you can verify the signature as follows:
If you do not get that “Good signature” message or if the key ID does not match, then you should stop and review whether you downloaded the images from a legitimate Kali Linux mirror. The failed verification strongly suggests that the image you have may have been tampered with.
If you did get the “Good signature” response, you can now be assured that the checksum in the SHA256SUMS file was actually provided by the Kali Linux development team. All that remains to be done to complete the verification is to validate that the signature you compute from the ISO you’ve downloaded matches the one in the SHA256SUMS file. You can do that on Linux or macOS with the following command (assuming that the ISO is named “kali-linux-2021.3-live-amd64.iso” and is in your working directory):
If the image is successfully authenticated, the response will look like this:
If you do not get “OK” in response, then stop and review what’s happened: the Kali image you have has apparently been tampered with. Do NOT use it.
Once you’ve downloaded and verified your image, you can proceed to create a bootable “Kali Linux Live” USB drive.
Updated on: 2021-Sep-27
Authors: g0tmi1k , gamb1t
Источник