- Kali Linux 2020.1 Release (Non-Root, Single Installer & NetHunter Rootless)
- Non-Root
- Kali as your Main OS
- Kali Single Installer Image
- ARM Images
- NetHunter Images
- Theming
- Kali-Undercover
- New Packages
- Python 2 End Of Life
- Giving A Helping Hand
- Download Kali Linux 2020.1
- Kali linux download free download
- Where to Get Official Kali Linux Images
- Verifying Your Downloaded Kali Image
- How Do I Verify My Downloaded Image?
Kali Linux 2020.1 Release (Non-Root, Single Installer & NetHunter Rootless)
We are here to kick off our first release of the decade, with Kali Linux 2020.1! Available for immediate download.
The following is a brief feature summary for this release:
Non-Root
Throughout the history of Kali (and its predecessors BackTrack, WHAX, and Whoppix), the default credentials have been root/toor . This is no more. We are no longer using the superuser account, root, as default in Kali 2020.1. The default user account is now a standard, unprivileged, user.
For more of the reasons behind this switch, please see our previous blog post. As you can imagine, this is a very large change, with years of history behind it. As a result, if you notice any issues with this, please do let us know on the bug tracker.
root/toor is dead. Long live kali/kali .
Kali as your Main OS
So with this, should you use Kali as your daily driver, as the primary OS? It’s up to you. There wasn’t anything really stopping you before, we just don’t encourage it. We still don’t. But its a helping hand for the people who are familiar with Kali enough.
Why do we not recommend it? Because we are unable to test for that usage pattern and we don’t want the influx of bug reports that would come with it. If you are brave enough to try it, you may wish to switch the branch from “rolling” to “kali-last-snapshot” to try and be more stable.
Kali Single Installer Image
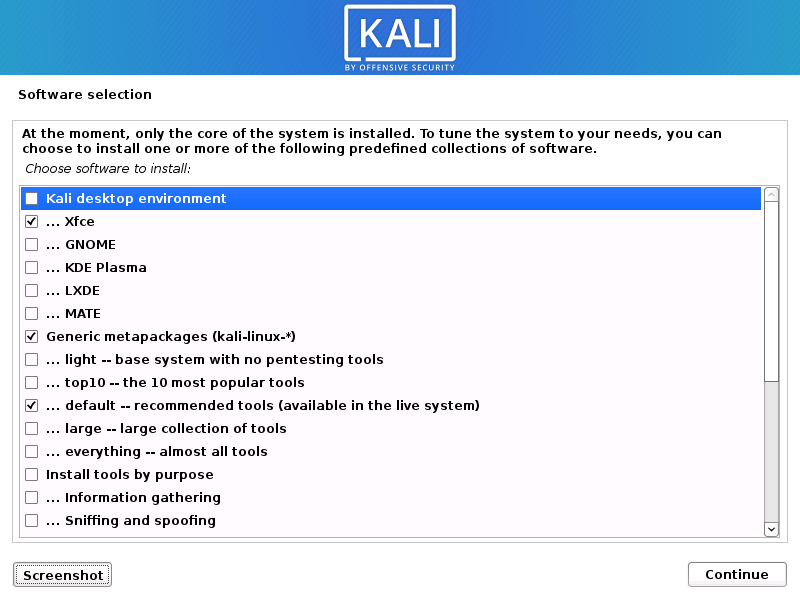
We took a good hard look at the usage of Kali, what images are actually downloaded, how they are put to use, and so on. With this information in hand, we decided to completely restructure and simplify the images we release. Going forward, we will have an installer image, a live image, and a network installer image.
These changes should allow for easier selection of the right image for you to download, while increasing flexibility on installation and further reducing download sizes.
Our Installer Image
- This is what we recommend for most users that want to install Kali on their system
- Doesn’t require a network connection (aka offline install) for the default package selection
- Able to select desktop environment to install (Previously there was a separate image for each DE: XFCE, GNOME, KDE, etc.)
- Able to select tools to install at install time
- Can’t be used to boot a live system. This is just an installer image.
- Filename:
- kali-linux-2020.1-installer-.iso
We are no longer offering separate images for every desktop environment (DE). Instead, we now have a single image with the option to pick your DE during installation. This means there isn’t a download link for Xfce (which is our default option since 2019.4), GNOME, KDE, MATE or LXDE DEs. Just one image to rule them all.
At install time, you may select the tools included with Kali (or none at all)! This gives you more control over what you want. We understand that Kali comes with more tools than some people use, or they have their own select tools they use. Now they can install Kali without any metapackages, giving them a bare Kali installation, so they can individually select what tools they want (rather than groups/).
The default image contains the kali-desktop-xfce and kali-tools-default packages, allowing for an offline installation of Kali (as it always has been). Selecting any non-default tools will require a network connection.
Note: “Kali Live” is not included in this image. If you wish to use live mode, you’ll need the live image.
Network Install Image
- Smallest image to download
- This requires a network connection to install
- During setup, it will download the latest packages every time it’s used
- Able to select desktop environment to install
- Able to select tools to install
- Can’t be used to boot a live system. This is just an installer image.
- Filename:
- kali-linux-2020.1-installer-netinst-.iso
It’s a very small image, containing only enough to install the base system, but behaving exactly like the full installer image, allowing you to install everything that Kali offers, provided that you have enabled network connectivity.
Live Image
- Its primary use is to be able to run Kali, without installing it
- But it also contains an installer, behaving like the “Network Install Image” described above
- Filename:
- kali-linux-2020.1-live-.iso
“Kali Live” hasn’t been forgotten about — it’s just moved to its own image. This allows you to try Kali without installing it and is perfect for running off a USB stick. You can install from this image, however, it will require a network connection (this is why we suggest the stand-alone install image for most users).
Alternatively, you can generate your own image, in particular if you want to use another desktop environment instead of our default Xfce. It’s not as hard as it sounds!.
ARM Images
You will probably notice a bit of a change in the ARM images starting with our 2020.1 release. There are fewer images available for download, due to both manpower and hardware constraints, some images won’t be posted without community assistance. The scripts are still updated, so if an image doesn’t exist for a machine you use, you will have to create it by running the build script on a Kali machine.
ARM images for 2020.1 will still run as root by default.
The sad news that a lot of people didn’t want to hear… an image for the Pinebook Pro isn’t included in the 2020.1 release. We are still working on getting it added, and as soon as it is ready we will post it.
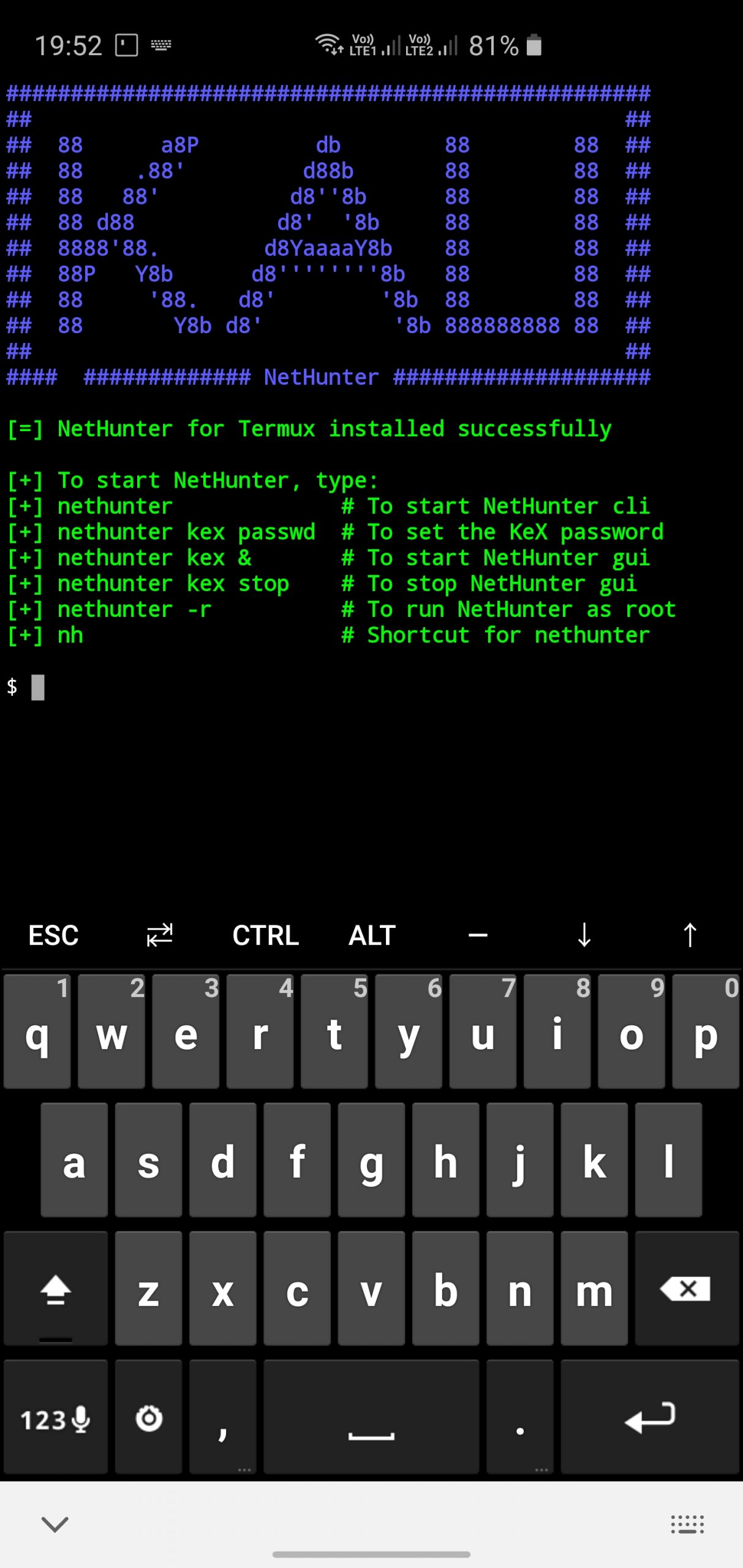
NetHunter Images
Our mobile pen-testing platform, Kali NetHunter, has also had some new improvements. You are now no longer required to root your phone in order to run Kali NetHunter, but that does come with some limitations.
To suit everybody’s needs, Kali NetHunter now comes in the following three editions:
- NetHunter — Needs rooted devices with custom recovery and patched kernel. Has no restrictions. Device specific images are available here.
- NetHunter Light — Needs rooted devices with custom recovery but no custom kernel. Has minor restrictions, i.e. no WiFi injection or HID support. Architecture specific images are available here.
- NetHunter Rootless — Installable on all stock standard, unmodified devices using Termux. Some limitations, like lack of db support in Metasploit and no root permissions. Installation instruction is available here.
The NetHunter documentation page includes a more detailed comparison. Each NetHunter edition comes with both the new “kali” user as well as root. KeX now supports multiple sessions so you can opt to run your pentest in one whilst writing a report in another.
Please note that due to how Samsung Galaxy devices function, the non-root user might not be able to run sudo but has to use su -c instead.
One of the peculiarities of the new “NetHunter Rootless” edition is that the default non-root user has almost full privileges in the chroot due to how proot containers work.
Theming
With our last release, we made a major change switching from GNOME to Xfce. That wasn’t the end for us; we have kept on going with the design work, and have more updates:
GNOME There is now a new theme for GNOME users and as an additional bonus, there is a light and dark theme!
Tools We are giving the tools that you are very fond of a makeover too! We are slowly working through our collection, refreshing them and adding in new icons.
Menu Eagle-eyed users may also notice the icons used in the menu have also been replaced.
Setup And if you opt to use the graphical installer of Kali, it’s also been updated (Before and after shots)
Kali-Undercover
We were not expecting the community’s overwhelming response to kali-undercover. So carrying on from Kali 2019.4 release, Kali-undercover now starts to feel even more like Windows to help blend in.
New Packages
Kali Linux is a rolling distribution, so it gets updates as soon as they are available, rather than waiting for “the next release”. So since the last release, we have the normal tool upgrades as well as a few new tools added, such as: cloud-enum , emailharvester , phpggc , sherlock , splinter .
We have a few new ( kali-community-wallpapers ) and old ( kali-legacy-wallpapers ) wallpapers to offer up if you want to customize or are feeling a little a little nostalgic.
Python 2 End Of Life
As a reminder, Python 2 has reached “end of life” on the 1st of January 2020. What this means is, we are removing tools that depend on Python 2. Why? Because they are no longer being maintained, they are not receiving updates, and they need replacing. The pentesting landscape is a dynamic field that is forever changing. It’s time to keep up. We will be doing our best to find alternatives that are actively worked upon.
Giving A Helping Hand
If you want to contribute to Kali please do! If you have an area, idea of something YOU would like to work on, please dig in. If you want to help, but don’t know where to start, please see our docs page. If you have a suggestion for a feature, please record it on the bug tracker.
Note: the bug tracker is for bugs & suggestions. Its not a place to get help or support — that’s for the forums.
Download Kali Linux 2020.1
Fresh images Why are you waiting? Start downloading now!
Existing Upgrades If you already have an existing Kali installation, remember you can always do a quick update:
You should now be on Kali Linux 2020.1. We can do a quick check by doing:
NOTE: The output of uname -r may be different depending on architecture.
As always, should you come across any bugs in Kali, please submit a report on our bug tracker. We’ll never be able to fix what we don’t know is broken.
Источник
Kali linux download free download
IMPORTANT! Never download Kali Linux images from anywhere other than the official sources.
Always be sure to verify the SHA256 checksums of the file you’ve downloaded against our official values.
It would be easy for a malicious entity to modify a Kali installation to contain exploits or malware and host it unofficially.
Where to Get Official Kali Linux Images
ISO Files for Intel-based PCs
In order to run Kali “Live” from a USB drive on standard Windows and Apple PCs, you’ll need a Kali Linux bootable ISO image, in either 32-bit or 64-bit format.
If you’re not sure of the architecture of the system you want to run Kali on, on Linux or macOS, you can run the command uname -m at the command line. If you get the response, “x86_64”, use the 64-bit ISO image (the one containing “amd64” in the file name); if you get “i386”, use the 32-bit image (the one containing “i386” in the file name). If you’re on a Windows system, the procedure for determining whether your architecture is detailed on Microsoft’s website.
The Kali Linux images are available both as directly downloadable “.iso/.img” files or via “.torrent” files.
Building your own Kali Linux ISO, standard or customized, is a very simple process.
Virtual Machines Images
If you want to run Kali Linux as a “guest” under VMware or VirtualBox, Kali Linux is available as a pre-built virtual machines with any guest tools already installed. These image are available in a 64-bit (amd64), and 32-bit PAE (i*86) formats.
ARM Images
The hardware architectures of ARM-based devices vary considerably, so it is not possible to have a single image that will work across all of them. Pre-built Kali Linux images for the ARM architecture are available for a wide range of devices.
Scripts for building your own ARM images locally are also available on GitLab. For more details, see the articles on setting up an ARM cross-compilation environment and building a custom Kali Linux ARM chroot.
Verifying Your Downloaded Kali Image
Why do I need to do this?
Before you run Kali Linux Live, or install it to your hard disk, you want to be very sure that what you’ve got actually is Kali Linux, and not an imposter. Kali Linux is a professional penetration testing and forensics toolkit. As a professional penetration tester, having absolute confidence in the integrity of your tools is critical: if your tools are not trustworthy, your investigations will not be trustworthy, either.
Moreover, as the leading penetration testing distribution, Kali’s strengths mean that a bogus version of Kali Linux could do a tremendous amount of damage if it were deployed unwittingly. There are plenty of people with plenty of reason to want to stick very sketchy stuff into something that looks like Kali, and you absolutely do not want to find yourself running something like that.
Avoiding this is simple:
- Only download Kali Linux via the official download pages at kali.org/downloads/ or offensive-security.com/kali-linux-vmware-arm-image-download/ — you will not be able to browse to these pages without SSL; encrypting the connection makes it much harder for an attacker to use a “man-in-the-middle” attack to modify your download. There are a few potential weaknesses to even these sources — see the sections on verifying the download with the SHA256SUMS file and its signature against the official Kali Development team private key for something much closer to absolute assurance.
- Once you’ve downloaded an image, and before you run it, always validate that it really is what it’s supposed to be by verifying its checksum using one of the procedures detailed below.
There are several methods for verifying your download. Each provides a certain level of assurance, and involves a corresponding level of effort on your part.
- You can download an ISO image from an official Kali Linux “Downloads” mirror, calculate the ISO’s SHA256 hash and compare it by inspection with the value listed on the Kali Linux site. This is quick and easy, but potentially susceptible to subversion via a DNS poisoning: it assumes that the site to which, for example, the domain “kali.org” resolves is in fact the actual Kali Linux site. If it somehow were not, an attacker could present a “loaded” image and a matching SHA256 signature on the fake web page. See the section “Manually Verify the Signature on the ISO (Direct Download)”, below.
- You can download an ISO image through the torrents, and it will also pull down a file — unsigned — containing the calculated SHA256 signature. You can then use the shasum command (on Linux and macOS) or a utility (on Windows) to automatically verify that the file’s computed signature matches the signature in the secondary file. This is even easier than the “manual” method, but suffers from the same weakness: if the torrent you pulled down is not really Kali Linux, it could still have a good signature. See the section “Verify the Signature on the ISO Using the Included Signature File (Torrent Download)”, below.
- To be as close to absolutely certain as possible that the Kali Linux download you’ve obtained is the real thing, you can download both a cleartext signature file and and version of the same file that has been signed with the official Kali Linux private key and use GNU Privacy Guard (GPG) to first, verify that the computed SHA256 signature and the signature in the cleartext file match and second, verify that the signed version of the file containing the SHA256 hash has been correctly signed with the official key.
If you use this more complicated process and successfully validate your downloaded ISO, you can proceed with pretty complete assurance that what you’ve got is the official image and that it has not been tampered with in any way. This method, while the most complex, has the advantage of providing independent assurance of the integrity of the image. The only way this method can fail is if the official Kali Linux private key is not only subverted by an attacker, but also not subsequently revoked by the Kali Linux development team. For this method, see the section on verification using the SHA256SUMS file.
What do I need to do this?
If you’re running on Linux, you probably already have GPG (GNU Privacy Guard) installed. If you’re on Windows or macOS, you’ll need to install the appropriate version for your platform.
- If you’re on a PC running Windows, download and install GPG4Win from here. Certain versions of Windows do not have the native ability to calculate SHA256 checksums. To check this, you can open the command prompt and run certutil -? . If you do have this installed, you can run certutil -hashfile kali-linux-2021.3-live-amd64.iso sha256 to verify your download. If you do not have certutil installed, you will also need a utility such as Microsoft File Checksum Integrity Verifier or Hashtab to verify your download.
- If you’re on a Macintosh running macOS, download and install GPGTools from here. Alternatively, if you have Homebrew installed, just run brew install gnupg
Once you’ve installed GPG, you’ll need to download and import a copy of the Kali Linux official key. Do this with the following command:
Your output should look like this:
Verify that the key is properly installed with the command:
The output will look like this:
You’re now set up to validate your Kali Linux download.
How Do I Verify My Downloaded Image?
Manually Verify the Signature on the ISO (Direct Download)
If you downloaded the ISO directly from the downloads page, verify it using the following procedure.
On Linux, or macOS, you can generate the SHA256 checksum from the ISO image you’ve downloaded with the following command (assuming that the ISO image is named “kali-linux-2021.3-live-amd64.iso”, and is in your current directory):
The output should look like this:
The resulting SHA256 signature, “e316b27025922e9f6bca0cacee6dde83dbfd4a549ad18026526f5824af639fc1”, can be seen to match the signature displayed in the “sha256sum” column on the official download page for the 64-bit Intel architecture Kali Linux 2021.3 ISO image:
Verify the Signature on the ISO Using the Included Signature File (Torrent Download)
If you downloaded your copy of the Kali Linux ISO image via the torrents, in addition to the ISO file (e.g. kali-linux-2021.3-live-amd64.iso), there will be a second file containing the computed SHA256 signature for the ISO, with the extension “.txt.sha256sum” (e.g. kali-linux-2021.3-live-amd64.txt.sha256sum). You can use this file to verify the authenticity of your download on Linux or macOS with the following command:
If the image is successfully authenticated, the response will look like this:
IMPORTANT! If you are unable to verify the authenticity of the Kali Linux image you have downloaded as described in the preceding section, do NOT use it! Using it could endanger not only your own system, but any network you connect to as well as the other systems on that network. Stop, and ensure that you have downloaded the images from a legitimate Kali Linux mirror.
Verify the ISO Using the SHA256SUMS File
This is a more complex procedure, but offers a much higher level of validation: it does not rely on the integrity of the web site you downloaded the image from, only the official Kali Linux development team key that you install independently. To verify your image this way for an Intel architecture version of Kali, you will need to download three files from the Kali “Live CD Image” site for the current release (v2021.3, as of this writing):
- The ISO image itself (e.g. kali-linux-2021.3-live-amd64.iso)
- The file containing the calculated SHA256 hash for the ISO, SHA256SUMS
- The signed version of that file, SHA256SUMS.gpg
Before verifying the checksums of the image, you must ensure that the SHA256SUMS file is the one generated by Kali Linux. That’s why the file is signed by Kali’s official key with a detached signature in SHA256SUMS.gpg. If you have not already done so, Kali’s official key can be downloaded and imported into your keychain with this command:
or this command
Your output should look like this:
You should verify that the key is properly installed with the command:
The output will look like this:
Once you have downloaded both SHA256SUMS and SHA256SUMS.gpg, you can verify the signature as follows:
If you do not get that “Good signature” message or if the key ID does not match, then you should stop and review whether you downloaded the images from a legitimate Kali Linux mirror. The failed verification strongly suggests that the image you have may have been tampered with.
If you did get the “Good signature” response, you can now be assured that the checksum in the SHA256SUMS file was actually provided by the Kali Linux development team. All that remains to be done to complete the verification is to validate that the signature you compute from the ISO you’ve downloaded matches the one in the SHA256SUMS file. You can do that on Linux or macOS with the following command (assuming that the ISO is named “kali-linux-2021.3-live-amd64.iso” and is in your working directory):
If the image is successfully authenticated, the response will look like this:
If you do not get “OK” in response, then stop and review what’s happened: the Kali image you have has apparently been tampered with. Do NOT use it.
Once you’ve downloaded and verified your image, you can proceed to create a bootable “Kali Linux Live” USB drive.
Updated on: 2021-Sep-27
Authors: g0tmi1k , gamb1t
Источник