- Kali Linux — Exploitation Tools
- Metasploit
- Armitage
- Linux Exploit Suggester
- Exploitation Tools in Kali Linux 2020.1
- Metasploit Framework Console msf
- MSFPC
- searchsploit
- Social Engineering Toolkit/SET
- sqlmap
- Conclusion
- About the author
- Younis Said
- Kali Linux – Exploitation Tools
- 1. Metasploit
- 2. BeEF
- 3. Armitage
- 4. SQLMap
- 5. aircrack-ng
Kali Linux — Exploitation Tools
In this chapter, we will learn about the various exploitation tools offered by Kali Linux.
Metasploit
As we mentioned before, Metasploit is a product of Rapid7 and most of the resources can be found on their web page www.metasploit.com. It is available in two versions — commercial and free edition. The differences between these two versions is not much hence, in this case we will be using the Community version (free).
As an Ethical Hacker, you will be using “Kali Ditribution” which has the Metasploit community version embedded, along with other ethical hacking tools which are very comfortable by saving time of installation. However, if you want to install as a separate tool it is an application that can be installed in the operating systems like Linux, Windows and OS X.
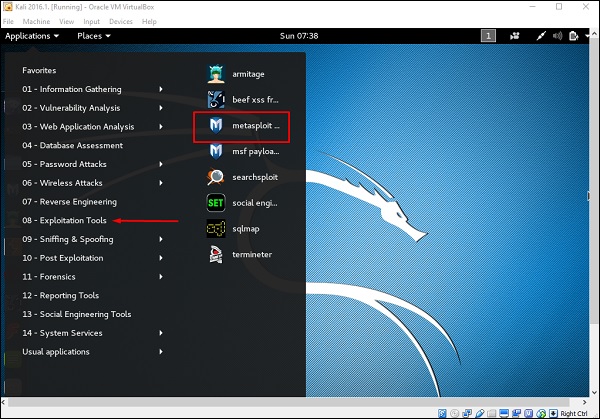
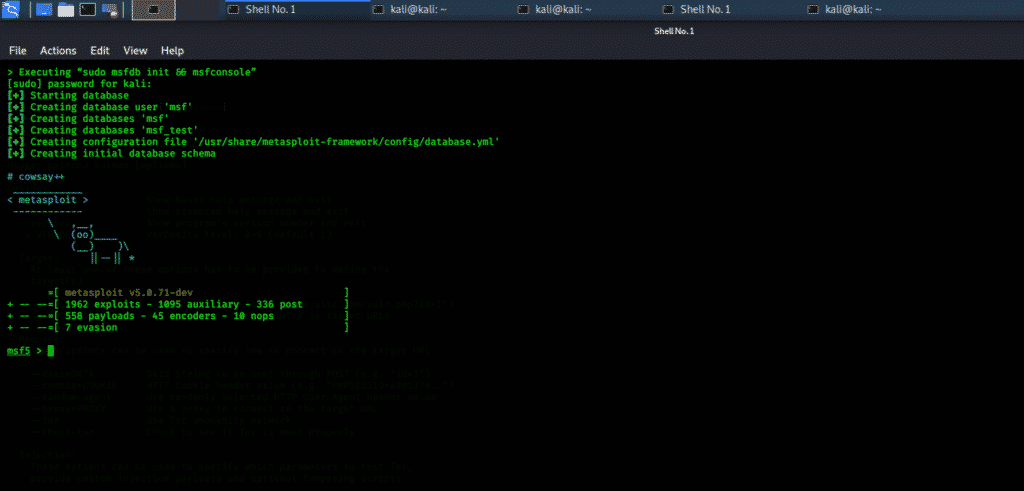
First, open the Metasploit Console in Kali. Then, go to Applications → Exploitation Tools → Metasploit.
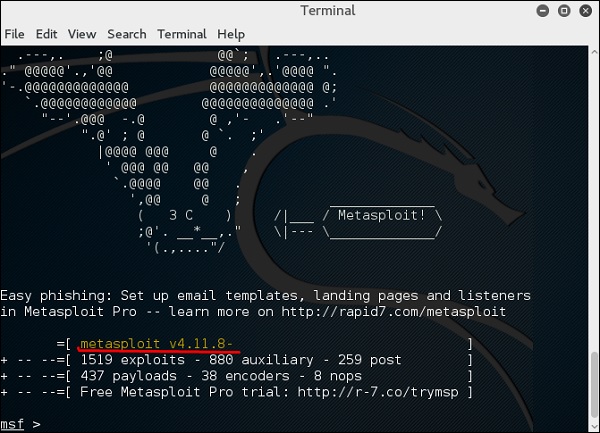
After it starts, you will see the following screen, where the version of Metasploit is underlined in red.
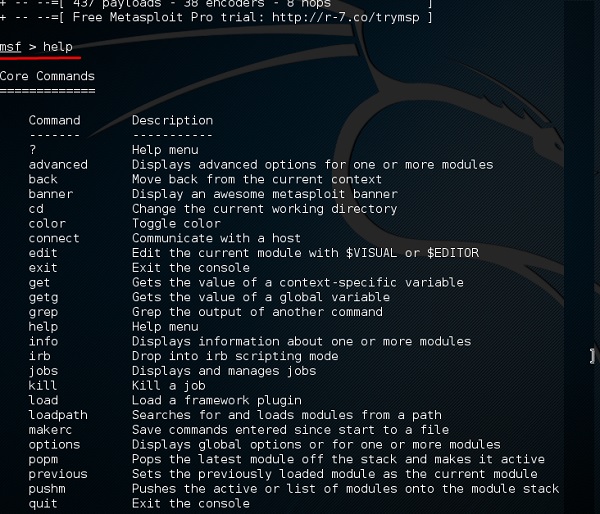
In the console, if you use help or ? symbol, it will show you a list with the commands of MSP along with their description. You can choose based on your needs and what you will use.
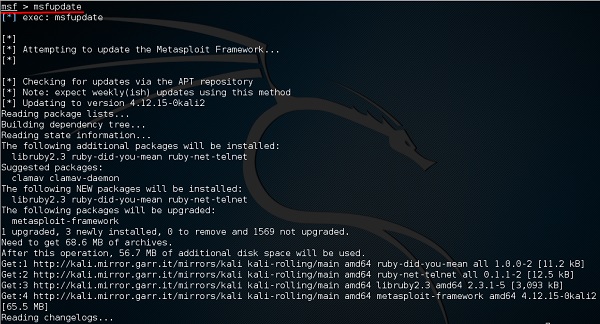
Another important administration command is msfupdate which helps to update the metasploit with the latest vulnerability exploits. After running this command in the console, you will have to wait several minutes until the update is complete.
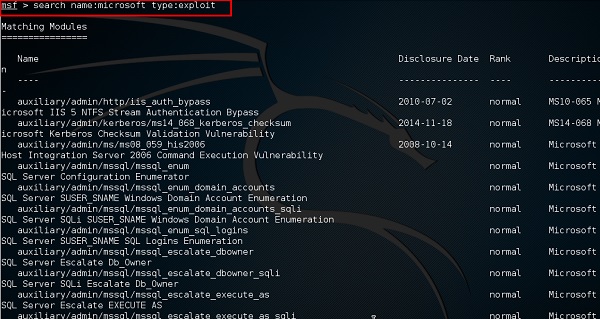
It has a good command called “Search” which you can use to find what you want as shown in the following screenshot. For example, I want to find exploits related to Microsoft and the command can be msf >search name:Microsoft type:exploit.
Where “search” is the command, ”name” is the name of the object that we are looking for, and “type” is what kind of script we are looking for.
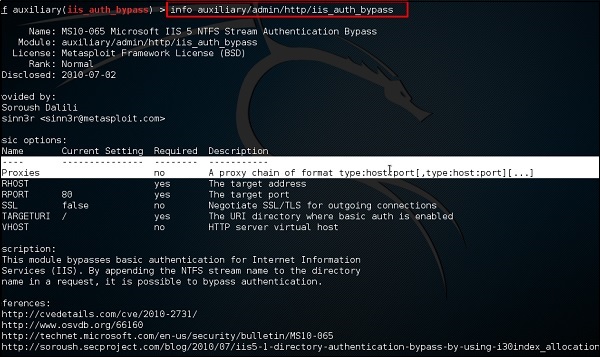
Another command is “info”. It provides the information regarding a module or platform where it is used, who is the author, vulnerability reference, and the payload restriction that this can have.
Armitage
Armitage GUI for metasploit is a complement tool for metasploit. It visualizes targets, recommends exploits, and exposes the advanced post-exploitation features.
Let’s open it, but firstly metasploit console should be opened and started. To open Armitage, go to Applications → Exploit Tools → Armitage.
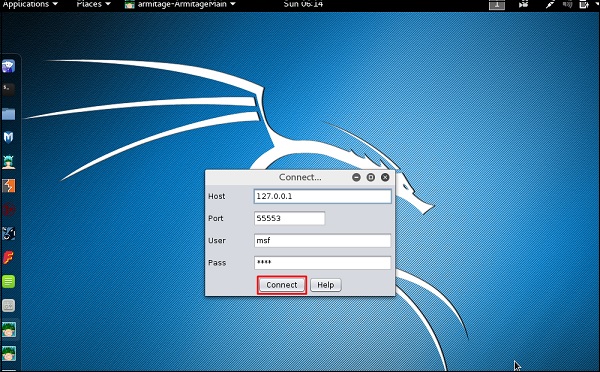
Click the Connect button, as shown in the following screenshot.
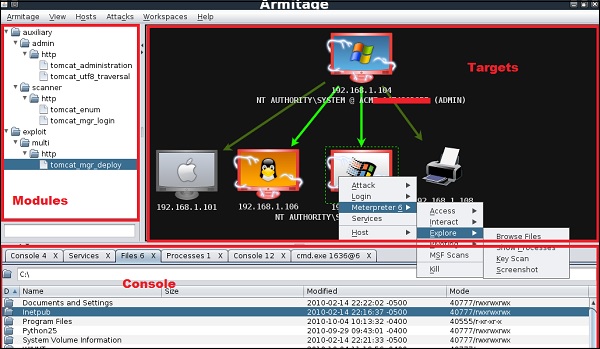
When it opens, you will see the following screen.
Armitage is user friendly. The area “Targets” lists all the machines that you have discovered and you are working with, the hacked targets are red in color with a thunderstorm on it.
After you have hacked the target, you can right-click on it and continue exploring with what you need to do such as exploring (browsing) the folders.
In the following GUI, you will see the view for the folders, which is called console. Just by clicking the folders, you can navigate through the folders without the need of metasploit commands.
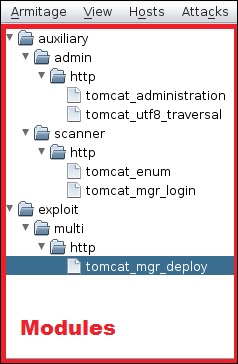
On the right side of the GUI, is a section where the modules of vulnerabilities are listed.
BeEF stands for Browser Exploitation Framework. It is a penetration testing tool that focuses on the web browser. BeEF allows the professional penetration tester to assess the actual security posture of a target environment using client-side attack vectors.
First, you have to update the Kali package using the following commands −
To start, use the following command −
Open the browser and enter the username and password: beef.
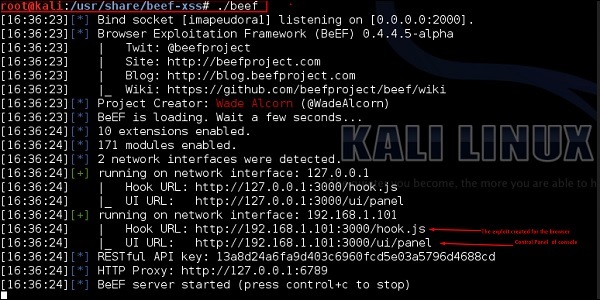
The BeEF hook is a JavaScript file hosted on the BeEF server that needs to run on client browsers. When it does, it calls back to the BeEF server communicating a lot of information about the target. It also allows additional commands and modules to be ran against the target. In this example, the location of BeEF hook is at http://192.168.1.101:3000/hook.js.
In order to attack a browser, include the JavaScript hook in a page that the client will view. There are a number of ways to do that, however the easiest is to insert the following into a page and somehow get the client to open it.
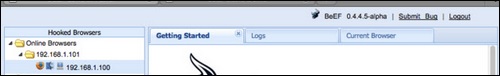
Once the page loads, go back to the BeEF Control Panel and click “Online Browsers” on the top left. After a few seconds, you should see your IP address pop-up representing a hooked browser. Hovering over the IP will quickly provide information such as the browser version, operating system, and what plugins are installed.
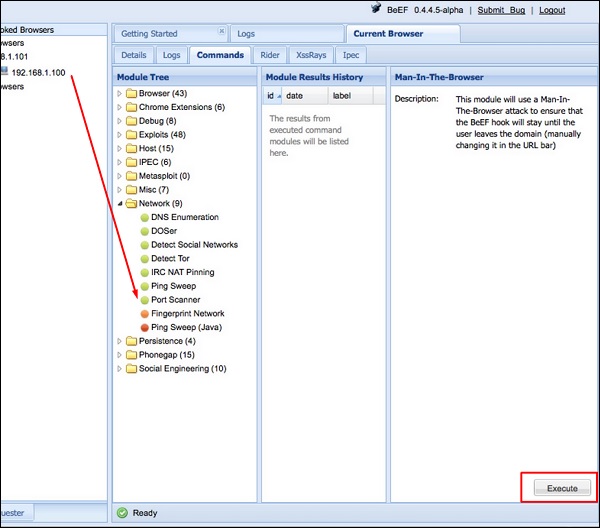
To remotely run the command, click the “Owned” host. Then, on the command click the module that you want to execute, and finally click “Execute”.
Linux Exploit Suggester
It suggests possible exploits given the release version ‘uname -r’ of the Linux Operating System.
To run it, type the following command −
3.0.0 is the kernel version of Linux OS that we want to exploit.
Источник
Exploitation Tools in Kali Linux 2020.1
Metasploit Framework Console msf
Metasploit Framework is a penetration testing tool that can exploit and validate vulnerabilities. This tool contains the basic infrastructure, specific content, and tools necessary for penetration testing and vast security assessment. Metasploit Framework is one of the most famous exploitation frameworks and is updated on a regular basis. New exploits are updated as soon as they are published. This program contains many tools that are used for creating security workspaces for vulnerability testing and penetration testing systems.
Metasploit Framework can be accessed in the Kali Whisker Menu, and can also be launched directly from the terminal.
Check the following commands to see the various tools included in the Metasploit Framework.
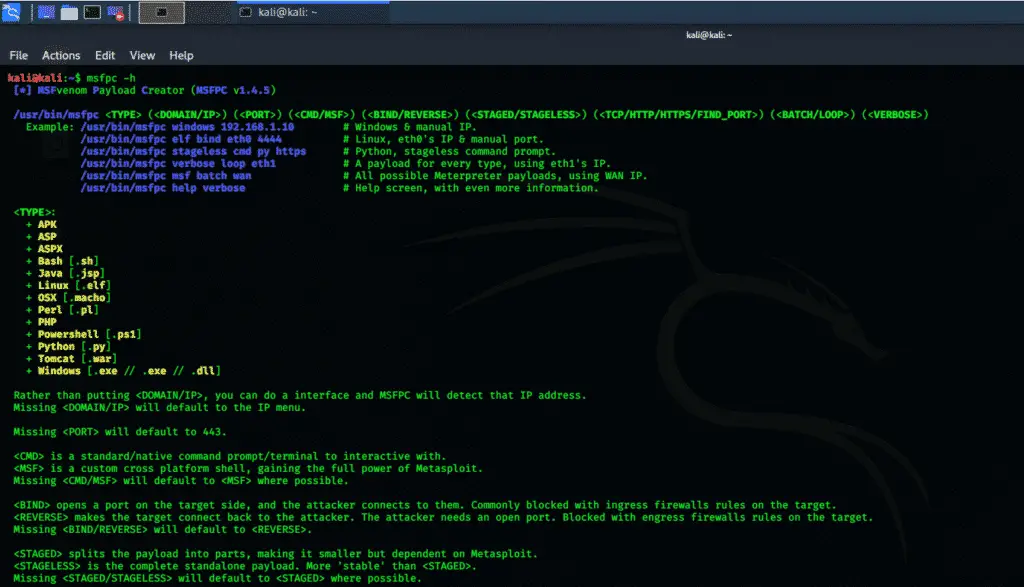
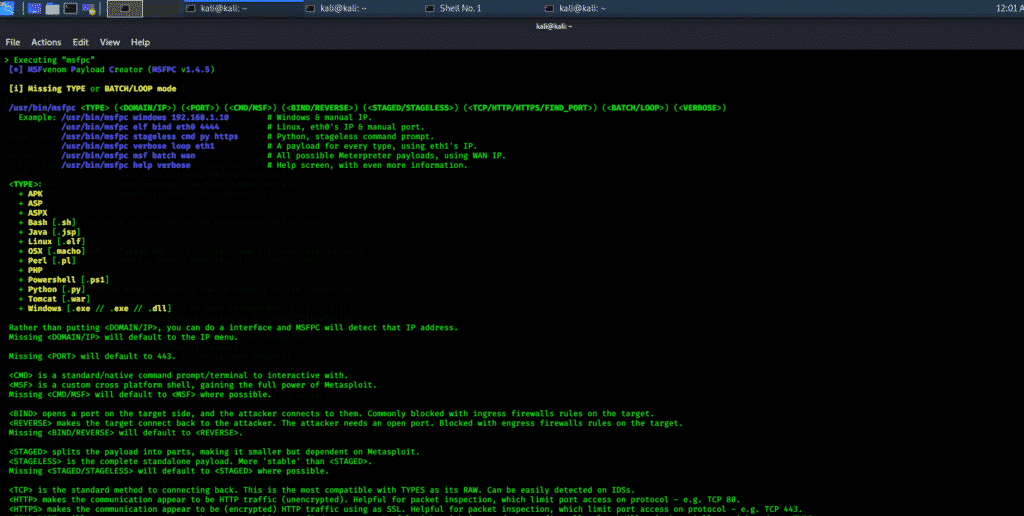
MSFPC
MSFPC is a package that contains several tools that can generate various payloads based on user-specific options. This package is also called the MSFvenom payload creator, and its goal is to automate the processes involved in working with Metasploit and msfvenom. The MSFPC help command can be launched using the following console command.
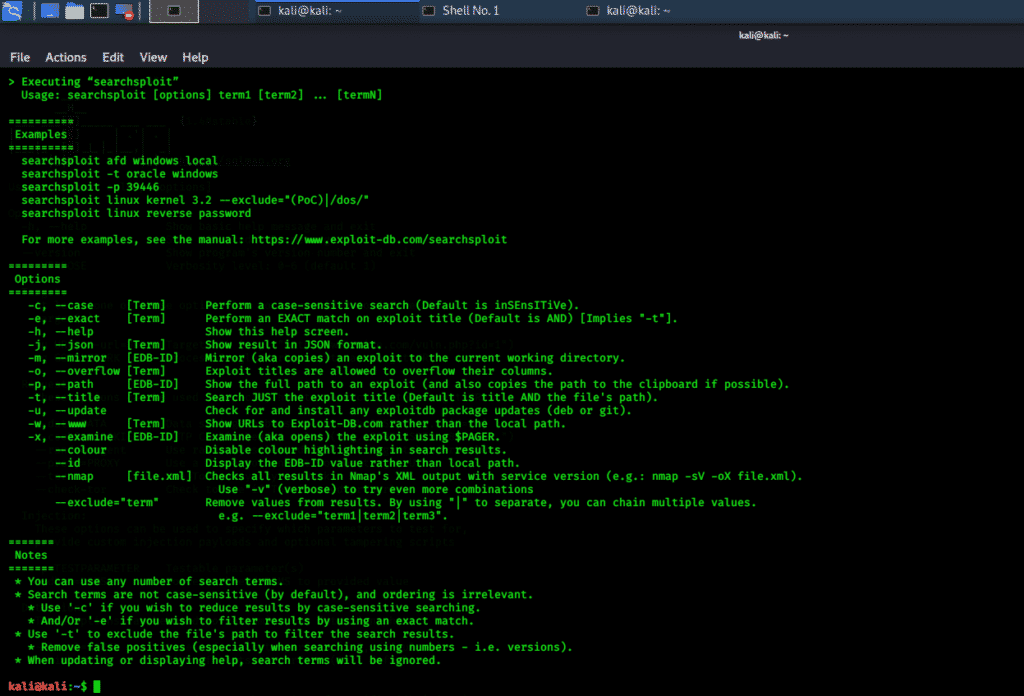
searchsploit
Searchsploit is a search tool for the Exploit-DB Framework that can execute detailed offline searches on a local machine. This method is useful in security testing and can be used for evaluating a network that does not have access to the internet. There are many vulnerabilities within the network, stored in binary files, that can be sought out using Exploit-DB binary searches.
Searchsploit is a console-based tool that can be accessed both from the Kali Whisker Menu and the terminal window.
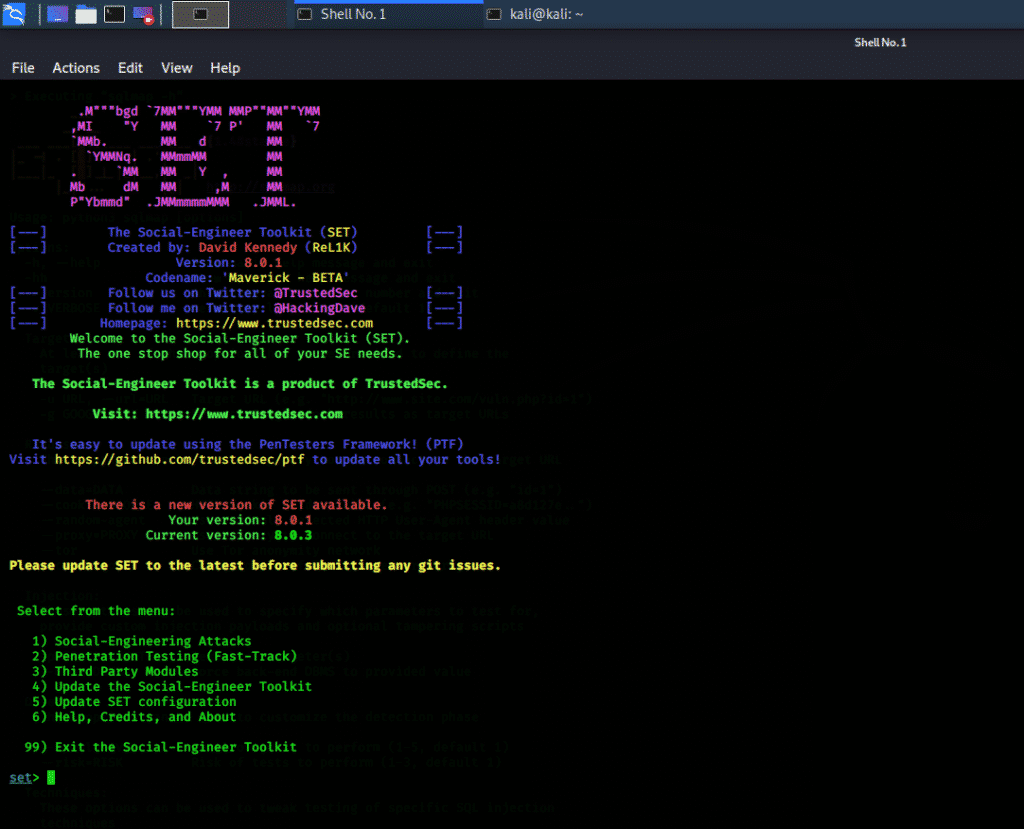
Social Engineering Toolkit/SET
Social Engineering Toolkit (SET) is an open-source, free-ware, penetration testing tool for social engineering and custom attacks. Social Engineering Toolkit contains several custom attack vectors that can help in making a successful attack in no time. This program is very fast and has two main types of attacks: social engineering attacks and penetration testing – or fast-track – attacks. This program can be started directly from the terminal window using the following command.
sqlmap
Sqlmap is one of the most popular open-source exploitation tools for SQL injection. Sqlmap automates the detection process and exploitation flaws of SQL database servers. This tool has a very powerful detecting engine. Sqlmap also provides a wide range of switches, from database fingerprinting to accessing the complete underlying file system. This program executes commands through out-of-band connections, and is the ultimate tool for penetration testing.
Features of this tool include:
- Full support for the following database management systems: Microsoft SQL Server, PostgreSQL, Microsoft Access, MySQL, SQLite, Oracle, and Firebird
- Provides support to various SQL injection methods
- Can bypass SQL injection and get access to the database
- Dictionary-based attacks for password hashing and cracking
A number of functions are included in the sqlmap framework, such as injection, detection, methods, enumerations, operating system access, and sqlmap shell.
Conclusion
In this article, we identified the most important exploitation frameworks and tools in Kali Linux 2020.1. All toolkits and frameworks discussed in this article are open-source and provide features that are necessary for every pentester.
About the author
Younis Said
I am a freelancing software project developer, a software engineering graduate and a content writer. I love working with Linux and open-source software.
Источник
Kali Linux – Exploitation Tools
After Scanning, information Gathering, and finding a vulnerability comes the main concept of hacking which is Exploitation of the vulnerability. Vulnerability is not that effective if it can not be exploited or it could not cause harm to the application, So in order to get the impact of the vulnerability, we have to exploit also in many cases we have to take down a hacker’s or a spammer’s website. So we have to find a vulnerability on the website and have to exploit it.
Kali Linux comes packed with 300+ tools for cybersecurity and penetration testing out of which many of the tools are used to exploit these vulnerabilities, a few of them are listed below.
1. Metasploit
Metasploit Framework is basically a penetration testing tool that exploits the website and validates vulnerabilities. This tool contains the basic infrastructure, specific content, and tools necessary for penetration testing and vast security assessment. Metasploit Framework is one of the most famous exploitation frameworks and is updated on a regular basis. It can be accessed in the Kali Whisker Menu, and can also be launched directly from the terminal. Also here, new exploits are updated as soon as they are published.
It contains many tools that are used for creating security workspaces for vulnerability testing and penetration testing systems. It was designed by rapid7 LLC and is completely open-source software and is easy to use.
To use Metasploit:
2. BeEF
BeEF or Browser Exploitation Framework is basically a penetration testing tool that runs and gets executed on the web browser. It also allows professional penetration tester using client-side attack vectors to assess the actual security posture of a target environment. This tool mainly focuses on the Web Browser. It hooks web browsers in order to use them as a base or launchpad to attack the system and to execute the malicious codes and payloads.
To use BeEF, enter the following command in the terminal.
3. Armitage
Armitage is a tool that is used to visualize targets, recommends exploits, and to expose exploitation features in the framework.
Armitage is basically a scriptable red team collaboration tool for Metasploit framework or in other words it is a GUI version of the Metasploit framework. It contains many tools that are used for creating security workspaces for vulnerability testing and penetration testing systems. Being a GUI based package, it is a good alternative to Metasploit.
To use Armitage, enter the following command in the terminal.
4. SQLMap
SQLMap is an open-source tool that is used to automate the process of manual SQL injection over a parameter on a website. It detects and exploits the SQL injection parameters itself all we have to do is to provide it with an appropriate request or URL. It supports 34 databases including MySQL, Oracle, PostgreSQL, etc.
To use sqlmap tool:
- sqlmap comes pre-installed in Kali Linux
- Just type sqlmap in the terminal to use the tool.
5. aircrack-ng
Aircrack is an all in one packet sniffer, WEP and WPA/WPA2 cracker, analyzing tool and a hash capturing tool. It is a tool used for wifi hacking. It helps in capturing the package and reading the hashes out of them and even cracking those hashes by various attacks like dictionary attacks. It supports almost all the latest wireless interfaces.
To use aircrack-ng, enter the following command in the terminal:
Источник