- 21 Best Kali Linux Tools for Hacking and Penetration Testing
- Top Kali Linux Tools for Hacking and Penetration Testing
- 1. Nmap
- 2. Lynis
- 3. WPScan
- 4. Aircrack-ng
- 5. Hydra
- 6. Wireshark
- 7. Metasploit Framework
- 8. Skipfish
- 9. Maltego
- 10. Nessus
- 11. Burp Suite Scanner
- 12. BeEF
- 13. Apktool
- 14. sqlmap
- 15. John the Ripper
- 16. Snort
- 17. Autopsy Forensic Browser
- 18. King Phisher
- 19. Nikto
- 20. Yersinia
- 21. Social Engineering Toolkit (SET)
- Top 10 Kali Linux Tools For Hacking
- 1. Nmap
- 2. Burp Suite
- 3. Wireshark
- 4. metasploit Framework
- 5. aircrack-ng
- 7. John the Ripper
- 8. sqlmap
- 9. Autopsy
- 10. Social Engineering Toolkit
21 Best Kali Linux Tools for Hacking and Penetration Testing
Last updated March 4, 2020 By Ankush Das 10 Comments
Here’s our list of best Kali Linux tools that will allow you to assess the security of web-servers and help in performing hacking and pen-testing.
If you read the Kali Linux review, you know why it is considered one of the best Linux distributions for hacking and pen-testing and rightly so. It comes baked in with a lot of tools to make it easier for you to test, hack, and for anything else related to digital forensics.
It is one of the most recommended Linux distro for ethical hackers. Even if you are not a hacker but a webmaster – you can still utilize some of the tools to easily run a scan of your web server or web page.
In either case, no matter what your purpose is – we shall take a look at some of the best Kali Linux tools that you should be using.
Note that not all tools mentioned here are open source.
Top Kali Linux Tools for Hacking and Penetration Testing
There are several types of tools that comes pre-installed. If you do not find a tool installed, simply download it and set it up. It’s easy.
1. Nmap
Nmap or “Network Mapper” is one of the most popular tools on Kali Linux for information gathering. In other words, to get insights about the host, its IP address, OS detection, and similar network security details (like the number of open ports and what they are).
It also offers features for firewall evasion and spoofing.
2. Lynis
Lynis is a powerful tool for security auditing, compliance testing, and system hardening. Of course, you can also utilize this for vulnerability detection and penetration testing as well.
It will scan the system according to the components it detects. For example, if it detects Apache – it will run Apache-related tests for pin point information.
3. WPScan
WordPress is one of the best open source CMS and this would be the best free WordPress security auditing tool. It’s free but not open source.
If you want to know whether a WordPress blog is vulnerable in some way, WPScan is your friend.
In addition, it also gives you details of the plugins active. Of course, a well-secured blog may not give you a lot of details, but it is still the best tool for WordPress security scans to find potential vulnerabilities.
4. Aircrack-ng
Aircrack-ng is a collection of tools to assess WiFi network security. It isn’t just limited to monitor and get insights – but it also includes the ability to compromise a network (WEP, WPA 1, and WPA 2).
If you forgot the password of your own WiFi network – you can try using this to regain access. It also includes a variety of wireless attacks with which you can target/monitor a WiFi network to enhance its security.
5. Hydra
If you are looking for an interesting tool to crack login/password pairs, Hydra will be one of the best Kali Linux tools that comes pre-installed.
It may not be actively maintained anymore – but it is now on GitHub, so you can contribute working on it as well.
6. Wireshark
Wireshark is the most popular network analyzer that comes baked in with Kali Linux. It can be categorized as one of the best Kali Linux tools for network sniffing as well.
It is being actively maintained, so I would definitely recommend trying this out. And it’s really easy to install Wireshark on Linux.
7. Metasploit Framework
Metsploit Framework is the most used penetration testing framework. It offers two editions – one (open source) and the second is the pro version to it. With this tool, you can verify vulnerabilities, test known exploits, and perform a complete security assessment.
Of course, the free version won’t have all the features, so if you are into serious stuff, you should compare the editions here.
8. Skipfish
Similar to WPScan, but not just focused for WordPress. Skipfish is a web application scanner that would give you insights for almost every type of web applications. It’s fast and easy to use. In addition, its recursive crawl method makes it even better.
For professional web application security assessments, the report generated by Skipfish will come in handy.
9. Maltego
Maltego is an impressive data mining tool to analyze information online and connect the dots (if any). As per the information, it creates a directed graph to help analyze the link between those pieces of data.
Do note, that this isn’t an open source tool.
It comes pre-installed, however, you will have to sign up in order to select which edition you want to use. If you want for personal use, the community edition will suffice (you just need to register for an account) but if you want to utilize for commercial purpose, you need the subscription to the classic or XL version.
10. Nessus
If you have a computer connected to a network, Nessus can help find vulnerabilities that a potential attacker may take advantage of. Of course, if you are an administrator for multiple computers connected to a network, you can make use of it and secure those computers.
However, this is not a free tool anymore, you can try it free for 7 days on from its official website.
11. Burp Suite Scanner
Burp Suite Scanner is a fantastic web security analysis tool. Unlike other web application security scanner, Burp offers a GUI and quite a few advanced tools.
However, the community edition restricts the features to only some essential manual tools. For professionals, you will have to consider upgrading. Similar to the previous tool, this isn’t open source either.
I’ve used the free version, but if you want more details on it, you should check out the features available on their official website.
12. BeEF
BeEF (Browser Exploitation Framework) is yet another impressive tool. It has been tailored for penetration testers to assess the security of a web browser.
This is one of the best Kali Linux tools because a lot of users do want to know and fix the client-side problems when talking about web security.
13. Apktool
Apktool is indeed one of the popular tools found on Kali Linux for reverse engineering Android apps. Of course, you should make good use of it – for educational purposes.
With this tool, you can experiment some stuff yourself and let the original developer know about your idea as well. What do you think you’ll be using it for?
14. sqlmap
If you were looking for an open source penetration testing tool – sqlmap is one of the best. It automates the process of exploiting SQL injection flaws and helps you take over database servers.
15. John the Ripper
John the Ripper is a popular password cracker tool available on Kali Linux. It’s free and open source as well. But, if you are not interested in the community-enhanced version, you can choose the pro version for commercial use.
16. Snort
Want real-time traffic analysis and packet logging capability? Snort has got your back. Even being an open source intrusion prevention system, it has a lot to offer.
The official website mentions the procedure to get it installed if you don’t have it already.
17. Autopsy Forensic Browser
Autopsy is a digital forensic tool to investigate what happened on your computer. Well, you can also use it to recover images from SD card. It is also being used by law enforcement officials. You can read the documentation to explore what you can do with it.
You should also check out their GitHub page.
18. King Phisher
Phishing attacks are very common nowadays. And, King Phisher tool helps test, and promote user awareness by simulating real-world phishing attacks. For obvious reasons, you will need permission to simulate it on a server content of an organization.
19. Nikto
Nikto is a powerful web server scanner – that makes it one of the best Kali Linux tools available. It checks in against potentially dangerous files/programs, outdated versions of server, and many more things.
20. Yersinia
Yersinia is an interesting framework to perform Layer 2 attacks (Layer 2 refers to the data link layer of OSI model) on a network. Of course, if you want a network to be secure, you will have to consider all the seven layers. However, this tool focuses on Layer 2 and a variety of network protocols that include STP, CDP, DTP, and so on.
21. Social Engineering Toolkit (SET)
If you are into pretty serious penetration testing stuff, this should be one of the best tools you should check out. Social engineering is a big deal and with SET tool, you can help protect against such attacks.
Wrapping Up
There’s actually a lot of tools that comes bundled with Kali Linux. Do refer to Kali Linux’ official tool listing page to find them all.
You will find some of them to be completely free and open source while some to be proprietary solutions (yet free). However, for commercial purpose, you should always opt for the premium editions.
We might have missed one of your favorite Kali Linux tools. Did we? Let us know about it in the comments section below.
Like what you read? Please share it with others.
Источник
Top 10 Kali Linux Tools For Hacking
Kali Linux is a Debian-derived Linux distribution that is maintained by Offensive Security. It was developed by Mati Aharoni and Devon Kearns. Kali Linux is a specially designed OS for network analysts, Penetration testers, or in simple words, it is for those who work under the umbrella of cybersecurity and analysis.
The official website of Kali Linux is Kali.org. It gained its popularity when it was practically used in Mr. Robot Series. It was not designed for general purposes, it is supposed to be used by professionals or by those who know how to operate Linux/Kali. To know how to install Kali Linux check its official documentation.
Sometimes we have to automate our tasks while performing penetration testing or hacking as there could be thousands of conditions and payloads to test and testing them manually is a difficult task, So to increase the time efficiency we use tools that come pre-packed with Kali Linux. These tools not only saves our time but also captures the accurate data and output the specific result. Kali Linux comes packed with more than 350 tools which could be useful for hacking or penetration testing. Here we have the list of important Kali Linux tools that could save a lot of your time and effort.
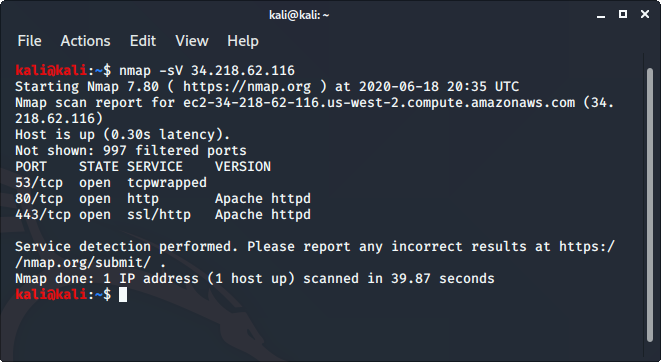
1. Nmap
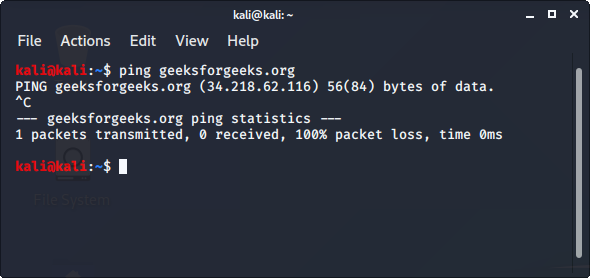
Nmap is an open-source network scanner that is used to recon/scan networks. It is used to discover hosts, ports, and services along with their versions over a network. It sends packets to the host and then analyzes the responses in order to produce the desired results. It could even be used for host discovery, operating system detection, or scanning for open ports. It is one of the most popular reconnaissance tools.
To use nmap:
- Ping the host with ping command to get the IP address
- Open the terminal and enter the following command there:
- Replace the IP address with the IP address of the host you want to scan.
- It will display all the captured details of the host.
To know more, you can read more from here .
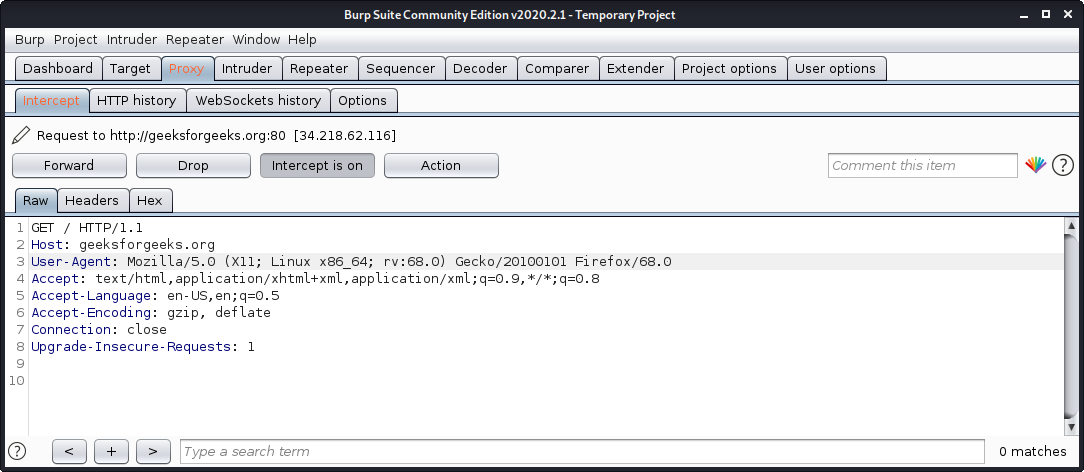
2. Burp Suite
Burp Suite is one of the most popular web application security testing software. It is used as a proxy, so all the requests from the browser with the proxy pass through it. And as the request passes through the burp suite, it allows us to make changes to those requests as per our need which is good for testing vulnerabilities like XSS or SQLi or even any vulnerability related to the web.
Kali Linux comes with burp suite community edition which is free but there is a paid edition of this tool known as burp suite professional which has a lot many functions as compared to burp suite community edition.
To use burpsuite:
- Read this to learn how to setup burp suite.
- Open terminal and type “burpsuite” there.
- Go to the Proxy tab and turn the interceptor switch to on.
- Now visit any URL and it could be seen that the request is captured.
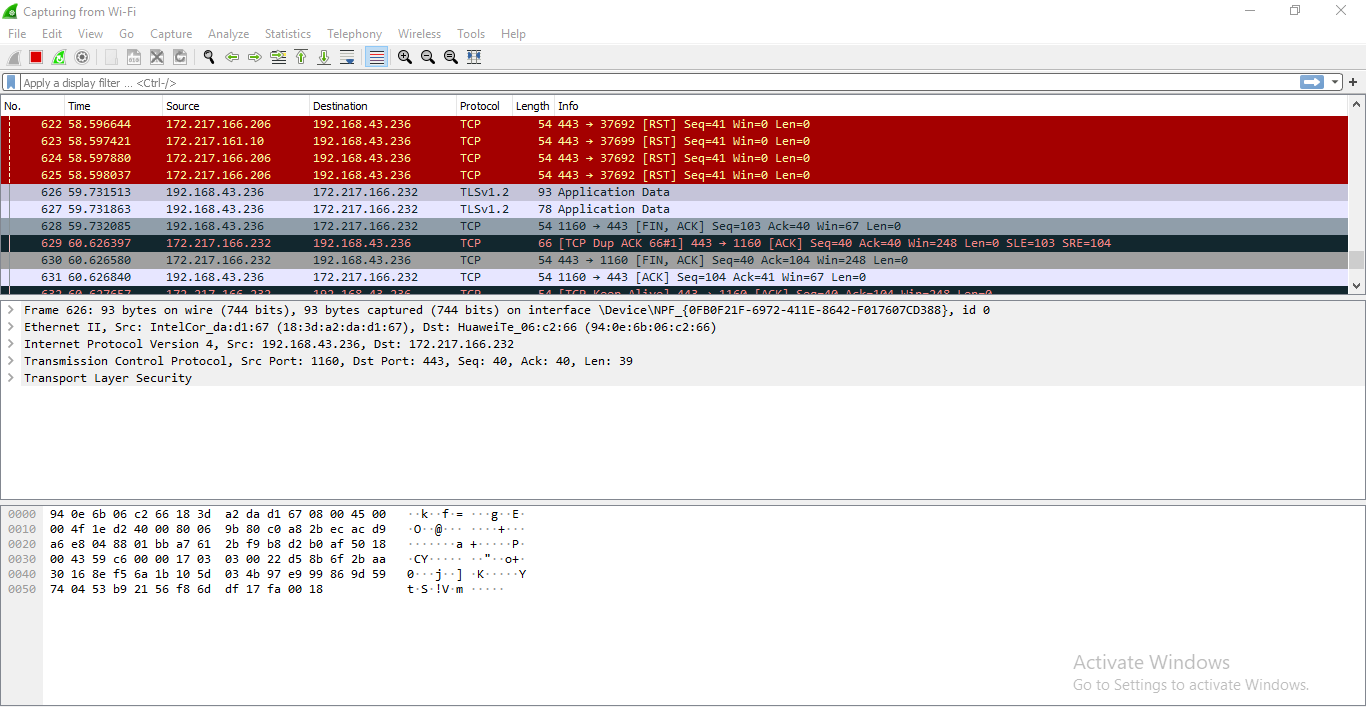
3. Wireshark
Wireshark is a network security tool used to analyze or work with data sent over a network. It is used to analyze the packets transmitted over a network. These packets may have information like the source IP and the destination IP, the protocol used, the data, and some headers. The packets generally have an extension of “.pcap” which could be read using the Wireshark tool. Read thisto learn how to set up and configure Wireshark.
To use wireshark:
- Open Wireshark and download a demo pcap file from here
- Press”ctrl+o” to open a pcap file in wireshsark.
- Now it can be seen that it display the list of packets along with the headers of these packets.
4. metasploit Framework
Metasploit is an open-source tool that was designed by Rapid7 technologies. It is one of the world’s most used penetration testing frameworks. It comes packed with a lot of exploits to exploit the vulnerabilities over a network or operating systems. Metasploit generally works over a local network but we can use Metasploit for hosts over the internet using “port forwarding“. Basically Metasploit is a CLI based tool but it even has a GUI package called “armitage” which makes the use of Metasploit more convenient and feasible.
To use metasploit:
- Metasploit comes pre-installed with Kali Linux
- Just enter “msfconsole” in the terminal.

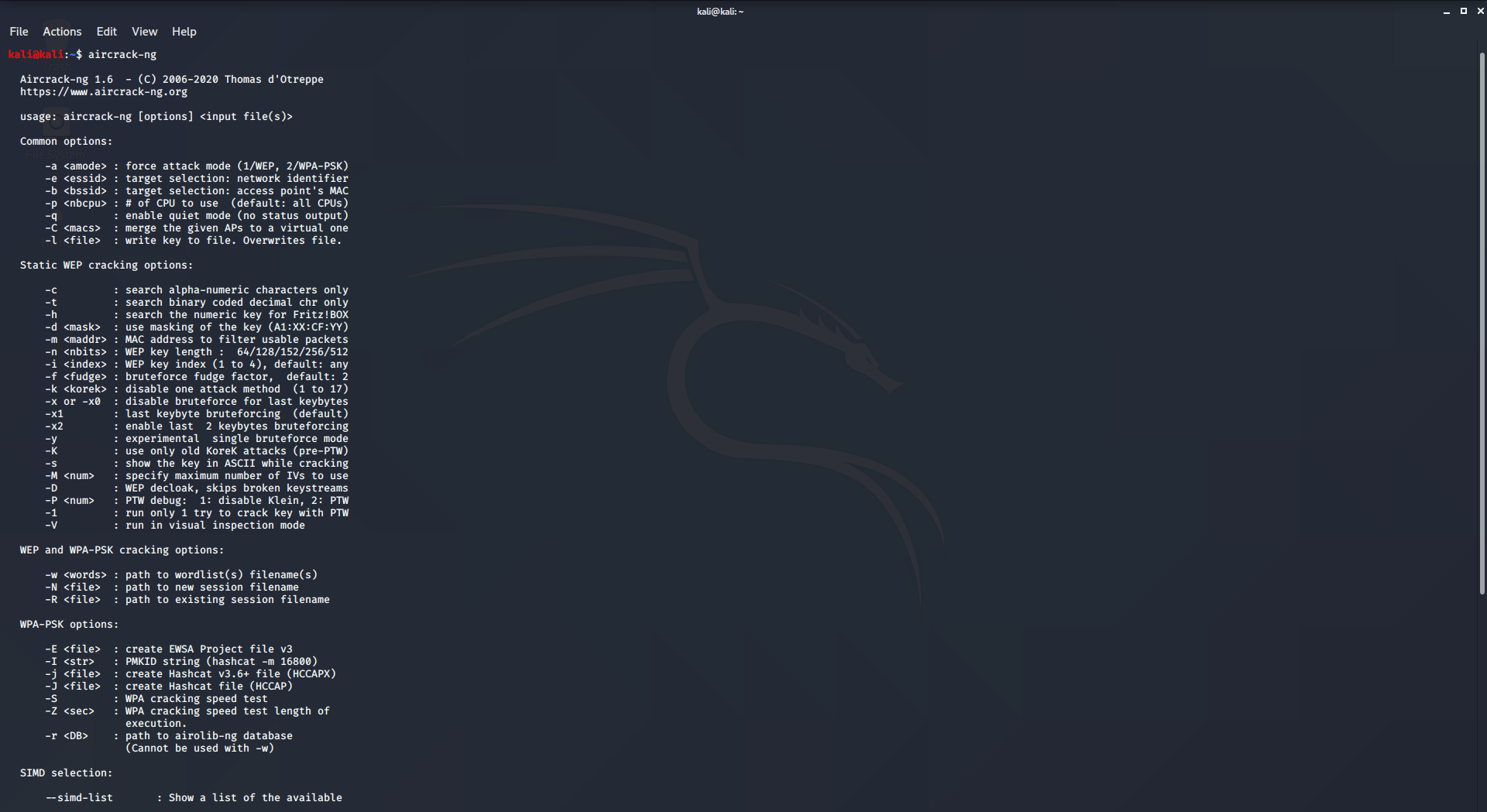
5. aircrack-ng
Aircrack is an all in one packet sniffer, WEP and WPA/WPA2 cracker, analyzing tool and a hash capturing tool. It is a tool used for wifi hacking. It helps in capturing the package and reading the hashes out of them and even cracking those hashes by various attacks like dictionary attacks. It supports almost all the latest wireless interfaces.
To use aircrack-ng:
- aircrack-ng comes pre-compiled with Kali Linux.
- Simply type aircrack-ng in the terminal to use it.
6. Netcat
Netcat is a networking tool used to work with ports and performing actions like port scanning, port listening, or port redirection. This command is even used for Network Debugging or even network daemon testing. This tool is considered as the Swiss army knife of networking tools. It could even be used to do the operating related to TCP, UDP, or UNIX-domain sockets or to open remote connections and much more.
To use netcat:
- Netcat comes pre-installed with Kali Linux.
- Just type “nc” or “netcat” in the terminal to use the tool.
- To perform port listening type the following commands in 2 different terminals.

Read this for more information ragarding netcat tool.
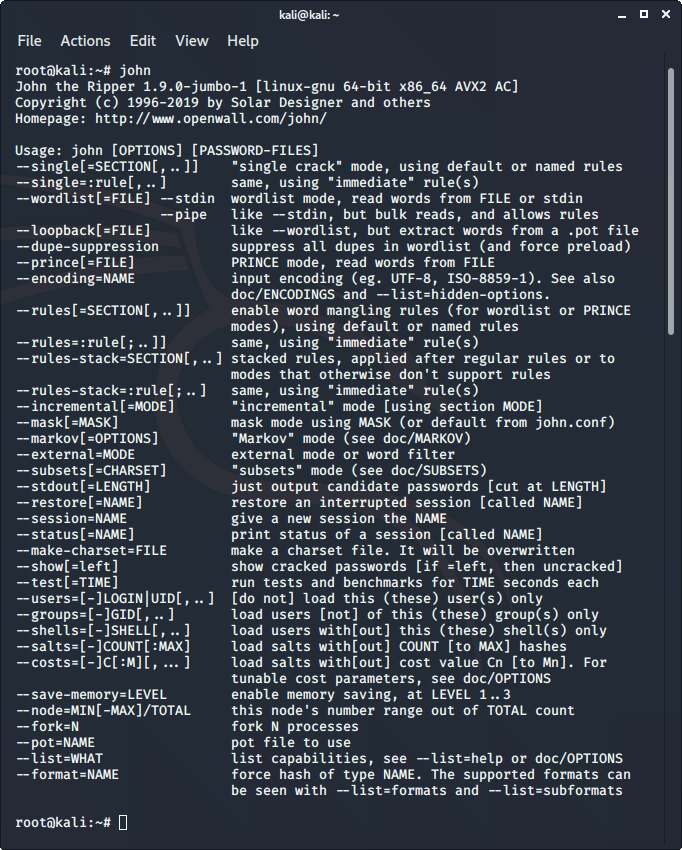
7. John the Ripper
John the Ripper is a great tool for cracking passwords using some famous brute for attacks like dictionary attack or custom wordlist attack etc. It is even used to crack the hashes or passwords for the zipped or compressed files and even locked files as well. It has many available options to crack hashes or passwords.
To use John the Ripper:
- John the ripper comes pre-installed in Kali Linux.
- Just type “john” in the terminal to use the tool.
8. sqlmap
sqlmap is one of the best tools to perform SQL injection attacks. It just automates the process of testing a parameter for SQL injection and even automates the process of exploitation of the vulnerable parameter. It is a great tool as it detects the database on its own so we just have to provide a URL to check whether the parameter in the URL is vulnerable or not, we could even use the requested file to check for POST parameters.
To use sqlmap tool:
- sqlmap comes pre-installed in Kali Linux
- Just type sqlmap in the terminal to use the tool.
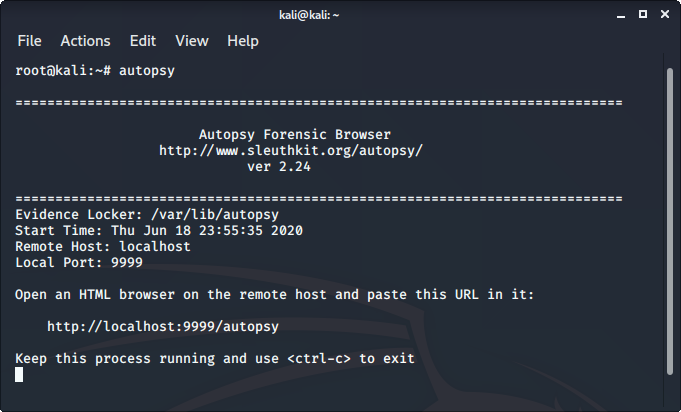
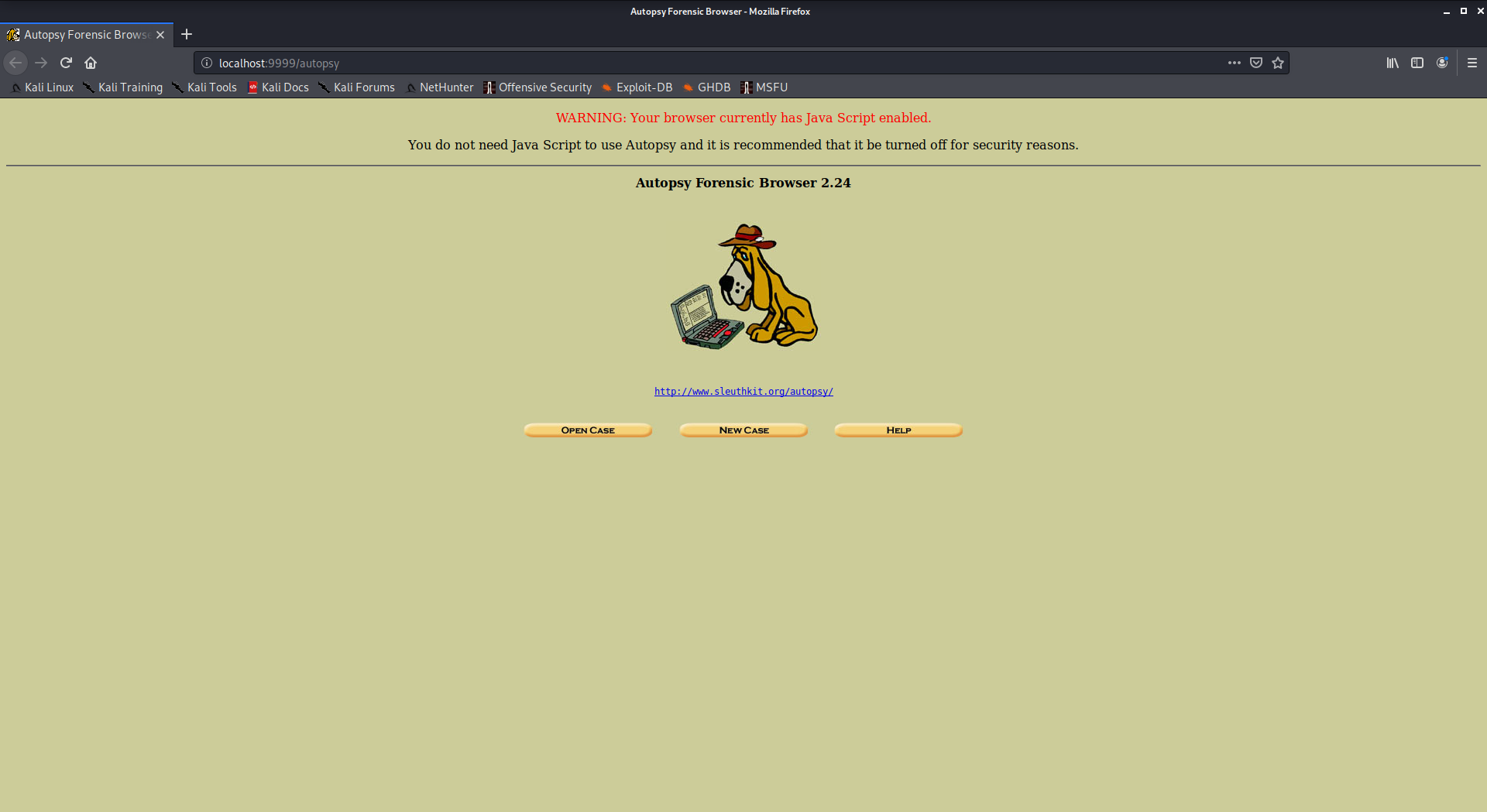
9. Autopsy
Autopsy is a digital forensics tool that is used to gather the information form forensics. Or in other words, this tool is used to investigate files or logs to learn about what exactly was done with the system. It could even be used as a recovery software to recover files from a memory card or a pen drive.
To use autopsy tool:
- Autopsy comes pre-installed in Kali Linux
- Just type “autopsy” in the terminal.
- Now visit http://localhost:9999/autopsy in order to use the tool.
10. Social Engineering Toolkit
Social Engineering Toolkit is a collection of tools that could be used to perform social engineering attacks. These tools use and manipulate human behavior for information gathering. it is a great tool to phish the websites even.
To use Social Engineering Toolkit
- Social Engineering Toolkit comes pre-installed with Kali Linux
- Just type “setoolkit” in the terminal.
- Agree to the terms and conditions to start using the social engineering toolkit.
Источник