- Инструменты Kali Linux
- Список инструментов для тестирования на проникновение и их описание
- PhoneInfoga
- Описание PhoneInfoga
- Справка по PhoneInfoga
- Руководство по PhoneInfoga
- Примеры запуска PhoneInfoga
- Установка PhoneInfoga
- Установка в Kali Linux
- Установка в BlackArch
- Ethical hacking and penetration testing
- InfoSec, IT, Kali Linux, BlackArch
- How to search for information by phone number
- How to install PhoneInfoga on Kali Linux
- Dealing with Google captcha
- How to get CX id
- Getting CSE API key
- Formatting phone numbers
- Custom formatting
- How to use PhoneInfoga
- Checking multiple numbers and saving the results to a file
- Footprinting Search
- Custom format reconnaissance
- Resources
- Footprinting
- Scylla – Phone Number & User Information Gathering Tool in Kali Linux
- Step-By-Step Installation of Scylla Tool
- Working with scylla
Инструменты Kali Linux
Список инструментов для тестирования на проникновение и их описание
PhoneInfoga
Описание PhoneInfoga
PhoneInfoga — это один из самых продвинутых инструментов для сканирвоания телефонных номеров используя только бесплатные источники. Цель состоит в том, чтобы сначала собрать с очень хорошей точностью стандартную информацию, такую как страна, регион, оператор и тип линии о любых телефонных номерах в международном формате. Затем выполнить поиск следов в поисковых системах, чтобы попытаться найти поставщика VoIP или определить владельца.
- Проверяет, существует ли номер телефона и возможен ли
- Собирает стандартную информацию, такую как страна, тип линии и носитель
- Выполняет разведку на основе открытых данных (OSINT) с использованием внешних API, Google Hacking, телефонных книг и поисковых систем
- Проверяет о репутации, социальные сети, одноразовые номера и многое другое
- Может сканировать нескольких номеров одновременно
- Использует настраиваемое форматирование для более эффективной разведки OSINT
- Автоматическое следование по нескольким пользовательским форматам
Справка по PhoneInfoga
Руководство по PhoneInfoga
Страница man отсутствует.
Примеры запуска PhoneInfoga
Запуск сбора информации по открытым источником о телефонном номере +74922778133:
Установка PhoneInfoga
Установка в Kali Linux
Затем скачайте исходный код и установите зависимости PhoneInfoga:
Установка в BlackArch
Информация об установке в другие операционные системы будет добавлена позже.
Источник
Ethical hacking and penetration testing
InfoSec, IT, Kali Linux, BlackArch
How to search for information by phone number
PhoneInfoga is one of the most advanced tools to scan phone numbers using only free resources. The goal is to first gather standard information such as country, area, carrier and line type on any international phone numbers with a very good accuracy. Then search for footprints on search engines to try to find the VoIP provider or identify the owner.
PhoneInfoga features are as follows:
- Check if phone number exists and is possible
- Gather standard informations such as country, line type and carrier
- OSINT footprinting using external APIs, Google Hacking, phone books & search engines
- Check for reputation reports, social media, disposable numbers and more
- Scan several numbers at once
- Use custom formatting for more effective OSINT reconnaissance
- Automatic footprinting on several custom formats
How to install PhoneInfoga on Kali Linux
The program uses Geckodriver, so start by installing Geckodriver with the following commands:
Then download the source code and install the PhoneInfoga dependencies:
Dealing with Google captcha
During its searches, the program actively googles. Therefore, Google begins to show the captcha. At this time, the program is displayed
If you check 1-2 phone numbers, then this will not be a problem for you. If you check a lot of numbers, solving the captcha becomes tedious.
We need to get 2 identifiers. One of them is called CX id, and the second is called the CSE API key. If you do not want to do this, you can skip this section (proceed to the next header) – you can use PhoneInfoga without these keys.
Let’s consider getting the keys to search on Google using the API.
How to get CX id
Go to https://cse.google.com/cse/create/new to create a new search engine
Fill the form with a fake domain site like example.com
Select English as language
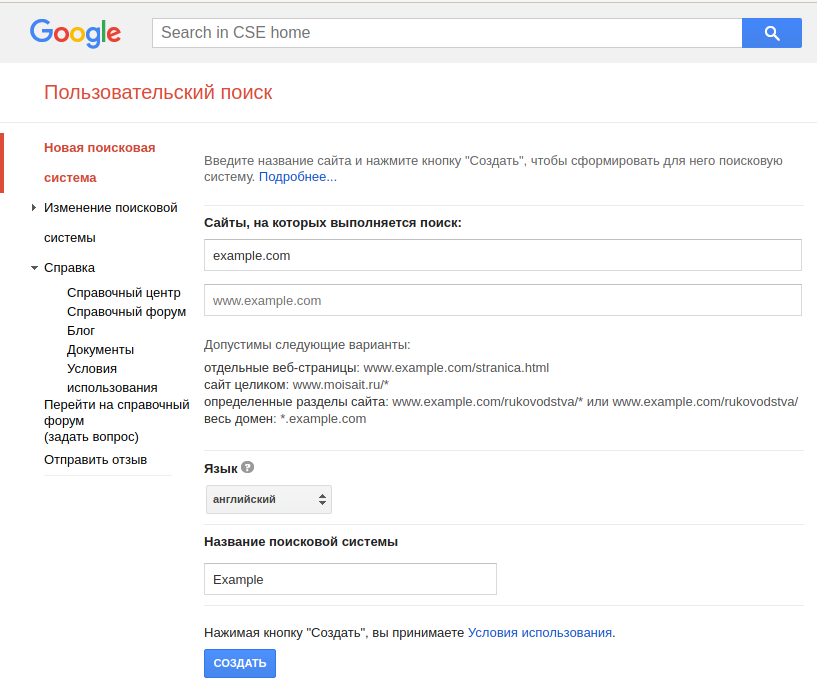
Give any name to your search engine and click on Create button
Go to https://cse.google.com/cse/all again and click on the search engine you just created.
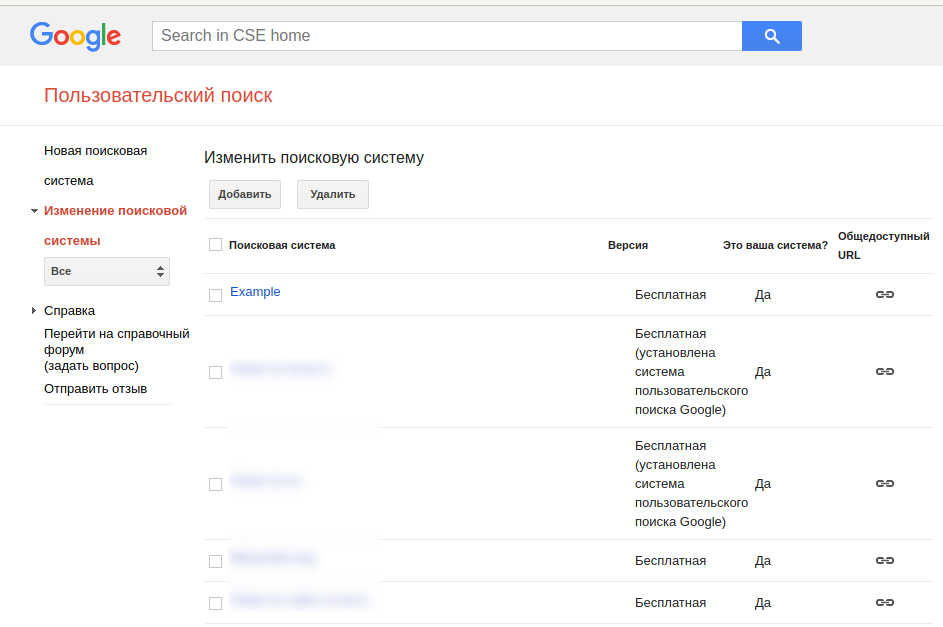
Select all entries in «Sites to search» and delete them
Turn «Search the entire web» to ON
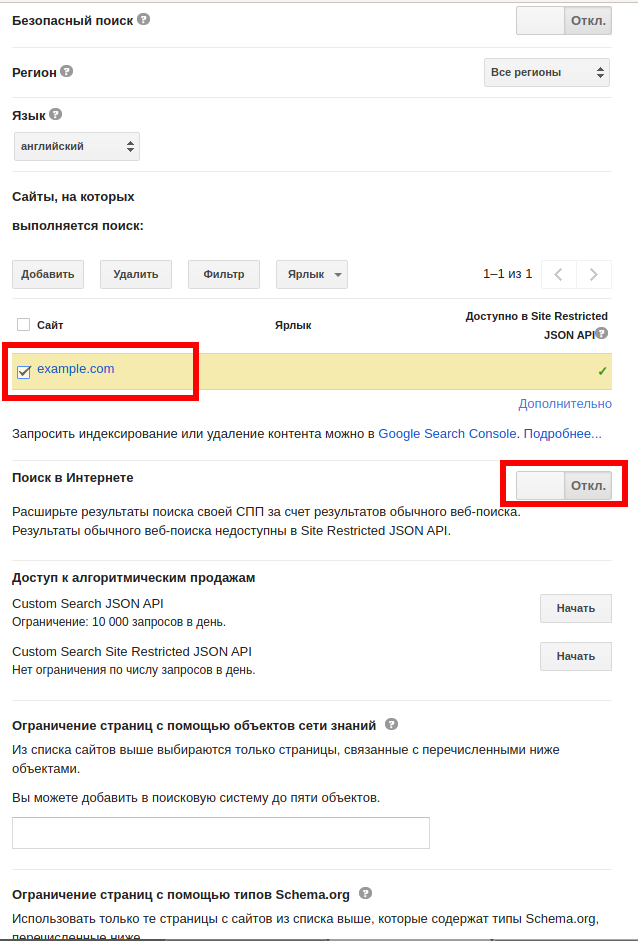
Click on the «Search engine ID» button and copy your search engine id. This is the value for google_cx_id field in config.py file.

Getting CSE API key
Click on “Create Credentials” and select “API Key”:

It will also need to be enabled:

Now in the PhoneInfoga folder open the config.py file:
And copy both keys there.
Formatting phone numbers
The tool only accepts E164 and International formats as input.
- E164: +3396360XXXX
- International: +33 9 63 60 XX XX
- National: 09 63 60 XX XX
- RFC3966: tel:+33-9-63-60-XX-XX
- Out-of-country format from US: 011 33 9 63 60 XX XX
E.164 formatting for phone numbers entails the following:
- A + (plus) sign
- International Country Calling code
- Local Area code
- Local Phone number
For example, here’s a US-based number in standard local formatting: (415) 555-2671

Here’s the same phone number in E.164 formatting: +14155552671

In the UK, and many other countries internationally, local dialing may require the addition of a ‘0’ in front of the subscriber number. With E.164 formatting, this ‘0’ must usually be removed.
For example, here’s a UK-based number in standard local formatting: 020 7183 8750
Here’s the same phone number in E.164 formatting: +442071838750
Custom formatting
Sometimes the phone number has footprints but is used with a different formatting. This is a problem because for example if we search for «+15417543010», we’ll not find web pages that write it that way : «(541) 754–3010». So the tool use a (optional) custom formatting given by the user to find further and more accurate results. To use this feature properly and make the results more valuable, try to use a format that someone of the number’ country would usually use to share the phone number online.
For example, French people usually write numbers that way online : 06.20.30.40.50 or 06 20 30 40 50.
For US-based numbers, the most common format is : 543-456-1234.
Here are some examples of custom formatting for US-based phone numbers :
- +1 618-555-xxxx
- (+1)618-555-xxxx
- +1/618-555-xxxx
- (618) 555xxxx
- (618) 555-xxxx
- (618) 555.xxxx
- (618)555xxxx
- (618)555-xxxx
- (618)555.xxxx
For European countries (France as example) :
- +3301 86 48 xx xx
- +33018648xxxx
- +33018 648 xxx x
- (0033)018648xxxx
- (+33)018 648 xxx x
- +33/018648xxxx
- (0033)018 648 xxx x
- +33018-648-xxx-x
- (+33)018648xxxx
- (+33)01 86 48 xx xx
- +33/018-648-xxx-x
- +33/01-86-48-xx-xx
- +3301-86-48-xx-xx
- (0033)01 86 48 xx xx
- +33/01 86 48 xx xx
- (+33)018-648-xxx-x
- (+33)01-86-48-xx-xx
- (0033)01-86-48-xx-xx
- (0033)018-648-xxx-x
- +33/018 648 xxx x
How to use PhoneInfoga
So, we got to know that you need to use the E164 format, which is nothing more than a phone number in which “8” is replaced by “+7”, and also all spaces, hyphens, brackets and any other characters except numbers are removed. Example number in this format: +74959999999
To search by phone number, use the -n option, after which you need to specify the number in the international format:
The data sources in PhoneInfoga are divided into groups called “scanners”. It is not possible to search using a specific scanner. To do this, specify its name after the -s option.
If not specified, then the default value is all, that is, all scanners.
- numverify
- ovh
- footprints
numverify provides standard but useful information such as country code, location, line type, and carrier.

The ovh scanner uses the OVH Telecom API to determine if this company has a VoIP number.
The footprints scanner uses the Google search engine and Google dorks to search for phone numbers across the Internet. This allows you to search for fraud reports, social media profiles, documents and more.

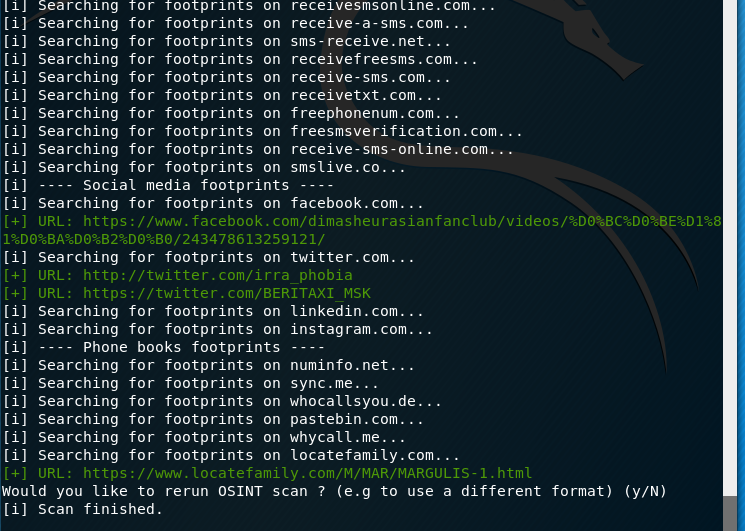
Sometimes the program asks questions:
- Would you like to use an additional format for this number? (y/n)
- Would you like to search for temporary number providers footprints? (Y/n)
- Would you like to rerun OSINT scan? (e.g. to use a different format) (y / N)
Checking multiple numbers and saving the results to a file
The program supports checking multiple numbers. They need to be saved to a file – one number per line and specify the path to this file after the -i option. To save the results to a file, specify the file name after the -o option. To disable color, use the —no-ansi flag:
The input file must contain one phone number per line. Invalid numbers will be skipped.
Footprinting Search
If you are not interested in information about the country, the carrier and other similar data, then with the -s option you can only enable footprints scan:
Custom format reconnaissance
You do not know where to look and what user format to use? Let the tool try several custom formats based on your country code.
Resources
Footprinting
Both free and premium resources are included. Be careful, the listing of a data source here does not mean it has been verified or is used in the tool. Data might be false. Use it as an OSINT framework.
Источник
Scylla – Phone Number & User Information Gathering Tool in Kali Linux
Scylla is a free and open-source tool available on Github. Scylla is based upon the concept of Open Source Intelligence (OSINT). This tool is used for information gathering. Scylla is written in python language. You must have python language installed in your Kali Linux in order to use the Scylla tool. Scylla is an advanced tool that allows it’s used to perform advanced information gathering. Scylla is also called The Information Gathering Engine. Scylla is used to find all social media accounts of a person who is assigned to a particular username. Scylla is used to find account information of the account of Instagram. Twitter accounts, websites/web servers, phone numbers, and names.
Scylla has a drastic support IoT search engine Shodan. This search engine lets you know about devices all over the internet. Scylla also has in-depth geolocation capabilities which makes it more powerful. Scylla has financial modules which allow the user to check whether their credit/debit card details have been leaked or not in a pasted data breach of companies. This tool makes it easy to search for a person on social media platform by just knowing his/her number or username. You have to give your username to Scylla and this tool will give you all the social media accounts information of the target.
Features of Scylla:
- Scylla is a free tool You can download and use it free of cost.
- Scylla is open source tool. Scylla’s source code is available on GitHub you can check it and contribute to it.
- Scylla works on the concept of Open Source Intelligence (OSINT).
- Scylla is used for information gathering.
- Scylla is an advanced tool used for advance searching on the internet.
- Scylla is written in python language. You must have python language installed into your Kali Linux operating system in order to use Scylla.
- Scylla is also called an information gathering Engine.
Uses of Scylla:
Step-By-Step Installation of Scylla Tool
Step 1: Open your Kali Linux operating system. Move to desktop. Here you have to create a directory called Scylla. To move to desktop use the following command.
Step 2: Now you are on the desktop. Here you have to create a directory Scylla. To create the Scylla directory using the following command.
Step 3: You have created a directory. Now use the following command to move into that directory.
Step 4: Now you are in Scylla directory. Now you have to install the tool using the following command.
Step 5: You have downloaded the tool use the following command to list out the contents of the tool.
Step 6: In order to use scylla we will have to move to the scylla directory. Use the following command to move in this directory.
Step 7: Now you are in the directory called scylla. Use the following command to list out the contents of the directory.
Step 8: You can see many files in this directory. These are the files of the tool. Now you have to install the requirements of the tool. Use the following command to install requirements.
Step 9: All the requirements have been installed. Now you have to run the tool using the following command.
Step 10: The tool is running finally. To get the help of the tool uses the following command.
Working with scylla
1. Use the Scylla tool to get information about Instagram account of a user.
This command is used to target Instagram accounts of users.
2. Use the Scylla tool to get information about the social media accounts of a user.
3. Use the Scylla tool to get information about the phone numbers.
4. Use the Scylla tool to get information about geolocation of an IP-address.
Источник
















