- Kali linux xfce 64 bit
- Where to Get Official Kali Linux Images
- Verifying Your Downloaded Kali Image
- How Do I Verify My Downloaded Image?
- Kali Linux 2021.1 Release (Command-Not-Found)
- Xfce & KDE Updates
- Terminals Tweaks
- Finding Commands That Didn’t Want To Be Found
- Partnerships with Tools Authors
- New Tools in Kali
- Kali’s Website
- Wallpapers
- Kali NetHunter Updates
- Kali ARM Updates
- Download Kali Linux 2021.1
Kali linux xfce 64 bit
IMPORTANT! Never download Kali Linux images from anywhere other than the official sources.
Always be sure to verify the SHA256 checksums of the file you’ve downloaded against our official values.
It would be easy for a malicious entity to modify a Kali installation to contain exploits or malware and host it unofficially.
Where to Get Official Kali Linux Images
ISO Files for Intel-based PCs
In order to run Kali “Live” from a USB drive on standard Windows and Apple PCs, you’ll need a Kali Linux bootable ISO image, in either 32-bit or 64-bit format.
If you’re not sure of the architecture of the system you want to run Kali on, on Linux or macOS, you can run the command uname -m at the command line. If you get the response, “x86_64”, use the 64-bit ISO image (the one containing “amd64” in the file name); if you get “i386”, use the 32-bit image (the one containing “i386” in the file name). If you’re on a Windows system, the procedure for determining whether your architecture is detailed on Microsoft’s website.
The Kali Linux images are available both as directly downloadable “.iso/.img” files or via “.torrent” files.
Building your own Kali Linux ISO, standard or customized, is a very simple process.
Virtual Machines Images
If you want to run Kali Linux as a “guest” under VMware or VirtualBox, Kali Linux is available as a pre-built virtual machines with any guest tools already installed. These image are available in a 64-bit (amd64), and 32-bit PAE (i*86) formats.
ARM Images
The hardware architectures of ARM-based devices vary considerably, so it is not possible to have a single image that will work across all of them. Pre-built Kali Linux images for the ARM architecture are available for a wide range of devices.
Scripts for building your own ARM images locally are also available on GitLab. For more details, see the articles on setting up an ARM cross-compilation environment and building a custom Kali Linux ARM chroot.
Verifying Your Downloaded Kali Image
Why do I need to do this?
Before you run Kali Linux Live, or install it to your hard disk, you want to be very sure that what you’ve got actually is Kali Linux, and not an imposter. Kali Linux is a professional penetration testing and forensics toolkit. As a professional penetration tester, having absolute confidence in the integrity of your tools is critical: if your tools are not trustworthy, your investigations will not be trustworthy, either.
Moreover, as the leading penetration testing distribution, Kali’s strengths mean that a bogus version of Kali Linux could do a tremendous amount of damage if it were deployed unwittingly. There are plenty of people with plenty of reason to want to stick very sketchy stuff into something that looks like Kali, and you absolutely do not want to find yourself running something like that.
Avoiding this is simple:
- Only download Kali Linux via the official download pages at kali.org/downloads/ or offensive-security.com/kali-linux-vmware-arm-image-download/ — you will not be able to browse to these pages without SSL; encrypting the connection makes it much harder for an attacker to use a “man-in-the-middle” attack to modify your download. There are a few potential weaknesses to even these sources — see the sections on verifying the download with the SHA256SUMS file and its signature against the official Kali Development team private key for something much closer to absolute assurance.
- Once you’ve downloaded an image, and before you run it, always validate that it really is what it’s supposed to be by verifying its checksum using one of the procedures detailed below.
There are several methods for verifying your download. Each provides a certain level of assurance, and involves a corresponding level of effort on your part.
- You can download an ISO image from an official Kali Linux “Downloads” mirror, calculate the ISO’s SHA256 hash and compare it by inspection with the value listed on the Kali Linux site. This is quick and easy, but potentially susceptible to subversion via a DNS poisoning: it assumes that the site to which, for example, the domain “kali.org” resolves is in fact the actual Kali Linux site. If it somehow were not, an attacker could present a “loaded” image and a matching SHA256 signature on the fake web page. See the section “Manually Verify the Signature on the ISO (Direct Download)”, below.
- You can download an ISO image through the torrents, and it will also pull down a file — unsigned — containing the calculated SHA256 signature. You can then use the shasum command (on Linux and macOS) or a utility (on Windows) to automatically verify that the file’s computed signature matches the signature in the secondary file. This is even easier than the “manual” method, but suffers from the same weakness: if the torrent you pulled down is not really Kali Linux, it could still have a good signature. See the section “Verify the Signature on the ISO Using the Included Signature File (Torrent Download)”, below.
- To be as close to absolutely certain as possible that the Kali Linux download you’ve obtained is the real thing, you can download both a cleartext signature file and and version of the same file that has been signed with the official Kali Linux private key and use GNU Privacy Guard (GPG) to first, verify that the computed SHA256 signature and the signature in the cleartext file match and second, verify that the signed version of the file containing the SHA256 hash has been correctly signed with the official key.
If you use this more complicated process and successfully validate your downloaded ISO, you can proceed with pretty complete assurance that what you’ve got is the official image and that it has not been tampered with in any way. This method, while the most complex, has the advantage of providing independent assurance of the integrity of the image. The only way this method can fail is if the official Kali Linux private key is not only subverted by an attacker, but also not subsequently revoked by the Kali Linux development team. For this method, see the section on verification using the SHA256SUMS file.
What do I need to do this?
If you’re running on Linux, you probably already have GPG (GNU Privacy Guard) installed. If you’re on Windows or macOS, you’ll need to install the appropriate version for your platform.
- If you’re on a PC running Windows, download and install GPG4Win from here. Certain versions of Windows do not have the native ability to calculate SHA256 checksums. To check this, you can open the command prompt and run certutil -? . If you do have this installed, you can run certutil -hashfile kali-linux-2021.3-live-amd64.iso sha256 to verify your download. If you do not have certutil installed, you will also need a utility such as Microsoft File Checksum Integrity Verifier or Hashtab to verify your download.
- If you’re on a Macintosh running macOS, download and install GPGTools from here. Alternatively, if you have Homebrew installed, just run brew install gnupg
Once you’ve installed GPG, you’ll need to download and import a copy of the Kali Linux official key. Do this with the following command:
Your output should look like this:
Verify that the key is properly installed with the command:
The output will look like this:
You’re now set up to validate your Kali Linux download.
How Do I Verify My Downloaded Image?
Manually Verify the Signature on the ISO (Direct Download)
If you downloaded the ISO directly from the downloads page, verify it using the following procedure.
On Linux, or macOS, you can generate the SHA256 checksum from the ISO image you’ve downloaded with the following command (assuming that the ISO image is named “kali-linux-2021.3-live-amd64.iso”, and is in your current directory):
The output should look like this:
The resulting SHA256 signature, “e316b27025922e9f6bca0cacee6dde83dbfd4a549ad18026526f5824af639fc1”, can be seen to match the signature displayed in the “sha256sum” column on the official download page for the 64-bit Intel architecture Kali Linux 2021.3 ISO image:
Verify the Signature on the ISO Using the Included Signature File (Torrent Download)
If you downloaded your copy of the Kali Linux ISO image via the torrents, in addition to the ISO file (e.g. kali-linux-2021.3-live-amd64.iso), there will be a second file containing the computed SHA256 signature for the ISO, with the extension “.txt.sha256sum” (e.g. kali-linux-2021.3-live-amd64.txt.sha256sum). You can use this file to verify the authenticity of your download on Linux or macOS with the following command:
If the image is successfully authenticated, the response will look like this:
IMPORTANT! If you are unable to verify the authenticity of the Kali Linux image you have downloaded as described in the preceding section, do NOT use it! Using it could endanger not only your own system, but any network you connect to as well as the other systems on that network. Stop, and ensure that you have downloaded the images from a legitimate Kali Linux mirror.
Verify the ISO Using the SHA256SUMS File
This is a more complex procedure, but offers a much higher level of validation: it does not rely on the integrity of the web site you downloaded the image from, only the official Kali Linux development team key that you install independently. To verify your image this way for an Intel architecture version of Kali, you will need to download three files from the Kali “Live CD Image” site for the current release (v2021.3, as of this writing):
- The ISO image itself (e.g. kali-linux-2021.3-live-amd64.iso)
- The file containing the calculated SHA256 hash for the ISO, SHA256SUMS
- The signed version of that file, SHA256SUMS.gpg
Before verifying the checksums of the image, you must ensure that the SHA256SUMS file is the one generated by Kali Linux. That’s why the file is signed by Kali’s official key with a detached signature in SHA256SUMS.gpg. If you have not already done so, Kali’s official key can be downloaded and imported into your keychain with this command:
or this command
Your output should look like this:
You should verify that the key is properly installed with the command:
The output will look like this:
Once you have downloaded both SHA256SUMS and SHA256SUMS.gpg, you can verify the signature as follows:
If you do not get that “Good signature” message or if the key ID does not match, then you should stop and review whether you downloaded the images from a legitimate Kali Linux mirror. The failed verification strongly suggests that the image you have may have been tampered with.
If you did get the “Good signature” response, you can now be assured that the checksum in the SHA256SUMS file was actually provided by the Kali Linux development team. All that remains to be done to complete the verification is to validate that the signature you compute from the ISO you’ve downloaded matches the one in the SHA256SUMS file. You can do that on Linux or macOS with the following command (assuming that the ISO is named “kali-linux-2021.3-live-amd64.iso” and is in your working directory):
If the image is successfully authenticated, the response will look like this:
If you do not get “OK” in response, then stop and review what’s happened: the Kali image you have has apparently been tampered with. Do NOT use it.
Once you’ve downloaded and verified your image, you can proceed to create a bootable “Kali Linux Live” USB drive.
Updated on: 2021-Sep-27
Authors: g0tmi1k , gamb1t
Источник
Kali Linux 2021.1 Release (Command-Not-Found)
Today we’re pushing out the first Kali Linux release of the year with Kali Linux 2021.1. This edition brings enhancements of existing features, and is ready to be downloaded or upgraded if you have an existing Kali Linux installation.
- Xfce 4.16 — Our preferred and current default desktop environment has been updated and tweaked
- KDE 5.20 — Plasma also received a version bump
- Terminals — mate-terminal , terminator and tilix all had various work carried out on them
- Command Not Found — A helping hand to say if a program needs to be installed
- Partnership with more tool authors — BC Security & Joohoi have been producing great tools and we want to support them
- New tools & updates — Multiple new tools have been added to Kali and are ready for you
- Kali NetHunter — New BusyBox & Rucky version, and boot-animation
- Kali ARM — Preliminary support for Parallels on Apple Silicon (Apple M1) & Raspberry Pi 400 (WiFi Support)
The Kali project itself also has a couple different changes:
- New Kali website — You may have noticed a few things looking different
- Kali newsletter — Rather than you coming to us for updates, we can push them to your inbox
Xfce & KDE Updates
How you choose to interact with Kali is completely up to you. You may want to access Kali locally or remotely, either graphically or on the command line. Even when you pick a method, there are still options you can choose from, such as a desktop environment.
By default, Kali uses Xfce, but during the setup process, allows for GNOME, KDE, or no GUI to be selected. After the setup is complete, you can install even more. We have pre-configurations for Enlightenment, i3, LXDE, and MATE as well.
So when a desktop environment gets an update, they often enhance day-to-day activities for their users. It’s best to hear it straight from the authors, for a tour of what’s changed:
Below is our tweaked GTK3 theme, on Xfce:
Terminals Tweaks
When we use Kali, we spend a significant amount of time using the command line. A lot of the time, we do it using a local terminal (rather than in a console or remote SSH). With the options of desktop environments, there are also choices when it comes to the terminals (same with what shell to use). We have been working away on various terminals ( xfce4-terminal , tmux , tilix , konsole , qterminal , and mate-terminal ) to “Kali-fy” them:
Finding Commands That Didn’t Want To Be Found
A while ago, we changed the default set of tools installed in Kali. Most users know they can either install a one-off package, or revert back to the old set of defaults ( apt install kali-linux-large ). But to help communicate our changes (as well as any new tools), we have now included command-not-found by default. This is an “optional” package, which can be removed without removing all of kali-linux-default .
Without command-not-found installed:
If you are wondering “How does this help me?”, or has the above ever happened to you, we like to think people’s next stage would be to do apt-cache search gitleaks and see it in the network repositories. But we can do better. Now with command-not-found :
As you can see from the above example:
- gitleaks — If the command you entered is the name of an executable available in Kali, it will say the package that you need to install (if its not already!)
- gitleakss — If you are “fat fingered” and make a typo, it may make a suggestion
- badcmd — If you typed in an invalid command that doesn’t exist in Kali, it will give the original message of “command not found”.
So, how can I get this magic? Good question! If you’re:
- Doing a fresh install of Kali Linux 2021.1 or later, it will “just happen” during the setup.
- Updating Kali and you are using a Bash shell, then it will “just happen” too.
- Updating Kali and you are using a Zsh shell, you will need to add the following lines to your
But it doesn’t have to end here. By adding COMMAND_NOT_FOUND_INSTALL_PROMPT=1 to your shell’s environment (e.g.
/.zshrc ), command-not-found will take it one step further, and also prompt you if you want to install the missing package. This change is something we will be putting in in a future release.
Partnerships with Tools Authors
Carrying on from our previous partnership with byt3bl33d3r, we have expanded to supporting:
- BC Security — Giving Kali exclusive early access to “Empire” ( powershell-empire ) & “StarKiller”
- Joohoi — The creator of “Fuzz Faster U Fool (ffuf)”
The announcement with Joohoi is new for Kali 2021.1. Like the previous sponsorships, you can either sponsor him directly to get the latest access to ffuf, use Kali Linux, or wait 30 days until the source code becomes public. However, he has also announced anyone who makes a significant contribution, which gets accepted into the project, also gets access!
New Tools in Kali
It wouldn’t be a Kali release if there weren’t any new tools added! A quick run down of what’s been added (to the network repositories):
- Airgeddon — Audit wireless networks
- AltDNS — Generates permutations, alterations and mutations of subdomains and then resolves them
- Arjun — HTTP parameter discovery suite
- Chisel — A fast TCP/UDP tunnel over HTTP
- DNSGen — Generates combination of domain names from the provided input
- DumpsterDiver — Search secrets in various filetypes
- GetAllUrls — Fetch known URLs from AlienVault’s Open Threat Exchange, the Wayback Machine, and Common Crawl
- GitLeaks — Searches Git repo’s history for secrets and keys
- HTTProbe — Take a list of domains and probe for working HTTP and HTTPS servers
- MassDNS — A high-performance DNS stub resolver for bulk lookups and reconnaissance
- PSKracker — WPA/WPS toolkit for generating default keys/pins
- WordlistRaider — Preparing existing wordlists
Kali’s Website
Until recently, the only way you could be reading this would have been from our RSS feed or directly from our blog (as we only recently made the announcement of the Kali Newletter). You may of noticed already, and we said that it was coming, and it finally has — kali.org has had a face-lift!
We have (finally) moved away from WordPress to Hugo. Similarly to Kali, the website will also be a rolling distribution. The recent change is mostly cosmetic and content (both were long overdue), and we have made plans for new features to be added.
Another upside of the switch is that we can take more advantage of what GitLab has to offer. We recently had an interview with GitLab about the switch.
On the subject of interviews, we also had a word with Mr Robot’s ARG Society if you missed that.
Wallpapers
Just a quick little thing, we have tweaked our wallpaper packages:
- kali-wallpapers-2020.4 — Kali’s wallpapers from 2020.4 and onwards (for the time being)
- kali-wallpapers-2019.4 — Kali’s wallpapers between 2019.4 and 2020.3.
- kali-wallpapers-legacy — BackTrack & Kali nostalgic backgrounds
- kali-wallpapers-all — Every wallpaper
- kali-community-wallpapers — created and submitted by the community (submit yours today!)
With the alterations to the packages, we have taken the time to improve support for Xfce when using them.
Kali NetHunter Updates
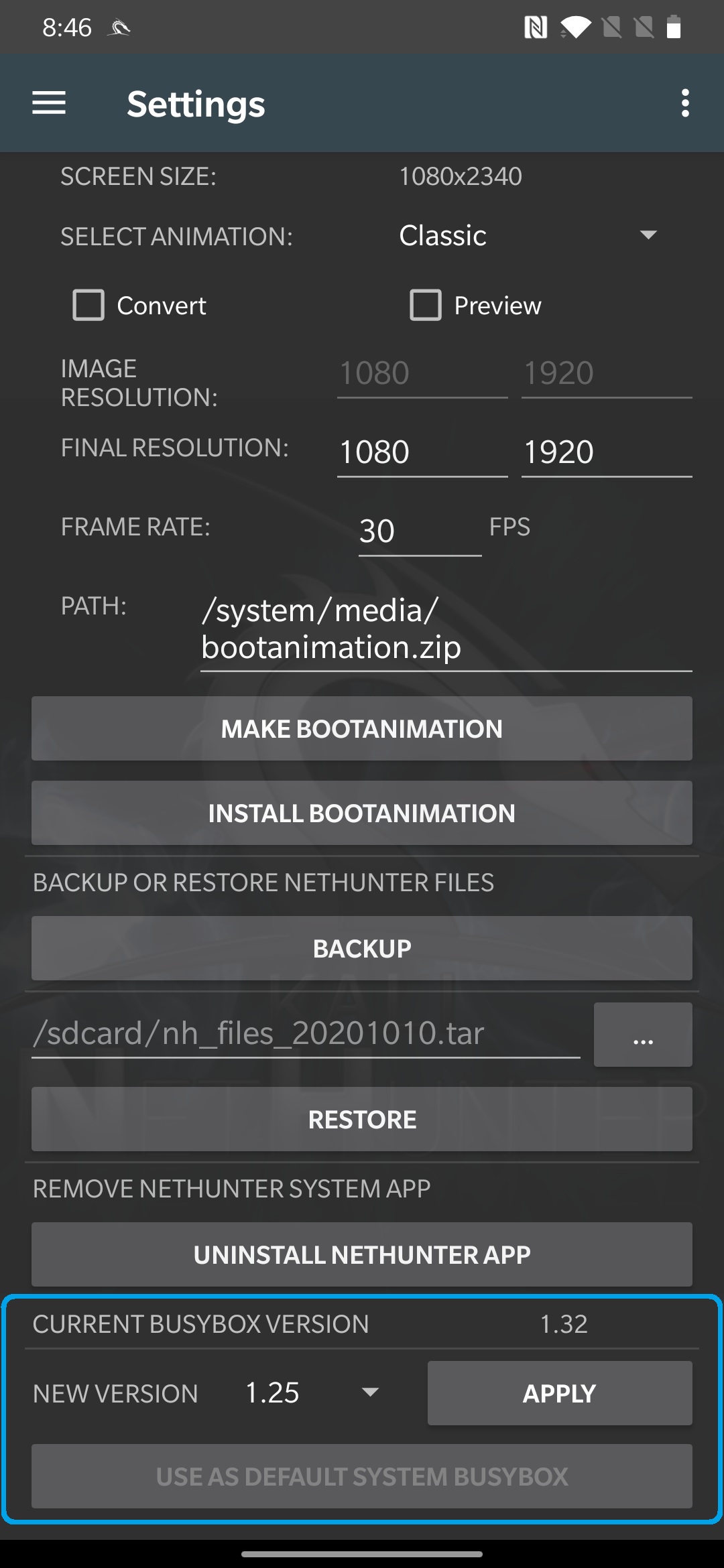
BusyBox, one of the core engines of Kali NetHunter, has received a well deserved upgrade to version “1.32.0-nethunter”. BusyBox is used internally to ensure that NetHunter tools and commands are executed consistently across the vast number of different Android versions and vendor modifications. This change, whilst big, should go unnoticed by users and will help developers to port their code to NetHunter with no hassles at all. @yesimxev has added a handy section to the settings menu, which allows developers to select different BusyBox versions for testing:
Speaking of developers: If you have any cool ideas you’d like to see included in Kali NetHunter or if you would like to contribute to this amazing project, please reach out to us in our forums or on GitLab. We would love to hear from you!
Tools have been updated to the latest versions, notably Rucky — the “modern looking USB Rubber Ducky Editor and Attack Launcher”, which has been completely re-written by its author @mayankmetha and released in the Kali NetHunter App Store as version 2.1.
We’ve also been busy working on the visual aspects of Kali NetHunter, with @s133py adding a stunning new boot-animation to the growing selection:
If you have a cool boot-animation you’d like to share, please submit a merge request to our Kali NetHunter boot-animation repository.
Kali ARM Updates
As you may have heard, Apple have released new Macs with their own processors, known as Apple Silicon (Apple M1). So far, only Parallels have released something publicly that people can use for virtualization. To that end, we have generated both an installer & live ISOs ( kali-linux-2021.1-installer-arm64.iso and kali-linux-2021.1-live-arm64.iso ) that can be used with VMs on Apple Silicon Macs. Many thanks to the people who reached out and offered to test and helped us to iron out the bugs. If you’d like to see it in action, David Bombal has put out a video of it.
We have also added support for the Raspberry Pi 400’s wireless card, however it is very important to note that this is not a nexmon firmware, as nexmon does not currently support it.
The Kali ARM build scripts have seen a few more improvements from Francisco Jose Rodriguez Martos and we appreciate the assistance greatly. If you’d like to get involved with ARM, check out the GitLab issue list.
Download Kali Linux 2021.1
Fresh Images: So what are you waiting for? Start downloading already!
Seasoned Kali Linux users are already aware of this, but for the ones who are not, we do also produce weekly builds that you can use as well. If you cannot wait for our next release and you want the latest packages (or bug fixes) when you download the image, you can just use the weekly image instead. This way you’ll have fewer updates to do. Just know that these are automated builds that we do not QA like we do our standard release images. But we gladly take bug reports about those images because we want any issues to be fixed before our next release!
Existing Installs: If you already have an existing Kali Linux installation, remember you can always do a quick update:
You should now be on Kali Linux 2021.1. We can do a quick check by doing:
NOTE: The output of uname -r may be different depending on the system architecture.
As always, should you come across any bugs in Kali, please submit a report on our bug tracker. We’ll never be able to fix what we do not know is broken! And Twitter is not a Bug Tracker!
Источник