- Windows 10 update history
- Updates for Windows 10, version 1903 and Windows Server, version 1903
- Current status of Windows 10, version 1903 and Windows Server, version 1903
- Notes and messages
- General
- End of servicing
- Troubleshooting
- How does Windows Update work?
- Download
- Install
- Commit
- How updating works
- Scanning updates
- How Windows Update scanning works
- Starts the scan for updates
- Identifies service IDs
- Finds network faults
- Downloading updates
- Installing updates
- Committing Updates
- How does Windows Update work?
- Download
- Install
- Commit
- How updating works
- Scanning updates
- How Windows Update scanning works
- Starts the scan for updates
- Identifies service IDs
- Finds network faults
- Downloading updates
- Installing updates
- Committing Updates
Windows 10 update history
Windows 10, version 1903 and Windows Server, version 1903
Updates for Windows 10, version 1903 and Windows Server, version 1903
Windows 10 is a service, which means it gets better through periodic software updates.
The great news is you usually don’t have to do anything! If you have enabled automatic updates, new updates will automatically download and install whenever they’re available, so you don’t have to think about it.
On the left side of this page, you’ll find a list of all the updates released for this version of Windows. You can also find more information about releases and any known issues. Installing the most recent update ensures that you also get any previous updates you might have missed, including any important security fixes.
Current status of Windows 10, version 1903 and Windows Server, version 1903
For the most up-to-date information about Known Issues for Windows and Windows Server, please go to the Windows release health dashboard.
Notes and messages
General
IMPORTANT Release notes are changing! To learn about the new URL, metadata updates, and more, see What’s next for Windows release notes.
IMPORTANT Starting in July 2020, we will resume non-security releases for Windows 10 and Windows Server, version 1809 and later. There is no change to the cumulative monthly security updates (also referred to as the «B» release or Update Tuesday release). For more information, see the blog post Resuming optional Windows 10 and Windows Server non-security monthly updates.
IMPORTANT Starting in July 2020, all Windows Updates will disable the RemoteFX vGPU feature because of a security vulnerability. For more information about the vulnerability, seeCVE-2020-1036 and KB4570006. After you install this update, attempts to start virtual machines (VM) that have RemoteFX vGPU enabled will fail, and messages such as the following will appear:
If you re-enable RemoteFX vGPU, a message similar to the following will appear:
“The virtual machine cannot be started because all the RemoteFX-capable GPUs are disabled in Hyper-V Manager.”
“The virtual machine cannot be started because the server has insufficient GPU resources.”
«We no longer support the RemoteFX 3D video adapter. If you are still using this adapter, you may become vulnerable to security risk. Learn more (https://go.microsoft.com/fwlink/?linkid=2131976)”
What’s new for Windows 10, version 1909 and Windows 10, version 1903 release notes
Windows 10, versions 1903 and 1909 share a common core operating system and an identical set of system files. As a result, the new features in Windows 10, version 1909 were included in the recent monthly quality update for Windows 10, version 1903 (released October 8, 2019), but are currently in a dormant state. These new features will remain dormant until they are turned on using an enablement package, which is a small, quick-to-install “master switch” that simply activates the Windows 10, version 1909 features.
To reflect this change, the release notes for Windows 10, version 1903 and Windows 10, version 1909 will share an update history page. Each release page will contain a list of addressed issues for both 1903 and 1909 versions. Note that the 1909 version will always contain the fixes for 1903; however, 1903 will not contain the fixes for 1909. This page will provide you with the build numbers for both 1909 and 1903 versions so that it will be easier for support to assist you if you encounter issues.
For more details about the enablement package and how to get the feature update, see the Windows 10, version 1909 delivery options blog.
End of servicing
IMPORTANT Windows 10, version 1903 will reach end of servicing on December 8, 2020. To continue receiving security and quality updates, Microsoft recommends that you update to the latest version of Windows 10. If you want to update to Windows 10, version 1909, you must use the Enablement Package KB4517245(EKB). Using the EKB makes updating faster and easier and requires a single restart. For more information, see Windows 10, version 1909 delivery options.
Troubleshooting
If you have questions or need help activating or troubleshooting Windows, see our help topics below:
For information about how to update, see Update Windows 10.
If you have questions about manually installing or removing an update, see Windows Update: FAQ.
Getting an error message when updating? See Troubleshoot problems updating Windows 10.
If you need to activate Windows, see Activation in Windows 10. If you’re having trouble with activation, see Get help with Windows activation errors.
To get the latest major update to Windows 10, see Get the Windows 10 October 2018 Update.
How does Windows Update work?
The Windows Update workflow has four core areas of functionality:
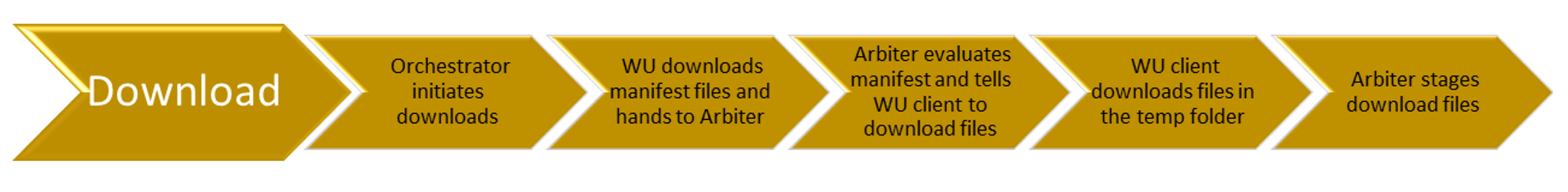
Download
Install
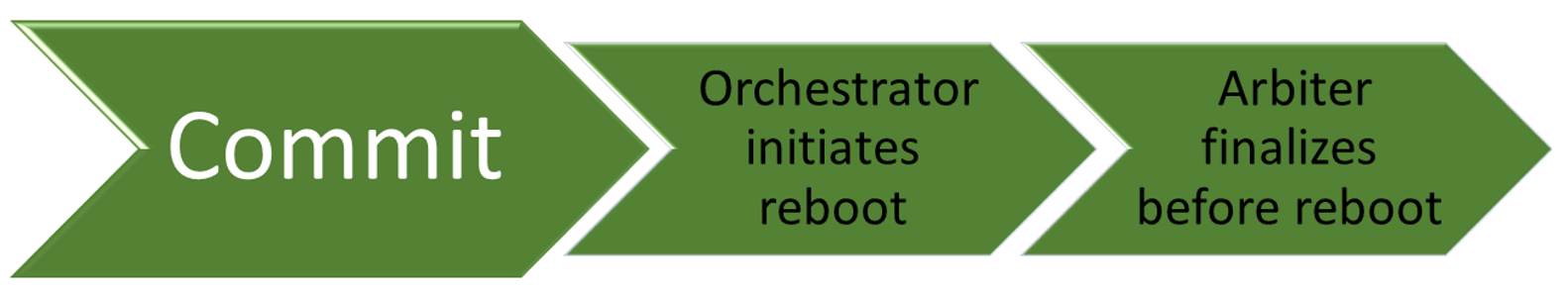
Commit
How updating works
During the updating process, the Windows Update Orchestrator operates in the background to scan, download, and install updates. It does these actions automatically, according to your settings, and silently so that doesn’t disrupt your computer usage.
Scanning updates
The Windows Update Orchestrator on your PC checks the Microsoft Update server or your WSUS endpoint for new updates at random intervals. The randomization ensures that the Windows Update server isn’t overloaded with requests all at the same time. The Update Orchestrator searches only for updates that have been added since the last time updates were searched, allowing it to find updates quickly and efficiently.
When checking for updates, the Windows Update Orchestrator evaluates whether the update is appropriate for your device. It uses guidelines defined by the publisher of the update, for example, Microsoft Office including enterprise group policies.
Make sure you’re familiar with the following terminology related to Windows Update scan:
| Term | Definition |
|---|---|
| Update | We use this term to mean several different things, but in this context it’s the actual updated code or change. |
| Bundle update | An update that contains 1-N child updates; doesn’t contain payload itself. |
| Child update | Leaf update that’s bundled by another update; contains payload. |
| Detector update | A special «update» that contains «IsInstalled» applicability rule only and no payload. Used for prereq evaluation. |
| Category update | A special «detectoid» that has an IsInstalled rule that is always true. Used for grouping updates and to allow the device to filter updates. |
| Full scan | Scan with empty datastore. |
| Delta scan | Scan with updates from previous scan already cached in datastore. |
| Online scan | Scan that uses the network and to check an update server. |
| Offline scan | Scan that doesn’t use the network and instead checks the local datastore. Only useful if online scan has been performed before. |
| CatScan | Category scan where caller can specify a categoryId to get updates published under that categoryId. |
| AppCatScan | Category scan where caller can specify an AppCategoryId to get apps published under that appCategoryId. |
| Software sync | Part of the scan that only checks for software updates (both the apps and the operating system). |
| Driver sync | Part of the scan that checks driver updates only. This sync is optional and runs after the software sync. |
| ProductSync | A sync based on attributes, in which the client provides a list of device, product, and caller attributes ahead of time to allow service to check applicability in the cloud. |
How Windows Update scanning works
Windows Update does the following actions when it runs a scan.
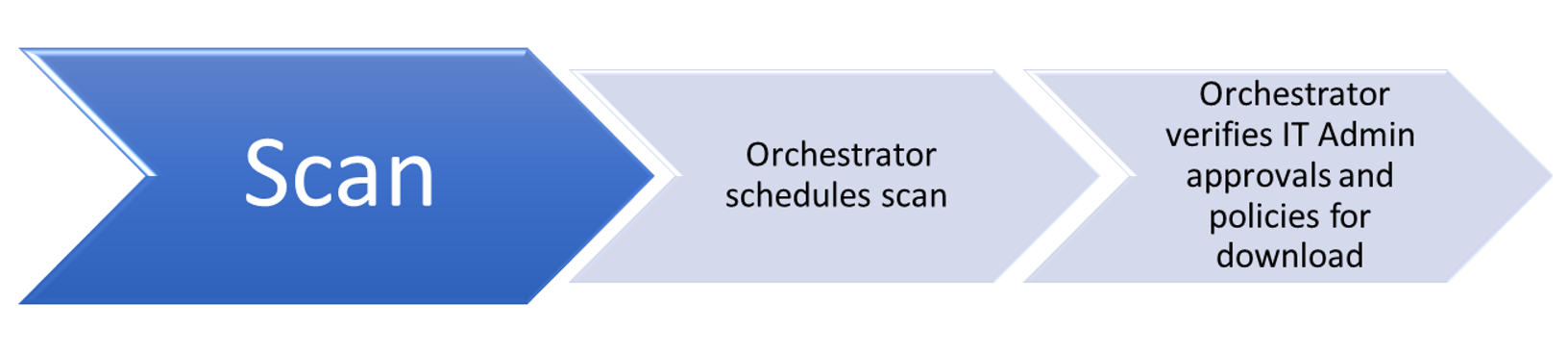
Starts the scan for updates
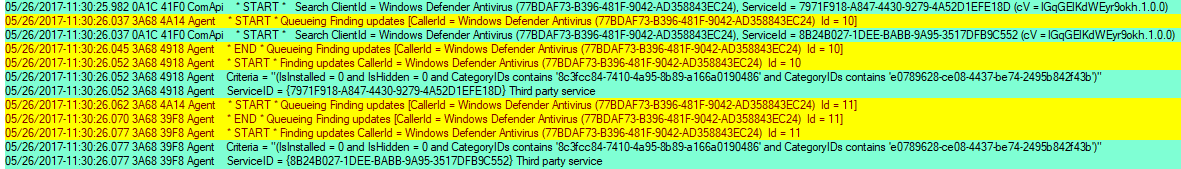
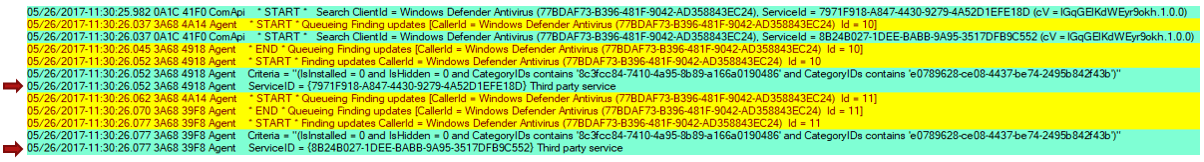
When users start scanning in Windows Update through the Settings panel, the following occurs:
- The scan first generates a “ComApi” message. The caller (Microsoft Defender Antivirus) tells the Windows Update engine to scan for updates.
- «Agent» messages: queueing the scan, then actually starting the work:
Updates are identified by the different IDs («ID = 10», «ID = 11») and from the different thread ID numbers.
Windows Update uses the thread ID filtering to concentrate on one particular task.
Identifies service IDs
Service IDs indicate which update source is being scanned.
The Windows Update engine treats every service as a separate entity, even though multiple services may contain the same updates.
Common service IDs
ServiceId here identifies a client abstraction, not any specific service in the cloud. No assumption should be made of which server a serviceId is pointing to. It’s totally controlled by responses from the Service Locator Service.
| Service | ServiceId |
|---|---|
| Unspecified / Default | WU, MU, or WSUS 00000000-0000-0000-0000-000000000000 |
| Windows Update | 9482F4B4-E343-43B6-B170-9A65BC822C77 |
| Microsoft Update | 7971f918-a847-4430-9279-4a52d1efe18d |
| Store | 855E8A7C-ECB4-4CA3-B045-1DFA50104289 |
| OS Flighting | 8B24B027-1DEE-BABB-9A95-3517DFB9C552 |
| WSUS or Configuration Manager | Via ServerSelection::ssManagedServer 3DA21691-E39D-4da6-8A4B-B43877BCB1B7 |
| Offline scan service | Via IUpdateServiceManager::AddScanPackageService |
Finds network faults
Common update failure is caused due to network issues. To find the root of the issue:
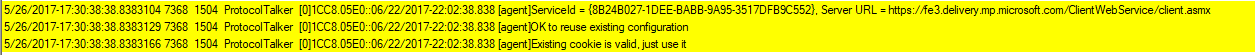
Look for «ProtocolTalker» messages to see client-server sync network traffic.
«SOAP faults» can be either client- or server-side issues; read the message.
The Windows Update client uses the Service Locator Service to discover the configurations and endpoints of Microsoft network update sources: Windows update, Microsoft Update, or Flighting.
If the search is against WSUS or Configuration Manager, you can ignore warning messages for the Service Locator Service.
On sites that only use WSUS or Configuration Manager, the Service Locator Service might be blocked at the firewall. In this case the request will fail, and though the service can’t scan against Windows Update or Microsoft Update, it can still scan against WSUS or Configuration Manager, since it’s locally configured.
Downloading updates
Once the Windows Update Orchestrator determines which updates apply to your computer, it will begin downloading the updates, if you have selected the option to automatically download updates. It does operation in the background without interrupting your normal use of the device.
To ensure that your other downloads aren’t affected or slowed down because updates are downloading, Windows Update uses Delivery Optimization, which downloads updates and reduces bandwidth consumption.
Installing updates
When an update is applicable, the «Arbiter» and metadata are downloaded. Depending on your Windows Update settings, when downloading is complete, the Arbiter will gather details from the device, and compare that with the downloaded metadata to create an «action list».
The action list describes all the files needed from Windows Update, and what the installation agent (such as CBS or Setup) should do with them. The action list is provided to the installation agent along with the payload to begin the installation.
Committing Updates
When the option to automatically install updates is configured, the Windows Update Orchestrator, in most cases, automatically restarts the device for you after installing the updates. It has to restart the device because it might be insecure, or not fully updated, until it restarts. You can use Group Policy settings, mobile device management (MDM), or the registry (not recommended) to configure when devices will restart after a Windows 10 update is installed.
How does Windows Update work?
The Windows Update workflow has four core areas of functionality:
Download
Install
Commit
How updating works
During the updating process, the Windows Update Orchestrator operates in the background to scan, download, and install updates. It does these actions automatically, according to your settings, and silently so that doesn’t disrupt your computer usage.
Scanning updates
The Windows Update Orchestrator on your PC checks the Microsoft Update server or your WSUS endpoint for new updates at random intervals. The randomization ensures that the Windows Update server isn’t overloaded with requests all at the same time. The Update Orchestrator searches only for updates that have been added since the last time updates were searched, allowing it to find updates quickly and efficiently.
When checking for updates, the Windows Update Orchestrator evaluates whether the update is appropriate for your device. It uses guidelines defined by the publisher of the update, for example, Microsoft Office including enterprise group policies.
Make sure you’re familiar with the following terminology related to Windows Update scan:
| Term | Definition |
|---|---|
| Update | We use this term to mean several different things, but in this context it’s the actual updated code or change. |
| Bundle update | An update that contains 1-N child updates; doesn’t contain payload itself. |
| Child update | Leaf update that’s bundled by another update; contains payload. |
| Detector update | A special «update» that contains «IsInstalled» applicability rule only and no payload. Used for prereq evaluation. |
| Category update | A special «detectoid» that has an IsInstalled rule that is always true. Used for grouping updates and to allow the device to filter updates. |
| Full scan | Scan with empty datastore. |
| Delta scan | Scan with updates from previous scan already cached in datastore. |
| Online scan | Scan that uses the network and to check an update server. |
| Offline scan | Scan that doesn’t use the network and instead checks the local datastore. Only useful if online scan has been performed before. |
| CatScan | Category scan where caller can specify a categoryId to get updates published under that categoryId. |
| AppCatScan | Category scan where caller can specify an AppCategoryId to get apps published under that appCategoryId. |
| Software sync | Part of the scan that only checks for software updates (both the apps and the operating system). |
| Driver sync | Part of the scan that checks driver updates only. This sync is optional and runs after the software sync. |
| ProductSync | A sync based on attributes, in which the client provides a list of device, product, and caller attributes ahead of time to allow service to check applicability in the cloud. |
How Windows Update scanning works
Windows Update does the following actions when it runs a scan.
Starts the scan for updates
When users start scanning in Windows Update through the Settings panel, the following occurs:
- The scan first generates a “ComApi” message. The caller (Microsoft Defender Antivirus) tells the Windows Update engine to scan for updates.
- «Agent» messages: queueing the scan, then actually starting the work:
Updates are identified by the different IDs («ID = 10», «ID = 11») and from the different thread ID numbers.
Windows Update uses the thread ID filtering to concentrate on one particular task.
Identifies service IDs
Service IDs indicate which update source is being scanned.
The Windows Update engine treats every service as a separate entity, even though multiple services may contain the same updates.
Common service IDs
ServiceId here identifies a client abstraction, not any specific service in the cloud. No assumption should be made of which server a serviceId is pointing to. It’s totally controlled by responses from the Service Locator Service.
| Service | ServiceId |
|---|---|
| Unspecified / Default | WU, MU, or WSUS 00000000-0000-0000-0000-000000000000 |
| Windows Update | 9482F4B4-E343-43B6-B170-9A65BC822C77 |
| Microsoft Update | 7971f918-a847-4430-9279-4a52d1efe18d |
| Store | 855E8A7C-ECB4-4CA3-B045-1DFA50104289 |
| OS Flighting | 8B24B027-1DEE-BABB-9A95-3517DFB9C552 |
| WSUS or Configuration Manager | Via ServerSelection::ssManagedServer 3DA21691-E39D-4da6-8A4B-B43877BCB1B7 |
| Offline scan service | Via IUpdateServiceManager::AddScanPackageService |
Finds network faults
Common update failure is caused due to network issues. To find the root of the issue:
Look for «ProtocolTalker» messages to see client-server sync network traffic.
«SOAP faults» can be either client- or server-side issues; read the message.
The Windows Update client uses the Service Locator Service to discover the configurations and endpoints of Microsoft network update sources: Windows update, Microsoft Update, or Flighting.
If the search is against WSUS or Configuration Manager, you can ignore warning messages for the Service Locator Service.
On sites that only use WSUS or Configuration Manager, the Service Locator Service might be blocked at the firewall. In this case the request will fail, and though the service can’t scan against Windows Update or Microsoft Update, it can still scan against WSUS or Configuration Manager, since it’s locally configured.
Downloading updates
Once the Windows Update Orchestrator determines which updates apply to your computer, it will begin downloading the updates, if you have selected the option to automatically download updates. It does operation in the background without interrupting your normal use of the device.
To ensure that your other downloads aren’t affected or slowed down because updates are downloading, Windows Update uses Delivery Optimization, which downloads updates and reduces bandwidth consumption.
Installing updates
When an update is applicable, the «Arbiter» and metadata are downloaded. Depending on your Windows Update settings, when downloading is complete, the Arbiter will gather details from the device, and compare that with the downloaded metadata to create an «action list».
The action list describes all the files needed from Windows Update, and what the installation agent (such as CBS or Setup) should do with them. The action list is provided to the installation agent along with the payload to begin the installation.
Committing Updates
When the option to automatically install updates is configured, the Windows Update Orchestrator, in most cases, automatically restarts the device for you after installing the updates. It has to restart the device because it might be insecure, or not fully updated, until it restarts. You can use Group Policy settings, mobile device management (MDM), or the registry (not recommended) to configure when devices will restart after a Windows 10 update is installed.