- Службы Windows Server Update Services (WSUS) Windows Server Update Services (WSUS)
- Описание роли сервера WSUS WSUS Server role description
- Практическое применение Practical applications
- Новые и измененные функции New and changed functionality
- Использование Windows PowerShell для управления WSUS Using Windows PowerShell to manage WSUS
- Содержание коллекции In this collection
- Развертывание служб Windows Server Update Services Deploy Windows Server Update Services
- Windows Server Update Services best practices
- Capacity limits
- Disable recycling and configure memory limits
- Check whether compression is enabled (if you want to conserve bandwidth)
- Configure products and categories
- Disable Itanium updates and other unnecessary updates
- Decline superseded updates and run maintenance
- WSUS with SSL setup
- Configure Antivirus Exclusions
- About Cumulative Updates and Monthly Rollups
- Using PowerShell to connect to a WSUS server
Службы Windows Server Update Services (WSUS) Windows Server Update Services (WSUS)
Область применения. Windows Server (Semi-Annual Channel), Windows Server 2019, Windows Server 2016, Windows Server 2012 R2, Windows Server 2012 Applies To: Windows Server (Semi-Annual Channel), Windows Server 2019, Windows Server 2016, Windows Server 2012 R2, Windows Server 2012
Службы Windows Server Update Services (WSUS) позволяют ИТ-администраторам развертывать новейшие обновления продуктов Майкрософт. Windows Server Update Services (WSUS) enables information technology administrators to deploy the latest Microsoft product updates. Службы WSUS позволяют в полной мере управлять процессом распределения обновлений, выпущенных через Центр обновления Майкрософт, среди компьютеров в сети. You can use WSUS to fully manage the distribution of updates that are released through Microsoft Update to computers on your network. В данном разделе представлен обзор этой роли сервера и дополнительные сведения о том, как развертывать и обслуживать WSUS. This topic provides an overview of this server role and more information about how to deploy and maintain WSUS.
Описание роли сервера WSUS WSUS Server role description
Сервер WSUS предоставляет возможности для управления обновлениями и их распространения через консоль управления. A WSUS server provides features that you can use to manage and distribute updates through a management console. Сервер служб WSUS может также быть источником обновлений для других серверов WSUS в организации. A WSUS server can also be the update source for other WSUS servers within the organization. Сервер WSUS, действующий как источник обновлений, называется вышестоящим сервером. The WSUS server that acts as an update source is called an upstream server. В реализации служб WSUS хотя бы один сервер WSUS в сети должен иметь возможность подключаться к Центру обновления Майкрософт для получения информации о доступных обновлениях. In a WSUS implementation, at least one WSUS server on your network must be able to connect to Microsoft Update to get available update information. Учитывая вопросы безопасности и конфигурации сети, администратор может самостоятельно определить количество дополнительных серверов, напрямую подключенных к Центру обновления Майкрософт. As an administrator, you can determine — based on network security and configuration — how many other WSUS servers connect directly to Microsoft Update.
Практическое применение Practical applications
Управление обновлениями — это процесс управления развертыванием и обслуживанием промежуточных выпусков программного обеспечения в рабочей среде. Update management is the process of controlling the deployment and maintenance of interim software releases into production environments. Это помогает поддерживать производительность, преодолевать уязвимости и обеспечивать стабильность рабочей среды. It helps you maintain operational efficiency, overcome security vulnerabilities, and maintain the stability of your production environment. Если организация не может устанавливать и поддерживать известный уровень доверия в своих операционных системах и прикладном программном обеспечении, то у нее может появиться ряд уязвимостей, что в случае взлома способно привести к потере дохода и интеллектуальной собственности. If your organization cannot determine and maintain a known level of trust within its operating systems and application software, it might have a number of security vulnerabilities that, if exploited, could lead to a loss of revenue and intellectual property. Чтобы минимизировать данную угрозу, необходимо правильно настроить системы, использовать последние версии программного обеспечения и установить рекомендуемые обновления ПО. Minimizing this threat requires you to have properly configured systems, use the latest software, and install the recommended software updates.
Основными сценариями, в которых WSUS повышает эффективность вашего бизнеса, являются: The core scenarios where WSUS adds value to your business are:
Централизованное управление обновлениями Centralized update management
Автоматизация управления обновлениями Update management automation
Новые и измененные функции New and changed functionality
Обновление с любой версии Windows Server, поддерживающей WSUS 3.2, до Windows Server 2012 R2 требует предварительного удаления WSUS 3.2. Upgrade from any version of Windows Server that supports WSUS 3.2 to Windows Server 2012 R2 requires that you first uninstall WSUS 3.2.
В Windows Server 2012 обновление с любой версии Windows Server с установленными службами WSUS 3.2 блокируется в процессе установки, если будет обнаружена служба WSUS 3.2. In Windows Server 2012, upgrading from any version of Windows Server with WSUS 3.2 installed is blocked during the installation process if WSUS 3.2 is detected. В этом случае вам будет предложено сначала удалить службы обновления Windows Server, а затем повторно обновить сервер. In that case, you will be prompted to first uninstall Windows Server Update Services prior to upgrading your server.
Но после изменений, внесенных в текущем выпуске Windows Server и Windows Server 2012 R2, установка не блокируется при обновлении с любой версии Windows Server и WSUS 3.2. However, because of changes in this release of Windows Server and Windows Server 2012 R2, when upgrading from any version of Windows Server and WSUS 3.2, the installation is not blocked. Если перед выполнением обновления Windows Server или Windows Server 2012 R2 не будут удалены службы WSUS 3.2, то задачи WSUS после установки будут завершаться ошибкой. Failure to uninstall WSUS 3.2 prior to performing a Windows Server 2012 R2 upgrade will cause the post installation tasks for WSUS in Windows Server 2012 R2 to fail. Известен только один метод решения такой проблемы — отформатировать жесткий диск и повторно установить Windows Server. In this case, the only known corrective measure is to format the hard drive and reinstall Windows Server.
Службы Windows Server Update Services представляют собой встроенную роль сервера со следующими дополнительными возможностями. Windows Server Update Services is a built-in server role that includes the following enhancements:
Может быть добавлена и удалена с помощью диспетчера серверов Can be added and removed by using the Server Manager
Включает командлеты Windows PowerShell для управления наиболее важными задачами администрирования в службах WSUS Includes Windows PowerShell cmdlets to manage the most important administrative tasks in WSUS
Добавляет возможность использования хэширования SHA256 для дополнительной безопасности Adds SHA256 hash capability for additional security
Обеспечивает разделение клиента и сервера, благодаря чему версии агента Центра обновления Windows (WUA) могут поставляться независимо от WSUS Provides client and server separation: versions of the Windows Update Agent (WUA) can ship independently of WSUS
Использование Windows PowerShell для управления WSUS Using Windows PowerShell to manage WSUS
Системным администраторам для автоматизации работы необходим охват с помощью автоматизации командной строки. For system administrators to automate their operations, they need coverage through command-line automation. Основной целью является облегчение администрирования WSUS, позволяя системным администраторам автоматизировать их ежедневный труд. The main goal is to facilitate WSUS administration by allowing system administrators to automate their day-to-day operations.
Какой эффект дает это изменение? What value does this change add?
Пропуская основные операции WSUS через Windows PowerShell, системные администраторы могут увеличить продуктивность, уменьшить время на изучение новых инструментов, а также снизить количество ошибок из-за неоправданных ожиданий, ставших результатом отсутствия согласованности простых операций. By exposing core WSUS operations through Windows PowerShell, system administrators can increase productivity, reduce the learning curve for new tools, and reduce errors due to failed expectations resulting from a lack of consistency across similar operations.
Что работает иначе? What works differently?
В более ранних версиях операционной системы Windows Server отсутствовали командлеты Windows PowerShell, а автоматизация управления обновлениями была затруднительным делом. In earlier versions of the Windows Server operating system, there were no Windows PowerShell cmdlets, and update management automation was challenging. Командлеты Windows PowerShell для операций WSUS дают дополнительную гибкость и быстроту системному администратору. The Windows PowerShell cmdlets for WSUS operations add flexibility and agility for the system administrator.
Содержание коллекции In this collection
В эту коллекцию включены следующие руководства по планированию, развертыванию и администрированию служб WSUS. The following guides for planning, deploying, and managing WSUS are in this collection:
Развертывание служб Windows Server Update Services Deploy Windows Server Update Services
Область применения. Windows Server (Semi-Annual Channel), Windows Server 2019, Windows Server 2016, Windows Server 2012 R2, Windows Server 2012 Applies To: Windows Server (Semi-Annual Channel), Windows Server 2019, Windows Server 2016, Windows Server 2012 R2, Windows Server 2012
Службы Windows Server Update Services (WSUS) позволяют ИТ-администраторам развертывать новейшие обновления продуктов Майкрософт. Windows Server Update Services (WSUS) enables information technology administrators to deploy the latest Microsoft product updates. WSUS — это роль сервера Windows Server, которую можно установить для распространения обновлений и управления ими. WSUS is a Windows Server server role that can be installed to manage and distribute updates. Сервер служб WSUS может быть источником обновлений для других серверов WSUS в организации. A WSUS server can be the update source for other WSUS servers within the organization. Сервер WSUS, действующий как источник обновлений, называется вышестоящим сервером. The WSUS server that acts as an update source is called an upstream server.
При реализации служб WSUS хотя бы один сервер служб WSUS в сети должен быть подключен к Центру обновления Майкрософт для получения информации о доступных обновлениях. In a WSUS implementation, at least one WSUS server in the network must connect to Microsoft Update to get available update information. В зависимости от безопасности сети и ее конфигурации вы можете определить, сколько других серверов напрямую подключено к Центру обновления Майкрософт. You can determine, based on network security and configuration, how many other servers connect directly to Microsoft Update.
Это руководство содержит базовые сведения о планировании развертывания службы Windows Server Update Service. This guide provides conceptual information for planning and deploying Windows Server Update Service.
Windows Server Update Services best practices
This article provides tips for avoiding configurations that experience poor performance because of design or configuration limitations in WSUS.
Original product version: В Configuration Manager (current branch), Windows Server Update Services
Original KB number: В 4490414
Capacity limits
Although WSUS can support 100,000 clients per server (150,000 clients when you use Configuration Manager), we don’t recommend approaching this limit.
Instead, consider using a configuration of 2-4 servers sharing the same SQL Server database. This way you have safety in numbers. If one server goes down, it won’t immediately spoil your weekend because no client can update while you must be updated against the latest zero-day exploit.
The shared database scenario also prevents a scan storm.
A scan storm can occur when many clients change WSUS servers and the servers don’t share a database. WSUS tracks activity in the database, so that both know what has changed since a client last scanned and will only send metadata that’s updated since then.
If clients change to a different WSUS server that uses a different database, they must do a full scan. A full scan can cause large metadata transfers. Transfers of greater than 1 GB per client may occur in these scenarios, especially if the WSUS server isn’t maintained correctly. It can generate enough load to cause errors when clients communicate with a WSUS instance. And clients retry repeatedly in this case.
Sharing a database means when a client switches to another WSUS instance that uses the same DB, the scan penalty isn’t incurred. The load increases aren’t the large penalty you pay for switching databases.
Configuration Manager client scans put more demand on WSUS than the stand-alone Automatic Updates. Configuration Manager, because it includes compliance checking, requests scans with criteria that will return all updates that are in any status except declined.
When the Automatic Updates Agent scans, or you select Check for Updates in Control Panel, the agent sends criteria to retrieve only those updates Approved for Install. The metadata returned will usually be less than when the scan is initiated by Configuration Manager. The Update Agent does cache the data, and the next scan requests will return the data from the client cache.
Disable recycling and configure memory limits
WSUS implements an internal cache that retrieves the update metadata from the database. This operation is expensive and very memory intensive. It can cause the IIS application pool that hosts WSUS (known as WSUSPool) to recycle when WSUSPool overruns the default private and virtual memory limits.
When the pool recycles, the cache is removed and must be rebuilt. It isn’t a large problem when clients are undergoing delta scans. But if you end up in a scan storm scenario, the pool will recycle constantly. And clients will receive errors when you make scan requests, such as HTTP 503 errors.
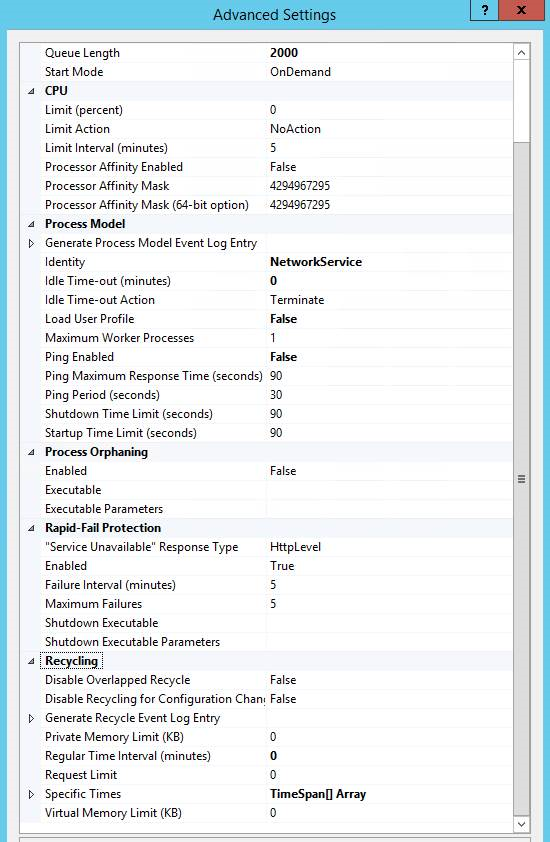
We recommend that you increase the default Queue Length, and disable both the Virtual and Private Memory Limit by setting them to 0. IIS implements an automatic recycling of the application pool every 29 hours, Ping, and Idle Time-outs, all which should be disabled. These settings are found in IIS Manager > Application Pools > choose WsusPool and then click the Advanced Settings link in the right side pane of IIS manager.
Here’s a summary of recommended changes, and a related screenshot. For more information, see Plan for software updates in Configuration Manager.
| Setting name | Value |
|---|---|
| Queue Length | 2000 (up from default of 1000) |
| Idle Time-out (minutes) | 0 (down from the default of 20) |
| Ping Enabled | False (from default of True) |
| Private Memory Limit (KB) | 0 (unlimited, up from the default of 1,843,200 KB) |
| Regular Time Interval (minutes) | 0 (to prevent a recycle, and modified from the default of 1740) |
In an environment that has around 17,000 updates cached, more than 24 GB of memory may be needed as the cache is built until it stabilizes (at around 14 GB).
Check whether compression is enabled (if you want to conserve bandwidth)
WSUS uses a compression type calls Xpress encoding. It implements compression on update metadata, and can result in significant bandwidth savings.
Xpress encoding is enabled in IIS ApplicationHost.config with this line under the element and a registry setting:
ApplicationHost.Config
Registry key
If both aren’t present, it can be enabled by running this command and then restarting the WsusPool application pool in IIS.
Xpress encoding will add some CPU overhead, and can be disabled if bandwidth isn’t a concern, but CPU usage is. The following command will turn it off.
Configure products and categories
When you configure WSUS, choose only the products and categories that you plan to deploy. You can always synchronize categories and products that you must have later. Adding them when you don’t plan to deploy them increases metadata size and overhead on the WSUS servers.
Disable Itanium updates and other unnecessary updates
It shouldn’t be an issue for much longer, because Windows Server 2008 R2 was the last version to support Itanium. But it bears mentioning.
Customize and use this script in your environment to decline Itanium architecture updates. The script can also decline updates that contain Preview or Beta in the update title.
It leads to the WSUS console being more responsive, but doesn’t affect the client scan.
Decline superseded updates and run maintenance
One of the most important things that you can do to help WSUS run better. Keeping updates around that are superseded longer than needed (for example, after you’re no longer deploying them) is the leading cause of WSUS performance problems. It’s ok to keep them around if you’re still deploying them. Remove them after you’re done with them.
For information about declining superseded updates and other WSUS maintenance items, see the Complete guide to Microsoft WSUS and Configuration Manager SUP maintenance article.
WSUS with SSL setup
By default, WSUS isn’t configured to use SSL for client communication. The first post-install step should be to configured SSL on WSUS to make sure security between server-client communications.
You must take one the following actions:
- Create a self-signed certificate. It isn’t ideal because every client would have to trust this certificate.
- Obtain one from a third-party certificate provider.
- Obtain one from your internal certificate infrastructure.
Your certificate must have the short server name, FQDN, and SAN names (aliases) that it goes by.
After you have the certificate installed, upgrade the Group Policy (or Client Configuration settings for software updates in Configuration Manager) to use the address and SSL port of the WSUS server. The port is typically 8531 or 443.
For example, configure GPO Specify intranet Microsoft update service location to https://wsus.contoso.com:8531 >.
Configure Antivirus Exclusions
About Cumulative Updates and Monthly Rollups
You may see the terms Monthly Rollups and Cumulative Update used for Windows OS updates. They may be used interchangeably. Rollups refer to the updates published for Windows 7, Windows 8.1, Windows Server 2008 R2, and Windows Server 2012 R2 that are only partly cumulative.
For more information, see the following blog posts:
With Windows 10 and Windows Server 2016, the updates were cumulative from the beginning:
Cumulative means that: you install the release version of the OS, and only have to apply the latest Cumulative Update to be fully patched. For the older operating systems, we don’t have such updates yet, although it’s the direction we’re heading in.
For Windows 7 and Windows 8.1, it means that after you install the latest monthly rollup, more updates will still be needed. Here’s an example for Windows 7 and Windows Server 2008 R2 on what it takes to have an almost fully patched system.
The following table contains the list of Windows Monthly Rollups and Cumulative Updates. You can also find them by searching for Windows update History.
| Windows version | Update |
|---|---|
| Windows 7 SP1 and Windows Server 2008 R2 SP1 | Windows 7 SP1 and Windows Server 2008 R2 SP1 update history |
| Windows 8.1 and Windows Server 2012 R2 | Windows 8.1 and Windows Server 2012 R2 update history |
| Windows 10 and Windows Server 2016 | Windows 10 and Windows Server update history |
| Windows Server 2019 | Windows 10 and Windows Server 2019 update history |
Another point to consider is that not all updates are published so that they sync automatically to WSUS. For example, C and D week Cumulative Updates are preview updates and won’t synchronize to WSUS, but must be manually imported instead. See the Monthly quality updates section of Windows 10 update servicing cadence.
Using PowerShell to connect to a WSUS server
Here’s just a code example to get you started with PowerShell and the WSUS API. It can be executed where the WSUS Administration Console is installed.