- Remote Server Administration Tools (RSAT) for Windows
- Introduction
- Download locations for RSAT
- RSAT for Windows 10 platform and tools support matrix
- RSAT for Windows 10, version 1809 or later versions
- Ldp exe windows 2012 r2
- Finding required and optional values for an attribute
- Understanding bind options for LDAP authentication
- Examples
Remote Server Administration Tools (RSAT) for Windows
RSAT enables IT administrators to remotely manage roles and features in Windows Server from a computer that is running Windows 10 and Windows 7 Service Pack 1.
Original product version: В Windows 10, version 1909, Windows 10, version 1903, Windows 10, version 1809, Windows 7 Service Pack 1, Windows Server 2019, Windows Server 2012 R2
Original KB number: В 2693643
Introduction
You can’t install RSAT on computers that are running Home or Standard editions of Windows. You can install RSAT only on Professional or Enterprise editions of the Windows client operating system. Unless the download page specifically states that RSAT applies to a beta, preview, or other prerelease version of Windows, you must be running a full (RTM) release of the Windows operating system to install and use RSAT. Some users have found ways of manually cracking or hacking the RSAT MSU to install RSAT on unsupported releases or editions of Windows. This behavior is a violation of the Windows end-user license agreement.
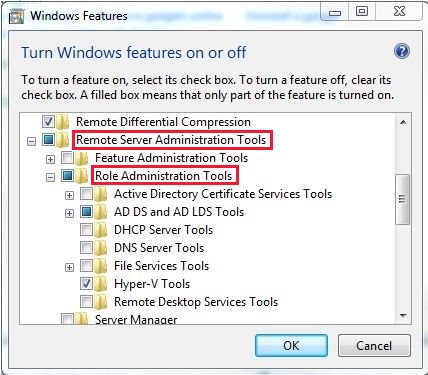
Installing RSAT is similar to installing Adminpak.msi in Windows 2000-based or Windows XP-based client computers. However, there’s one major difference: in Windows 7, the tools aren’t automatically available after you download and install RSAT. Enable the tools that you want to use by using Control Panel. To enable the tools, click Start, click Control Panel, click Programs and Features, and then click Turn Windows features on or off.
In the RSAT releases for Windows 10, tools are again all enabled by default. You can open Turn Windows features on or off to disable tools that you don’t want to use for Windows 7.
For RSAT in Windows 7, you must enable the tools for the roles and features that you want to manage after you run the downloaded installation package.
You can’t do the following changes for RSAT in Windows 8 or later versions.
If you have to install management tools in Windows Server 2012 R2 for specific roles or features that are running on remote servers, you don’t have to install additional software. Start the Add Roles and Features Wizard in Windows Server 2012 R2 and later versions. Then, on the Select Features page, expand Remote Server Administration Tools, and then select the tools that you want to install. Complete the wizard to install your management tools.
Download locations for RSAT
RSAT for Windows 10 platform and tools support matrix
| Remote Server Administration Tools Technology | Description | Manages technology in Windows Server 2012 R2 | Manages technology in Windows Server 2016 Technical Preview and Windows Server 2012 R2 |
|---|---|---|---|
| Active Directory Certificate Services (AD CS) tools | AD CS tools include the Certification Authority, Certificate Templates, Enterprise PKI, and Online Responder Management snap-ins. | в€љ | в€љ |
| Active Directory Domain Services (AD DS) tools and Active Directory Lightweight Directory Services (AD LDS) tools | AD DS and AD LDS tools include the following tools: |
— Active Directory Administrative Center
— Active Directory Domains and Trusts
— Active Directory Sites and Services
— Active Directory Users and Computers
— ADSI Edit
— Active Directory module for Windows PowerShell
— Tools such as
- DCPromo.exe
- LDP.exe
- NetDom.exe
- NTDSUtil.exe
- RepAdmin.exe
- DCDiag.exe
- DSACLs.exe
- DSAdd.exe
- DSDBUtil.exe
- DSMgmt.exe
- DSMod.exe
- DSMove.exe
- DSQuery.exe
- DSRm.exe
- GPFixup.exe
- KSetup.exe
- NlTest.exe
- NSLookup.exe
- W32tm.exe
— Connection Manager Administration Kit console
— Remote Access provider for Windows PowerShell
— Web Application Proxy
GUI tools support Windows Server 2016 Technical Preview and Windows Server 2012 R2. Only PowerShell tools work in Windows Server 2012.
— Share and Storage Management tools
— Distributed File System tools
- The DFS Management snap-in
- The Dfsradmin.exe , Dfsrdiag.exe , Dfscmd.exe , Dfsdiag.exe , and Dfsutil.exe command-line tools
- PowerShell modules for DFSN and DFSR
— File Server Resource Manager tools
- The File Server Resource Manager snap-in
- The Dirquota.exe , Filescrn.exe , and Storrept.exe command-line tools.
— Services for NFS Administration tools
— iSCSI management cmdlets for Windows PowerShell
— Work Folders Management tools
The Share and Storage Management snap-in is deprecated after the release of Windows Server 2016. Storage Replica is new in Windows Server 2016 Technical Preview, and won’t work in Windows Server 2012 R2.
Group Policy has some new features in Windows Server 2016 Technical Preview that aren’t available on older operating systems.
IPAM tools in Remote Server Administration Tools for Windows 10 can’t be used to manage IPAM running in Windows Server 2012 R2.
IPAM tools in Remote Server Administration Tools for Windows 10 can’t be used to manage IPAM running in Windows Server 2012 R2.
— Remote Desktop snap-ins
— RD Gateway Manager
— tsgateway.msc
— RD Licensing Manager
— licmgr.exe
— RD Licensing Diagnoser
— lsdiag.msc
Use Server Manager to administer all other RDS role services except RD Gateway and RD Licensing.
Remote management with Server Manager is available in Windows Server 2016 Technical Preview, Windows Server 2012 R2, and Windows Server 2012.
WSRM has been deprecated in Windows Server 2012 R2. Tools for managing WSRM aren’t available in RSAT for Windows 8.1 and later releases of RSAT.
RSAT for Windows 10, version 1809 or later versions
You can’t use the Turn Windows features on and off dialog from the Control Panel
Installing the RSAT Tools for Windows 10 version 1809 and later version is slightly different from earlier versions. RSAT is now part of the Operating System an can be installed via Optional Features.
To enable the tools, click Start, click Settings, click Apps, and then click Optional features, after that click on the panel Add a feature and enter Remote in the search bar.
Ldp exe windows 2012 r2
Applies To: Windows Server 2008, Windows Server 2012, Windows 8
Performs operations such as connect, bind, search, modify, add, delete against any Lightweight Directory Access Protocol (LDAP)-compatible directory, such as ActiveВ Directory Domain Services (ADВ DS). Ldp is an LDAP client that you use to view objects that are stored in ADВ DS along with their metadata, such as security descriptors and replication metadata.
Ldp is a graphical user interface (GUI)-based, Windows Explorer–like tool with a scope pane on the left that is used for navigating through the Active Directory namespace, and a details pane on the right that is used for displaying the results of the LDAP operations. Any text that is displayed in the details pane can be selected with the mouse and copied to the Clipboard.
Ldp is built into Windows ServerВ 2008. It is available if you have the ADВ DS server role installed. To start ldp, click Start, click Run, type ldp and then click OK.
For examples of how to use this command, see Examples.
Finding required and optional values for an attribute
The schema defines objects as well as the attributes and permissible values for each. Schema classes that contain attribute information about objects can be viewed. To view this information, search cn=Schema,cn=Configuration,dc=ForestRootDomain for classSchema objects.
Understanding bind options for LDAP authentication
There are several authentication methods available in ldp that allow a client to bind to an LDAP server. The best method depends on several factors.
Cleartext password. Try not to use this, as it is not secure.
MSN (Microsoft Network) authentication. This package brings up a dialog box to prompt the user for MSN credentials.
Normandy authentication, new MSN authentication. Same usage as MSN.
WindowsВ NT domain authentication. Use NULL credentials and attempt to use default logged-in user credentials.
Negotiate with the server for any of: MSN, DPA, NTLM. Should be used for LDAPv2 servers only.
Use GSSAPI Negotiate package to negotiate security package of either KerberosВ V5 or NTLM (or any other package the client and server negotiate). Pass in NULL credentials to specify default logged-in user. If Negotiate package is not installed on server or client, this will fall back to Sicily negotiation.
Examples
Example 1: Add a new object to an LDAP directory
To add a user to ActiveВ Directory by using ldp:
On the Browse menu, click Add child.
In the Add dialog box, in the Dn input box, enter the distinguished name of the new object.
In the Edit Entry section, add the new attributes and values. Click Enter after typing in each attribute and associated value:
To add the attribute or value combination to the Entry List box, click Edit.
To add the information to ActiveВ Directory using LDAP APIs when all the attributes are entered, click Run.
Example 2: Search an LDAP directory
To search ActiveВ Directory by using ldp:
On the Browse menu, click Search.
The Search dialog box opens.
In the following searches, the LDAP directory is ADВ DS. For user names, it contains a givenName attribute for first names, and an attribute of sn for last names.
To search for all users that have a first name of John and a last name of either Smith or Jones, type the following in the Filter field:
To search for users that have a last name of Jones, but filter out those users that have a first name of John or Jane, and also filter out users that have not logged on at least 100В times, type the following in the Filter field. (The exclamation point (!) is the NOT operator.)
To search for reserved characters as part of an attribute value, you must precede the reserved character with an escape character. Use the following escape characters to represent the associated characters:
To search for all of the users whose display names end in a close parenthesis character, type the following in the Filter field:
To search for all users who have a surname that starts with the letterВ J, type the following in the Filter field. (Queries support the wildcard character (*).)
To search for users whose home directories are G:\Accounting, type the following in the Filter field. (The attribute name is home-directory.)
Example 3: Control the returns on a search of an LDAP directory
In this example, you use the Search Options dialog box to control which attributes are displayed in a search. Just a few attributes are displayed; the rest are filtered and do not display in the details window of ldp.
To control which attributes display:
In the Attributes input box, type the attributes to display:
Separate attributes with a semicolon. No spaces are necessary. All other attributes will be filtered out of the display.
A range is specified for the memberof attribute. Because a semicolon is used, the entire section must be separated from the rest of the attributes by quotation marks.
All searches display only the memberof, objectClass, and objectGUID attributes in the details pane. To return all attributes, replace any existing list of attributes with the wildcard character (*).
Example 4: View replication metadata for an object
To list the replication metadata for an object in ActiveВ Directory:
On the Browse menu, point to Replication and then click View Metadata.
The Replication Metadata dialog box opens.
In the Object DN field, enter the distinguished name of the object, and then click OK.
The output will look similar to the output in the following table.