- Как: Сгенерировать Хэш Пароля в Linux и как узнать тип хэша
- Сгенерировать Хэш Пароля в Linux
- Создать Хэш Пароля для /etc/shadow
- Узнать тип хэша
- Добавить комментарий Отменить ответ
- /etc/shadow – HowTo: Generate Password Hash in Linux
- Generate Password Hash for /etc/shadow
- Different Ways To Generate A Strong Password In Linux
- Generate a strong password in Linux
- Method 1 — using OpenSSL
- Method 2 — using Pwgen
- Method 3 — using GPG
- Method 4 — using Apg
- Method 5 — using xkcdpass
- Method 6 — using Urandom
- Method 7 — using Makepasswd
- Method 8 — using a Perl script
- Help us to help you:
- You May Also Like
- A List Of Useful Console Services For Linux.
- How To Assign Multiple IP Addresses To Single.
- How To View The Contents Of An Archive.
- WebGoat Teaches You To Fix Web Application Flaws.
- DF-SHOW – A Terminal File Manager Based On.
- Create Persistent Bootable USB Using Ventoy In Linux
- 14 comments
Как: Сгенерировать Хэш Пароля в Linux и как узнать тип хэша
Сгенерировать Хэш Пароля в Linux
Linux хранить зашифрованные пароли пользователей, также как и другую информацию связанную с безопасностью, например сроки действия аккаунтов или паролей, в файле /etc/shadow .
Однажды у вас может возникнуть необходимость вручную отредактировать файл /etc/shadow для того, чтобы задать или изменить чей-то пароль.
В отличие от файла /etc/passwd , который могут читать все, файл /etc/shadow должен быть доступен для чтения ИСКЛЮЧИТЕЛЬНО пользователю ROOT.
Для этого вам придется сгенерировать хэш пароля в формате, который будет совмести с /etc/shadow .
Нет необходимости устанавливать дополнительные утилиты, так как это может быть легко сделано из командной строки в Linux с помощью Python.
Создать Хэш Пароля для /etc/shadow
Зашифрованные пароли в /etc/shadow хранятся в следующем формате:
$ID обозначает тип шифрования, $SALT — это случайная (до 16 символов) строка и $ENCRYPTED — хэш пароля.
| Тип Хэша | ID | Длина Хэша |
|---|---|---|
| MD5 | $1 | 22 символов |
| SHA-256 | $5 | 43 символов |
| SHA-512 | $6 | 86 символов |
Используйте следующие команды из терминала в Linux для создания хэшированых паролей со случайной солью для /etc/shadow .
Создать MD5 Хэш пароля:
Создать SHA-256 Хэш пароля:
Создать SHA-512 Хэш пароля:
Надеюсь эти команды будут вам полезны.
Только не забудьте поменять MySecretPassword на ваш YourSecretPassword.
Как вы видите, это действительно очень легко генерировать хэши для /etc/shadow из командной строки в Linux с помощью Python.
В частности потому, что Python, по умолчанию, установлен в большинстве Linux дистрибутивах.
Узнать тип хэша
Существуют два основных параметра, которые могут помочь распознать тип используемой хэш-функции:
- Длина ХЭШа (каждая хэш-функция имеет определенную выходную длину);
- Используемый алфавит (есть ли английские буквы? числа 0-9 и A-F … возможно это hex? используются ли специальные символы?).
Step 1: Скачиваем последнюю версию (v1.1 на текущий момент)
Step 2: Запускаем скрипт и копируем интересующие нас ХЭШи
Добавить комментарий Отменить ответ
Для отправки комментария вам необходимо авторизоваться.
Источник
/etc/shadow – HowTo: Generate Password Hash in Linux
Linux stores users’ encrypted passwords, as well as other security information, such as account or password expiration values, in the /etc/shadow file.
Someday you may need to edit the /etc/shadow file manually to set or change ones password.
Unlike the /etc/passwd that is readable for everyone, the /etc/shadow file MUST be readable by the ROOT user only.
For this you would have to generate password hash in the format compatible with /etc/shadow .
Cool Tip: Want to create a USER with ROOT privileges? This can be very dangerous! But if you insist… Read more →
There is no need to install any additional tools as it can be easily done from the Linux command line using Python.
Generate Password Hash for /etc/shadow
The $ID indicates the type of encryption, the $SALT is a random (up to 16 characters) string and $ENCRYPTED is a password’s hash.
| Hash Type | ID | Hash Length |
|---|---|---|
| MD5 | $1 | 22 characters |
| SHA-256 | $5 | 43 characters |
| SHA-512 | $6 | 86 characters |
Cool Tip: Got a hash but don’t know what type is it? Find out how to easily identify different hash types! Read more →
Use the below commands from the Linux shell to generate hashed password for /etc/shadow with the random salt.
Generate MD5 password hash:
Generate SHA-256 password hash:
Generate SHA-512 password hash:
Hope these commands will be helpful.
Just don’t forget to replace MySecretPassword with YourSecretPassword.
As you can see, it is really very easy to generate hashes for the /etc/shadow from the Linux command line using Python.
Particularly for the reason that the Python is installed by default on the most Linux distributions.
Источник
Different Ways To Generate A Strong Password In Linux
A while ago we have covered how to force users to use a strong password in DEB based systems such as Debian, Ubuntu, Linux Mint, Elementary OS etc. You might wonder how a strong password looks like, and how could we create one? No worries! Here are a few different ways to generate a strong password in Linux. Of course, there are many free tools and ways to accomplish this task, however I consider these methods are simple, and straightforward.
Generate a strong password in Linux
There could be many ways. As of now, I am aware of the following methods. I will update this list when I came across any new methods. Let us get started.
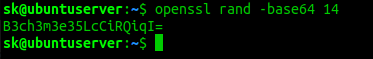
Method 1 — using OpenSSL
OpenSSL comes preinstalled in most Linux distributions.
To generate a random password with OpenSSL, run the following command in the Terminal:
Here, ‘-base64’ string will make sure the password can be typed on a keyboard.
Sample output:
The above command will generate a 14 byte random value encoded with base64. You can count the number of characters in the above random value by decoding it using command:
As you can see, we have generated a random and strong password with 14 characters long. The -d and -c flags in the above command refers «decode» and «byte count» respectively.
To generate generate a 16 byte (128 bit) random value, the command would be:
For more details, refer the man pages.
Method 2 — using Pwgen
pwgen is simple, yet useful command line utility to generate a random and strong password in seconds. It designs secure passwords that can be easily memorized by humans. It is available in the most Unix-like operating systems.
To install pwgen in DEB based systems, run:
In RPM based systems:
In Arch based systems:
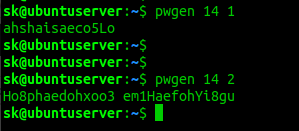
Once pwgen installed, generate a random and strong password with length of 14 letters using command:
Sample output:
The above command will generate only one password with length of 14 characters. To generate 2 different passwords with length of 14 characters, run:
Sample output:
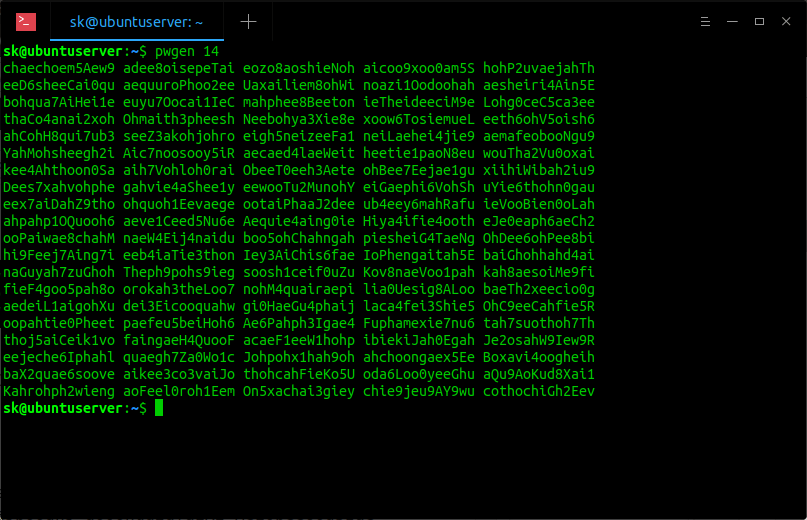
To generate 100 different passwords (Not necessary though) with length of 14 characters, run:
To include at least 1 number in the password run:
Sample output:
There are also some useful options available to use with pwgen command.
For more details, check the man pages.
Method 3 — using GPG
GPG (GnuPG or GNU Privacy Guard), is free command-line program and replacement of Symantec’s PGP cryptographic software.
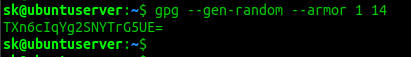
To generate a random and strong password with length of 14 characters using GPG, run the following command from the Terminal:
This command will generate a secure, random, strong and base64 encoded password.
For more details, refer man pages.
Suggested read:
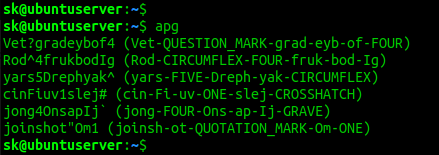
Method 4 — using Apg
Apg (stands for Automatic Password Generator) is a command line utility for generating strong random passwords. A good thing is Apg will generate «pronounceable» passwords. They are referred to as «pronounceable» because the passwords may actually be pronounced like regular words.
To install Apg on CentOS / RHEL, enable [EPEL] repository:
And the install it using command:
To install Apg on Ubuntu, enable [universe] repository:
And then install it using command:
Once installed, run Apg command to generate strong and random passwords:
As you can see in the above output, Apg generates 6 passwords. As I mentioned earlier, all generated passwords are pronounceable like a regular words and the pronunciation of each password is given in the brackets.
If you want to generate random character passwords instead of pronounceable passwords, use «-a 1» option like below.
More details can be found in its man pages.
Suggested read:
Method 5 — using xkcdpass
Xkcdpass is a flexible and scriptable password generator which generates strong passphrases. It is inspired
by XKCD 936.
Xkcdpass is available in the default repositories of some Linux distributions.
To install Xkcdpass on Arch Linux and its variants, run:
On Debian, Ubuntu:
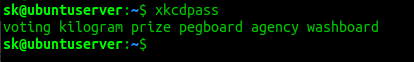
Once installed, run xkcdpass to generate a random passphrases.
This command generates one command with default options.
By default, it will generate 6 passphrases. You can use -n option to create any number of passphrases. The following command will display 10 random passphrases.
For further details, go through xkcdpass man pages.
Method 6 — using Urandom
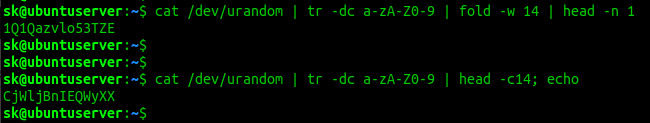
This yet another way to generate a random passphrases in Linux. We can use the /dev/urandom is a special file that serve as pseudorandom number generator in Unix-like operating systems. We can use this file to generate a random strings and use it as a password.
Here we use tr command to delete unwanted characters and print the 14 random characters.
You can also use the following command if you prefer a bit shorter version.
Man pages will give more information about /dev/urandom/ file.
Method 7 — using Makepasswd
Makepasswd is a command line utility to generate and encrypt plaintext passwords in Unix-like systems. It generates true random passwords using /dev/urandom which we discussed in the previous section.
Install Makepasswd on Ubuntu using commands:
And then install it using command:
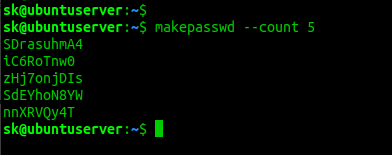
Once installed, create some random password using command:
By default, it generates one password. If you want to more one, for example 5, use:
To generate passwords with exactly N characters, for example 14, do:
Generate passwords with at most N characters (E.g. 20):
Generate passwords with at least N characters (E.g. 5):
You can, of course, combine these options and produce the result as you wish.
The above command will generate 5 passwords, each with at least 5 characters.
For more details, look into the man pages.
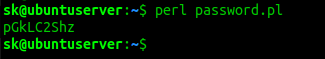
Method 8 — using a Perl script
Perl is available in the most Linux distribution’s default repositories. Install it using the default package manager like below.
For example, to install on Arch based systems:
On DEB based systems run:
On RPM based systems, run:
Once Perl installed, create a file:
Add the following contents in it.
Save and close the file.
Now, go to the location where you saved the file, and run the following command:
Replace password.pl with your own filename.
Sample output:
Note: I couldn’t find the original author of this script. If anyone know the author’s name, please let me know in the comment section below. I will add the author name in this guide.
Please note that you must either memorize or keep the passwords you have generated in a safe place. If you find it difficult to remember passwords, use a password manager. Here are few password managers to try.
Even though there are numerous password managers are avialble, I strongly recommend you to memorize the password and delete it from your system. It is much better just in case your system is compromised.
Thanks for stopping by!
Help us to help you:
- Subscribe to our Email Newsletter : Sign Up Now
- Support OSTechNix : Donate Via PayPal
- Download free E-Books and Videos : OSTechNix on TradePub
- Connect with us: Reddit | Facebook | Twitter | LinkedIn| RSS feeds
Have a Good day!!
I am Senthil Kumar, more commonly known as SK to my friends, from India. I love to read, write and explore topics on Linux, Unix and all other technology related stuff.
How To Find Which Service Is Listening On A Particular Port
How To Create Persistent Live USB Using Mkusb On Ubuntu
You May Also Like
A List Of Useful Console Services For Linux.
How To Assign Multiple IP Addresses To Single.
How To View The Contents Of An Archive.
WebGoat Teaches You To Fix Web Application Flaws.
DF-SHOW – A Terminal File Manager Based On.
Create Persistent Bootable USB Using Ventoy In Linux
14 comments
openssl passwd -1 -salt xyz mypasswordhere
Hello,
thanks for your article.
In the first example, the command should be “openssl rand -base64 14”.
Since the syntax for openssl rand is “openssl rand [flags] num”.
Thanks for pointing it out. I updated the guide with more methods now.
If you want to generate xkcd style passwords without having to install anything, here’s a one liner I wrote a while back. -n 5 gives you five words, -n 4 would give you 4 words. The tr’s are to remove punctuation (like apostrophes), convert lower to upper case and replace spaces with dashes.
shuf -n 5 /usr/share/dict/words | tr -d ‘[:punct:]’ | tr ‘[:lower:]’ ‘[:upper:]’ | tr ‘\n’ ‘-‘ | head -c-1; echo
I currently used diceware. It can be installed on most Linux distributions.
No need for that. Just think of a sentence memorable to you – for example: “This article proposes mechanisms that are not necessary, and which lead to passwords you can’t really remember.” Select the first letter in each word: “Tapmtann,awltpycrr.” You can use a shorter sentence, selecting instead the first two letters in each word, when they have more than just one letter: “Ashse,bunese.” As long as you don’t use a published sentence, the passwords generated by this approach can be as strong as you want.
Nice article but I’ll pick a few nits, being a security professional…
Any passwords less that 12 characters are horribly insecure, so take out all the above that generate weak passwords. Even the 12 character minimum does not provide sufficient entropy and is antiquated. Any generator generating monkey on a keyboard strings is immediately suspect and should not be used.
The xkcd example is the only good one I saw here. I’ve added that to my systems [THX. ]. Xkcd had it exactly right. But it’s only a start. Add mixed case, numbers, punctuation, and some deliberate mispeelings, and you’ve got something there. But it’s a great start and the only one that I liked here. The rest of them seem to be so last century.
The shuf example in the comments was good, I hadn’t thought about using that with /usr/share/dict/words and I only used the IETF OPIE lexicon of 2048 words in a home grown effort over a decade ago (that how old some of this stuff is). But the shuf example is overburdened with excessive “tr” dross. You want punctuation and you want mixed case. Why would you want to weaken your passwords? I have a full rich mix of uppercase, lowercase, numbers, and punctuations in all my passwords and I use a generator like my own or the xkcd example as a starting point to then “enrich them” with additional camel case and numbers (1337 sp33k) and punctuation and mispeeling (sic).
By far, the largest threat to passwords is PASSWORD REUSE. This is fine if this is your only password to your only system and you never register with web sites. I have over 10,000 passwords (I am NOT exaggerating here) in my KeyPassXC database. KeyPass / KeyPassX / KeyPassXC / KeyPassDroid all support an encryption seed file as well as a password. Make that password long and tough. Put that password into a hardware token like YubKey (2 slots) or OnlyKey (24 slots in 2 profiles with a self destruct PIN). Only unlock your password database with your hardware token. Then make every password different and store it in your password safe. Then, if someone cracks your system, they don’t have your key. If someone cracks a web site with your password, it won’t work anywhere else. Only think I wish the KeyPass / KeyPassX / KeyPassXC / KeyPassDroid (and others) would add would be an xkcd generator to their password generators. Even then, they fill in a suggested password that you can (and should) modify yourself to enrich the complexity. If you use a password manager, most have a decent generator built-in.
I found the last recommendation in this article to “memorize the password and delete it from your system. It is much better just in case your system is compromised” to be totally inappropriate anything but the most trivial of circumstances as it naturally inclines you to use password reuse to cut down on the number of passwords you have to remember and thus compromising them all.
I personally use a OnlyKey for my login to my systems and for unlocking my KeyPassXC database and unlocking my FireFox Secure Service Container (SSC).
You can install xkcdpass on Fedora and other RPM derivatives using this (obviously you need pip but that’s in the repos):
Источник