- How to sudo without password on CentOS Linux
- Run sudo without password on CentOS Linux
- How to execute ALL sudo commands without password on CentOS
- Conclusion
- How to run sudo command without a password on a Linux or Unix
- How to to run sudo command without a password:
- How do I execute ALL sudo commands without password?
- How do I test it?
- Conclusion
- How to Run ‘sudo’ Command Without Entering a Password in Linux
- If You Appreciate What We Do Here On TecMint, You Should Consider:
- How to Run sudo Commands Without Password
- Execute all sudo commands without password [not recommended]
- Why use visudo for editing sudoer file?
- Run only specific sudo commands without password
- How do I run specific sudo commands without a password?
- 2 Answers 2
- Use the NOPASSWD directive
- Using /etc/sudoers.d instead of modifying /etc/sudoers
- If sudoers is messed up
How to sudo without password on CentOS Linux
Run sudo without password on CentOS Linux
- Backup /etc/sudoers file, run:
sudo cp /etc/sudoers /root/sudoers.bak - Edit the /etc/sudoers file on CentOS:
sudo visudo - Run /usr/sbin/rebootcommand without password on CentOS:
marlena ALL = NOPASSWD: /usr/bin/reboot - Save and exit the file.
How to execute ALL sudo commands without password on CentOS
Type the following command as root user:
# visudo
Or
$ sudo visudo
Append the following entry to run ALL command without a password for a user named marlena:
Save and close the file in vim. It is also possible to grant access to the group name such as sysadm. Any member of sysadm group can run command without a password. The syntax is
Of course, you can force the sysadm group to run only given commands such as /usr/sbin/reboot and systemctl:
- No ads and tracking
- In-depth guides for developers and sysadmins at Opensourceflare✨
- Join my Patreon to support independent content creators and start reading latest guides:
- How to set up Redis sentinel cluster on Ubuntu or Debian Linux
- How To Set Up SSH Keys With YubiKey as two-factor authentication (U2F/FIDO2)
- How to set up Mariadb Galera cluster on Ubuntu or Debian Linux
- A podman tutorial for beginners – part I (run Linux containers without Docker and in daemonless mode)
- How to protect Linux against rogue USB devices using USBGuard
Join Patreon ➔
Here is my sample config file:
Conclusion
You learned how to run ‘sudo’ command without entering a password in CentOS Linux using various configuration options. For more information see sudo command man page here.
🐧 Get the latest tutorials on Linux, Open Source & DevOps via
Источник
How to run sudo command without a password on a Linux or Unix
I ‘m a new Unix system user. How do I use sudo command without a password on a Linux or Unix-like systems? I log in as tom@my-cloud-server-ip and disabled root login for ssh. After login, I need to run some commands as root user. I am the only sysadmin using my server. How do I run or execute sudo command without a password for a user named Tom under Debian/Ubuntu/CentOS Linux cloud server?
sudo (“superuser do”) is nothing but a tool for Linux or Unix-like systems to run commands/programs as another user. Typically as a root user or another user. You can delegate common tasks such as reboot the server or restart the Apache or make a backup using sudo for unprivileged users. By default, sudo needs that a user authenticates using a password before running a command. Some times you may need to run a command with root privileges, but you do not want to type a password using sudo command. This is useful for scripting or any other purpose. This can be achieved by editing /etc/sudoers file and setting up correct entries. You need to consider any security consequence of allowing a sudo command execute without a password.
| Tutorial details | |
|---|---|
| Difficulty level | Easy |
| Root privileges | Yes |
| Requirements | sudo on Linux or Unix/BSD/macOS |
| Est. reading time | 3 mintues |
NOTE: Initial setup must be done using the root account. One can gain root access by directly log in as root using console, ssh, or su command:
su —
In all cases, you must know the root password in advance before sudo can be configured to commands without a password. You might have sudo access and grant another user account passwordless access for commands.
How to to run sudo command without a password:
- Gain root access: su —
- Backup your /etc/sudoers file by typing the following command:
cp /etc/sudoers /root/sudoers.bak - Edit the /etc/sudoers file by typing the visudo command:
visudo - Append/edit the line as follows in the /etc/sudoers file for user named ‘vivek’ to run ‘/bin/kill’ and ‘systemctl’ commands:
vivek ALL = NOPASSWD: /bin/systemctl restart httpd.service, /bin/kill - Save and exit the file.
How do I execute ALL sudo commands without password?
Type the following command as root user:
# visudo
Or if you have sudo access and want to grant another user permission, try:
$ sudo visudo
Append the following entry to run ALL command without a password for a user named tom:
- No ads and tracking
- In-depth guides for developers and sysadmins at Opensourceflare✨
- Join my Patreon to support independent content creators and start reading latest guides:
- How to set up Redis sentinel cluster on Ubuntu or Debian Linux
- How To Set Up SSH Keys With YubiKey as two-factor authentication (U2F/FIDO2)
- How to set up Mariadb Galera cluster on Ubuntu or Debian Linux
- A podman tutorial for beginners – part I (run Linux containers without Docker and in daemonless mode)
- How to protect Linux against rogue USB devices using USBGuard
Join Patreon ➔
Here is my sample config file:
Fig.01: How to execute sudo without password for tom user
How do I test it?
Simply run /bin/kill to kill any process without a password:
[vivek@server ]$ sudo /bin/kill pid-here
OR
[vivek@server ]$ sudo /bin/systemctl restart httpd.service
Conclusion
You learned how to run a command without a password when using sudo on Linux or Unix-like systems. There is a significant security risk associated with passwordless operations. Hence, I would strongly recommend NOT doing this, but as they say, “it is not UNIX’s job to stop you from shooting your foot. If you so choose to do so, then UNIX’s job is to deliver Mr. Bullet to Mr. Foot in the most efficient way it knows.” For more info read man pages:
visudo(8)
🐧 Get the latest tutorials on Linux, Open Source & DevOps via
Источник
How to Run ‘sudo’ Command Without Entering a Password in Linux
In case you are running Linux on a machine that you normally use alone, say on a laptop, entering a password each time you invoke sudo can become so boring in the long run. Therefore, in this guide, we will describe how to configure sudo command to run without entering a password.
This setting is done in the /etc/sudoers file, which drives sudoers to use default security policy plugin for the sudo command; under the user privilege specification section.
Important: In the sudeors file, the authenticate parameter which is turned on by default is used for authentication purposes. If it is set, users must authenticate themselves via a password (or other means of authentication) before they run commands with sudo.
However, this default value may be overridden using the NOPASSWD (require no password when user invokes sudo command) tag.
The syntax to configure user privileges is as follows:
- user_list – list of users or a user alias that has already been set.
- host_list – list of hosts or a host alias on which users can run sudo.
- effective_user_list – list of users they must be running as or a run as alias.
- tag_list – list of tags such as NOPASSWD.
- command_list – list of commands or a command alias to be run by user(s) using sudo.
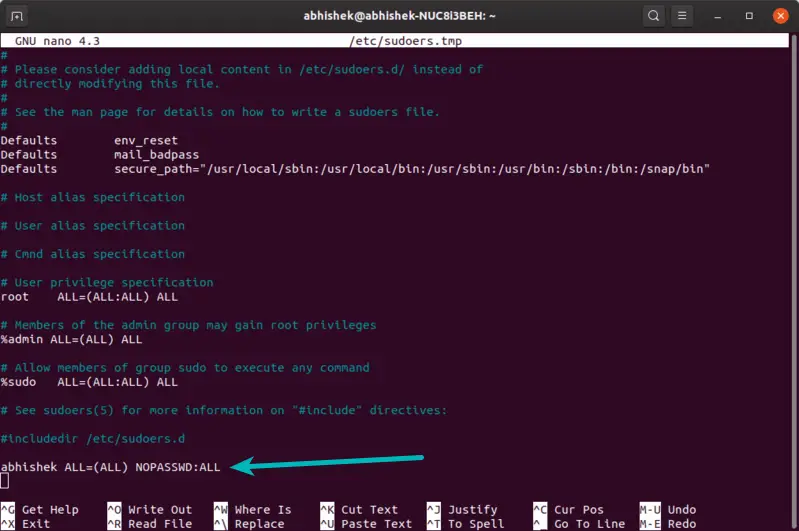
To allow a user ( aaronkilik in the example below) to run all commands using sudo without a password, open the sudoers file:
And add the following line:
For the case of a group, use the % character before the group name as follows; this means that all member of the sys group will run all commands using sudo without a password.
To permit a user to run a given command ( /bin/kill ) using sudo without a password, add the following line:
The line below will enable member of the sys group to run the commands: /bin/kill, /bin/rm using sudo without a password:

For more sudo configuration and additional usage options, read our articles that describes more examples:
In this article, we described how to configure sudo command to run without entering a password. Do not forget to offer us your thoughts about this guide or other useful sudeors configurations for Linux system administrators all in the comments.
If You Appreciate What We Do Here On TecMint, You Should Consider:
TecMint is the fastest growing and most trusted community site for any kind of Linux Articles, Guides and Books on the web. Millions of people visit TecMint! to search or browse the thousands of published articles available FREELY to all.
If you like what you are reading, please consider buying us a coffee ( or 2 ) as a token of appreciation.
We are thankful for your never ending support.
Источник
How to Run sudo Commands Without Password
Learn how to run some or all sudo commands without entering the password on Ubuntu or any other Linux distribution.
Most Linux distributions like Ubuntu, Debian, Fedora use the sudo mechanism to allow admin users to run commands with root privileges.
When you run a command with sudo, it asks for your account’s password. The default timeout for the password is 15 minutes (in Ubuntu Linux). Which means that you’ll have to enter the password again if you run a command with sudo after fifteen minutes.
Some users may find it cumbersome to enter the password all the time. This is specially if you are the only user on the system or if you think some commands are okay to run without password.
In Linux, you can change sudo configuration to run some or all command with sudo but without entering password.
If you are on a server, you should be extra careful specially if you have SSH enabled. Maybe, you should disable SSH access with password first.
Let’s see how to use sudo with no password.
But first, back up the sudoer file as a precautionary measure:
Execute all sudo commands without password [not recommended]
Use the following command to edit the /etc/sudoers file:
This will open the default text editor (Nano in Ubuntu) for editing this file. All you have to do is to add a line like this in this file:
Of course, you have to replace the user_name in the above command with your user name.
Exit the shell and enter again and you should see the changes reflected.
Why use visudo for editing sudoer file?
Now, you may edit /etc/sudoers file manually in a text editor like Vim, however, that is not advised.
If you make a syntax error while editing this file, the consequences can be fatal. This is why you a dedicated tool called visudo is used for editing sudo configuration file.
The visudo tool creates a new temp file where you can edit the sudoer file using the default text editor. When you try to save your changes, it performs a check and notifies if there is any syntax error.
It provides you some options to deals with the changes.
But it’s not a good practice to run all the sudo commands without password. Thankfully, there is a solution for that as well.
Run only specific sudo commands without password
You can configure sudo in a way that only commands of your choice can be run without password.
For example, if you want the apt update and apt upgrade to be run without entering the password for sudo in Ubuntu, here’s what you need to do.
Open the file for editing:
And then add a line like this:
Save the changes and you are good to go.
I hope you like this quick little tutorial about using sudo without password. Any questions or suggestions are always welcome.
Источник
How do I run specific sudo commands without a password?
On one particular machine I often need to run sudo commands every now and then. I am fine with entering password on sudo in most of the cases.
However there are three sudo commands I want to run without entering password:
- sudo reboot
- sudo shutdown -r now
- sudo shutdown -P now
How can I exclude these commands from password protection to sudo ?
2 Answers 2
Use the NOPASSWD directive
You can use the NOPASSWD directive in your /etc/sudoers file.
If your user is called user and your host is called host you could add these lines to /etc/sudoers :
This will allow the user user to run the desired commands on host without entering a password. All other sudo ed commands will still require a password.
The commands specified in the sudoers file must be fully qualified (i.e. using the absolute path to the command to run) as described in the sudoers man page. Providing a relative path is considered a syntax error.
If the command ends with a trailing / character and points to a directory, the user will be able to run any command in that directory (but not in any sub-directories therein). In the following example, the user user can run any command in the directory /home/someuser/bin/ :
Note: Always use the command visudo to edit the sudoers file to make sure you do not lock yourself out of the system – just in case you accidentally write something incorrect to the sudoers file. visudo will save your modified file to a temporary location and will only overwrite the real sudoers file if the modified file can be parsed without errors.
Using /etc/sudoers.d instead of modifying /etc/sudoers
As an alternative to editing the /etc/sudoers file, you could add the two lines to a new file in /etc/sudoers.d e.g. /etc/sudoers.d/shutdown . This is an elegant way of separating different changes to the sudo rights and also leaves the original sudoers file untouched for easier upgrades.
Note: Again, you should use the command visudo to edit the file to make sure you do not lock yourself out of the system:
This also automatically ensures that the owner and permissions of the new file is set correctly.
If sudoers is messed up
If you did not use visudo to edit your files and then accidentally messed up /etc/sudoers or messed up a file in /etc/sudoers.d then you will be locked out of sudo .
The solution could be to fix the files using pkexec which is an alternative to sudo .
To fix /etc/sudoers :
To fix /etc/sudoers.d/shutdown :
If the ownership and/or permissions are incorrect for any sudoers file, the file will be ignored by sudo so you might also find yourself locked out in this situation. Again, you can use pkexec to fix this.
The correct permissions should be like this:
Use pkexec like this to fix ownership and permissions:
Источник