- Using Linux Syscalls in C Programming
- Brief Intro to Syscalls
- Programming with Syscalls
- Example Syscall Usage
- Linux system call from с
- Table of Contents (template)
- 1. Introduction
- 2. System call in depth
- 3. Linux/i386 system calls
- 4. References
- 1. Introduction
- 2. System call in depth
- 3. Linux/i386 system calls
- Complete list of system calls with description
- 0. sys_setup
- 1. sys_exit
- 2. sys_fork
- 3. sys_read
- 4. sys_write
- 5. sys_open
- 6. sys_close
- 7. sys_waitpid
- 8. sys_creat
- 9. sys_link
- 10. sys_unlink
- 11. sys_execve
- 12. sys_chdir
- 13. sys_time
- 14. sys_mknod
- 15. sys_chmod
- 16. sys_lchown
- 17. sys_break
- 18. sys_oldstat
- 19. sys_lseek
- 20. sys_getpid
- 21. sys_mount
- 22. sys_umount
- 23. sys_setuid
- 24. sys_getuid
- 25. sys_stime
- 26. sys_ptrace
- 27. sys_alarm
- 28. sys_oldfstat
- 29. sys_pause
- 30. sys_utime
- Linux Exec System Call
- Why exec is used?
- Inner Working of exec
- Syntaxes of exec family functions:
- Description:
- Example 1: Using exec system call in C program
- example.c
- hello.c
- Difference between fork() and exec() system calls:
- Example 2: Combining fork() and exec() system calls
Using Linux Syscalls in C Programming
This topic was published by DevynCJohnson and viewed 2701 times since » January 02, 2016 @ 15:46EST «. The last page revision was » March 04, 2016 @ 07:57EST «.
The Linux kernel has many system calls (syscalls) that perform low-level tasks. These system calls can be used as functions when writing programs that perform a low-level task or retrieve information from the kernel and other important processes. It may help some Linux users to understand how to implement syscalls in their programming.
Brief Intro to Syscalls
A system call is a special function/command that a program uses to communicate with the kernel of the operating system. The Linux kernel has a variety of system calls that it recognizes. There are about six kinds of system calls (depending on how you want to classify them). These six are process control, information maintenance, communication, file management, memory management, and device management. «Information maintenance» is referring to system time, attributes of files and devices, and many other sets of information. «Communication» refers to networking, data transfer, attachment/detachment of remote devices.
When an application is compiled on Linux, it gets the code for the standard system calls from the GNU C Library, which is also called «glibc». This is the library used for applications that run on systems using the Linux kernel, Hurd kernel, or GNU userland. Some derivatives of glibc are used in applications running on other kernels. One reason why applications compiled for one operating system do not work on another is because the application uses different system calls.
Programming with Syscalls
When writing a program in C or some other programming language, it is important to know that programs should not use a real system call directly. Rather, system calls should use a wrapper, such as libc (glibc). When using wrappers, the system call commands will use the same parameters as the real kernel system calls.
In C-programming, the library that provides access to syscalls is » » which is obtain from the «Kernel headers» package. This C library provides wrappers for using the syscall. Once the program is compiled and working, it does not initiate the syscalls directly. Instead, the program uses functions from the libc library.
When programming syscalls in applications, it is best to view the man-pages to know the parameters and data-types associated with the syscall. To lookup a system call in the man-pages via command-line, type «man 2 SYSCALL» where «SYSCALL» is the name of the system call that will be used. The «2» indicates that the syscall portion of the man-pages will be searched for the desired syscall. Once the man-page is found, information about the syscalls parameters, parameter data-types, data-type of output, and programming notes will be seen and should be read carefully. If the man-page does not provide enough information (or none at all), then check the Internet for the needed information.
Example Syscall Usage
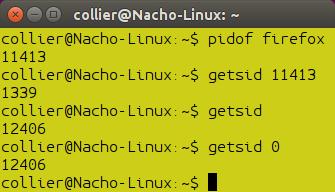
The best way to learn how to use a syscall is by seeing a simple yet useful and real example. I made a small command-line program using the C programming language. This program returns the Session ID (SID) of the specified Process ID (PID). The Session ID is retrieved by the «getsid()» syscall.
NOTE: The below code will only work on Linux. Windows and many other operating systems do not have the «getsid()» syscall.
The compiled executable is used in a command-line and uses a PID as an argument (getsid PID). The command then returns the Session ID of the specified PID. If no PID is specified, then a PID of «0» is assumed.
NOTE: The official download page for the «getsid» command-line utility is http://dcjtech.info/topic/getsid-get-session-id-utility/. That page also includes compilation and installation instructions.
The » «, » «, and » » are needed to use the «getsid» syscall. Some system calls (like «statvfs») need different libraries, so be sure to research the needed libraries for the desired syscall. The «pid_t» data-type is a signed integer that is used for Process IDs, Session IDs, Parent Process Ids, and possibly some other IDs. Integers (int) and «pid_t» data can be type-casted between each other easily.
To use «getsid», the syscall must be initialized and its return value and parameters must have their data-types properly declared ( pid_t getsid(pid_t pid); ). After the syscall is initialized, it can be used as a function («sid = getsid(pid);»). In that line of code, the Session ID of the specified PID (pid) is returned by the syscall (technically a syscall wrapper) and stored in the variable «sid».
As mentioned before, some syscalls may use different libraries and the syscall itself may need to be initialized in some special way. For instance, to use the «statvfs» system call, the library » » is needed, but not » «, » «, or » «. In addition, the buffer used by statvfs must be declared («struct statvfs buf;»). When statvfs is executed as a function/command, the data is stored in «buf». When running «statvfs», the output is the return-status code. For example, to use «statvfs», the initialization code is «int statvfs(const char *path, struct statvfs *buf);» and «statvfs» is executed as «ret = statvfs(path,&buf);». To get the filesystem data retrieved by statvfs, access the «buf» variable in a form like «buf.f_bsize» to get the block size. To output such a value in a command-line, the printf command could be used — printf(«Block Size (bytes): %ld\n», buf.f_bsize);
Obviously, when using syscalls, it is very important to view documentation about the desired syscall and understand the data-types and required libraries.
Источник
Linux system call from с
Copyright (C) 1999-2000 by Konstantin Boldyshev
This list is NOT READY and is under heavy construction, a lot of entries are missing, and some may be incorrect. This is more a template than a real document. Meanwhile, I suggest you to examine this list by H-Peter Recktenwald.
Table of Contents (template)
1. Introduction
2. System call in depth
- 2.1 What is system call?
2.2 View from the Kernel side
2.3 View from the userland
2.4 Using system calls
3. Linux/i386 system calls
4. References
1. Introduction
First of all note that these are not libc «system calls», but real system calls provided by Linux Kernel.
List is intended to cover Linux 2.4 / 2.2 / 2.0.
2. System call in depth
3. Linux/i386 system calls
All system calls introduced/removed in specific Linux version are marked with (VER+/-) label (f.e. 2.2+ means that this call was introduced in Linux 2.2, and is missing in Linux 2.0). Square brackets hold real kernel name of system call from arch/i386/kernel/entry.S (as appeared in Syntax), if it differs from «official» in include/asm-i386/unistd.h.
Complete list of system calls with description
0. sys_setup
Syntax: int sys_setup(void)
Action: return -ENOSYS on Linux 2.2
Details: old sys_setup call
1. sys_exit
Syntax: int sys_exit(int status)
Action: terminate the current process
Details: status is return code
2. sys_fork
Syntax: int sys_fork()
Action: create a child process
3. sys_read
Syntax: ssize_t sys_read(unsigned int fd, char * buf, size_t count)
Action: read from a file descriptor
4. sys_write
Syntax: ssize_t sys_write(unsigned int fd, const char * buf, size_t count)
Action: write to a file descriptor
5. sys_open
Syntax: int sys_open(const char * filename, int flags, int mode)
Action: open and possibly create a file or device
6. sys_close
Syntax: sys_close(unsigned int fd)
Action: close a file descriptor
7. sys_waitpid
Syntax: int sys_waitpid(pid_t pid,unsigned int * stat_addr, int options)
Action: wait for process termination
8. sys_creat
Syntax: int sys_creat(const char * pathname, int mode)
Action: create a file or device
9. sys_link
Syntax: int sys_link(const char * oldname, const char * newname)
Action: make a new name for a file
10. sys_unlink
Syntax: int sys_unlink(const char * pathname)
Action: delete a name and possibly the file it refers to
11. sys_execve
Syntax: int sys_execve(struct pt_regs regs)
Action: execute program
12. sys_chdir
Syntax: int sys_chdir(const char * filename)
Action: change working directory
13. sys_time
Syntax: int sys_time(int * tloc)
Action: get time in seconds
14. sys_mknod
Syntax: int sys_mknod(const char * filename, int mode, dev_t dev)
Action: create a directory or special or ordinary file
15. sys_chmod
Syntax: int sys_chmod(const char * filename, mode_t mode)
Action: change permissions of a file
16. sys_lchown
Syntax: int sys_lchown(const char * filename, uid_t user, gid_t group)
Action: change ownership of a file
17. sys_break
Syntax: int sys_break()
Action: return -ENOSYS
Details: call exists only for compatibility
18. sys_oldstat
Syntax: int sys_stat(char * filename, struct __old_kernel_stat * statbuf)
19. sys_lseek
Syntax: off_t sys_lseek(unsigned int fd, off_t offset, unsigned int origin)
Action: reposition read/write file offset
20. sys_getpid
Syntax: int sys_getpid(void)
Action: get process identification
21. sys_mount
Syntax: int sys_mount(char * dev_name, char * dir_name, char * type, unsigned long new_flags, void * data)
Action: mount filesystems
22. sys_umount
Syntax: int sys_oldumount(char * name)
Action: unmount filesystem
23. sys_setuid
Syntax: int sys_setuid(uid_t uid)
Action: set user identity
24. sys_getuid
Syntax: int sys_getuid(void)
Action: get user identity
25. sys_stime
Syntax: int sys_stime(int * tptr)
Action: set time
26. sys_ptrace
Syntax: int sys_ptrace(long request, long pid, long addr, long data)
Action: process trace
27. sys_alarm
Syntax: unsigned int sys_alarm(unsigned int seconds)
Action: set an alarm clock for delivery of a signal
28. sys_oldfstat
Syntax: int sys_fstat(unsigned int fd, struct __old_kernel_stat * statbuf)
29. sys_pause
Syntax: int sys_pause(void)
Action: wait for signal
30. sys_utime
Syntax: int sys_utime(char * filename, struct utimbuf * times)
Action: change access and/or modification times of an inode
Источник
Linux Exec System Call
The exec system call is used to execute a file which is residing in an active process. When exec is called the previous executable file is replaced and new file is executed.
More precisely, we can say that using exec system call will replace the old file or program from the process with a new file or program. The entire content of the process is replaced with a new program.
The user data segment which executes the exec() system call is replaced with the data file whose name is provided in the argument while calling exec().
The new program is loaded into the same process space. The current process is just turned into a new process and hence the process id PID is not changed, this is because we are not creating a new process we are just replacing a process with another process in exec.
If the currently running process contains more than one thread then all the threads will be terminated and the new process image will be loaded and then executed. There are no destructor functions that terminate threads of current process.
PID of the process is not changed but the data, code, stack, heap, etc. of the process are changed and are replaced with those of newly loaded process. The new process is executed from the entry point.
Exec system call is a collection of functions and in C programming language, the standard names for these functions are as follows:
It should be noted here that these functions have the same base exec followed by one or more letters. These are explained below:
e: It is an array of pointers that points to environment variables and is passed explicitly to the newly loaded process.
l: l is for the command line arguments passed a list to the function
p: p is the path environment variable which helps to find the file passed as an argument to be loaded into process.
v: v is for the command line arguments. These are passed as an array of pointers to the function.
Why exec is used?
exec is used when the user wants to launch a new file or program in the same process.
Inner Working of exec
Consider the following points to understand the working of exec:
- Current process image is overwritten with a new process image.
- New process image is the one you passed as exec argument
- The currently running process is ended
- New process image has same process ID, same environment, and same file descriptor (because process is not replaced process image is replaced)
- The CPU stat and virtual memory is affected. Virtual memory mapping of the current process image is replaced by virtual memory of new process image.
Syntaxes of exec family functions:
The following are the syntaxes for each function of exec:
Description:
The return type of these functions is Int. When the process image is successfully replaced nothing is returned to calling function because the process that called it is no longer running. But if there is any error -1 will be returned. If any error is occurred an errno is set.
- pathis used to specify the full path name of the file which is to be executes.
- argis the argument passed. It is actually the name of the file which will be executed in the process. Most of the times the value of arg and path is same.
- const char* argin functions execl(), execlp() and execle() is considered as arg0, arg1, arg2, …, argn. It is basically a list of pointers to null terminated strings. Here the first argument points to the filename which will be executed as described in point 2.
- envpis an array which contains pointers that point to the environment variables.
- file is used to specify the path name which will identify the path of new process image file.
- The functions of exec call that end with e are used to change the environment for the new process image. These functions pass list of environment setting by using the argument envp. This argument is an array of characters which points to null terminated String and defines environment variable.
To use the exec family functions, you need to include the following header file in your C program:
Example 1: Using exec system call in C program
Consider the following example in which we have used exec system call in C programming in Linux, Ubuntu: We have two c files here example.c and hello.c:
example.c
CODE:
hello.c
CODE:
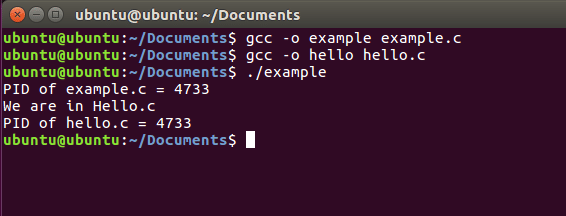
OUTPUT:
In the above example we have an example.c file and hello.c file. In the example .c file first of all we have printed the ID of the current process (file example.c is running in current process). Then in the next line we have created an array of character pointers. The last element of this array should be NULL as the terminating point.
Then we have used the function execv() which takes the file name and the character pointer array as its argument. It should be noted here that we have used ./ with the name of file, it specifies the path of the file. As the file is in the folder where example.c resides so there is no need to specify the full path.
When execv() function is called, our process image will be replaced now the file example.c is not in the process but the file hello.c is in the process. It can be seen that the process ID is same whether hello.c is process image or example.c is process image because process is same and process image is only replaced.
Then we have another thing to note here which is the printf() statement after execv() is not executed. This is because control is never returned back to old process image once new process image replaces it. The control only comes back to calling function when replacing process image is unsuccessful. (The return value is -1 in this case).
Difference between fork() and exec() system calls:
The fork() system call is used to create an exact copy of a running process and the created copy is the child process and the running process is the parent process. Whereas, exec() system call is used to replace a process image with a new process image. Hence there is no concept of parent and child processes in exec() system call.
In fork() system call the parent and child processes are executed at the same time. But in exec() system call, if the replacement of process image is successful, the control does not return to where the exec function was called rather it will execute the new process. The control will only be transferred back if there is any error.
Example 2: Combining fork() and exec() system calls
Consider the following example in which we have used both fork() and exec() system calls in the same program:
Источник