- How to Switch (su) to Another User Account without Password
- 1. Using PAM Authentication Module
- 2. Using Sudoers File
- If You Appreciate What We Do Here On TecMint, You Should Consider:
- How to create a user without password in Linux
- What is passwd command?
- What is useradd command?
- Method-1: Creating a user without password using passwd command
- Method-1.a: Using passwd comamnd
- Method-2: Creating a user without password using chpasswd command
- Method-3: Creating a user without password using useradd command
- Method-3.a: Using /sbin/nologin shell
- Method-3.b: Changing the shell to false
- Method-3.c: Changing the shell to /dev/null
- Closing Notes
- How to run sudo command without a password on a Linux or Unix
- How to to run sudo command without a password:
- How do I execute ALL sudo commands without password?
- How do I test it?
- Conclusion
- How to Run sudo Commands Without Password
- Execute all sudo commands without password [not recommended]
- Why use visudo for editing sudoer file?
- Run only specific sudo commands without password
How to Switch (su) to Another User Account without Password
In this guide, we will show how to switch to another or a specific user account without requiring a password. For example, we have a user account called postgres (the default PostgreSQL superuser system account), we want every user (typically our PostgreSQL database and system administrators) in the group called postgres to switch to the postgres account using the su command without entering a password.
By default, only the root user can switch to another user account without entering a password. Any other user will be prompted to enter the password of the user account they are switching to (or if they are using the sudo command, they will be prompted to enter their password), if they don’t provide the correct password, they get an “authentication failed” error as shown in the following screenshot.

You can use any of the two solutions provided below to solve the above issue.
1. Using PAM Authentication Module
PAM (Pluggable authentication modules) are at the core of user authentication on modern Linux operating systems. To allow users in a specific group to switch to another user account without a password, we can modify the default PAM settings for the su command in the /etc/pam.d/su file.
Add the following configurations after “auth sufficient pam_rootok.so” as shown in the following screenshot.
In the above configuration, the first line checks if the target user is postgres, if it is, the service checks the current user, otherwise, the default=1 line is skipped and the normal authentication steps are executed.
The line that follows checks if the current user is in the group postgres, if yes , the authentication process is considered successful and returns sufficient as a result. Otherwise, the normal authentication steps are executed.

Save the file and close it.
Next, add the user (for example aaronk) that you want to su to the account postgres without a password to the group postgres using usermod command.
Now try to su to the postgres account as the user aaronk, you should not be prompted for a password as shown in the following screenshot:

2. Using Sudoers File
You can also su to another user without requiring a password by making some changes in the sudoers file. In this case, the user (for example aaronk) who will switch to another user account (for example postgres) should be in the sudoers file or in the sudo group to be able to invoke the sudo command.
Then add the following configuration below the line “%sudo ALL=(ALL:ALL) ALL” as shown in the following screenshot.

Save and close the file.
Now try to su to the account postgres as the user aaronk, the shell should not prompt you to enter a password:

That’s all for now! For more information, see the PAM manual entry page (man pam.conf) and that of sudo command as well (man sudo).
If You Appreciate What We Do Here On TecMint, You Should Consider:
TecMint is the fastest growing and most trusted community site for any kind of Linux Articles, Guides and Books on the web. Millions of people visit TecMint! to search or browse the thousands of published articles available FREELY to all.
If you like what you are reading, please consider buying us a coffee ( or 2 ) as a token of appreciation.
We are thankful for your never ending support.
Источник
How to create a user without password in Linux
This article title may sound awkward to you, but it’s useful. You may ask, why would we want to create a user without a password. I thought that too, but my friend faced this question in one of the interviews.
So, I want to share this with users who are looking for an answer to this question. Practically it may not be useful, but you should know the answer.
This article shows you how to create a user account without a password OR an empty password on Linux.
What is passwd command?
The passwd command is one of the most frequently used command by Linux administrator’s to update users’ authentication tokens in the /etc/shadow file by calling the Linux-PAM and Libuser API’s.
What is useradd command?
Linux is a multi-user operating system that allows more than one user to interact with the system at the same time. The “useradd” command is used to create new user accounts. When executed, “useradd” command creates a new user account as per the options specified in the ‘/etc/default/useradd file’ & ‘/etc/login.defs’ file.
Now let’s delve into some of the methods used to create a user account without password:
Method-1: Creating a user without password using passwd command
You can create a user without a password on Linux using the “passwd” command as follows :
Run the useradd command to create a user account as shown in the example below.
Note: we can use the commands “useradd” or “adduser” interchangeably to create a user in Linux.
useradd is native binary compiled with the system. But, adduser is a perl script which uses useradd binary in back-end. adduser is more user friendly and interactive than its back-end useradd. There’s no difference in features provided.
Once you have created the user, use the passwd command to remove the user’s password.
Details:
- -f or —force Force operation
- -u or —unlock Unlock the password for the named account (root only)
Method-1.a: Using passwd comamnd
Alternatively, you can use the -d option with the passwd command to remove the password for a user.
Details:
- -d or —delete Delete the password for the named account (root only)
Now, you’ve created a user with “disabled password”. But when you try to access it, it will ask for the password at the same time not allowing you to login.
You might get an error message saying “Access denied”.
That’s the expected behavior and you will not receive an error message such as “No password, you cannot login”.
Method-2: Creating a user without password using chpasswd command
You can create a user with an empty password on Linux using the “chpasswd” command.
Run the below command to create a user account:
Once you have created the user, use the below command to remove the user’s password. The -e option expects a hashed password, but you are given a simple password, which is why it is not taken.
Details:
- -e or —encrypted Supplied passwords are encrypted
Method-3: Creating a user without password using useradd command
You can create a password-free user on Linux using the “useradd” command.
The -p option expects a hashed password, but you are provided with a simple password, which is why it is not taken.
Details:
- -p or —password Encrypted password of the new account
Method-3.a: Using /sbin/nologin shell
User account can be created with the /sbin/ nologin shell option. This shell usually does not allow the user to log in to the computer.
You will receive the following message when you attempt to switch the account from the root.
Details:
- -s or —shell Login shell of the new account
Method-3.b: Changing the shell to false
We can use the /bin/false option with the “useradd” command to create a new user without password. ‘/bin/false’ is just a binary that immediately exits, returning false, when it’s called. The user logs in and immediately sees the login prompt again.
This shell works exactly like the one above, and it does not allow the user to log in to the computer.
When you try to switch the account from the root you get nothing.
Method-3.c: Changing the shell to /dev/null
‘/dev/null’ is a simple device which is implemented in software and doesn’t correspond to any hardware device on the system.
dev/null looks empty when you read from it, whereas data written to this device simply “disappears.”
User can be disabled by changing the shell to /dev/null as shown below:
Closing Notes
You learnt different ways to create a user without a password in Linux.
If you found this article helpful, please do share with your friends and spread the knowledge. Please feel free to comment below if you have any queries/concerns. We will get back to you as soon as we can. Happy learning!
Источник
How to run sudo command without a password on a Linux or Unix
I ‘m a new Unix system user. How do I use sudo command without a password on a Linux or Unix-like systems? I log in as tom@my-cloud-server-ip and disabled root login for ssh. After login, I need to run some commands as root user. I am the only sysadmin using my server. How do I run or execute sudo command without a password for a user named Tom under Debian/Ubuntu/CentOS Linux cloud server?
sudo (“superuser do”) is nothing but a tool for Linux or Unix-like systems to run commands/programs as another user. Typically as a root user or another user. You can delegate common tasks such as reboot the server or restart the Apache or make a backup using sudo for unprivileged users. By default, sudo needs that a user authenticates using a password before running a command. Some times you may need to run a command with root privileges, but you do not want to type a password using sudo command. This is useful for scripting or any other purpose. This can be achieved by editing /etc/sudoers file and setting up correct entries. You need to consider any security consequence of allowing a sudo command execute without a password.
| Tutorial details | |
|---|---|
| Difficulty level | Easy |
| Root privileges | Yes |
| Requirements | sudo on Linux or Unix/BSD/macOS |
| Est. reading time | 3 mintues |
NOTE: Initial setup must be done using the root account. One can gain root access by directly log in as root using console, ssh, or su command:
su —
In all cases, you must know the root password in advance before sudo can be configured to commands without a password. You might have sudo access and grant another user account passwordless access for commands.
How to to run sudo command without a password:
- Gain root access: su —
- Backup your /etc/sudoers file by typing the following command:
cp /etc/sudoers /root/sudoers.bak - Edit the /etc/sudoers file by typing the visudo command:
visudo - Append/edit the line as follows in the /etc/sudoers file for user named ‘vivek’ to run ‘/bin/kill’ and ‘systemctl’ commands:
vivek ALL = NOPASSWD: /bin/systemctl restart httpd.service, /bin/kill - Save and exit the file.
How do I execute ALL sudo commands without password?
Type the following command as root user:
# visudo
Or if you have sudo access and want to grant another user permission, try:
$ sudo visudo
Append the following entry to run ALL command without a password for a user named tom:
- No ads and tracking
- In-depth guides for developers and sysadmins at Opensourceflare✨
- Join my Patreon to support independent content creators and start reading latest guides:
- How to set up Redis sentinel cluster on Ubuntu or Debian Linux
- How To Set Up SSH Keys With YubiKey as two-factor authentication (U2F/FIDO2)
- How to set up Mariadb Galera cluster on Ubuntu or Debian Linux
- A podman tutorial for beginners – part I (run Linux containers without Docker and in daemonless mode)
- How to protect Linux against rogue USB devices using USBGuard
Join Patreon ➔
Here is my sample config file:
Fig.01: How to execute sudo without password for tom user
How do I test it?
Simply run /bin/kill to kill any process without a password:
[vivek@server ]$ sudo /bin/kill pid-here
OR
[vivek@server ]$ sudo /bin/systemctl restart httpd.service
Conclusion
You learned how to run a command without a password when using sudo on Linux or Unix-like systems. There is a significant security risk associated with passwordless operations. Hence, I would strongly recommend NOT doing this, but as they say, “it is not UNIX’s job to stop you from shooting your foot. If you so choose to do so, then UNIX’s job is to deliver Mr. Bullet to Mr. Foot in the most efficient way it knows.” For more info read man pages:
visudo(8)
🐧 Get the latest tutorials on Linux, Open Source & DevOps via
Источник
How to Run sudo Commands Without Password
Learn how to run some or all sudo commands without entering the password on Ubuntu or any other Linux distribution.
Most Linux distributions like Ubuntu, Debian, Fedora use the sudo mechanism to allow admin users to run commands with root privileges.
When you run a command with sudo, it asks for your account’s password. The default timeout for the password is 15 minutes (in Ubuntu Linux). Which means that you’ll have to enter the password again if you run a command with sudo after fifteen minutes.
Some users may find it cumbersome to enter the password all the time. This is specially if you are the only user on the system or if you think some commands are okay to run without password.
In Linux, you can change sudo configuration to run some or all command with sudo but without entering password.
If you are on a server, you should be extra careful specially if you have SSH enabled. Maybe, you should disable SSH access with password first.
Let’s see how to use sudo with no password.
But first, back up the sudoer file as a precautionary measure:
Execute all sudo commands without password [not recommended]
Use the following command to edit the /etc/sudoers file:
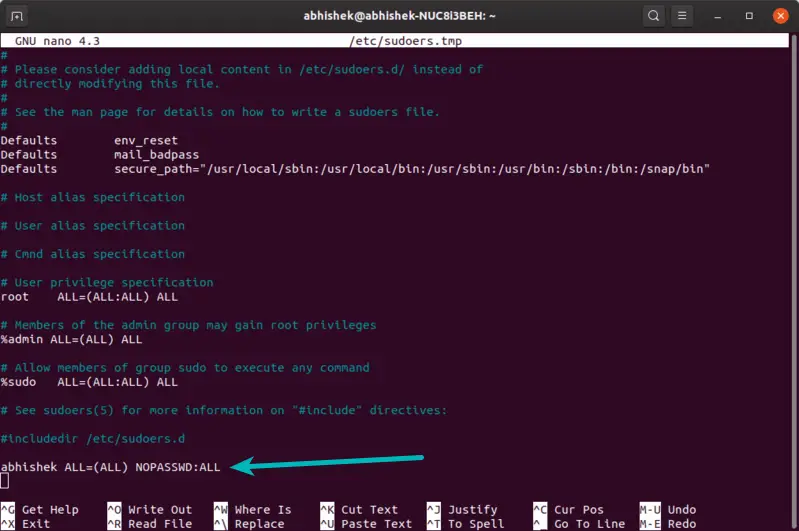
This will open the default text editor (Nano in Ubuntu) for editing this file. All you have to do is to add a line like this in this file:
Of course, you have to replace the user_name in the above command with your user name.
Exit the shell and enter again and you should see the changes reflected.
Why use visudo for editing sudoer file?
Now, you may edit /etc/sudoers file manually in a text editor like Vim, however, that is not advised.
If you make a syntax error while editing this file, the consequences can be fatal. This is why you a dedicated tool called visudo is used for editing sudo configuration file.
The visudo tool creates a new temp file where you can edit the sudoer file using the default text editor. When you try to save your changes, it performs a check and notifies if there is any syntax error.
It provides you some options to deals with the changes.
But it’s not a good practice to run all the sudo commands without password. Thankfully, there is a solution for that as well.
Run only specific sudo commands without password
You can configure sudo in a way that only commands of your choice can be run without password.
For example, if you want the apt update and apt upgrade to be run without entering the password for sudo in Ubuntu, here’s what you need to do.
Open the file for editing:
And then add a line like this:
Save the changes and you are good to go.
I hope you like this quick little tutorial about using sudo without password. Any questions or suggestions are always welcome.
Источник