- Что такое LVFS и как его использовать?
- Что такое LVFS?
- Как использовать LVFS?
- fwupd
- Contents
- Installation
- Graphical front-ends
- Usage
- Setup for UEFI upgrade
- Prepare ESP
- Secure Boot
- Using your own keys
- Troubleshooting
- Stuck when rebooting
- No error but no upgrade on reboot
- read-only filesystem error
- UEFI ESP partition not detected or configured
- MSR plugin is failing to load
- Linux Vendor Firmware Service: We Need Your Help
- Published by
- hughsie
- 7 thoughts on “Linux Vendor Firmware Service: We Need Your Help”
Что такое LVFS и как его использовать?
Использование Linux в качестве настольной операционной системы с повседневными драйверами связано со множеством тонкостей. Вы должны учитывать, доступны ли драйверы для оборудования, которое вы хотите использовать, доступно ли программное обеспечение, которое вы хотите использовать, и совместим ли Linux со всеми различными элементами управления безопасностью, которыми вам, возможно, придется управлять, с такими вещами, как Active Directory. безраздельно властвует в корпоративном мире.
Однако есть еще кое-что, о чем мы часто забываем: прошивка. Прошивка — это программное обеспечение для оборудования, конфигурации и параметры, с которыми программное обеспечение может взаимодействовать в форме драйверов, позволяющих вам его использовать. Так ли важны обновления прошивки? Как получить обновления прошивки в Linux? Почему производители должны делать свои прошивки доступными для Linux? Это все вопросы, на которые даны ответы в этой статье о том, что такое LVFS и как его использовать.
Что такое LVFS?
LVFS или Linux Vendor Firmware Service — это программный стек, который позволяет поставщикам оборудования добавлять свои микропрограммы на веб-сайт и получать обновления микропрограмм для компьютеров Linux, использующих это оборудование. Звучит достаточно просто, правда?
Это так, но последствия более сложны, чем веб-сайт, на котором запущены cronjobs, и демон, работающий в локальных системах. В течение многих лет пользователи Linux не имели доступа к самым основным функциям микропрограмм, которые могут включать новые функции и исправлять ошибки. Благодаря LVFS пользователи Linux получают доступ к таким функциям, как DisplayPort через USB C и исправлениям для контроллера Thunderbolt на своих новых Lenovo ThinkPads.
Кроме того, LVFS показывает, какие поставщики наиболее заинтересованы в том, чтобы их оборудование хорошо работало под Linux. Если вы посмотрите на список поддерживаемых устройств , вы заметите, что крупные поставщики, такие как Lenovo и Dell, активно добавляют новые устройства в список и вносят обновления прошивки для довольно старых устройств. Лично у меня нет никаких устройств в списке, но я знаю, что степень пересечения пользователей ThinkPad и пользователей Linux довольно высока, а это означает, что они максимально приближены к первоклассному опыту.
Кроме того, это создает более полный жизненный цикл продукта для поставщиков. Dell может добавить обновления прошивки для всех ноутбуков и настольных компьютеров, подпадающих под их линейку Project Sputnik, а Lenovo может сделать то же самое для всей линейки ThinkPad и ThinkStation с установленной Linux. Это беспроигрышный вариант как для пользователей, так и для поставщиков.
Как использовать LVFS?
Существует системный демон, называемый fwupdFirmWare UPdate Daemon, который доступен в большинстве основных репозиториев. Он может быть даже предустановлен в вашей системе, что упрощает работу.
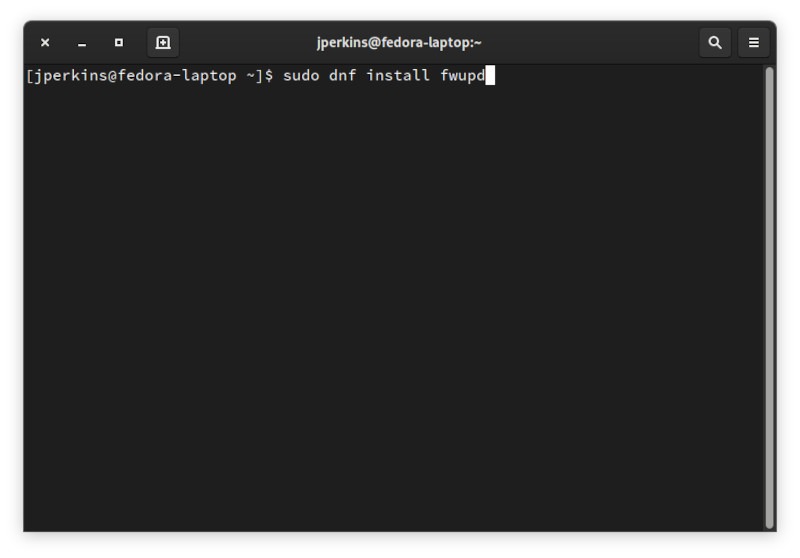
Если он не установлен, вы сможете найти имя пакета как fwupd. Если бы он не был установлен в моей системе Fedora, команда для этого была бы такой:
Вы можете заменить это менеджером пакетов в вашей текущей системе.
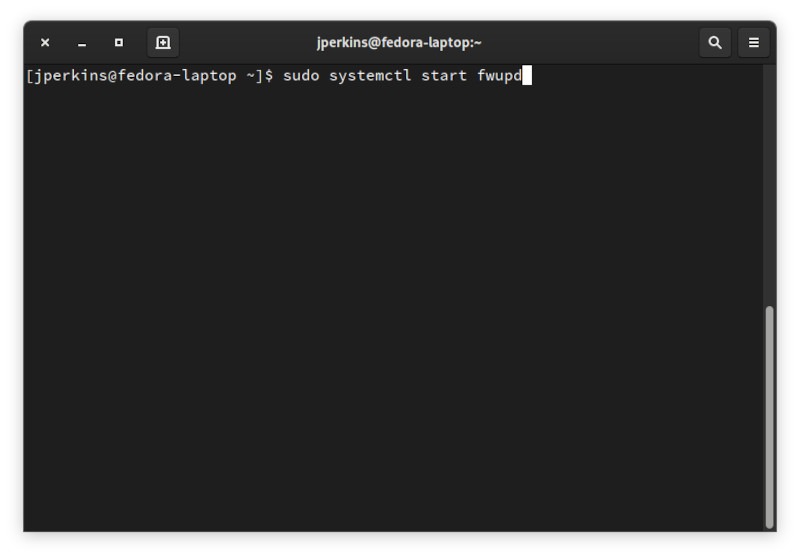
После его установки вам нужно будет запустить службу в systemd. Для этого выполните следующую команду:
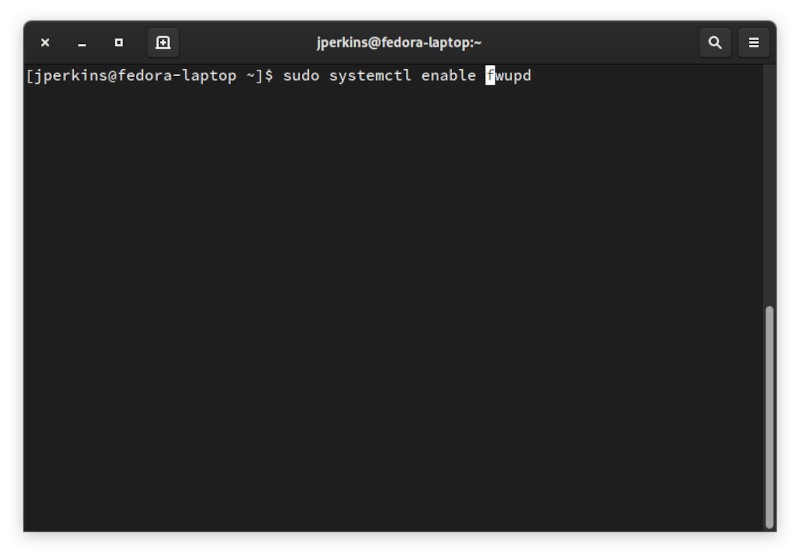
Вы также можете включить его автоматический запуск при включении вашей системы, выполнив эту команду:
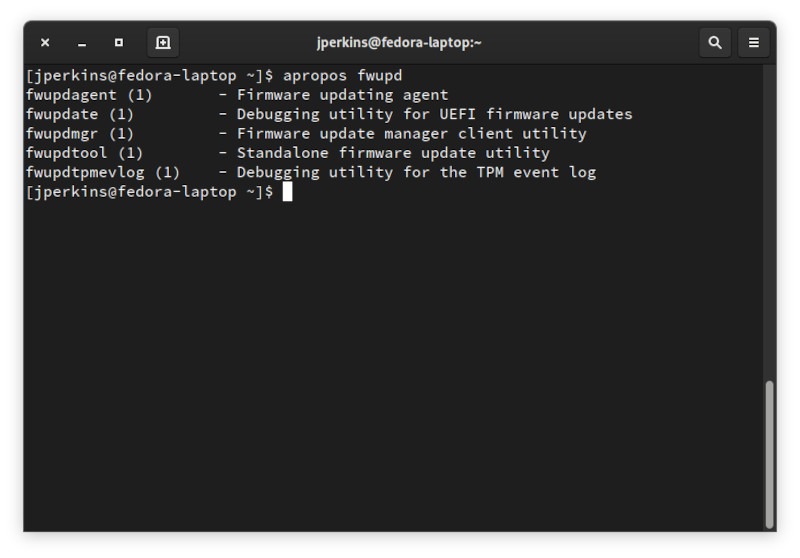
Оттуда вы можете запустить следующую команду, чтобы увидеть все параметры вашей команды, относящиеся к fwupd:
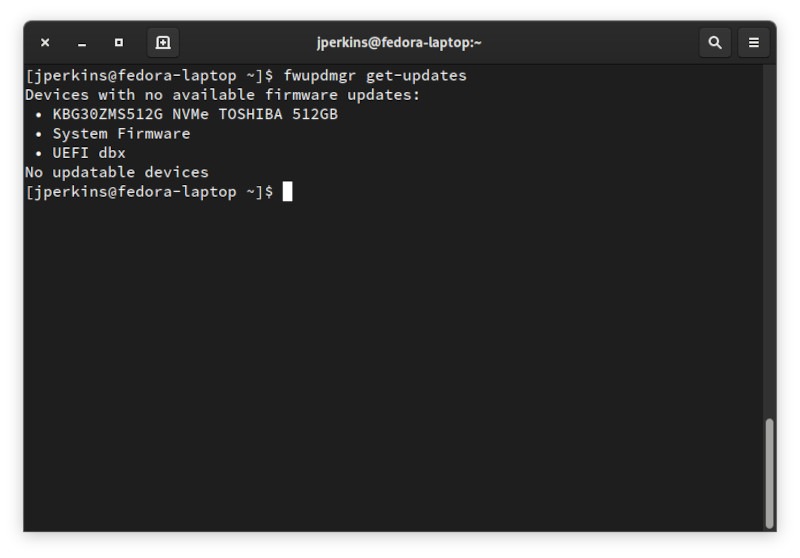
Вы обнаружите, что команда, которую вы чаще всего хотите использовать для обновления прошивки, такова:
В моей системе нет совместимых устройств, но если бы я сделал это, то fwupd мог бы творить чудеса и получать обновления.
Теперь, когда вы знаете, что такое LVFS и как его использовать, вы должны быть более уверены в создании нового ПК для вашей системы Linux.
Источник
fwupd
fwupd is a simple daemon allowing you to update some devices’ firmware, including UEFI for several machines.
Supported devices are listed here and more are to come.
Contents
Installation
See #Setup for UEFI upgrade if you intend such an use.
Graphical front-ends
Certain desktop environments front-end solutions have built-in fwupd support:
- GNOME Software — Will check for updates periodically and automatically download firmwares in the background on GNOME. After a firmware has been downloaded a popup will be displayed in Gnome Software to perform the update.
https://wiki.gnome.org/Apps/Software || gnome-software
- KDE Discover — Software center used with Plasma. With the release of KDE Plasma 5.14, a new fwupd backend has been implemented in KDE Discover for firmware updates. These firmware updates are shown with other system updates.
https://userbase.kde.org/Discover || discover
- GNOME Firmware — Application to upgrade, downgrade and reinstall firmware on devices supported by fwupd. It can unlock locked fwupd devices, verify firmware on supported devices and display all releases for a fwupd device.
https://gitlab.gnome.org/hughsie/gnome-firmware-updater || gnome-firmware
Usage
To display all devices detected by fwupd:
To download the latest metadata from the Linux Vendor firmware Service (LVFS):
To list updates available for any devices on the system:
To install updates:
Setup for UEFI upgrade
The following requirements should be met:
- Make sure you are booted in UEFI mode, it will not work in legacy boot mode.
- Verify your EFI variables are accessible.
- Mount your EFI system partition (ESP) properly. esp is used to denote the mountpoint in this section.
Prepare ESP
fwupd will copy all the necessary files over to the esp , but for this to work, a basic folder layout must be present on your esp .
This constitutes the creation of an EFI directory on your esp :
Restart the fwupd.service unit afterwards. You can now fwupdmgr refresh and fwupdmgr update . You will be prompted to reboot (into the firmware updater).
Secure Boot
Currently, fwupd relies on shim to chainload the fwupd EFI binary on systems with Secure Boot enabled. For this to work, shim has to be installed correctly.
Using your own keys
Alternatively, you have to manually sign the UEFI executable used to perform upgrades, which is located in /usr/lib/fwupd/efi/fwupdx64.efi . The signed UEFI executable is expected in /usr/lib/fwupd/efi/fwupdx64.efi.signed . Using sbsigntools , this can be achieved by running:
To automatically sign this file when installed or upgraded, a Pacman hook can be used:
Make sure to replace keyfile and certfile with the corresponding paths of your keys.
Instead of a pacman hook you can also create a symlink from /usr/lib/fwupd/efi/fwupdx64.efi to /usr/lib/fwupd/efi/fwupdx64.efi.signed and add the file to the EXTRA_SIGN list in /etc/sbupdate.conf .
Finally, you have to change the line containing DisableShimForSecureBoot in /etc/fwupd/uefi_capsule.conf to DisableShimForSecureBoot=true and restart fwupd.service .
Troubleshooting
Stuck when rebooting
fwupdmgr update reports no error, but the reboot it prompts stuck and holding the power button has no response. Try switching off the power, or press the reset button (on a laptop, it might be a hole on the back) to force-reboot.
No error but no upgrade on reboot
Symptom: fwupdmgr update reports no error and prompts for reboot (e.g., on BIOS update). However, the system reboots normally (or stuck) and the firmware update does NOT happen.
Possible cause: In BIOS settings changing the boot order must be allowed.
Possible other solution if there are multiple updates pending: Try updating packages one at a time. Use the following to select packages:
(Where update_ID is something like f95c9218acd12697af946874bfe4239587209232 .)
read-only filesystem error
At least fwupdmgr 1.5.2 deducts the wrong mount point if bind is used to mount esp to /boot [1]. Consequently it fails to write the UEFI update file to /boot/EFI/arch/fw ( fwupdmgr while it should be written to esp/EFI/arch/fw .) This results in a (misleading) «file system is read-only» error message. In case the update was performed by Discover (or any other fwupd-capable Update GUI), no error or misleading errors may be shown.
As a workaround, run umount /boot first if it was bind-mounted to esp/EFI/arch before, then run fwupdmgr update to write the UEFI update file to esp/EFI/arch/fw , mount /boot and reboot the system to perform the UEFI update.
UEFI ESP partition not detected or configured
fwupd needs udisks2 to detect the ESP. As a workaround, the mount point can also be specified manually:
Also see the relevant article in the fwupd wiki.
MSR plugin is failing to load
The MSR plugin allows querying the state of DCI, a debugging interface available for Intel CPUs that should be disabled on production machines according to fwupd’s documentation.
This plugin needs the msr kernel module loaded. msr is a built-in kernel module in all the official Arch Linux kernel packages, but unofficial kernel packages might have it as a loadable kernel module. In the latter case, we need to explicitly load it by automatically loading the msr module with systemd.
Источник
Linux Vendor Firmware Service: We Need Your Help
I spend a lot of my day working on framework software for other programs to use. I enjoy this plumbing, and Red Hat gives me all the time I need to properly design and build these tricky infrastructure-type projects. Sometimes, just one person isn’t enough.
For the LVFS project, I need vendors making hardware to submit firmware files with carefully written metadata so that they can be downloaded by hundreds of thousands of Linux users securely and automatically. I also need those vendors to either use a standardized flashing protocol (e.g. DFU or UEFI) or to open the device specifications enough to allow flashing firmware without signing an NDA.
Over the last couple of months I’ve been emailing various tech companies trying to get hold of the right people to implement this. So far the reaction from companies has been enthusiastic and apathetic in equal measures. I’ve had a few vendors testing the process, but I can’t share those names just yet as most companies have been testing with unreleased hardware.
This is where you come in. On your Linux computer right now, think about what hardware you own that works in Linux that you know has user-flashable firmware? What about your BIOS, your mouse, or your USB3 hub? Your network card, your RAID card, or your video card?
Things I want you to do:
- Find the vendor on the internet, and either raise a support case or send an email. Try and find a technical contact, not just some sales or marketing person
- Tell the vendor that you would like firmware updates when using Linux, and that you’re not able to update the firmware booting to Windows or OS-X
- Tell the vendor that you’re more likely to buy from them again if firmware updates work on Linux
- Inform the vendor about the LVFS project : http://www.fwupd.org/
At all times I need you to be polite and courteous, after all we’re asking the vendor to spend time (money) on doing something extra for a small fraction of their userbase. Ignoring one email from me is easy, but getting tens or hundreds of support tickets about the same issue is a great way to get an issue escalated up to the people that can actually make changes.
So please, spend 15 minutes opening a support ticket or sending an email to a vendor now.
Published by
hughsie
Richard has over 10 years of experience developing open source software. He is the maintainer of GNOME Software, PackageKit, GNOME Packagekit, GNOME Power Manager, GNOME Color Manager, colord, and UPower and also contributes to many other projects and opensource standards. Richard has three main areas of interest on the free desktop, color management, package management, and power management. Richard graduated a few years ago from the University of Surrey with a Masters in Electronics Engineering. He now works for Red Hat in the desktop group, and also manages a company selling open source calibration equipment. Richard’s outside interests include taking photos and eating good food. View all posts by hughsie
7 thoughts on “Linux Vendor Firmware Service: We Need Your Help”
Is there an easy tool to detect hardware with user-flashable firmwares?
Unfortunately no. I’ve been going through my hardware and checking with the upstream vendor for a flashing tool. Some devices need a magic packet to go into DFU mode, so it’s not like you can detect the upload capability during normal rumtime.
The tool doesn’t have to be that advanced. It could just enumerate all the hardware and prune the devices with already existing firmware in the repo.
If I search for ‘about’ on my Gnome F22 laptop The ‘Details’ app pops up. It has categories on the left for: Overview, Default Applications, Removable Media. How about adding ‘Devices’?
When I boot a new laptop with Fedora I’d like to know: what hardware is installed, is it supported, if not why not (unknown device vs. known but patent encumbered drivers), what can I do about it (eg. swap a Broadcom WiFi card for Intel).
Windows gives your laptop a score based on performance. Linux could give your laptop a score based also on hardware support.
The next step could be: write a polite letter to a manufacturer as you’ve described here. I think a lot of people would like to play their small part in the process, but unless they’ve read your blog on this day in history they’re unlikely to know about it.
Btw. When this is fully launched, the LVFS front page should have a list of the manufacturers with firmware in the repo. Maybe some stats on number of laptops and individual devices supported. The list should function as the kind of social proof you’ve probably seen on websites launched by startups. We want an engineer at Asus or Acer to be able to show their manager that Dell and Lenovo already do this – this is obviously something that their peers just do.
Thanks for working on this.
ATM the link is throwing 503s at me. That’s not really nice …
It might help to have a template that people can copy/paste to make sure it is polite, complete and helpful.
A draft, feel free to correct and optimise:
I am using your product . This product uses firmware that sometimes needs to be updated. Which is a problem as I am using Linux.
I would like to inform you of the LVFS project : https://beta-lvfs.rhcloud.com/ that aims to solve this problem in a very comfortable way for you and for me. It aims to automate the distribution process of firmware updates, allowing you to save a lot of time and ressources.
Would you kindly consider using this solution for your products? For more information feel free to contact Richard Hughes, the project manager of the LVFS system under .
Should you support the LVFS system for your products, I would definitely promote your products for doing the right thing and I will continue to buy more.
1. since people are busy (lazy), a web-form/generator would be even better than a template. A nice dropdown with vendors (products?), an editable database with support e-mail addresses that grows over time, everything that enables a user to get a text and a mailto link with few clicks. (much like those forms for mailing politicians, it could have quite an impact)
2. I don’t completly agree to the “small fraction of their userbase” argument (of course, i’d still be polite). Normally, small userbase means small demand means higher price. Excluding a userbase completly is bad business practice (and doesn’t really work as we see). Consider how many linux users are decision makers for a number of other users. The average linux user has more influence than the average win/mac user concerning hardware purchases. At least that’s my feeling, i’m lacking figures to proof that claim.
But in any way, hardware should be/is built for a platform, not for an operating system. OS specific drivers were a bad decision in the first place. And except maybe graphics cards, I don’t really get the concept of all drivers being closed source. I just don’t… 🙂
Hello Richard! It is a nice idea, an idea that was coming many times in my mind. It will be easier / quicker for each company to submit their updates to a unified platform and then this platform to distribute these updates. Some efforts exist.
About your aim, why you dont publish directly the email that are you senting in order to make it easier for us to help you? Please publish it, and then send me an email to find my vendors!
Thanks! Good luck!
[WORDPRESS HASHCASH] The poster sent us ‘0 which is not a hashcash value.
Источник