- UNIX / Linux PGP TarBall File Signature Keys Verification
- Step 1. Download tar ball / software along with PGP key for verification
- Step 2. Checking PGP signatures / verification
- Step 3. Linux or Unix command to grab the public key from a key server
- Step 4. Verify PGP Signature of Downloaded Nginx Software on Linux / Unix
- Step 5. Command to grab the public key from a web server
- So, how do I build trust and mark Maxim Dounin’s PGP key as trusted?
- How do I delete “Maxim Dounin ” key?
- Conclusion
- How to Verify PGP Signature of Downloaded Software on Linux
- Example: Verify PGP Signature of VeraCrypt
- Importing Public Key from a Trusted Source
- How To Verify Files and Signatures with PGP In Linux?
- Find PGP Information
- Download Apache Source
- Verify Source Code
- Add Public Key Server
- Check Again Signature File
- How Do I Verify a PGP Signature?
- How PGP Works
- PGP Signatures
- How Do I Verify a PGP Signature?
- Verifying SHA256SUMS.gpg
- Searching gpg Keys:
- Conclusion
- About the author
- David Adams
UNIX / Linux PGP TarBall File Signature Keys Verification
I ‘ve downloaded open-source software from the Internet. The download server also provided me the PGP signature file. How do I verify that signature (file.tar.gz.asc) file against downloaded software release (software.version.tar.gz) under Linux / UNIX operating systems? How can I verify PGP signature of downloaded software on Linux / Unix?
PGP is an acronym for Pretty Good Privacy. It provides cryptographic privacy and authentication. PGP is often used for encrypting and decrypting e-mails and files. We can use the PGP signature of downloaded software from the Internet too. For all FOSS based project, you should download the PGP signatures and MD5/SHA hashes and verify them before using them. Linux and many other UNIX like operating systems can use The GNU Privacy Guard. However, any OpenPGP-compliant program should work successfully with software. The following instructions assume that you are using the GNU Privacy Guard.
| Tutorial details | |
|---|---|
| Difficulty level | Intermediate |
| Root privileges | No |
| Requirements | gpg command on Linux or Unix |
| Est. reading time | 2m |
Step 1. Download tar ball / software along with PGP key for verification
For example, purpose you will download nginx web server and verify the same with PGP. Use the wget command to grab latest version:
$ cd /tmp
$ wget http://nginx.org/download/nginx-1.18.0.tar.gz
$ wget https://nginx.org/download/nginx-1.18.0.tar.gz.asc
Let us list files using the ls command, enter:
$ ls -l
Sample outputs:
Step 2. Checking PGP signatures / verification
Type the following gpg command:
$ gpg nginx-1.18.0.tar.gz.asc
## OR ##
$ gpg —with-fingerprint nginx-1.18.0.tar.gz.asc
Sample outputs:
However, the gpg command failed to check the signature as we don’t have the author’s public key 520A9993A1C052F8 in our local Linux / Unix server or workstation. Hence, we need to grab the public key from a key server (such as pgpkeys.mit.edu) or download it from the author’s web site.
Step 3. Linux or Unix command to grab the public key from a key server
The syntax is as follows:
Try to grab the public key A524C53E, enter:
$ gpg —recv-key 520A9993A1C052F8
$ gpg —verbose —recv-key 520A9993A1C052F8
As you can see, Maxim Dounin is listed on the Nginx project site along with his keys:
Step 4. Verify PGP Signature of Downloaded Nginx Software on Linux / Unix
Now, try to verify the software signature again as follows:
$ gpg —verify nginx-1.18.0.tar.gz.asc nginx-1.18.0.tar.gz
You should see outputs as follows:
Step 5. Command to grab the public key from a web server
Again, use the wget command to grab the public key from a web server:
$ wget https://nginx.org/keys/mdounin.key
Import the key from mdounin.key file, enter:
$ gpg —import mdounin.key
Now, try to verify the software signature again using the gpg keys:
$ gpg gpg —verify nginx-1.18.0.tar.gz.asc nginx-1.18.0.tar.gz
The signature is good, but you don’t trust this PGP key. In other words, the file has not tampered. However, you need to additionally verify that key 520A9993A1C052F8 was created by the real Nginx author named Maxim Dounin and not by someone else.
- No ads and tracking
- In-depth guides for developers and sysadmins at Opensourceflare✨
- Join my Patreon to support independent content creators and start reading latest guides:
- How to set up Redis sentinel cluster on Ubuntu or Debian Linux
- How To Set Up SSH Keys With YubiKey as two-factor authentication (U2F/FIDO2)
- How to set up Mariadb Galera cluster on Ubuntu or Debian Linux
- A podman tutorial for beginners – part I (run Linux containers without Docker and in daemonless mode)
- How to protect Linux against rogue USB devices using USBGuard
Join Patreon ➔
So, how do I build trust and mark Maxim Dounin’s PGP key as trusted?
This is a little complicated as you never met Maxim Dounin face to face. To vouch for the key’s authenticity, you can do so by signing it with your own private key and mailing it back to its owner. This is a simple and easy way to build a trust relationship. Another quick option is to use the following command:
gpg —edit-key
For example:
$ gpg —edit-key mdounin@mdounin.ru trust
WARNING : Do not trust keys blindly to get rid of the warnings. For downloaded software verification, you don’t need to set up a web of trust. The following example is just for demonstration purposes as I never met the author/people behind Nginx or vouch for him.
Now, try to verify the software signature again:
$ gpg —verify nginx-1.18.0.tar.gz.asc nginx-1.18.0.tar.gz
Since, you have entered the web of trust, you should not see any warning message on screen.
How do I delete “Maxim Dounin ” key?
The syntax is as follows to list and delete unwated keys:
$ gpg —list-key
$ gpg —delete-keys B0F4253373F8F6F510D42178520A9993A1C052F8
## or ##
$ gpg —delete-keys 520A9993A1C052F8
Conclusion
In this quick tutorial, you learned about PGP and how to verify the PGP signature of downloaded software from the Internet under Linux or Unix-like systems. See following resources for further information:
🐧 Get the latest tutorials on Linux, Open Source & DevOps via
Источник
How to Verify PGP Signature of Downloaded Software on Linux
PGP (Pretty Good Privacy) is a public key cryptography software that can be used to encrypt and sign data communication. In this tutorial, we will look at how to verify the PGP signature of software downloaded from the Internet on Linux.
Linux users can securely install software from their distribution’s repositories. But there are times when you need to download and install software from a website. How can you be sure that the software you downloaded wasn’t tampered with?
Some software authors sign their software using a PGP program such as GPG (GNU Privacy Guard), which is a free software implementation of the OpenPGP standard. In that case, you can verify the integrity of software using GPG.
The process is relatively simple:
- You download the public key of the software author.
- Check the public key’s fingerprint to ensure that it’s the correct key.
- Import the correct public key to your GPG public keyring.
- Download the PGP signature file of the software.
- Use public key to verify PGP signature. If the signature is correct, then the software wasn’t tampered with.
We will use VeraCrypt as an example to show you how to verify PGP signature of downloaded software.
Example: Verify PGP Signature of VeraCrypt
Although VeraCrypt is open source software, it isn’t included in Ubuntu repository. We can download VeraCrypt Linux installer from official website. I use Ubuntu 20.04 desktop, so I download the .deb file for Ubuntu 20.04.
On the VeraCrypt download page, you can also find the PGP public key and PGP signature download link. Click the links to download these two files. You can run the following command to download PGP public key of VeraCrypt.
Before you do anything with the public key, you must always check the key’s fingerprint to see if it’s the correct key. Display the fingerprint of the key using the command below.
The second line of the output is the key’s fingerprint.
If you are using a very old version of GPG ( gpg —version ) like 1.4.20, then use the following command to display the fingerprint.
Compare it with the fingerprint published on VeraCrypt website.
As you can see, the two fingerprints are identical, which means the public key is correct. So you can import the public key to your GPG public keyring with:
Now verify the signature of the software installer file using the command below. You need to specify the signature file ( .sig ) and the software installer file. This is a detached signature, meaning that the signature and software are in separate files.
The output should say “Good Signature”.
The signature is a hash value, encrypted with the software author’s private key. GPG uses the public key to decrypt hash value, then calculate the hash value of VeraCrypt installer and compare the two. If these two hash values match, then the signature is good and the software wasn’t tampered with.
If GPG tells you it’s a bad signature, then the software installer was tampered with or corrupted.
Importing Public Key from a Trusted Source
Note that if the software author tells you his/her public key ID on the website, then you can import the public key with the following command, so you don’t have to manually download the PGP public key and import it to your keyring.
Then display the fingerprint with:
And compare the fingerprint from output with the one published on website. This is more secure because the public key is imported from a public key server, which by default is set to hkp://keys.gnupg.net in
/.gnupg/gpg.conf file. There’re hundreds of public keyservers around the world. Ubuntu has their own key server. MIT also has one.
If you see the following error,
then you can try a different key server, like this:
I hope this tutorial helped you verify PGP signature of software downloads. As always, if you found this post useful, then subscribe to our free newsletter or follow us on Twitter or like our Facebook page.
Источник
How To Verify Files and Signatures with PGP In Linux?
GnuPG is an opensource and popular alternative to the PGP. PGP provides encryption-related function. PGP provides a hash function like standard Linux packages. We will look ow to verify files downloaded from the internet with their PGP signatures to verify.
Find PGP Information
In this example, we will use the Apache source code. Apache PGP signature can be found and downloaded like below.

We can see that the signature file have asc extension with the same name with the compressed source code file.
Download Apache Source
We will download Apache source code related with previously downloaded PGP signature.

Verify Source Code
We will verify downloaded Apache source code with PGP by providing the signature file. We will just provide the asc file which will match the source file in the same directory.

There is a problem Can’t check signature: No Public key error. This is because we havent added the Public key of the Apache from a server.
Add Public Key Server
We will add the public key server to check our signature file. We will use —keyserver option in order to specify the GPG key server which can be an IP address or hostname. Then we will use the —recv-key option and provide the ID of the RSA key which is provided with the asc file.

We have successfully received a public key from the server. We can see there is some information about the imported key.
- Some name and web address about the key is provided.
- `Total number processed` shows total keys processes which is 1 in this example.
- `Imported` is imported key count which is 1 in this example.
Check Again Signature File
We will check the signature file again. I hope it works.

We can see that the signed data is determined. Also, the RSA key is printed to the screen. The signer information also provided which is Daniel Ruggeri .
Источник
How Do I Verify a PGP Signature?
PGP is not only used to secure information from cyber threats but also to check file integrity.
This tutorial explains easily how PGP works and how to verify PGP signatures.
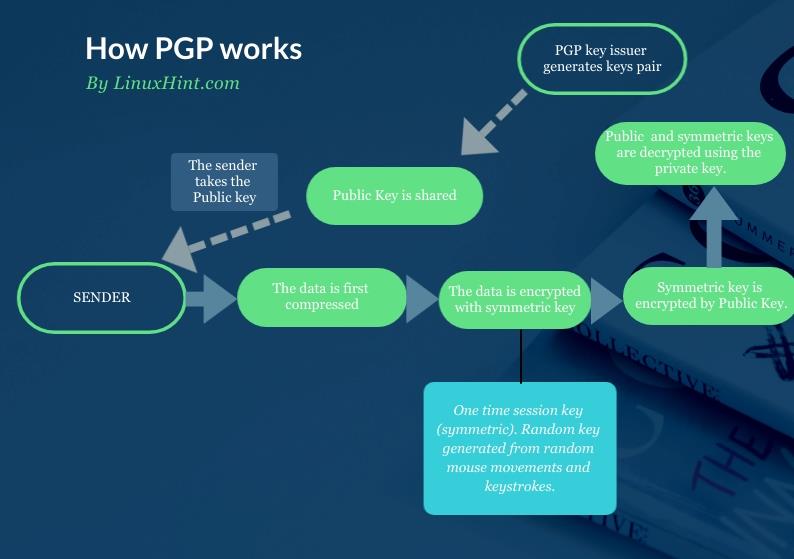
How PGP Works
The image below depicts a PGP public key. This PGP public key can be decrypted only with a specific private PGP key. The issuer of the public key below also issued a private PGP key since they are generated in the same process. He only shares the public key.
If you take his public key to encrypt a message to him, he will be able to decrypt the message using his private key. Only his private key can decrypt the message you encrypted using his public key.
The information is encrypted using the public key, and decrypted using the private key. This is called asymmetric encryption.
So even if an attacker manages to intercept the message without the private key, he is unable to see the message content.
The advantage of asymmetric encryption is the simplicity to exchange keys. But its disadvantage is it can’t encrypt large amounts of data, and that’s why PGP implements both of them.
Symmetric encryption is applied when the public key is used to encrypt the protected data. With the public key, the sender does two things: first generates the symmetric encryption to protect the data, and then it applies asymmetric encryption, which does not encrypt the data itself, but the symmetric key, which protects the data.
To be more technical, before the symmetric key is applied, the data is also compressed before being encrypted with the symmetric key and public key. The following chart flow shows the whole process:
PGP Signatures
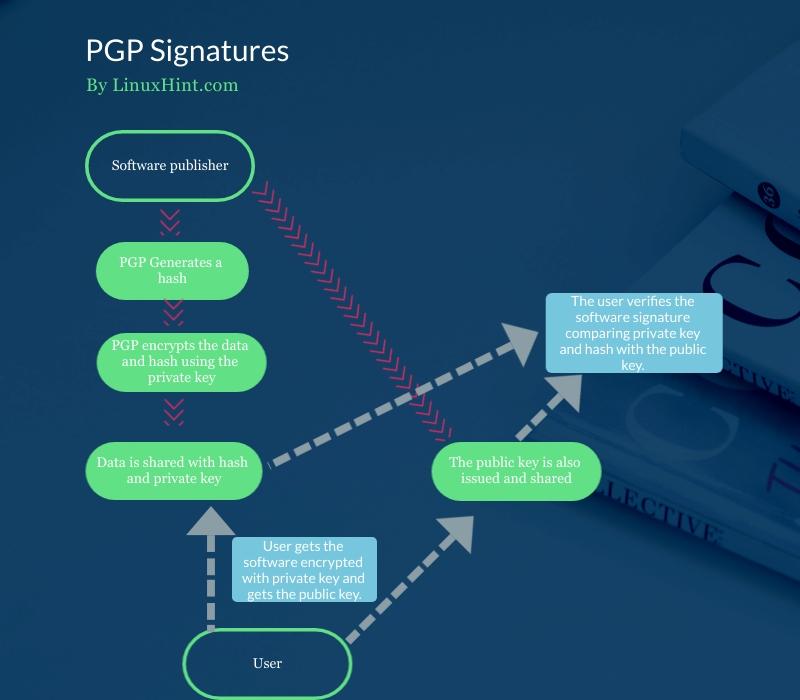
PGP is also used to check packages’ integrity. This is achieved through digital signature, which can be done with PGP.
First, PGP generates a hash that is encrypted with the private key. Both private key and hash can be decrypted using the public key.
PGP creates a digital signature, for example, for an ISO image using DSA or RSA algorithms. In this case, the private key is attached to the software or ISO Image, contrary to the operation described previously. The public key is also shared.
Users use the public key to verify the signature attached to the released software.
The following chart flow shows how the private key and hash is attached to the software and how the user takes the software with the attached hash and private key together with the public key to verify the signature:
How Do I Verify a PGP Signature?
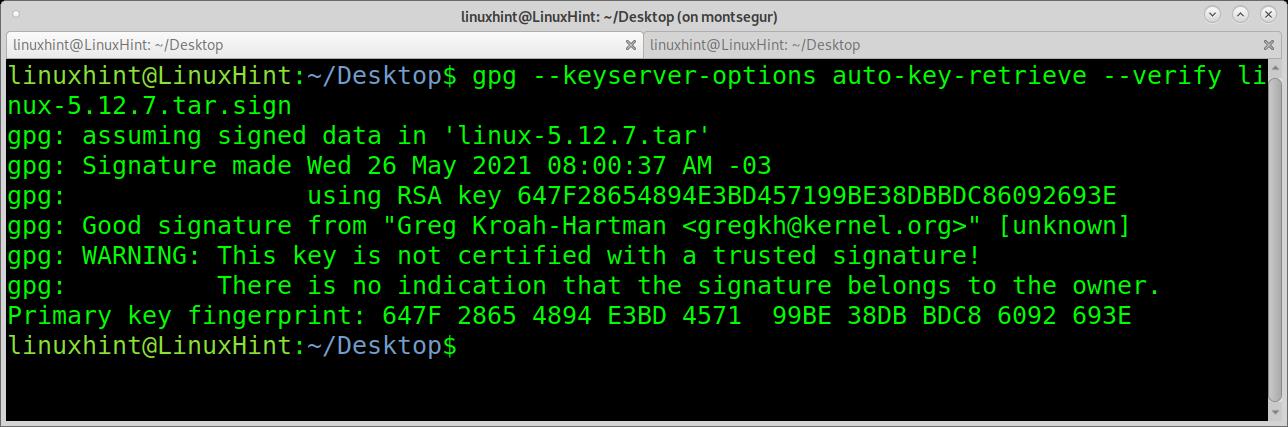
The first example shows how to verify the Linux kernel signature. To try it, access https://kernel.org and download a kernel version and its PGP file. For this example, I will download files linux-5.12.7.tar.xz and linux-5.12.7.tar.sign.
The first example shows how to verify the signature with a single command. According to the man page, this option combination is going to be deprecated in future versions. However, it is still widely used, and while the specific combination will be deprecated, the options will remain.
The first option –keyserver-options allows defining options for the keyserver where public keys are stored. Basically, this allows the implementation of public keys fetching options.
The –keyserver-options is combined with the –auto-key-retrieve option to automatically retrieve public keys from a keyserver when verifying signatures.
To find the public keys, this command will read the signature looking for a defined preferred keyserver or signer’s ID through a lookup process using Web Key Directory.
As you can see, the signature is good, but there is a warning message saying gpg can’t confirm the signature belongs to the owner. Anyone can issue a public signature as Greg Krohan-Hartman. You know the signature is legitimate because you trust the server you have downloaded it from. In this case, it is specified in the .sign downloaded from kernel.org.
This warning is always present, and you can avoid it by adding signatures to a signature trusted list using the option –edit-key trust. The truth is no user does it, and the Gpg community requested the warning removal.
Verifying SHA256SUMS.gpg
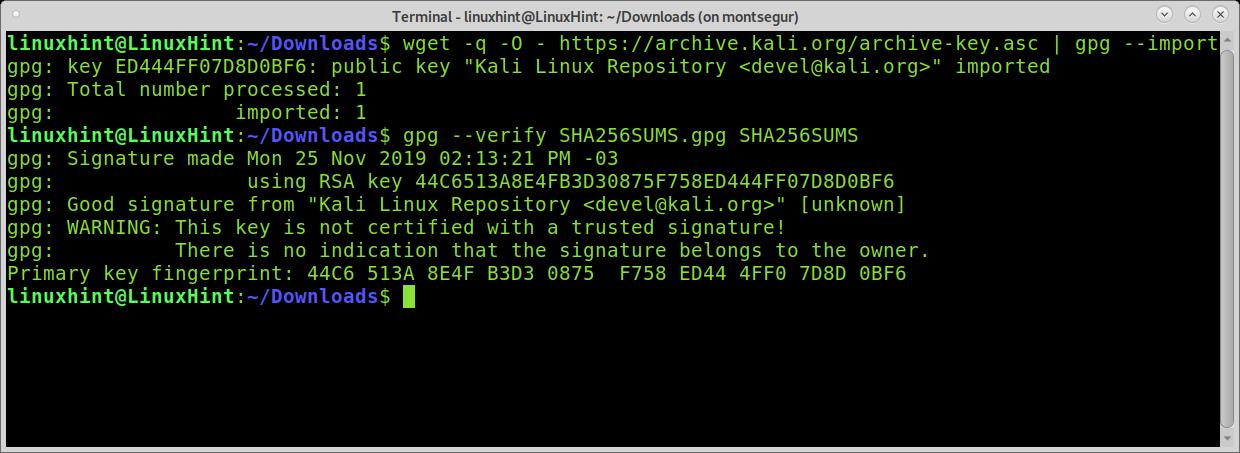
In the following example, I will verify the integrity of an old Kali Linux image I found in my box. For this purpose, I downloaded the SHA256SUMS.gpg and SHA256SUMS files belonging to the same iso image.
Once you download an iso image, the SHA256SUMS.gpg, and SHA256SUMS, you need to get the public keys. In the following example, I fetch the keys using wget and gpg –import (Kali verification instructions link to this key server).
Then I verify the file integrity by calling gpg with the –verify argument:
wget -q -O — https: // archive.kali.org / archive-key.asc | gpg —import
gpg —verify SHA256SUMS.gpg SHA256SUMS
As you can see, the signature is good, and the verification was successful.
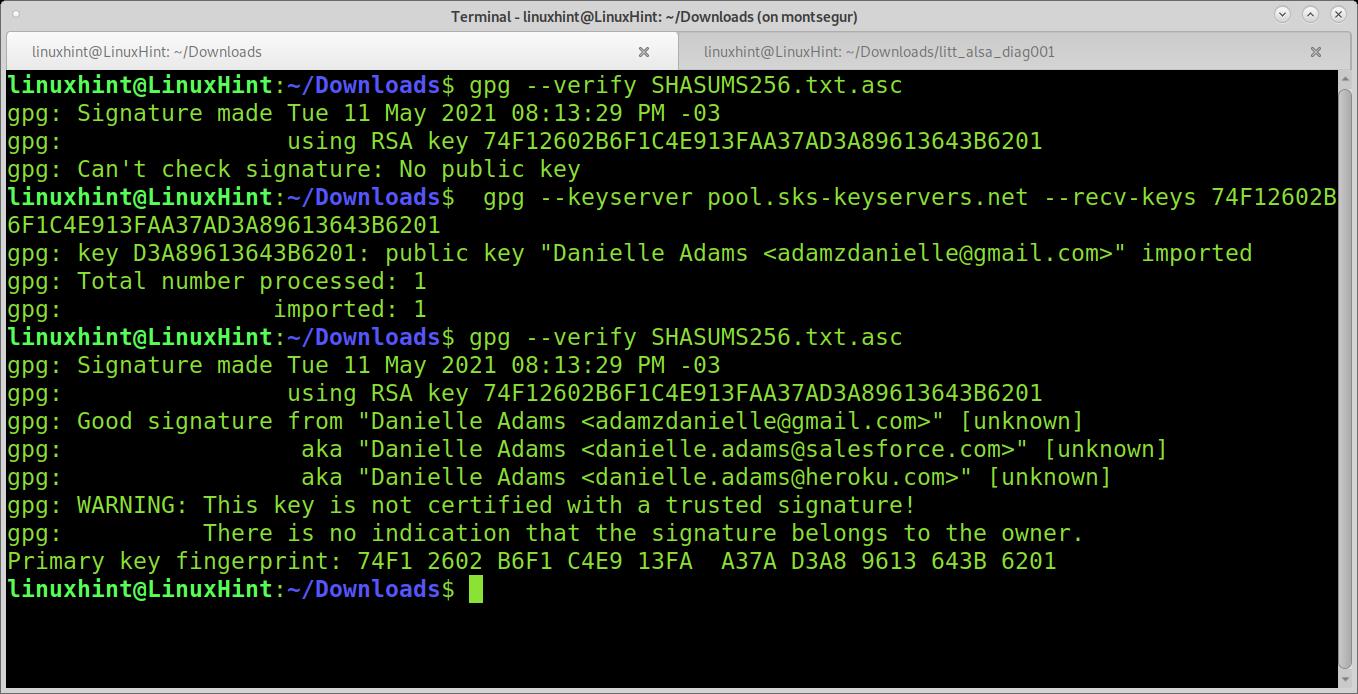
The following example shows how to verify a NodeJS download. The first command returns an error because there is no public key. The error indicates I need to search for the key 74F12602B6F1C4E913FAA37AD3A89613643B6201. Usually, you can also find the key ID in the instructions.
By using the option –keyserver, I can specify the server to search for the key. By using the option –recv-keys, I retrieve keys. Then the verification works:
I copy the key I need to fetch, and then I run:
gpg —keyserver pool.sks-keyservers.net —recv-keys
gpg —verify SHASUMS256.txt.asc
Searching gpg Keys:
If auto retrieving keys doesn’t work and you can’t find the verification-specific instructions, you can search the key in a keyserver using the option –search-key.
As you can see, the key was found. You can also retrieve it by pressing the number of the key you want to retrieve.
Conclusion
Verifying downloads’ integrity may prevent serious problems or explain them, for example, when downloaded software doesn’t work correctly. The process with gpg is pretty easy, as shown above, as long as the user gets all the necessary files.
Understanding asymmetric encryption or public and private keys-based encryption is a basic need to interact safely on the internet, for example, using digital signatures.
I hope this tutorial on PGP signatures was helpful. Keep following Linux Hint for more Linux tips and tutorials.
About the author
David Adams
David Adams is a System Admin and writer that is focused on open source technologies, security software, and computer systems.
Источник