- Как использовать сканер портов в сетевой утилите Mac OS X
- Сканировать порты по IP или домену из Mac OS X
- Ports Open (Networking)
- Ports
- Spotlight on Network Utility to List Ports
- List open files = lsof
- Protocols
- Processes Tour
- For a list of processes on Mac:
- Resources
- Honeypots
- Question: Q: Checking TCP/UDP ports!
- Helpful answers
- How to Use the Port Scanner in Mac OS X Network Utility
- How to Scan Ports on an IP or Domain from Mac OS X
Как использовать сканер портов в сетевой утилите Mac OS X
Mac OS X поставляется со встроенным сканером портов, просто одним из множества функций, заправленных в когда-либо полезное приложение Network Utility. Это означает, что вам не нужно беспокоиться о командной строке или устанавливать более сложные инструменты, такие как nmap, для быстрого сканирования открытых портов в заданном IP или домене, вместо этого вы можете сделать это через дружественный графический интерфейс. Несмотря на то, что это довольно продвинутая утилита, на самом деле она очень проста в использовании.
Быстрое оповещение: помните, что более новые версии OS X переместили Network Utility для захоронения в системной папке, это не значит, что ее нельзя использовать, это просто означает, что вам нужно либо сделать псевдоним, либо запустить его из Spotlight, или получить от него информацию о системе. В целях этого пошагового руководства мы будем использовать Spotlight для запуска Network Utility и запуска сканирования, поскольку это самый простой и быстрый маршрут, хотя, если вы планируете часто использовать инструмент, вы, вероятно, захотите сделать псевдоним самостоятельно. Хорошо, давайте перейдем к сканирующим портам.
Сканировать порты по IP или домену из Mac OS X
Вы можете выбрать любой локальный или удаленный IP-адрес для сканирования, если вы одиноки в сети (или даже воздушно-gapped) и все еще хотите попробовать это самостоятельно, используйте в качестве цели IP-адрес «127.0.0.1»:
- Hit Command + Spacebar для вызова Spotlight и введите «Network Utility», а затем ключ возврата для запуска приложения Network Utility
- Выберите вкладку «Сканирование портов»
- Введите IP-адрес или доменное имя, которое вы хотите отсканировать для открытых портов, и выберите «scan»
- Необязательно, но не обязательно рекомендуется, вы можете установить диапазон портов для сканирования между ними, если вы просто хотите найти определенный набор активных служб
127.0.0.1 или «localhost» будет просто проверять локальный Mac для открытых портов, если вы новичок в сканировании портов, что может быть предпочтительным способом, поскольку наиболее разумно хорошо защищенные удаленные домены отклоняют входящие запросы или не реагируют на них ,
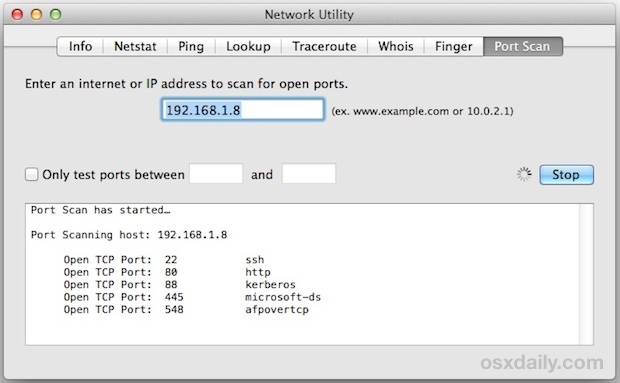
Пусть запущен инструмент сканирования портов, и вы быстро начнете видеть любые открытые порты TCP и их традиционно идентифицированное использование. Например, вы можете увидеть что-то вроде этого, если вы сканируете localhost (127.0.0.1):
Началось сканирование портов …
Хост порта сканирования: 127.0.0.1
Открыть TCP-порт: 22 ssh
Открыть TCP-порт: 80 http
Открытый TCP-порт: 88 kerberos
Открыть TCP-порт: 445 microsoft-ds
Открытый TCP-порт: 548 afpovertcp
Открыть TCP-порт: 631 ipp
Открыть TCP-порт: 3689
Видимые порты будут отличаться для каждой машины в зависимости от того, какие сервисы и серверы доступны, но если вы сканируете Mac и ПК, вы обычно найдете веб-серверы, SMB-порт для совместного использования Windows 445, AFP Apple File Sharing на порту 548, возможно, активный видимый SSH-сервер на 22, UDP-серверах и, возможно, множество других. Сканирование порта будет довольно высоким, поскольку оно сканирует, поэтому просто отпустите его, если вы хотите увидеть все.
Если вы видите абсолютно ничего, но вы знаете, что IP активен с открытыми службами, либо машина не транслируется, машина-получатель отклоняет все запросы, либо может быть настроен сильный брандмауэр. Это делает портативный сканер Network Utility отличным способом быстро проверить безопасность и проверить потенциальные уязвимости или активные службы на соседних компьютерах Mac, iOS, Windows, Linux-машинах и других компьютерах.
Сетевая утилита, очевидно, ограничена Mac, и, хотя на стороне iOS нет встроенных инструментов, можно выполнить сканирование портов с iPhone и iPad с помощью приложения для пальцев — бесплатный инструмент, который очень удобно дополняет расширенный набор инструментов для пользователей iOS.
Источник
Ports Open (Networking)
What ports are open for hacking on my Mac and Linux machine?
Here is how to see what ports are open listening on a server.
This is perhaps the most important potential vulnerability.
Having ports listenting to outside traffic also takes CPU effort, which consumes electricity and thus reduce battery life.
Ports
PAT (Port Address Translation) maps ports.:
- 0 — 1023 = well-know ports
- 1024 — 49141 = Registered ports (1433 for MS SQL, 1431 for Oracle SQL, etc.)
- 49152 — 54535 65535 = dynamic ports
Port 3389 is used for communicating with Microsoft’s RDP (Remote Desktop Protocol) on Windows machines. See My notes on Windows RDP.
Common TCP Ports in layer 4: REMEMBER
- 80/443 = HTTPS (Secure, encrypted)
21/990 = FTP and FTPS which adds SSL & TLS to encrypt
3389 = RDP (Remote Desktop Protocol) from Microsoft
143/993 = IMAP (Internet Message Access Protocol) files remain on server / TLS
No port for ICMP RFC 792 Pings RFC 1122 as it’s in IP transport layer
- 8080, 8081 = Limits Microservice
- 8888 = Spring Cloud Config server
- 8000,8001,8002,… = Currency Exhange Microservice
- 8100,8101,8102,… = Currency Conversion Microservice
- 8761 = Netflix Eureka Naming Server
- 8765 = API Gateway
- 9411 = Zipkin Distributed Tracing Server
IP header protocol field REMEMBER
- 1 = ICMP (Internet Control Message Protocol)
- 2 = IGMP (Internet Group Management Protocol) to estab. multicaset group transmitted to at once
- 6 = TCP (Transmission Control Protocol)
- 17 = UDP (User Datagram Protocol) used by VOIP
- 115 = L2TP (Layer 2)
Spotlight on Network Utility to List Ports
Apple’s macOS Spotlight is like Window’s Search omni-box. *
Press Command+Spacebar.
Type the name of utilities that are buried, such as Network Utility.
Click the keyboard return/enter key to launch the Network Utility app.
Select the «Port Scan» tab.
Enter the IP (such as 127.0.0.1), localhost, or domain name you wish to scan for open ports.
Choose scan to see what ports the server responds to.
List open files = lsof
In a Terminal command line:
PROTIP: If you’ll be using this often, create an alias such as of .
“lsof” is a contraction for “list open files”. Without any options specifications, lsof lists all open files belonging to all active processes.
“-nP” is a combination of “n” for no resolution of IPs to hostnames using DNS and “P” for no resolution of Port names from numbers.
This is because the command already takes several seconds to run.
“+c 15” specifies command width of 15.
Piping to grep filters out only lines containing “LISTEN”.
NOTE: All options are shown by this command:
Drag your Terminal window wider to remove word-wrap.
“FD” column lists File Descriptors. “u” is for read and write mode. “r” for read only, “w” for write-only.
Linux requires root on operations for well-known ports below 1024.
Protocols
TCP (Transmission Control Protocol) is the most commonly used protocol on the Internet and any TCP/IP network. TCP enables two hosts to establish a connection and exchange streams of data. TCP guarantees delivery of data and that packets will be delivered in the same order in which they were sent. Guaranteed communication/delivery is the key difference between TCP and UDP on ort 53.
UDP (Datagram Protocol) is connectionless and does not guarantee reliable communication; it’s up to the application that received the message to process any errors and verify correct delivery. UDP is often used with time-sensitive applications, such as audio/video streaming, where dropping some packets is preferable to waiting for delayed data.
Processes Tour
NOTE: Drag the scroll bar to see what is beyond what is displayed.
mongod is MongoDB listening on port 27017.
I should keep that closed unless I need it.
In Node, close all connections when the app closes completely:
2BUA8C4S2C
When I search for “2BUA8C4S2C” I see “2BUA8C4S2C.com.agilebits” in folder /Users/mac/Library/Group Containers
This says This port is used only on the loopback interface (127.0.0.1) for the 1Password extension to talk to the 1Password Agent. It should be safe to firewall it from any sources other than 127.0.0.1. If you do a packet capture on lo0 and then filter by tcp.port == 6258 you can see what traffic is being passed. Nothing is transmitted in the clear.
Skype I don’t mind keeping open. I use it a lot.
Dropbox — why does it need to be kept open?
I’ll use just their web page when I need it.
Resilio\x20Sync I used once to get a file.
In Resilio Preferences, uncheck “Start Resilio Sync on startup”.
SketchMirrorHel
XMPP ports 56989 and 56990
For a list of processes on Mac:
Don’t visit http://www.westwind.com/reference/OS-X/background-processes.html
ftp (tftp) should not appear.
Scan other machines
brew install nmap
(Zenmap is the GUI)
There are a lot of options
nmap -h
nmap [scan type] [options]
There are a lot of options
nmap -h
Scan for vulnerabilities using nmap scripts.
Scan for vulnerabilities using vulnerability scanners:
Scans for versions of applications and operating systems. Compare those against known vulnerabilities and exploits.
Devices on the Internet with open ports are indexed by Shodan.io.
SNR (software defined radios)
Resources
Learn basic hardware hacking with UbertoothOne and HackRF One.
Network Intrusion detection systems (NIDS)
AlienVault Open Source SIEM (OSSIM) with Open Threat Exchange (OTX) Security Information and Event Management (SIEM) software.
Honeypots
Commercial Honeypot software:
- Fortinet – FortiDeceptor
- Attivio — BOTsink
- Fidelis – Fidelis Deception
- TrapX– DeceptionGrid
- Illusive – Illusive Platform
Источник
Question: Q: Checking TCP/UDP ports!
What’s up everybody,
Does anyobody know how to check if a port is open? (tcp/udp)
Posted on Jan 20, 2011 6:09 PM
Helpful answers
Even this post is rather old, but it still comes up with the search results so I would like to reply a solution to the question.
You can open the Terminal in Mac (type terminal on Spotlight) and then use NetCat command by typing like a sample below to test your specific port like this replacing 1xx with your target IP address, then the port to check.
>nc -vnzu 1xx.xxx.xxx.xxx 53
or if you want to check a range of ports for example from port 1 to 53, just type
>nc -vnzu 1xx.xxx.xxx.xxx 1-53
NetCat is already a built-in command in Mac so no need to install anything.
Hope this helps.
Jul 7, 2015 11:49 PM
There’s more to the conversation
Loading page content
Page content loaded
Use the Network Utility in the /Applications/Utilities/ folder to scan 127.0.0.1 for open ports.
Jan 20, 2011 6:11 PM
isn’t there another way?
would be better if there was a program..
Jan 20, 2011 6:48 PM
Network Utility is a program, no?
Other options include downloading and building nmap, which can be quite useful.
Or +sudo lsof -i+ might possibly be of use?
Jan 20, 2011 7:23 PM
Jan 21, 2011 10:29 PM
Welcome to the forums.
Common Mac OS X tools used here include Network Utility, lsof, and telnet and ping, and dns-sd and ping for Bonjour and mDNS, depending on details are sought.
(With the Windows entries from your footer, various of these tools and equivalents are what can be obtained by loading Cygwin or by loading Microsoft’s SUA/SFU tools, and with some add-ons. PowerShell might or does have analogs here, but the old MS-DOS shell was pretty limited in what diagnostics were available without additions. There was telnet and ping, but some other bits were missing.)
Add-on tools include nmap. (nmap is a fairly gonzo-useful tool for this sort of thing.)
telnet works nicely for brute-force port tests on the LAN.
And FWIW, if those public web site tools do work and if you’re on your own LAN, then definitely also consider checking the settings of and consider upgrading the LAN security. Those tools and those web sites should be blocked by default by the firewall or the gateway device found on most any LAN; whether that’s a low-end NAT device, a server-grade firewall, or otherwise.
Jan 22, 2011 7:31 AM
If you’re trying to figure out whether your client machine is being blocked in the outbound direction (client to Internet) by something like your home firewall, or your ISP, then try http://www.firebind.com.
Firebind is the only tool on the Internet that can test any of the 65535 TCP or UDP ports in the outbound direction. If you want, you can test the entire TCP and UDP range.
Источник
How to Use the Port Scanner in Mac OS X Network Utility
Mac OS X comes with a bundled port scanner tool, just one of a variety of features tucked into the ever useful Network Utility app. That means you don’t need to bother with the command line or install more advanced tools like nmap to quickly scan for open ports on a given IP or domain, instead you can do it all through the friendly graphical interface. Despite being a fairly advanced utility, it’s actually very easy to use.
Quick sidenote: remember that newer releases of Mac OS X have relocated Network Utility to be buried in a system folder, that doesn’t mean it can’t be used, it just means you have to either make an alias, launch it from Spotlight, or get to it from System Info. For the purpose of this walkthrough we’ll use Spotlight to launch Network Utility and start the scan since it’s the easiest and quickest route, though if you plan on using the tool often you’ll probably want to make an alias yourself. OK, let’s jump right to scanning ports.
How to Scan Ports on an IP or Domain from Mac OS X
You can choose any local or remote IP to scan, if you’re solitary on a network (or even air gapped) and still want to try this out yourself, use the loopback IP of “127.0.0.1” as the target:
- Hit Command+Spacebar to summon Spotlight and type “Network Utility” followed by the return key to launch the Network Utility app
- Select the “Port Scan” tab
- Enter the IP or domain name you wish to scan for open ports and choose “scan”
- Optional, but not necessarily recommended, you can set a port range to scan between if you just want to search for a specific set of active services
127.0.0.1 or “localhost” will just check the local Mac for open ports, if you’re new to port scanning that may be the preferred way to go since most reasonably well secured remote domains reject incoming requests or don’t respond to them.
Let the Port Scan tool run and you will quickly start to see any open TCP ports and their traditionally identified usage. For example, you may see something like this if you scan localhost (127.0.0.1):
Port Scan has started…
Port Scanning host: 127.0.0.1
Open TCP Port: 22 ssh
Open TCP Port: 80 http
Open TCP Port: 88 kerberos
Open TCP Port: 445 microsoft-ds
Open TCP Port: 548 afpovertcp
Open TCP Port: 631 ipp
Open TCP Port: 3689 daap
Visible ports are going to differ per machine depending on what services and servers are available, but if you’re scanning Macs and PC’s you’ll commonly find web servers, SMB Windows sharing port 445, AFP Apple File Sharing on port 548, maybe active visible SSH server on 22, UDP servers, and potentially a wide variety of others. The port scan will go quite high as it scans, so just let it run if you want to see everything.
If you see absolutely nothing come up but you know an IP is active with open services, either the machine isn’t broadcasting, the recipient machine is rejecting all requests, or perhaps a strong firewall is configured. This makes Network Utility’s port scanner an excellent way to quickly check security and test out potential vulnerabilities or active services on neighboring Macs, iOS devices, Windows, Linux machines, and whatever other computers are getting scanned.
Network Utility is obviously limited to the Mac, and while there are no built-in tools on the iOS side of things, it is possible to perform port scanning from an iPhone and iPad with the fing app a free tool that is very handy addition to the advanced iOS users toolkit.
Источник