- Java 2 Standard Edition SDK (J2SE SDK)
- Quick guides
- Add certificate in Java on macOS
- How to preserve the CAcerts keystore on Mac across updates?
- 3 Answers 3
- How do I find out what keystore my JVM is using?
- 10 Answers 10
- How to Import Public Certificates into Java’s Truststore from a Browser
- Troubleshooting troublesome certificates
- Steps to follow
- Find your current Java version
- Get the Root CA SHA-1 fingerprint of the service from your browser
- List all the trusted public Root CAs in your Java truststore
- Check if the certificate from your browser already exists in the truststore
- Export the certificate(.cer file) from the browser
- Import the certificate(.cer file) into Java’s truststore:
- Important to remember
- References
- How to use ssl certificates in Java on a Mac
- 3 Answers 3
Java 2 Standard Edition SDK (J2SE SDK)
The latest J2SE SDK version can be downloaded from: http://java.sun.com/j2se/
Quick guides
Add certificate in Java on macOS
Information
I was using the ant get task to get files from https://www.mobilefish.com/..
The ant task shows the following error message:
javax.net.ssl.SSLHandshakeException: sun.security.validator.ValidatorException: PKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target at sun.security.ssl.Alerts.getSSLException(Alerts.java:192)
To solve this problem you need to add the SSL certificate to the Java keystore.
Operating system used
macOS (Sierra) 10.12.3
Procedure
- The Java keystore is located at.
Type: echo $JAVA_HOME/jre/lib/security
The Java keystore is the file: $JAVA_HOME/jre/lib/security/cacerts
Note:
This means that every installed java version has its own cacerts file.
If you use another java version you need to reinstall the certificate.
To show all certificates installed in the keystore.
Type: cd $JAVA_HOME/jre/lib/security
Type: keytool -list -keystore cacerts
The keystore password is (default): changeit
You should see:
Enter keystore password:
Keystore type: JKS
Keystore provider: SUN
Your keystore contains 104 entries
verisignclass2g2ca [jdk], Aug 25, 2016, trustedCertEntry,
Certificate fingerprint (SHA1): B3:EA:C4:4
:
Note:
If you want to see more detailed information, add the -v flag.
Type: keytool -list -v -keystore cacerts
Before you import the certificate in the keystore make a backup of the keystore.
Type: cd $JAVA_HOME/jre/lib/security
Type: sudo cp cacerts cacerts.orig
Import your self signed certificate in the keystore.
Type: cd $JAVA_HOME/jre/lib/security
Type: sudo keytool -importcert -alias domain -file /path/to/certificate.crt -keystore cacerts
For example, type:
sudo keytool -importcert -alias sand.mobilefish.com -file /etc/apache2/ssl/sand.mobilefish.crt -keystore cacerts
You should see:
Password: your_root_password
Enter keystore password: changeit
Owner: [email protected], CN=sand.mobilefish.com, OU=Research and development, O=Mobilefish.com, L=Zaandam, ST=Noord-Holland, C=NL
Issuer: [email protected], CN=sand.mobilefish.com, OU=Research and development, O=Mobilefish.com, L=Zaandam, ST=Noord-Holland, C=NL
Serial number: 8a7362fba9376522
Valid from: Fri Aug 25 13:04:25 CEST 2017 until: Mon Aug 23 13:04:25 CEST 2027
:
Trust this certificate? [no]: yes
Certificate was added to keystore
More information about the keytool.
Type: keytool -help
Источник
How to preserve the CAcerts keystore on Mac across updates?
Mac OS X has the CA keystore in /System/Library/Frameworks/JavaVM.framework/Home/lib/security/cacerts. This keystore seems to be overwritten by every Java update, which is very annoying since we have internal CAs for development environments, testing…
Is there a way to preserve keystore changes across Apple JSRs, and now, with Snow Leo JSR3, also across updates for the separate Java developer packages (whose JDKs use the same keystore)?
3 Answers 3
[ This is outdated info — see the answer below for 10.6+ ]
/System/Library/Frameworks/JavaVM.framework/Home/ is a symlink to Versions/CurrentJDK/Home within JavaVM.framework. Obviously this will change with a new Version. Use the full path (e.g. /System/Library/Frameworks/JavaVM.framework/Versions/1.6.0/Home ) and it won’t change across updates.
The following parameters can be used to specify the location of the cacerts file to java:
Make a copy of the cacerts in the java home directory (with internal CAs) and put it somewhere in your home directory. Then put the full path to the cacerts file location as the value of javax.net.ssl.trustStore property above. That copy will not get overwritten by Java updates. The default password is ‘changeit’.
Two downsides to this approach are:
- Your file won’t get any updates to the cacerts file in the sdk. This is primarily an issue if a certificate authority is compromised.
- Everywhere you need the custom cacerts (build tools, app server, etc), these parameters need to be specified.
Источник
How do I find out what keystore my JVM is using?
I need to import a certificate into my JVM keystore. I am using the following:
so I would need to probably change my call into something like:
10 Answers 10
Your keystore will be in your JAVA_HOME—> JRE —>lib—> security—> cacerts . You need to check where your JAVA_HOME is configured, possibly one of these places,
Computer—>Advanced —> Environment variables—> JAVA_HOME
Your server startup batch files.
In your import command -keystore cacerts (give full path to the above JRE here instead of just saying cacerts).
Keystore Location
Each keytool command has a -keystore option for specifying the name and location of the persistent keystore file for the keystore managed by keytool. The keystore is by default stored in a file named .keystore in the user’s home directory, as determined by the «user.home» system property. Given user name uName, the «user.home» property value defaults to
Thus, if the user name is «cathy», «user.home» defaults to
/.keystore file! If I left off the -keystore parameter, I couldn’t figure out which default keystore keytool targeting. I kept looking for other cacerts somewhere else on the machine. I didn’t expect keytool to generate
/.keystore in the home directory, nor for it to be named .keystore instead of cacerts . You’ve filled in a blank that the Java folks should document! Thank you!
Mac OS X 10.12 with Java 1.8:
From there it’s in:
I have a cacerts keystore in there.
To specify this as a VM option:
I’m not saying this is the correct way (Why doesn’t java know to look within JAVA_HOME?), but this is what I had to do to get it working.
Источник
How to Import Public Certificates into Java’s Truststore from a Browser
Troubleshooting troublesome certificates
- Were you ever able to connect to an HTTPS service endpoint from your browser but not from a Java application?
- Do you know where to fetch certificates?
- Has your server’s HTTPS SSL certificate changed?
- Is your version of Java unable to recognize a Root CA?
If you have faced any of these issues, this article might help.
Recently, while I started an application on my local system that connects to an HTTP service endpoint over SSL, I got an error (shown below) as the application was not able to recognize the Root Certificate Authority(CA) of the endpoint.
The error message indicates that the application could not establish a secured connection over SSL (you may see this issue if you are using a certificate that is issued by an internal Certificate Authority or Self-Signed certificate). The trust is handled by having root and intermediate (may not be required if using the default JVM security setting) certificates of your SSL certificate on a trusted keystore which I was missing. I didn’t know where to look for the right certificate so I did a bit of digging.
Since I could connect to the endpoint in the browser over SSL, I extracted the Root CA certificate from the browser and inserted it into my Java truststore. Viola, I could successfully access the HTTPS endpoint from my application!
Steps to follow
Find your current Java version
- If you have multiple Java versions, you need to decide which version of Java to use with the certificate.
Get the Root CA SHA-1 fingerprint of the service from your browser
- Go to the HTTPS service endpoint in your browser
- Click on the lock button on the address bar
- Go to Certificate
- Select the Root Certificate Authority(top-level parent)
- Get the SHA-1 fingerprint of the Root CA. This example is from the screenshot below:
List all the trusted public Root CAs in your Java truststore
- Navigate to the $JAVA_HOME/jre/lib/security folder for the cacerts file
- cacerts is the default Java truststore. A truststore authenticates peers. A keystore authenticates yourself. cacerts is where Java stores public certificates of trusted Root CAs
- Use the following command (on Unix, a similar command is available in other OSes) to list the existing certs in the truststore:
- This truststore contains 95 entries with the name of the Root CA along with trusted SHA-1 certificate fingerprints as shown below:
Check if the certificate from your browser already exists in the truststore
- From the above list of trusted entries in the truststore, search for the SHA-1 fingerprint from the browser
- If the SHA-1 fingerprint from the browser doesn’t exist in your truststore, proceed to the steps below
Export the certificate(.cer file) from the browser
- I’ll be exporting the certificate for an HTTPS endpoint from Chrome on Mac
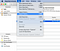
- Go to chrome://settings/privacyin the address bar
- Click on Manage certificates to open the Keychain Accesstool on Mac
- On the left side of Keychain Access tool, select System under Keychains and My Certificates under Category
- Select the certificate you want to export, then File > Export Items > Select .cer file format > Save
Import the certificate(.cer file) into Java’s truststore:
- Be careful to only import the certificates to the truststore that you trust
- After you export the certificate from the browser into .cer file, you need to import it into the truststore as follows:
- After you have successfully imported the certificate, you can check if it exists in the truststore based on the alias and the fingerprints of the Root CA
- Restart your JVM and your application should now be able to recognize the Root CA and connect to the endpoint over SSL
Important to remember
- If you need to delete a certificate from the truststore that was inserted by accident:
- Instead of adding the certificate to the default Java truststore, you can also create a custom truststore and add it as a JVM parameter while starting the application:
- cacerts files correspond to a version of Java. If you have multiple versions be mindful that you might have to insert the certificate in the right version of Java
References
Please reach out to me if you have any questions/ suggestions or if you think anything is not accurate.
Источник
How to use ssl certificates in Java on a Mac
I found this question: Import Windows certificates to Java, which had the answer for a Windows machine. I have been unable to find the equivalent to -Djavax.net.ssl.trustStoreType=WINDOWS-ROOT for MacOS.
3 Answers 3
On OSX you can set -Djavax.net.ssl.trustStoreType=KeychainStore to use the OSX keychain for trusted certificates; which is part of the Apple JCA Provider.
Jacob Blanton provided the solution in his comment, above. By adding -Djavax.net.ssl.trustStore=
to MAVEN_OPTS in my .bash_profile, both standalone Maven and Maven in Eclipse were able to access the repo as needed [after I installed the cert to cacerts using the instructions Jorge Campos linked to in his comment, found here https://blog.alwold.com/2011/06/30/how-to-trust-a-certificate-in-java-on-mac-os-x/ ]
- The path java in my case was: «/Library/Java/JavaVirtualMachines/jdk1.8.0_211.jdk/Contents/Home»
- In my
/.bash_profile I put this line:
export JAVA_HOME=»/Library/Java/JavaVirtualMachines/jdk1.8.0_211.jdk/Contents/Home»
after that I typed source ˜/.bash_profile
type echo echo $JAVA_HOME
- You should see something like that:
java version «1.8.0_211»
Java(TM) SE Runtime Environment (build 1.8.0_211-b12)
Java HotSpot(TM) 64-Bit Server VM (build 25.211-b12, mixed mode)
Источник