- SSH port forwarding — Example, command, server config
- Contents
- What Is SSH Port Forwarding, aka SSH Tunneling?
- Local Forwarding
- Remote Forwarding
- Opening Backdoors into the Enterprise
- Server-Side Configuration
- How to Prevent SSH Port Forwarding from Circumventing Firewalls
- Manas Tungare
- Parameters
- local_port
- service_host
- service_port
- ssh_server_host
- ssh_server_port
- ssh_server_username
- The Entire Command, Line by Line
- Common Errors and Solutions
- Error message: channel 3: open failed: connect failed: Connection refused
- Cannot listen on port X on local machine because of network policies.
- Error message: Privileged ports can only be forwarded by root.
- Error message: bind: Address already in use, channel_setup_fwd_listener: cannot listen to port: xxxx, Could not request local forwarding.
- I want other hosts on my network to be able to use the tunnel I established.
- I don’t know what local port is available for me to use.
- Как сделать переадресацию портов в Mac OS X
- 6 ответов
SSH port forwarding — Example, command, server config
Contents
What Is SSH Port Forwarding, aka SSH Tunneling?
SSH port forwarding is a mechanism in SSH for tunneling application ports from the client machine to the server machine, or vice versa. It can be used for adding encryption to legacy applications, going through firewalls, and some system administrators and IT professionals use it for opening backdoors into the internal network from their home machines. It can also be abused by hackers and malware to open access from the Internet to the internal network. See the SSH tunneling page for a broader overview.
Local Forwarding
Local forwarding is used to forward a port from the client machine to the server machine. Basically, the SSH client listens for connections on a configured port, and when it receives a connection, it tunnels the connection to an SSH server . The server connects to a configurated destination port, possibly on a different machine than the SSH server.
Typical uses for local port forwarding include:
Tunneling sessions and file transfers through jump servers
Connecting to a service on an internal network from the outside
Connecting to a remote file share over the Internet
Quite a few organizations for all incoming SSH access through a single jump server . The server may be a standard Linux/Unix box, usually with some extra hardening, intrusion detection, and/or logging, or it may be a commercial jump server solution.
Many jump servers allow incoming port forwarding, once the connection has been authenticated. Such port forwarding is convenient, because it allows tech-savvy users to use internal resources quite transparently. For example, they may forward a port on their local machine to the corporate intranet web server, to an internal mail server’s IMAP port, to a local file server’s 445 and 139 ports, to a printer, to a version control repository, or to almost any other system on the internal network. Frequently, the port is tunneled to an SSH port on an internal machine.
In OpenSSH , local port forwarding is configured using the -L option:
This example opens a connection to the gw.example.com jump server, and forwards any connection to port 80 on the local machine to port 80 on intra.example.com .
By default, anyone (even on different machines) can connect to the specified port on the SSH client machine. However, this can be restricted to programs on the same host by supplying a bind address:
The LocalForward option in the OpenSSH client configuration file can be used to configure forwarding without having to specify it on command line.
Remote Forwarding
In OpenSSH, remote SSH port forwardings are specified using the -R option. For example:
This allows anyone on the remote server to connect to TCP port 8080 on the remote server. The connection will then be tunneled back to the client host, and the client then makes a TCP connection to port 80 on localhost . Any other host name or IP address could be used instead of localhost to specify the host to connect to.
This particular example would be useful for giving someone on the outside access to an internal web server. Or exposing an internal web application to the public Internet. This could be done by an employee working from home, or by an attacker.
By default, OpenSSH only allows connecting to remote forwarded ports from the server host. However, the GatewayPorts option in the server configuration file sshd_config can be used to control this. The following alternatives are possible:
This prevents connecting to forwarded ports from outside the server computer.
This allows anyone to connect to the forwarded ports. If the server is on the public Internet, anyone on the Internet can connect to the port.
This means that the client can specify an IP address from which connections to the port are allowed. The syntax for this is:
In this example, only connections from the IP address 52.194.1.73 to port 8080 are allowed.
OpenSSH also allows the forwarded remote port to specified as 0. In this case, the server will dynamically allocate a port and report it to the client. When used with the -O forward option, the client will print the allocated port number to standard output.
Opening Backdoors into the Enterprise
Remote SSH port forwarding is commonly used by employees to open backdoors into the enterprise. For example, the employee may set get a free-tier server from Amazon AWS , and log in from the office to that server, specifying remote forwarding from a port on the server to some server or application on the internal enterprise network. Multiple remote forwards may be specified to open access to more than one application.
The employee would also set GatewayPorts yes on the server (most employees do not have fixed IP addresses at home, so they cannot restrict the IP address).
For example, the following command opens access to an internal Postgres database at port 5432 and an internal SSH port at port 2222.
Server-Side Configuration
The AllowTcpForwarding option in the OpenSSH server configuration file must be enabled on the server to allow port forwarding. By default, forwarding is allowed. Possible values for this option are yes or all to allow all TCP forwarding, no to prevent all TCP forwarding, local to allow local forwardings, and remote to allow remote forwardings.
Another option of interest is AllowStreamLocalForwarding , which can be used to forward Unix domain sockets. It allows the same values as AllowTcpForwarding . The default is yes .
The GatewayPorts configuration option as described above also affects remote port forwardings. Possible values were no (only local connections from server host allowed; default), yes (anyone on the Internet can connect to remote forwarded ports), and clientspecified (client can specify an IP address that can connect, anyone can if not specified).
How to Prevent SSH Port Forwarding from Circumventing Firewalls
We recommend that port forwarding be expressly disabled when not needed. Leaving port forwarding enabled can expose the organization to security risks and backdoors. For example, if a server intended to only provide SFTP file transfers allows port forwardings, those forwardings might be used to gain unintended access into the internal network from the Intranet.
The problem is that port forwarding can in practice only be prevented by a server or firewall. An enterprise cannot control all servers on the Internet. Firewall-based control can also be tricky, as most organizations have servers in Amazon AWS and other cloud services, and those servers are usually accessed using SSH.
Источник
Manas Tungare
After spending about an hour configuring what should, in theory, be a simple matter, I figured I’d write a blog post that might one day save another soul an hour or so from his or her life. So, for good karma, basically. In the past, I have set up port forwarding on Linux, Mac OS X and Windows, so I was a little worried that it took me about an hour trying to appease the SSH deities (and daemons).
The command itself is just a single line; the devil is in the parameters. I’m splitting the command over several lines and adding line numbers to illustrate the details and separate the parts of the long-ish command for easier explanation. Feel free to type it all on a single line (after removing the line numbers and the line-break markers ( «\» ) of course!)
Parameters
Now for the various parameters used in the command above. Some of them may be omitted if the defaults are used, but I have included all of them in the example above to cover the most general case.
local_port
The port on your local machine that your local program expects to be able to connect to. If this is one of the reserved ports (i.e., under 1023), you will have to run your ssh tunnel command as root (using sudo). Ports above 1024 are freely available for any user to listen on.
service_host
The fully-qualified domain name or the IP address of the server that is hosting the service that you wish to connect to. For example, if this is a web site, it could be google.com or yahoo.com. It does not have to be under your control, nor does it have to be the machine that you’re SSHing into. It is just any host on the Internet that you can access from ssh_server_host . Often this is a server you are not allowed to access from your own machine, e.g. a chat server or IRC server. Or you may wish to hide the fact from the administrator of your local network that you are connecting to this server (e.g. when you’re out at a coffee shop on a sniffable insecure wireless network, or in a country with laws forbidding access to free information.)
Important: If you’re trying to access a service running on the same machine as ssh_server_host , remember to use 127.0.0.1, not localhost. What’s the difference, you say? Well, since IPv6 is here to stay, localhost can map to either 127.0.0.1 (IPv4) or ::1/128 (IPv6). If your applications aren’t all IPv6-compliant, this can cause some headache. Hopefully, we will all be on IPv6 in the near future, but till then, this is a way to make things work. If you’re trying to use IPv6, you need to use **local_port**/**service_host**/**service_port** (slashes instead of colons.)
service_port
The port number on which the desired service is running. Here are some common port numbers:
| Service | Port |
|---|---|
| Web: HTTP | 80 |
| Web over SSL: HTTPS | 443 |
| Outgoing email: SMTP | 25 |
| Incoming email: POP3 | 110 |
| Incoming email: IMAP | 143 |
| VNC | 5900 |
| iTunes Music Sharing | 3689 |
ssh_server_host
The machine that you’re SSHing into. This is the one that is running sshd, the SSH daemon.
ssh_server_port
The port number on which the SSH daemon is listening on ssh_server_host . This is most likely 22; you should only use a different value if your sysadmin has told you that the SSH server is running on another port (or if you’re a sysadmin yourself and you set up your SSH server to run on a non-standard port for security through obscurity.)
ssh_server_username
The username you would use to connect to ssh_server_host in a regular SSH session. This may or may not be the same as the username you currently use on your local machine.
The Entire Command, Line by Line
- Line 1 simply calls the ssh program;
- Line 2 sets up the port forwarding. The **-L** parameter specifies that this is a remote-to-local tunnel. If you wanted to create a local-to-remote tunnel, you’d have used **-R** instead of **-L** . The next three parameters are from our list above, separated by colons. (Use slashes instead of colons for IPv6.) If you want to set up multiple tunnels from the same host, simply repeat line 2 as many times as you’d like, once for each set of **local_port:service_host:service_port** .
- Line 3 selects a port on the ssh_server_host to connect to. Omit this line if you’re connecting to the default port 22.
- Line 4 specifies the username to use on the ssh_server_host . It is also possible to use the **ssh_server_username@ssh_server_host** syntax instead of the -l parameter.
- Line 5 indicates to ssh that no commands be run on the remote system. Since you’re using this SSH connection simply for tunneling, this is a useful option to set.
- Line 6 contains the most basic parameter of this entire process. Please don’t get this wrong.
Common Errors and Solutions
Error message: channel 3: open failed: connect failed: Connection refused
Change localhost to 127.0.0.1 in the ssh -L parameter.
Cannot listen on port X on local machine because of network policies.
Try to use another port locally. Ports such as 3306 (MySQL) may have been left open. These are good to use for SSH tunneling if you aren’t already running MySQL.
Error message: Privileged ports can only be forwarded by root.
Use a port above 1024, or try to set up the SSH tunnel as root.
Error message: bind: Address already in use, channel_setup_fwd_listener: cannot listen to port: xxxx, Could not request local forwarding.
Some local server process is already listening on the local port you’re trying to forward to. Pick a different local port and configure your program to connect to th at port instead. If your program cannot be configured to listen to a different port, try to find what server process is occupying that port ( netstat -a on Linux or lsof -i -P on Mac OS X) and stop it. Retry setting up the tunnel.
I want other hosts on my network to be able to use the tunnel I established.
By default, only local clients can connect to SSH tunnels established this way.
Use the -g option when setting up the tunnel. Realize that this is insecure, but it may make sense in certain scenarios.
I don’t know what local port is available for me to use.
Linux: netstat -a | grep LISTEN
Mac OS X: lsof -i -P | grep LISTEN
will show you the ports that are in use. Generally, you can pick any that’s not already taken. To make sure you’re not breaking some other unknown protocol, check the IANA Well-known Port Numbers list and pick one that’s not taken.
If you’ve not been able to debug this so far, try passing the -v parameter to ssh to see verbose output. Add another -v for more verbose output.
If you’re reading this, and come across any specific source of trouble, please let me know so I can add it to this mini HOWTO.
Источник
Как сделать переадресацию портов в Mac OS X
Я хотел бы сделать все входящие подключения к порту 1000 моего хоста (IP: 200.234.XXX.XXX) перенаправить на порт 80 на хосте 10.211.55.5
Как я могу сделать это на моем хосте? Он работает под управлением Mac OS X 10.5.8
6 ответов
довольно просто сделать, Во-первых, вам нужно будет включить службу удаленного входа в систему на вашем mac (Системные Настройки ->обмен ->Удаленный Вход). Это запускает SSH-сервер.
затем выполните следующую команду в терминале OS X:
вы, возможно, потребуется принять отпечаток пальца сервера первоначально, а также введите свой локальный пароль для входа ssh. (Вы также можете настроить локальный для локального ssh открытый / закрытый ключ для сделайте это не запрашивать пароль, оставит, что в качестве упражнения для читателя.)
очень простое использование универсального инструмента ncat:
sudo ncat —sh-exec «ncat 10.211.55.5 80» -l 1000 —keep-open
получить двоичные файлы ncat / nmap для Mac OS X с официального сайта: http://nmap.org/download.html#macosx
EDIT: добавлен sudo для прослушивания ограниченного порта
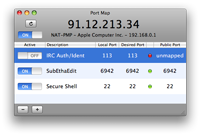
предполагая, что у вас есть маршрутизатор UPnP, его легко настроить порты с помощью PortMap
Он имеет очень простой пользовательский интерфейс.
Ну, я могу сказать вам, как я делаю такие вещи на моем Mac OS X 10.5.8 системы.
Я начал с ответа о NAT, но я думаю, что вам действительно нужна программа пересылки TCP (вы упоминаете «прокси» и переадресацию портов.)
есть несколько способов сделать это, в зависимости от ваших потребностей, даже » SSH » может быть нажата в действие, хотя мой любимый короткий и сладкий способ-это скрипт Perl tcpforward.
Если вам нужна манипуляция HTTP (вы, возможно, потребуется настроить http перенаправляет, так что, когда запрос приходит на URL без завершающего ‘ / ‘ вы не получите перенаправлены на реальный, недоступный, сервер), то Apache может сделать работу обратного прокси-сервера. Вы захотите посмотреть на mod_proxy и в частности ProxyPass и ProxyPassReverse. Делай не включить ProxyRequests, это для прямого проксирования. Для этого можно использовать собственный Apache Mac OS, если у вас он работает. Он приходит с mod_proxy и /и т. д./httpd/httpd сервер.conf-файл конфигурации для обновления.
даже с Apache, вам нужно убедиться, что все ссылки в содержании реального сервера относительны, если они ссылаются на реальный сервер, то вы можете попробовать модуль mod_proxy_html (у меня нет опыта, насколько хорошо это работает.)
Источник