- NetworkMiner
- Download NetworkMiner
- Networkminer kali linux ���������
- Networkminer kali linux ���������
- Carving Packets from Memory
- Walkthrough of DFIR Madness PCAP
- NetworkMiner 2.7 Released
- Network Forensics Classes for EU and US
- Detecting Cobalt Strike and Hancitor traffic in PCAP
- CapLoader 1.9 Released
- Running NetworkMiner in Windows Sandbox
- Analysing a malware PCAP with IcedID and Cobalt Strike traffic
NetworkMiner
NetworkMiner is an open source Network Forensic Analysis Tool (NFAT) for Windows (but also works in Linux / Mac OS X / FreeBSD). NetworkMiner can be used as a passive network sniffer/packet capturing tool in order to detect operating systems, sessions, hostnames, open ports etc. without putting any traffic on the network. NetworkMiner can also parse PCAP files for off-line analysis and to regenerate/reassemble transmitted files and certificates from PCAP files.
NetworkMiner makes it easy to perform advanced Network Traffic Analysis (NTA) by providing extracted artifacts in an intuitive user interface. The way data is presented not only makes the analysis simpler, it also saves valuable time for the analyst or forensic investigator.
NetworkMiner has, since the first release in 2007, become a popular tool among incident response teams as well as law enforcement. NetworkMiner is today used by companies and organizations all over the world.
| NetworkMiner (free edition) | NetworkMiner Professional | |
|---|---|---|
| Live sniffing |  |  |
| Parse PCAP files |  |  |
| Parse PcapNG files |  | |
| IPv6 support |  |  |
| Extract files from FTP, TFTP, HTTP, HTTP/2, SMB, SMB2, SMTP, POP3, IMAP and LPR traffic |  |  |
| Extract X.509 certificates from SSL encrypted traffic like HTTPS, SMTPS, IMAPS, POP3S, FTPS etc. |  |  |
| Decapsulation of GRE, 802.1Q, PPPoE, VXLAN, OpenFlow, SOCKS, MPLS and EoMPLS |  |  |
| Receive Pcap-over-IP |  |  |
| Runs in Windows and Linux |  |  |
| OS Fingerprinting (*) |  |  |
| JA3 and JA3S hash extraction |  |  |
| Audio extraction and playback of VoIP calls |  | |
| OSINT lookups of file hashes, IP addresses, domain names and URLs |  | |
| Port Independent Protocol Identification (PIPI) |  | |
| User Defined Port-to-Protocol Mappings (decode as) |  | |
| Export to CSV / Excel / XML / CASE / JSON-LD |  | |
| Configurable file output directory |  | |
| Configurable time zone (UTC, local or custom) |  | |
| Geo IP localization (**) |  | |
| DNS Whitelisting (***) |  | |
| Advanced OS fingerprinting |  | |
| Web browser tracing (4:10 into this video) |  | |
| Online ad and tracker detection |  | |
| Host coloring support |  | |
| Command line scripting support |  (through NetworkMinerCLI) (through NetworkMinerCLI) | |
| Price | Free | $ 1200 USD |
| Download NetworkMiner | ||
| * Fingerprinting of Operating Systems (OS) is performed by using databases from Satori and p0f ** This product includes GeoLite data created by MaxMind, available from http://maxmind.com/ *** Domain names in the DNS tab are checked against the Alexa top 1,000,000 sites | ||
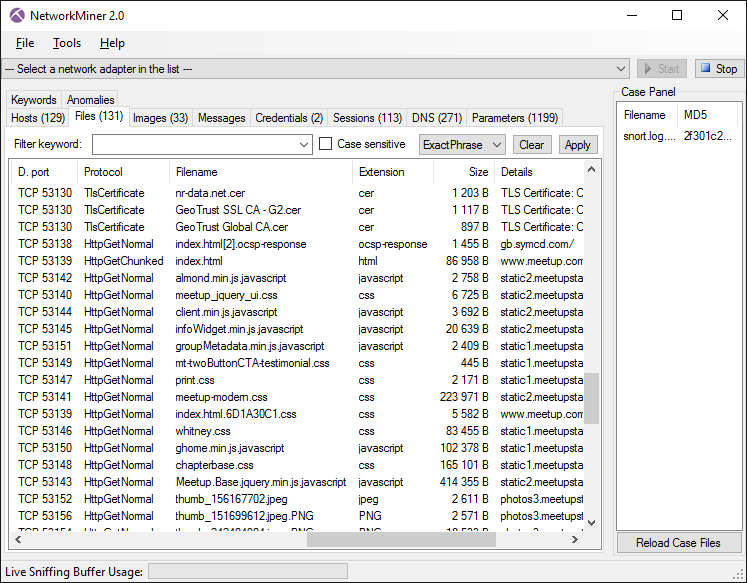
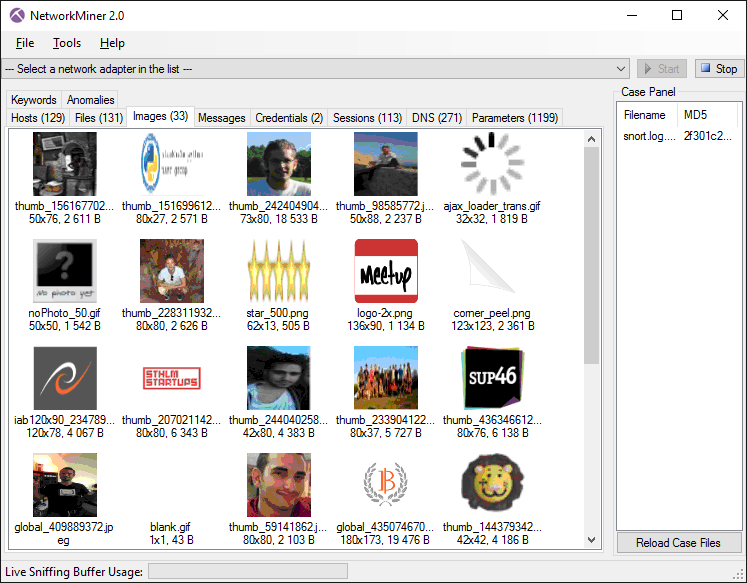
NetworkMiner can extract files, emails and certificates transferred over the network by parsing a PCAP file or by sniffing traffic directly from the network.
NetworkMiner showing files extracted from sniffed network traffic to disk
NetworkMiner showing thumbnails for images extracted to disk
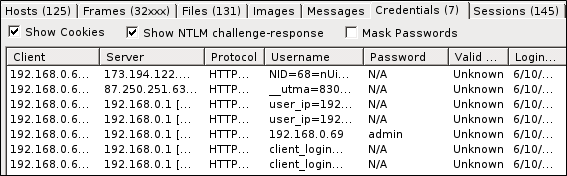
User credentials (usernames and passwords) for supported protocols are extracted by NetworkMiner and displayed under the «Credentials» tab. The credentials tab sometimes also show information that can be used to identify a particular person, such as user accounts for popular online services like Gmail or Facebook.

Another very useful feature is that the user can search sniffed or stored data for keywords. NetworkMiner allows the user to insert arbitrary string or byte-patterns that shall be searched for with the keyword search functionality.
NetworkMiner Professional can be delivered either as an Electronic Software Download (ESD) or shipped physically on a USB flash drive. The product is exactly the same, regardless of delivery method. NetworkMiner is a portable application that doesn’t require any installation, which means that the USB version can be run directly from the USB flash drive. However, we recommend that you copy NetworkMiner to the local hard drive of your computer in order to achieve maximum performance.
Download NetworkMiner
The latest version of NetworkMiner can be downloaded from:
» https://www.netresec.com/?download=NetworkMiner « (executable application)
SHA256 hash: df4057eb0256dab23dee9c248d60db11d46b20d344d8769ca0e5768afd76dd3f
» https://www.netresec.com/?page=NetworkMinerSourceCode « (source code)
SHA256 hash: 7afaf30e2907e9df3cf68fce1869b04e8bd667e5ac4619cea2a014445a38d330
For older releases of NetworkMiner (prior to version 2.0), please visit the NetworkMiner page on SourceForge:
http://sourceforge.net/projects/networkminer/files/networkminer/
However, please note that we no longer release new versions of NetworkMiner on SourceForge.
Источник
Networkminer kali linux ���������
Недавно, при обсуждении в одном чате вопроса: как из Wireshark вытащить файл, всплыла утилита NetworkMiner. Пообщавшись с коллегами и по гуглив в Интернете, я сделал вывод, что об этой утилите знает не так много народу. Так как утилита в разы упрощает жизнь исследователя/пентестера, то исправляю этот недостаток и расскажу сообществу о том, что же такое NetworkMiner.
NetworkMiner – утилита для перехвата и анализа сетевого траффика между хостами локальной сети, написанная под ОС Windows (но также работает в Linux, Mac OS X, FreeBSD).
NetworkMiner может быть использована в качестве пассивного сниффера сетевых пакетов, анализ которых позволит обнаружить фингерпринт операционных систем, сессий, хостов, а также открытые порты. NetworkMiner также позволяет анализировать PCAP файлы в автономном режиме и восстановить передаваемые файлы и сертификаты безопасности.
И так, приступим к рассмотрению.
Утилита доступна в двух редакциях: Free и Professional (стоимость 700 USD).
В редакции Free доступны следующие опции:
- перехват траффика;
- разбор PCAP файла;
- прием PCAP файла по IP;
- определение ОС.
В редакции Professional добавляются опции:
- разбор PcapNG файла,
- Определение протокола порта,
- Экспорт данных в CSV / Excel,
- Проверка DNS имен по сайту http://www.alexa.com/topsites,
- Локализация по IP,
- Поддержка командной строки.
В данной статье рассмотрим опцию разбор PCAP файла, полученного от Wireshark.
Но для начала установим NetworkMiner в Kali Linux.
- По умолчанию, пакеты Mono уже стоят в KaliLinux, но если они не установлены, то выполняем следующее действие:
sudo apt-get install libmono-winforms2.0-cil
- Далее скачиваем и устанавливаем NetworkMiner
wget sf.net/projects/networkminer/files/latest -O /tmp/nm.zip
sudo unzip /tmp/nm.zip -d /opt/
cd /opt/NetworkMiner*
sudo chmod +x NetworkMiner.exe
sudo chmod -R go+w AsscodebledFiles/
sudo chmod -R go+w Captures/
- Чтобы запустить NetworkMiner используем следующую команду:
Далее запустим Wireshark, соберем траффик в нашей локальной сети и сохраним в файл PCAP.
Для информации. Пять минут перехвата траффика у себя в тестовой сети собрало более 30 000 различных пакетов.
Как понимаете, анализировать такой трафик достаточно трудоемко и по времени затратно. Wireshark обладает встроенными фильтрами и достаточно гибок, но что делать когда надо быстро проанализировать траффик, не изучая всего многообразия Wireshark?
Попробуем посмотреть какую информацию нам предоставит NetworkMiner.
- Открываем полученный PCAP в NetworkMiner. Понадобилось меньше минуты, чтобы проанализировать дамп траффика из более 30 000 пакетов.
- На вкладке Hosts приводится список всех хостов, участвующих в формирование траффика, с детальной информацией по каждому хосту:
- На вкладке Frames, трафик приводится в виде пакетов с информацией по каждому уровню модели OSI (Канальному, Сетевому и Транспортному).
- Следующая вкладка Credentials покажет перехваченные попытки авторизации в открытом виде. Вот так потратив меньше минуты можно из большого дампа трафика сразу получить логин и пароль на авторизацию. Я это делал на примере своего роутера.
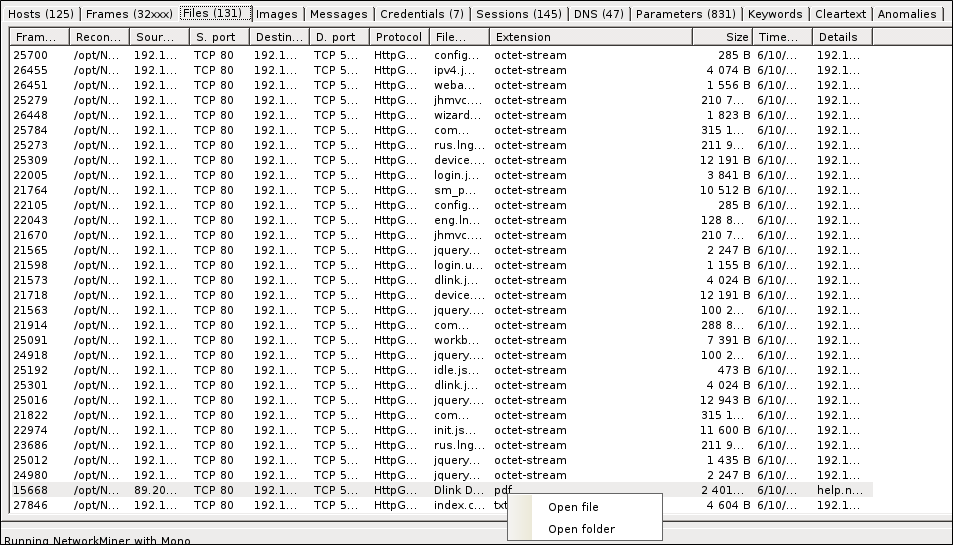
- И еще одна вкладка, которая облегчает получение данных из трафика – это Files.
В нашем примере мне попался pdf файл, который можно сразу открыть и посмотреть.
Но больше всего я удивился, когда обнаружил в дампе трафика — txt файл, как оказалось от моего роутера DIR-620. Так вот этот роутер, при авторизации на нем, передает в текстовом виде все свои настройки и пароли, в том числе от WPA2.
В итоге, утилита оказалась довольно интересная и полезная.
Тебе, дорогой читатель, отдаю на прочтение данную статью, а я пошел покупать новый роутер.
Источник
Networkminer kali linux ���������
In this video I demonstrate that text typed into the Windows 10 start menu gets sent to Microsoft and how that traffic can be intercepted, decrypted and parsed.
The video cannot be played in your browser.
The XML files shown in the video were sent by Cortana’s «SmartSearch» app to in HTTP/2 POST requests. As shown in the video, the POST’ed keystrokes can be found inside requestInfo XML tags that have a «RawQuery» key.
The following tcpdump and grep commands can be used to list the RawQuery data sent to Bing in these HTTP/2 requests:
Running that command on the PolarProxy PCAP file from the video gives the following output:
The same data also gets sent in the query string variable «qry» of GET requests for , as shown in this NetworkMiner screenshot.
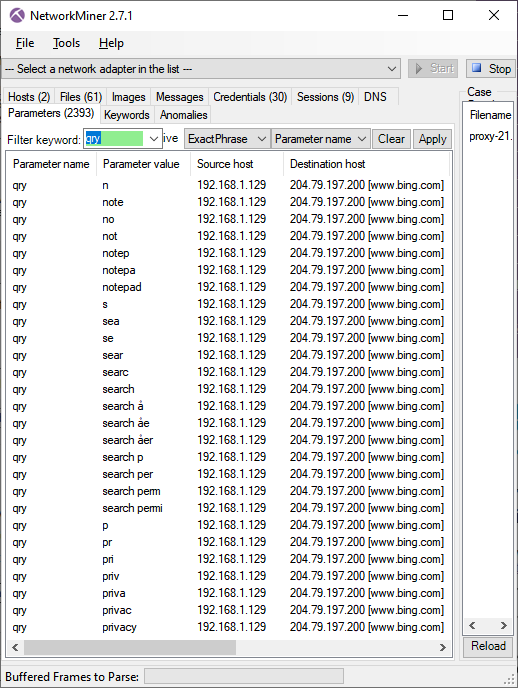
Image: NetworkMiner’s Parameters tab with filter «qry» on «Parameter name» column
How to Intercept, Decrypt and Decode HTTPS Traffic
The following section presents the technical details regarding my setup, so that others can reproduce and verify these findings.
My first step was to install PolarProxy on a Linux machine on the local network. PolarProxy is a TLS proxy, which can intercept and decrypt TLS traffic. This TLS proxy is primarily designed to decrypt traffic from malware and hackers, but can also be used to decrypt legitimate traffic when needed.
PolarProxy was configured to listen for incoming TLS connections on TCP port 443 and output PCAP data with the decrypted traffic as if it had been transmitted over TCP 80. The decrypted traffic was accessible as a real-time stream through a PCAP-over-IP service running on port 57012. Here’s the full command that was used to start PolarProxy:
In the video I showed the Windows 10 client’s modified hosts file, which included an entry for www.bing.com pointing to the PolarProxy machine. What was not shown in the video though, is that PolarProxy’s own CA certificate had been added to the Win10 machine’s list of trusted root CA’s, as explained in the «Trusting the PolarProxy root CA» section of the PolarProxy installation instructions. With these two changes in place all HTTPS requests for www.bing.com from the Win10 PC got diverted through the PolarProxy TLS inspection service, which then decrypted and re-encrypted the traffic before forwarding it to Bing.
The decrypted Bing requests could be accessed either locally on the Linux machine, or remotely using the PCAP-over-IP service on TCP port 57012. I used NetworkMiner to read the live PCAP stream with decrypted traffic from port 57012 and extract all files being sent and received in real-time.
Is it Possible to Disable the Cortana Search?
When Ars Technica reporters asked Microsoft back in 2015 if there was any way to disable this communication, Microsoft replied with the following statement:
As part of delivering Windows 10 as a service, updates may be delivered to provide ongoing new features to Bing search, such as new visual layouts, styles and search code. No query or search usage data is sent to Microsoft, in accordance with the customer’s chosen privacy settings.
There are plenty of how-to guides online with instructions on how the Cortana search feature can be disabled. Most of these guides suggest disabling the AllowCortana setting in group policies or in the registry. We’ve tried several of the settings suggested in these how-to guides, but none of them seem to prevent Windows from sending keystrokes to Bing.
If you know how to successfully disable Cortana’s Bing searches, then please feel free to reach out to us so that we can update this blog post.
UPDATE 210928 — How to Actually Disable Cortana Search
Twitter user @GeorgeProfonde3 reached out to suggest a fix that might prevent the start menu from sending data to Bing. We have now verified this fix and we’re happy to announce that it works (at least for us).
- Start regedit
- Open the following registry key:
- Ensure that the value for CortanaConsent is set to 0
- Create a new DWORD registry entry called «BingSearchEnabled» with value 0
You should no longer see any connections to www.bing.com when interacting with the start menu after implementing this fix. We’re still not sure how to disable the cortana search traffic using Group Policies though.
Posted by Erik Hjelmvik on Tuesday, 28 September 2021 08:24:00 (UTC/GMT)





Carving Packets from Memory
Someone who says «We’re gonna pull the packet captures out of the router» probably has no clue how to capture network traffic. In the Lindell case, statements like these were results of an elaborate hoax.
Nevertheless, such a statement doesn’t have to be nonsense — if it comes from someone who knows how to dump the physical memory from the router. There are actually more packets available in the RAM of a router, or computer for that matter, than you might think.
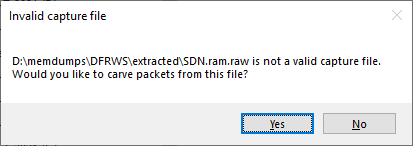
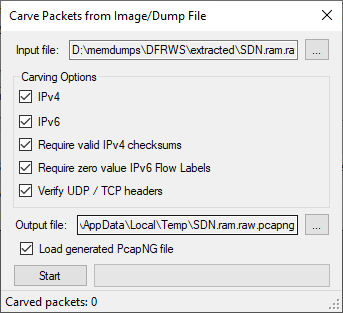
The Forensic Challenge from DFRWS 2016 contains a memory dump from an SDN switch. If you drag-and-drop SDN.ram.raw from that challenge to CapLoader then you’ll be asked if you wanna carve packets from the memory dump.
This packet carving feature is also available in the free trial version of CapLoader.
Clicking «Yes» in the dialogue brings up a configuration window. The default settings are okay in most cases.
After pressing «Start» CapLoader will start identifying packets in the memory dump from the SDN switch. The packets will be saved to a Pcap-NG file located in the %TEMP% directory, unless you specified a different output location in the config window.
You can download a copy of the Pcap-NG file that I generated with CapLoader 1.9.2 here:
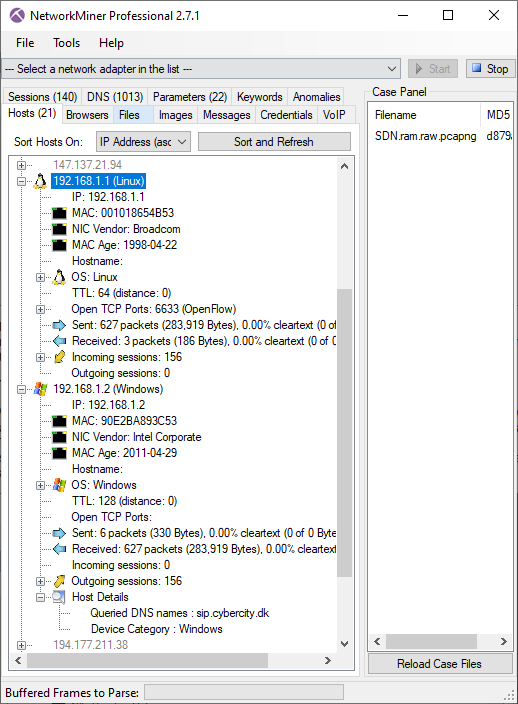
Here’s what it looks like when the carved packets have been loaded into NetworkMiner Professional.
As you can see, a great deal of information can be extracted about the hosts on this network just by examining the dumped memory from the SDN switch.
What about Bulk Extractor?
Simson Garfinkel’s bulk_extractor can also extract packets from memory dumps. It was actually a research paper by Simson that inspired me to implement a packet carver in the first place.
There are a few significant differences between bulk_extractor and CapLoader with regards to packet carving though. One difference is that bulk_extractor identifies network packets by looking for Ethernet frames containing IPv4 packets, while CapLoader looks for IPv4 or IPv6 packets containing TCP or UDP packets. The output from bulk_extractor is usually quite similar to that of CapLoader, and so is the parsing speed. CapLoader was just slightly faster in our tests and carved about 3% more packets compared to bulk_extractor, these additional packets were primarily IPv6 packets and packets that weren’t encapsulated by an Ethernet frame.
Where can I download memory dumps?
I posted a question on Twitter, asking the #DFIR community for their favorite publicly available memory dumps prior to writing this blog post, and I received lots of great answers. Thank you all for contributing! I have now compiled the following list of places from where you can download memory dumps:
For a more detailed blog post on CapLoader’s packet carving functionality, please see our Carving Network Packets from Memory Dump Files blog post from 2014.
Posted by Erik Hjelmvik on Tuesday, 31 August 2021 15:10:00 (UTC/GMT)





Walkthrough of DFIR Madness PCAP
I recently came across a fantastic digital forensics dataset at dfirmadness.com, which was created by James Smith. There is a case called The Stolen Szechuan Sauce on this website that includes forensic artifacts like disk images, memory dumps and a PCAP file (well, pcap-ng actually). In this video I demonstrate how I analyzed the capture file case001.pcap from this case.
The video cannot be played in your browser.
Follow Along in the Analysis
Please feel free to follow along in the analysis performed in the video. You should be able to use the free trial version of CapLoader and the free open source version of NetworkMiner to perform most of the tasks I did in the video.
Here are some of the BPF and Column Criteria filters that I used in the video, so that you can copy/paste them into CapLoader.
- net 10.0.0.0/8
- Umbrella_Domain =
- not ip6 and not net 224.0.0.0/4
- host 194.61.24.102 or host 203.78.103.109 or port 3389
References and Links
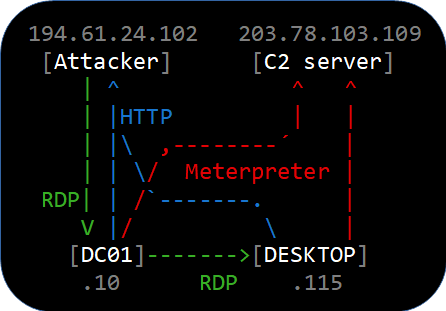
All events in this timeline take place on September 19, 2020. Timestamps are in UTC.
- 02:19:26 194.61.24.102 performs RDP brute force password attack against DC01.
- 02:21:47 RDP password brute force successful.
- 02:22:08 194.61.24.102 connects to DC01’s RDP service as Administrator.
- 02:22:36 194.61.24.102 connects to DC01’s RDP service as Administrator again.
- 02:24:06 DC01 downloads coreupdater.exe from 194.61.24.102 using IE11.
- 02:25:18 DC01 establishes Metrepreter reverse_tcp connection to 203.78.103.109.
- 02:29:49 DC01 re-establishes Metrepreter reverse_tcp connection to 203.78.103.109.
- 02:35:55 DC01 connects to DESKTOP’s RDP service Administrator (username in Kerberos traffic).
- 02:39:58 DESKTOP download coreupdater.exe from 194.61.24.102 using MS Edge.
- 02:40:49 DESKTOP establishes Metrepreter reverse_tcp connection to 203.78.103.109.
- 02:56:03 194.61.24.102 connects to DC01’s RDP service as Administrator one last time.
- 02:56:38 DC01 re-establishes Metrepreter reverse_tcp connection to 203.78.103.109.
- IP : 194.61.24.102 (Attacker)
- IP : 203.78.103.109 (C2 server)
- MD5 : eed41b4500e473f97c50c7385ef5e374 (coreupdater.exe)
- JA3 Hash : 84fef6113e562e7cc7e3f8b1f62c469b (RDP scan/brute force)
- JA3 Hash : 6dc99de941a8f76cad308d9089e793d7 (RDP scan/brute force)
- JA3 Hash : e26ff759048e07b164d8faf6c2a19f53 (RDP scan/brute force)
- JA3 Hash : 3bdfb64d53404bacd8a47056c6a756be (RDP scan/brute force)
Wanna learn more network forensic analysis techniques? Then check out our upcoming network forensics classes in September and October.
Posted by Erik Hjelmvik on Friday, 09 July 2021 13:20:00 (UTC/GMT)





NetworkMiner 2.7 Released
We are happy to announce the release of NetworkMiner 2.7 today! The new version extracts documents from print traffic and pulls out even more files and parameters from HTTP as well as SMB2 traffic. We have also updated our JA3 implementation to fingerprint the server side in TLS sessions using JA3S hashes and added a few tweaks to the user interface to better identify the extension of extracted files.
Extraction of Printed Data
NetworkMiner 2.7 can extract documents from LPR/LPD print traffic on TCP 515 (RFC1179). The extracted print data is saved to disk as .prn files, which can be analyzed with tools like PCL Paraphernalia. The professional version of NetworkMiner also comes with a carver that attempts to extract PostScript and PDF files from print traffic.
Improved File Extraction from PCAP
One of the premier features of NetworkMiner is its ability to extract transferred files from network traffic. We have fine tuned NetworkMiner’s file extraction code for SMB2 as well as HTTP POST in this release, in order to retrieve as much information as possible from these protocols. We’ve also added more granular logging of SMB2 requests and responses to the Parameters tab.
More DNS Types Supported
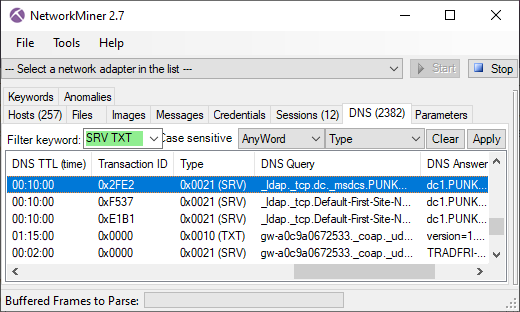
NetworkMiner 2.7 now parses DNS TXT and SRV resource records, which are displayed in NetworkMiner’s DNS tab. The TXT records can be used for almost anything, but the SRV records are used to map service types to the hostnames that provide that service. SRV lookups are often used in order to locate the domain controller on a network by querying for .
DNS SRV of lookups are performed by malware and attackers as well as for legitimate reasons, even though attackers sometimes make mistakes that can be used for detection or threat hunting.
TLS Server Fingerprinting with JA3S
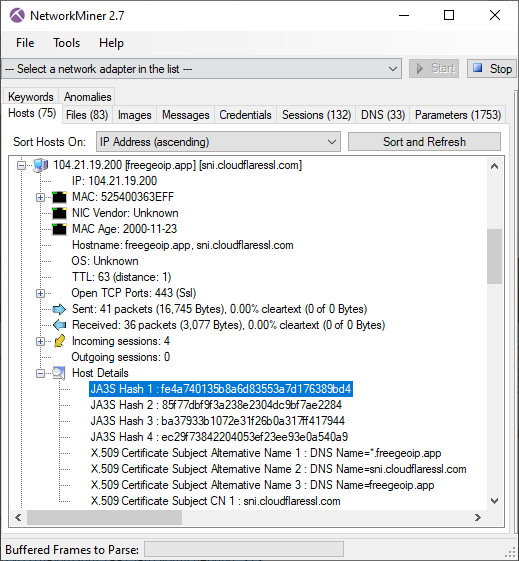
We introduced TLS client fingerprinting using JA3 hashes in NetworkMiner 2.5. We have now also added support for JA3S hashes, which is a method for fingerprinting the server side of a TLS connection. The JA3S hashes are extracted from the “Server Hello” TLS packets and shown on NetworkMiner’s Parameters tab as well as in the Host Details of the server. We have also improved how NetworkMiner displays the JA3 hashes in the Host Details view.
Additional User Interface Improvements
Double clicking on an extracted file in NetworkMiner’s Files tab now brings up the File Details window. We’ve extended this window to also include a simple hex viewer and a feature that attempts to identify the file type based on the reassembled file’s header.
The file type identification feature is also used in order to provide more accurate file extensions to extracted files, such as “.exe” or “.zip”, instead of the “.octet-stream” that you’d often see in previous versions of NetworkMiner. We have added a warning dialogue to NetworkMiner 2.7 that shows up if a user tries to run an executable file directly from the NetworkMiner GUI.
Our commercial tool NetworkMiner Professional has received a few additional updates. It can, for example, carve PDF and PostScript files from extracted LPR print data. We have also added several OSINT services, such as ANY.RUN, MalwareBazaar, URLHaus and ThreatFox, for performing lookups of file hashes. The OSINT context menu is opened by right-clicking an extracted file in NetworkMiner Professional.
GPS data stored in pcap-ng option fields, typically by Kismet, is now extracted as capture file metadata. Right-click a capture file and select «Show Metadata» to show the coordinates from Kismet. We have also re-implemented the support for a PCAP-over-IP listener in NetworkMinerCLI, which is the command line version of NetworkMiner Pro. This feature allows the command line tool to receive PCAP data over a TCP socket instead of reading from a capture file. The PCAP-over-IP listener feature was previously broken in NetworkMinerCLI.
We’d like to thank Hayo Brouwer (of Ricoh) for requesting the LPR extraction feature and providing capture files for testing, Jeff Rivett for reporting a 64 bit issue with WinPcap/Npcap and Ali Mohd for reporting the broken PCAP-over-IP listener feature.
Upgrading to Version 2.7
Users who have purchased NetworkMiner Professional can download a free update to version 2.7 from our customer portal, or use the “Help > Check for Updates” feature. Those who instead prefer to use the free and open source version can grab the latest version of NetworkMiner from the official NetworkMiner page.
Posted by Erik Hjelmvik on Tuesday, 15 June 2021 11:55:00 (UTC/GMT)





Network Forensics Classes for EU and US
We have now scheduled two new live online classes, one in September and one in October. The September class is adapted to European time and the October one is adapted to American time. The contents are exactly the same in both classes.
The training is split into four interactive morning sessions (4 hours each), so that you have the afternoon free to either practice what you learned in class or do your “normal” day job. The number of attendees will be limited in order to enable attendees to ask questions or even cover short ad-hoc side tracks. We plan to accept something like 10 to 15 attendees per class. The class registration will be closed once we reach this attendee limit.
- 🇪🇺 September 20-23, 2021. Live Online Training «PCAP in the Morning EU»
⏲️ Time: 8:30 AM to 12:30 PM CET (Central European Time)
💸 Price: € 820 EUR per student (€ 738 EUR if registering before August 20) - 🇺🇸 October 25-28, 2021. Live Online Training «PCAP in the Morning US»
⏲️ Time: 9:00 AM to 1:00 PM EDT (US Eastern Daylight Time)
💸 Price: $1,000 USD per student ($900 USD if registering before September 25)
We will be analyzing a unique 30GB PCAP data set captured during June 2020 on an Internet connected network with multiple clients, an AD server, a web server, an android tablet and some embedded devices. As you’ve probably guessed, the capture files contain traffic from multiple intrusions by various attackers, including APT style attackers and botnet operators. The initial attack vectors are using techniques like exploitation of web vulnerabilities, spear phishing, a supply chain attack and a man-on-the-side attack!
See our training page for more info about the “PCAP in the Morning” classes.
To sign up for a class, simply send an email to sales@netresec.com with the class dates, your name and invoice address. We will then send you a PayPal payment link that you can use to complete your training registration.
Hope to see you there!
Cheers,
Erik Hjelmvik
Creator of NetworkMiner and founder of Netresec
Posted by Erik Hjelmvik on Monday, 07 June 2021 09:55:00 (UTC/GMT)





Detecting Cobalt Strike and Hancitor traffic in PCAP
This video shows how Cobalt Strike and Hancitor C2 traffic can be detected using CapLoader.
Your browser does not support the video tag.
I bet you’re going:
😱 OMG he’s analyzing Windows malware on a Windows PC.
Relax, I know what I’m doing. I have also taken the precaution of analyzing the PCAP file in a Windows Sandbox, which just takes a couple of seconds to deploy and run.
The capture file I’m looking at is called “2021-05-13-Hancitor-traffic-with-Ficker-Stealer-and-Cobalt-Strike.pcap” and can be downloaded from here:
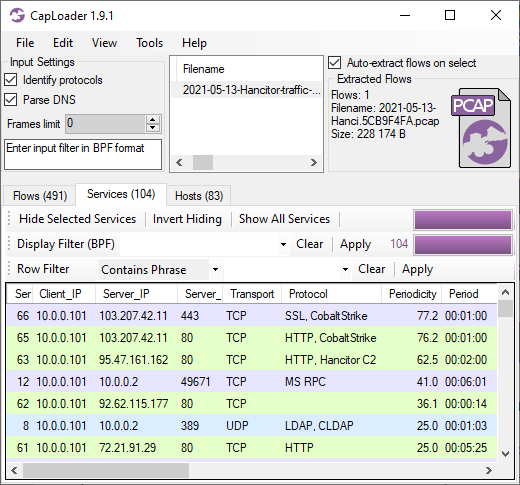
CapLoader’s Services tab shows us that the connections to TCP 80 and 443 on are very periodic, with a detected period of exactly 1 minute. CapLoader successfully identifies the protocols for these two services as over HTTP and over SSL, respectively. The third service in this list is also very periodic, that’s the Hancitor trojan beaconing to its C2 server every two minutes.
CapLoader uses machine learning to identify the application layer protocol based on the behavior of the traffic, not the port number. This means that there can be false positives, i.e. the protocol classification that CapLoader gives a flow or service might be wrong. It is more common, however, for CapLoader to yield false negatives, which means that it can’t identify the protocol. The detection of Cobalt Strike inside of HTTP and SSL traffic was recently introduced in the latest 1.9 release of CapLoader. I expected this feature to detect Cobalt Strike traffic in HTTP, but I was delighted to see that CapLoader often detects even TLS encrypted Cobalt Strike beaconing with really good precision!
As shown in the video, the Cobalt Strike beacon config can easily be extracted from the network traffic using NetworkMiner and Didier Stevens’ 1768 K python script.
The output from Didier’s 7868.py tool looks something like this:
As you can see, it uses HTTP for transport with a “sleeptime” of 1 minute (60000 ms) and This means that a new connection will be made to the Cobalt Strike C2 server every minute. The fact that there was no jitter is what gives this service such a high value in CapLoader’s “Periodicity” column.
Network Forensics Training
Are you interested in learning more about how to analyze network traffic from Cobalt Strike and other backdoors, malware and hacker tools? Then take a look at the live online network forensics classes I will be teaching in September and October!
Posted by Erik Hjelmvik on Monday, 31 May 2021 08:30:00 (UTC/GMT)





CapLoader 1.9 Released
A new version of the PCAP filtering tool CapLoader has been released today. The new CapLoader version 1.9 is now even better at identifying protocols and periodic beacons than before. The user interface has also been improved to make it easier to filter and drill down in network traffic to extract interesting, malicious or unusual traffic.
More Protocols Identified
We’ve added port-independent protocol detection for over 20 new protocols since the last release. The newly added protocols include some that are used by malicious tools and backdoors such as hTran, RevengeRAT, Tofsee and Winsecsrv, as well as legitimate protocols like WireGuard (VPN) and RemoteFX (UDP based remote desktop). We’ve also improved our support for ICS traffic analysis by adding protocol identification of SCADA protocols DNP3 and IEC 60870-5-104.
CapLoader also detects what we call “sub-protocols”, which are communication protocols that use other L7 protocols as transport. We have extended the sub-protocol detection in CapLoader 1.9 to include traffic like Anchor_DNS and dnscat traffic, which both run on top of DNS. We have also added detection of Cobalt Strike beacons over HTTP and HTTPS, even though the latter is quite difficult to detect due to the application data being encrypted.
CapLoader 1.9 comes with several user interface improvements that help you solve the “needle in the haystack” problem even more efficiently than before.
The context menus in the Flows, Services and Hosts tabs can now be used to select rows based on values in any column, such as “Select all flows where Duration > 10 minutes” (when right-clicking a 10 minute flow).
The “Keyword Filter” is now called “Row Filter” in order to avoid getting it mixed up with the “Find Keyword” feature. The Row Filter has also been enhanced with a new filtering mode, to complement the Contains / All Words / Any Words / RegEx options, which is called “Column Criteria”. The Column Criteria can be used to filter the displayed rows based on the values in a user-specified column. The Column Criteria “Duration > 00:10:00” will, for example, only show flows that are 10 minutes or longer, while “ASN = 3301” shows the flows going to Telia’s AS3301.
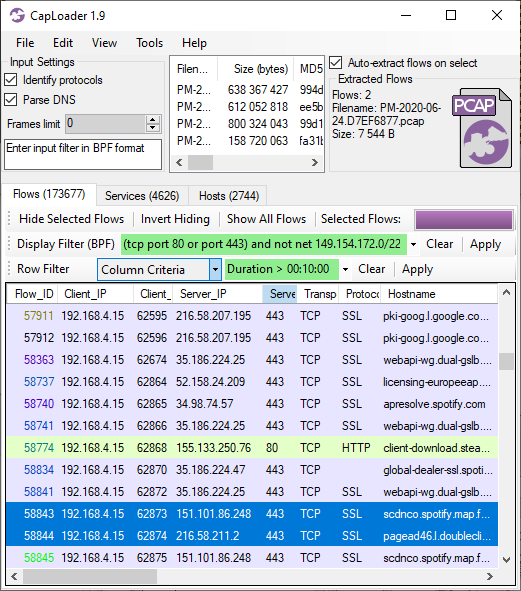
Image: CapLoader with Row Filter Column Criteria «Duration > 00:10:00»
We have also extended CapLoader’s BPF implementation to support VLAN id’s, so that you can use expressions like “vlan 100” as input filter as well as display filter. The BPF implementation also supports logic operators, so that more advanced filters like “(tcp port 80 or port 443) and not net 149.154.172.0/22” can be used.
CapLoader has a method for detecting periodic connection patterns, which was introduced in CapLoader 1.4. This feature can be used to detect clients that connect to a service at regular intervals, such as a beacon used for command-and-control or email client connecting to a mail server. We have improved the periodicity detection in CapLoader 1.9 so that it now detects periodic services more accurately.
The Initial Round Trip Time (iRRT) in the Flows and Services tabs is now measured in milliseconds instead of seconds in order to avoid “bulky numbers” (h/t Eddi).
There was previously a significant delay when selecting many flows at once (like 100.000). We’ve improved the performance of this feature in CapLoader 1.9, so that you can now select several hundred thousands flows at once without having to wait for an unresponsive GUI to update.
More OSINT Lookup Services
A feature in CapLoader that often comes in handy is the ability to right-click a flow, service or host and open a website with OSINT information about the clicked IP address or domain name. We have now replaced some of the OSINT services with new better ones.
Bug fixes and Credits
Several bugs have been fixed in this new release of CapLoader, much thanks to feedback we’ve received from our users. We’d like to thank Anders Regert and Mandy van Oosterhout for reporting bugs in CapLoaders “Save As” feature. We’d also like to thank Hyun Dowon for reporting a snap length corruption bug that previously appeared when exporting flows from Pcap-NG files We have also fixed an issue where capture files were previously not always merged in chronological order when being aggregated.
Updating to the Latest Release
Users who have purchased a license for CapLoader can download a free update to version 1.9 from our customer portal. All others can download a free 30 day trial from the CapLoader product page (no registration required).
Posted by Erik Hjelmvik on Tuesday, 25 May 2021 12:20:00 (UTC/GMT)





Running NetworkMiner in Windows Sandbox
NetworkMiner can be run in a highly efficient Windows Sandbox in order to analyze malicious PCAP files in Windows without accidentally infecting your Windows PC. This blog post shows how to set up a Windows Sandbox that always boots up a fresh install of Windows 10 with the latest version of NetworkMiner installed.
I generally recommend analyzing Windows malware in Linux, or some other non-Windows environment, in order to avoid accidentally infecting yourself (NetworkMiner runs fine in Linux btw). Nevertheless, I still often find myself loading capture files containing malicious network traffic into CapLoader and NetworkMiner under Windows. I have previously demonstrated that this can be a quick and crude way to perform an anti virus scan of files contained in a pcap file.
If you want to analyze malicious traffic in Windows with minimal risk of infecting yourself then you should definitely check out Microsoft’s Windows Sandbox (available in Windows 10 Pro and Enterprise editions). The Windows Sandbox is using Windows containers, so it’s very efficient compared to spinning up a full Windows VM. It also provides features like kernel isolation, so that the sandbox container doesn’t use the same kernel as the host, and ensures that a new Windows environment is created every time the sandbox is run. Windows Sandbox also doesn’t run any anti-virus, so it won’t interfere with the extraction of malicious contents from within the analyzed capture files.
Follow these steps to install Windows Sandbox:
- Run OptionalFeatures.exe (the “Turn Windows features on or off” window)
- Enable the “Windows Sandbox” feature (check the box)
- Reboot
Then create a sandbox config, which downloads and installs the latest version of NetworkMiner every time the sandbox is started, by creating a file called “NetworkMinerSandbox.wsb” with the following contents:
C:\Users\Erik\pcap
true
cmd.exe /C «curl -L https://www.netresec.com/?download=NetworkMiner | C:\Users\WDAGUtilityAccount\Desktop\
Note: Replace “C:\Users\Erik\pcap” with whatever location your capture files are at
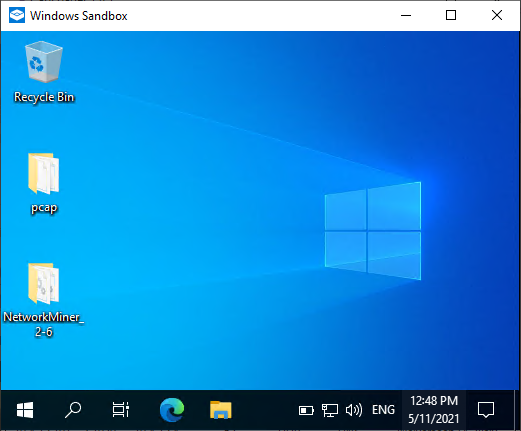
After starting NetworkMinerSandbox.wsb you’ll have a fresh Windows machine up and running within a couple of seconds. The latest version of NetworkMiner and your PCAP dir are both accessible from the sandbox’s desktop.
Image: NetworkMiner 2.6 installed in a clean Windows Sandbox environment
Moving files in or out of the sandbox is just a matter of copy and paste (Ctrl+C / Ctrl+V).
VirtualBox and Windows Sandbox
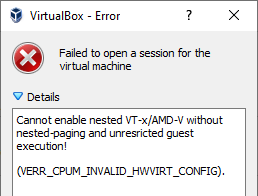
Are you using VirtualBox to run virtual machines on your Windows host and getting an error message saying “Cannot enable nested VT-x/AMD-V without nested-paging and unrestricted guest execution” after enabling Windows Sandbox?
Even though Windows Sandbox doesn’t need Hyper-V it still requires a hypervisor, which unfortunately conflicts with VirtualBox. You can disable the hypervisor by running the following command as administrator:
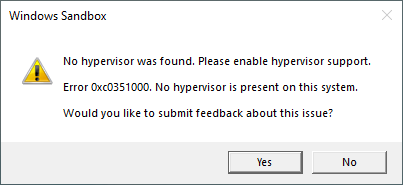
. and then rebooting the computer before starting a VirtualBox VM with “nested VT-x” enabled. Turning off the hypervisor will unfortunately prevent Windows Sandbox from running, giving an error message saying “No hypervisor was found. Please enable hypervisor support.”
To re-enable the hypervisor, in order to run Windows Sandbox again, you’ll need to run
and reboot the host.
Update May 26, 2021
We have now uploaded a simple Windows Sandbox config to our website here:
This script runs on any Windows Pro machine that has the Sandbox feature active.
Posted by Erik Hjelmvik on Tuesday, 11 May 2021 13:39:00 (UTC/GMT)





Analysing a malware PCAP with IcedID and Cobalt Strike traffic
This network forensics walkthrough is based on two pcap files released by Brad Duncan on malware-traffic-analysis.net. The traffic was generated by executing a malicious JS file called StolenImages_Evidence.js in a sandbox environment.
The capture file starts with a DNS lookup for banusdona.top, which resolved to 172.67.188.12, followed by an HTTP GET request for «/222g100/index.php» on that domain. The following PowerShell oneliner is returned in the HTTP response from banusdona.top:
This oneliner instructs the initial dropper to download a Win32 DLL payload from and save it as «JwWdx.dat» in the user’s temp directory and then run the DLL with:
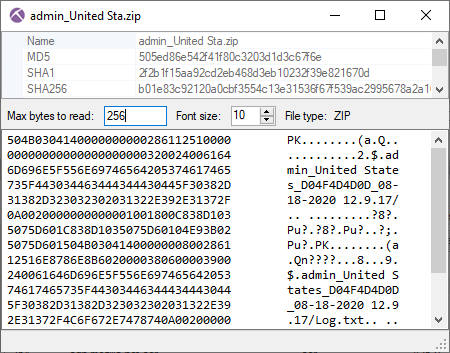
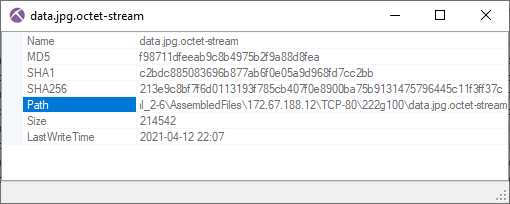
As you can see in the screenshot below, the HTTP response for this second request to banusdona.top has Content-Type «application/octet-stream», but also a conflicting Content-disposition header of «attachment;filename=data.jpg», which indicates that the file should be saved to disk as «data.jpg». Nevertheless, the «MZ» header in the transferred data reveals that the downloaded data wasn’t an image, but a Windows binary (dll or exe).
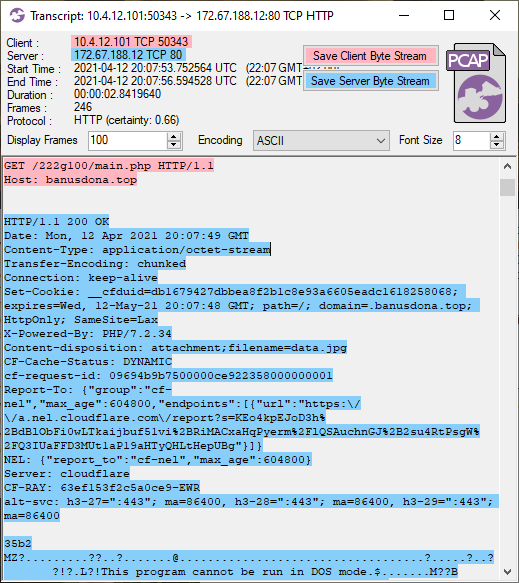
The downloaded file gets extracted from the pcap file by NetworkMiner as «data.jpg.octet-stream».
Right-clicking «data.jpg.octet-stream» in NetworkMiner and selecting «Calculate MD5. » brings up a new window with additional file details, such as MD5 and SHA hashes of the reassembled file.
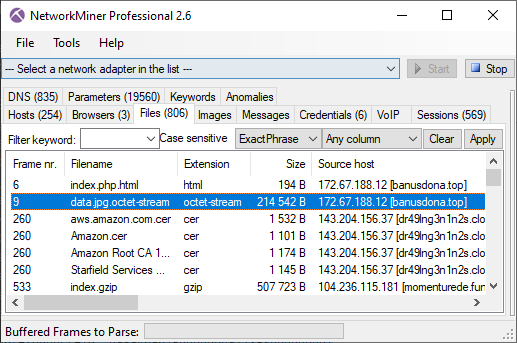
This file is available on VirusTotal, where we can see that it’s a DLL that several AV vendors identify as «Cerbu» or «IcedID». VirusTotal’s C2AE sandbox analysis of the DLL also reveals the domain name «momenturede.fun» in the process’ memory. As you might expect, a connection is made to that domain just a few seconds later. A nice overview of these connections can be seen in CapLoader’s Flow tab.
The momenturede.fun server returns a 500kB file, which NetworkMiner extracts from the pcap file as «index.gzip».
This turns out to be an encrypted IcedID DLL file, which has been analyzed by Ali Aqeel here:
https://aaqeel01.wordpress.com/2021/04/09/icedid-analysis/
Right after the IcedID download we see a series of HTTPS connections towards odd domains like vaccnavalcod.website, mazzappa.fun, ameripermanentno.website and odichaly.space, all of which resolved to IP 83.97.20.176. That host is most likely a command-and-control (C2) server used by the IcedID malware.
CapLoader’s «Services» tab also reveals that the TLS connections to port 443 on 83.97.20.176 are very periodic, with a new connection every 5 minutes. Periodic connection patterns like this is a typical indicator of C2 traffic, where the malware agent connects back to the C2 server on regular intervals to check for new tasks.
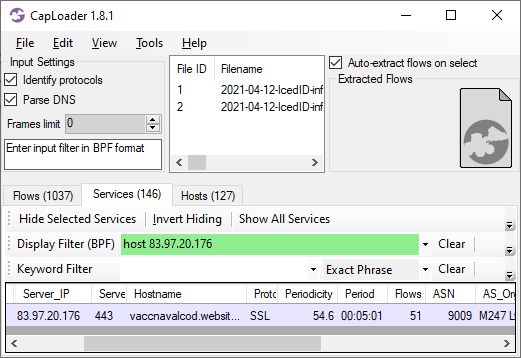
The traffic to 83.97.20.176 is encrypted, so we can’t inspect the payload to verify whether or not it is IcedID C2 communications. What we can do, however, is to extract the HTTPS server’s X.509 certificate and the JA3 hash of the client’s TLS implementation from the encrypted traffic.
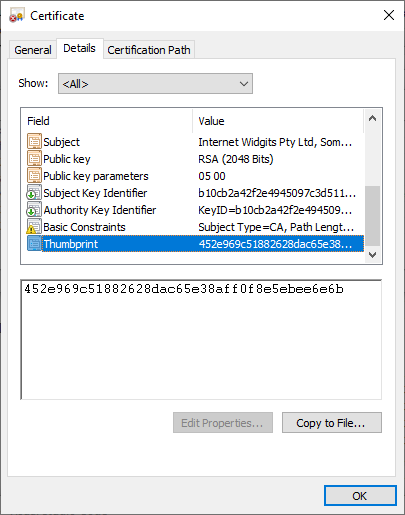
NetworkMiner has extracted the X.509 certificates for vaccnavalcod.website, mazzappa.fun, ameripermanentno.website and odichaly.space to disk as «localhost.cer».
It turns out that all these sites used the same self-signed certificate, which had SHA1 fingerprint 452e969c51882628dac65e38aff0f8e5ebee6e6b. The X.509 certificate was created using OpenSSL’s default values, such as «Internet Widgits Pty Ltd» etc. Further details about this certificate can be found on censys.io.
The JA3 hashes used by the IcedID malware agent can be found in NetworkMiner’s Hosts tab as well as in the Parameters tab.
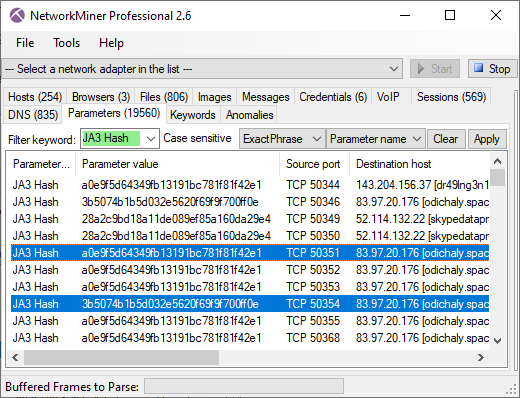
The JA3 hashes for the client that connects to the C2 server are a0e9f5d64349fb13191bc781f81f42e1 and 3b5074b1b5d032e5620f69f9f700ff0e. Several legitimate Windows applications unfortunately have the same JA3 hashes, so we can’t use them to uniquely identify the IcedID agents.
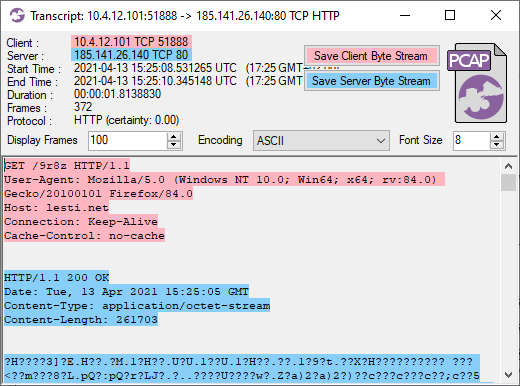
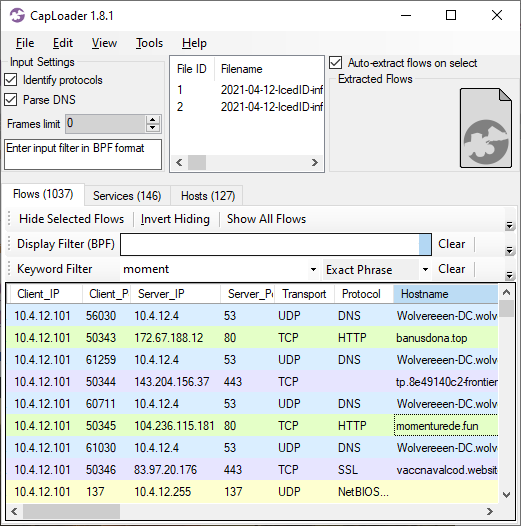
The IcedID C2 traffic continues for over 19 hours, at which point we suddenly see a connection to a new suspicious domain called «lesti.net» on 185.141.26.140. The first HTTP request to that domain is used to download a 261703 byte file, as can be seen in this Flow Transcript from CapLoader:
NetworkMiner extracts this file as «9r8z.octet-stream» . This turns out to be a Cobalt Strike beacon download, which we can decode with Didier Stevens’ fantastic 1768.py script.
The output from 1768.py reveals that this Cobalt Strike beacon is using the following URIs for C2 communication:
- GET URI: http://lesti[.]net/userid=
- POST URI: http://lesti[.]net/update.php
We can also see that the Cobalt Strike license-id (a.k.a. watermark) is 1580103814. This ID can be used to link this Cobalt Strike beacon to other campaigns. Below is a list of Cobalt Strike C2 servers using license-id 1580103814 discovered by Tek in December 2020:
- 45.147.229[.]157
- selfspin[.]com
- savann[.]org
- palside[.]com
- server3.msadwindows[.]com
- mapizzamates[.]com
- fixval[.]com
- rackspare-technology[.]download
- 108.177.235[.]148
- matesmapizza[.]com
Update 4 May 2021
Sergiu Sechel published a blog post yesterday, which included a list of Cobalt Strike C2 servers. We fed this list to Tek’s scan_list.py script in order to see if license-id 1580103814 is still active. It turned out it was. We found the following 27 domains and IP’s running Cobalt Strike C2 servers on TCP 443 using that license-id.
- 151.236.14[.]53
- 151.236.14[.]53
- 172.241.27[.]70
- 193.29.13[.]201
- 193.29.13[.]201
- 193.29.13[.]209
- 194.165.16[.]60
- 193.29.13[.]209
- 193.29.13[.]201
- 194.165.16[.]60
- 194.165.16[.]60
- dain22[.]net
- drellio[.]com
- feusa[.]net
- fut1[.]net
- helle1[.]net
- hars2t[.]com
- kasaa[.]net
- idxup[.]com
- maren2[.]com
- mgfee[.]com
- massflip[.]com
- oaelf[.]com
- repdot[.]com
- scalewa[.]com
- tulls[.]net
- wellser[.]org
The full output from our re-scan of Sergiu’s C2 list can be found on pastebin.
Update 8 May 2021
Security researcher Michael Koczwara is tracking Cobalt Strike license 1580103814 as APT actor LuckyMouse (a.k.a. Emissary Panda or APT 27). Michael’s Cobalt Stike C2 dataset, which currently contains 25 unique C2 IPs and domains for license-id 1580103814, is available as a Google Docs spreadsheet (see the «LuckyMouse Actor» tab).
Indicators of Compromise — IOCs
- MD5: 8da75e1f974d1011c91ed3110a4ded38
- SHA1: e9b5e549363fa9fcb362b606b75d131dec6c020e
- SHA256: 0314b8cd45b636f38d07032dc8ed463295710460ea7a4e214c1de7b0e817aab6
- DNS: banusdona.top
- IP: 172.67.188.12
- MD5: f98711dfeeab9c8b4975b2f9a88d8fea
- SHA1: c2bdc885083696b877ab6f0e05a9d968fd7cc2bb
- SHA256: 213e9c8bf7f6d0113193f785cb407f0e8900ba75b9131475796445c11f3ff37c
- DNS: momenturede.fun
- IP: 104.236.115.181
- MD5: 96a535122aba4240e2c6370d0c9a09d3
- SHA1: 485ba347cf898e34a7455e0fd36b0bcf8b03ffd8
- MD5: 11965662e146d97d3fa3288e119aefb2
- SHA1: b63d7ad26df026f6cca07eae14bb10a0ddb77f41
- SHA256: d45b3f9d93171c29a51f9c8011cd61aa44fcb474d59a0b68181bb690dbbf2ef5
- DNS: vaccnavalcod.website
- DNS: mazzappa.fun
- DNS: ameripermanentno.website
- DNS: odichaly.space
- IP: 83.97.20.176
- SHA1: 452e969c51882628dac65e38aff0f8e5ebee6e6b
- DNS: lesti.net
- IP: 185.141.26.140
- MD5: 449c1967d1708d7056053bedb9e45781
- SHA1: 1ab39f1c8fb3f2af47b877cafda4ee09374d7bd3
- SHA256: c7da494880130cdb52bd75dae1556a78f2298a8cc9a2e75ece8a57ca290880d3
- Cobalt Strike Watermark: 1580103814
Network Forensics Training
Are you interested in learning more about how to analyze captured network traffic from malware and hackers? Have a look at our network forensic trainings. Our next class is a live online event called PCAP in the Morning.
Posted by Erik Hjelmvik on Monday, 19 April 2021 09:45:00 (UTC/GMT)





Источник