- nslookup Command in Linux (Name Server Lookup)
- 1. Basic DNS Lookup
- 2. Reverse DNS Lookup
- 3. Query to Specific DNS Server
- 4. Find SOA Record for Domain
- 5. Query MX Record
- 6. Query TXT Records for Domain
- 7. Find All Records of Domain
- 8. Using nslookup in Interactive Mode
- Conclusion
- Как пользоваться командой nslookup в Linux?
- Принцип работы DNS
- Синтаксис nslookup
- Примеры
- 8 Linux Nslookup Commands to Troubleshoot DNS (Domain Name Server)
- 1. Find out “A” record (IP address) of Domain
- 2. Find out Reverse Domain Lookup
- 3. Find out specific Domain Lookup.
- 4. To Query MX (Mail Exchange) record.
- 5. To query NS(Name Server) record.
- 6. To query SOA (Start of Authority) record.
- 7. To query all Available DNS records.
- 8. Enable Debug mode
- If You Appreciate What We Do Here On TecMint, You Should Consider:
- Linux nslookup command
- Description
- Reverse DNS lookups
- Querying the NS record of a domain
- Querying the MX record
- Querying the SOA record
- Viewing all available NS records
- Querying another DNS
- Querying on a non-standard port
- Debugging the query transaction
- Interactive mode
- Syntax
- Technical description
- Arguments
- Options
- Interactive commands
- Configuration files
- Deprecation
- Examples
- Related commands
nslookup Command in Linux (Name Server Lookup)
nslookup stands for “name server lookup” is a useful command for getting information from DNS server. It also very useful for troubleshooting DNS related issues. It queries to DNS (Domain Name Server) and get the dns records for any domain for ip address.
In this tutorial you will get some useful examples for nslookup command available on Linux servers. This command is also available on Windows systems as well.
1. Basic DNS Lookup
Use nslookup command followed by the domain name will return the Address records for a domain. For example, to view DNS record for domain tecadmin.net, type:
2. Reverse DNS Lookup
A Reverse DNS (rDNS) lookup is when you have an IP address and want to find associated domain name. You will see any output only if a reverse zone is configured corresponding to that IP address. Generally, this is configured by the hosting provider or datacenters.
To view the reverse dns lookup for an IP address, type:
3. Query to Specific DNS Server
The default nslookup quires to DNS server configured on your system’s network interface. But you can specify the DNS server to which nslookup queried directly instead of local configured.
You need to pass additional parameter of name server IP address or domain name. For example to query to 9.9.9.9 name server use the following command.
4. Find SOA Record for Domain
SOA is the abbreviation of Start of Authority. This is an useful DNS record for any domain contains administrative information about the zone.
To find the SOA record of any domain, you need to specify -type=soa as command line parameter. For example:
5. Query MX Record
You can also query for MX (Mail Exchange) records for any domain. These domain records are responsible for emails delivery.
6. Query TXT Records for Domain
TXT records are useful for multiple types of records like DKIM, SPF, etc. You can find all TXT records configured for any domain using below command.
7. Find All Records of Domain
Use -query=any to list all records for a domain.
8. Using nslookup in Interactive Mode
We can also use nslookup in interactive mode. To go in interactive mode type nslookup on console and press enter. You will get nslookup prompt like > . Here you can run the same query and get the information for domain from DNS server. For your understanding, I have added comments in between commands.
Conclusion
In this tutorial, you have learned about uses of nslookup command.
Источник
Как пользоваться командой nslookup в Linux?
Для проверки DNS используется универсальная команда nslookup. Она есть как в Windows, так и в Linux. Утилита поможет получить IP-адрес, а также сделать обратное преобразование и определить скорость работы DNS сервера.
Принцип работы DNS
Интернет — большое количество устройств, которые связаны между собой в сеть. Под устройством можем понимать сервера, компьютеры, ноутбуки и так далее. Для объединения компьютеров в сеть используются ip-адреса, однако людям работать с ними не удобно, гораздо удобнее воспринимать информацию с символьными именами, например www.vseprolinux.ru.
Чтобы не запоминать много цифр в виде ip-адресов, в 80-х годах была создана DNS — система доменных имен, протокол прикладного уровня. Он преобразовывает имена устройств (компьютеров) в IP-адреса.
Теперь вместо адреса достаточно ввести в адресную строку доменное имя, название сайта в виде www.site.ru, далее уже Ваш ДНС делает запрос, чтобы узнать ip-адрес запрашиваемого узла.
Все это хорошо, только если не работает ДНС, то и не работает сайт, для диагностики проблем ДНС системы обычно используется команда nslookup.
Синтаксис nslookup
Рассмотрим синтаксис команды.
nslookup [параметры] [домен] [сервер]
Домен — доменное имя. Сервер — необязательный аргумент
- -type — тип записи ДНС. ns, txt, ptr, cname, soa и другие;
- -port — порт ДНС;
- -recurse — если ДНС не отвечает, то использоваться другие DNS;
- -retry — количество попыток;
- -timeout — время;
- -fail — если DNS доменных имен возвращает ошибку, то использовать другой сервер.
Примеры
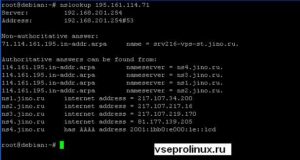
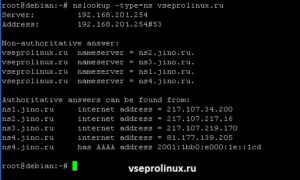
Узнаем IP-адрес сайта vseprolinux.ru. Для этого выполним команду без аргументов.
На скриншоте выше видно:
- Server: 192.168.201.254 — адрес текущего ДНС сервера компьютера, который указан а настройках сети, в моем случае /etc/resolv.conf
- Address: 192.168.201.254#53 — IP-адрес вместе с портом. По умолчанию используется 53 порт.
- Non-authoritative answer — не авторитетный ответ. Такой ответ выдается в двух случаях: ДНС не обслуживает зону, и ответ получен из кэша, данные могли устареть. Авторитетным ответом будет считаться только если сервер имеет полную информацию о зоне.
- 195.161.114.71 — IP-адрес сайта.
Теперь сделаем обратное преобразование.
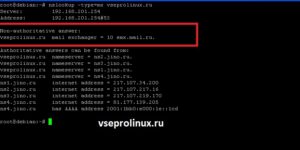
Получим NS запись.
Запись MX содержит всего два поля:
- приоритет;
- адрес сервера принимающего почту для данного домена.
Чем ниже значения, тем более высокий приоритет.
В наше время все больше внимания уделяется защите от спама в email сообщениях. Выделим два основных варианта, через TXT запись DNS:
- spf — Sender Policy Framework. Представляется собой текстовую запись, которая содержит список хостов, которые имеют права отправлять письма от домена;
- dkim -DomainKeys Identified Mail. TXT запись ключа. Для определения отправителя добавляется цифровая подпись, далее подпись автоматически проверяется получателем.
Чтобы узнать TXT надпись, введем в терминале команду с типом txt:
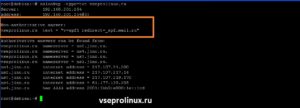
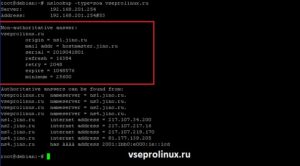
Утилита может вывести техническую информацию о домене «Start Of Authority». Для этого используется тип запроса soa:
Утилита в Линуксе покажет такие записи:
- origin — от кого узнали информацию;
- mail addr — email address администратора домена;
- serial — время в формате timestamp;
- refresh — время в секундах, когда нужно повторить подключения для обновления информации;
- retry — время в секундах, через которое повторять подключения к DNS, если он недоступен;
- expire — время в секундах, через сколько времени считать иформацию устаревшей полученную от первого ДНС;
- minimum — время в секундах до следующего обновления.
Источник
8 Linux Nslookup Commands to Troubleshoot DNS (Domain Name Server)
nslookup is a command-line administrative tool for testing and troubleshooting DNS servers (Domain Name Server). It is used to query specific DNS resource records (RR) as well. Most operating systems comes with built-in nslookup feature.

This article demonstrates widely used nslookup command in detail. Nslookup can be run in two modes: Interactive and Non-Interactive. The Interactive mode is used to query DNS-Server about various domains and hosts. Non-Interactive mode is used to query about information of a domain or host.
You might also be interested in following article :
1. Find out “A” record (IP address) of Domain
Above command query domain www.yahoo.com with 4.2.2.2 public DNS server and below section shows Non-authoritative answer: displays A record of www.yahoo.com
2. Find out Reverse Domain Lookup
3. Find out specific Domain Lookup.
4. To Query MX (Mail Exchange) record.
MX record is being used to map a domain name to a list of mail exchange servers for that domain. So that it tells that whatever mail received / sent to @yahoo.com will be routed to mail server.
5. To query NS(Name Server) record.
6. To query SOA (Start of Authority) record.
7. To query all Available DNS records.
8. Enable Debug mode
To enable Debug Mode ‘set debug’ will return you verbose information like TTL, here’s the output.
In this article, we have tried to cover nslookup commands which may help you to search (DNS) Domain Name Service related information. Next article will be on Linux Dig command which is Similar to nslookup. If you liked the article please share with your friends and don’t forget to give your valuable feedback’s through comment box.
If You Appreciate What We Do Here On TecMint, You Should Consider:
TecMint is the fastest growing and most trusted community site for any kind of Linux Articles, Guides and Books on the web. Millions of people visit TecMint! to search or browse the thousands of published articles available FREELY to all.
If you like what you are reading, please consider buying us a coffee ( or 2 ) as a token of appreciation.
We are thankful for your never ending support.
Источник
Linux nslookup command
On Unix-like operating systems, the nslookup command queries Internet name servers interactively for information.
Description
nslookup, which stands for «name server lookup», finds information about a named domain.
By default, nslookup translates a domain name to an IP address (or vice versa). For instance, to find the IP address of microsoft.com, you could run the command:
. and you would receive a response like this:
Here, 8.8.8.8 is the address of our system’s Domain Name Server. This is the server our system is configured to use to translate domain names into IP addresses. «#53» indicates we are communicating with it on port 53, which is the standard port number domain name servers use to accept queries.
Below this, we have our lookup information for microsoft.com. Our name server returned two entries, 134.170.185.46 and 134.170.188.221. This indicates microsoft.com uses a round robin setup to distribute server load. When you access micrsoft.com, you may be directed to either of these servers and your packets are routed to the correct destination.
You can see that we have received a «Non-authoritative answer» to our query. An answer is «authoritative» only if our DNS has the complete zone file information for the domain in question. More often, our DNS has a cache of information representing the last authoritative answer it received when it made a similar query; this information is passed on to you, and qualified as «non-authoritative» by the server: the information was recently received from an authoritative source, but the DNS server is not itself that authority.
Reverse DNS lookups
We can also perform the operation above in reverse by providing the IP address rather than the domain name. For instance, the command:
. returns information resembling the following:
Querying the NS record of a domain
The NS record of a domain is a map of all name servers that are authoritative for that domain. You can query a domain’s NS record using the option -type=ns, like this:
. and the response resembles the following:
This output gives us the names of the four microsoft.com name servers (which actually belong to the msft.net domain), according to our DNS’s (non-authoritative) information. If there is an available source for authoritative answers, it is listed at the bottom of the output.
Querying the MX record
The MX record is a map of mail exchange servers for a domain. When you send an e-mail to a domain, for example «@microsoft.com», mail is routed to Microsoft’s MX servers.
You can query a domain for its MX record using the -type=mx option. For example:
. responds with output resembling the following:
Here, the mail exchanger address is prefixed with a number (10). If there were more than one mail exchanger, they would each have a different number, with the lower numbers representing a higher priority. So if there were another exchanger with the prefix 5, that server would take precedence over the server listed here.
Querying the SOA record
The SOA (Start Of Authority) record for a domain provides technical information about the domain. It can be queried with the option -type=soa.
The information listed here is the cached version held by our domain name server. It includes:
- origin: The authority from which the information originated.
- mail addr: The e-mail address of the domain administrator (the first dot would be an @ symbol in an e-mail address, so here the e-mail address is [email protected]).
- serial: Revision data for this information, in the form YYYYMMDDNN. Here, the information is current as of August 11, 2014; 02 means it was the second revision made on that day.
- refresh: A number representing the interval, in seconds, after which the secondary name server checks the primary name server for an updated revision of this information. This information tells us the secondary Microsoft name server’s information is never more than two hours (7200 seconds) out of date.
- retry: The secondary nameserver waits this many seconds before attempting to reconnect to the primary name server after a failed attempt.
- expire: The secondary nameserver’s cache of the primary nameserver’s information always is considered invalid after this many seconds.
- minimum: The secondary nameserver’s cache of the primary nameserver’s information should not be refreshed if this amount of time has not elapsed since the last refresh.
Viewing all available NS records
We can also view all available NS records for a domain using the option -type=any. For example:
Querying another DNS
By default, nslookup queries the same DNS the system is configured to use for all network operations. You can specify a custom DNS to query, however, by specifying it on the command line. For example:
. provides us with the authoritative answer to our previous query of microsoft.com:
This is useful not only for obtaining authoritative information, but for finding out exactly what information a certain DNS currently has cached.
Querying on a non-standard port
By default, domain name servers accept queries on port 53. If this is configured differently on the server you are trying to query, you can specify another port number using the -port= option:
Here, the query attempt failed because our DNS uses the standard port, number 53.
Debugging the query transaction
Advanced users may need to examine more closely the details of the query transaction. This can be achieved using the -debug option:
Interactive mode
You can also run multiple commands interactively by running nslookup with no options:
This brings you to a special command prompt where you can use commands to perform any of the operations listed above. It looks like this:
At this prompt, you can type a domain name or IP address to query your DNS for its basic information:
. or, to submit a specific query type, you can set the type with set type=value, and then run the query. For instance, these two commands are the equivalent of running nslookup -type=any microsoft.com from the command line:
When ready to exit nslookup‘s Interactive Mode, run the command exit:
. and you are returned to the command line.
There are other commands you can run from interactive mode; see: Interactive commands below for a list.
Syntax
Technical description
nslookup is a program used to query Internet domain name servers for information.
nslookup has two modes: interactive and non-interactive. Interactive mode allows the user to query name servers for information about various hosts and domains or print a list of hosts in a domain. Non-interactive mode is used to print the name and requested information for a host or domain.
Arguments
Interactive mode is entered in the following cases:
- When no arguments are given (the default name server is used).
- When the first argument is a hyphen («—«) and the second argument is the hostname or Internet address of a name server.
Non-interactive mode is used when the name or Internet address of the host to be looked up is given as the first argument (which can be preceded by options). The optional second argument specifies the hostname or address of a name server, to be used instead of the system’s default DNS.
Options
Options can be specified on the command line if they precede the arguments and are prefixed with a hyphen. For example, to change the default query type to host information, and the initial timeout to 10 seconds, type:
The name of the option corresponds to the keyword of the set command. See below for a description of these keywords and their available settings.
Interactive commands
| host [server] | Look up information for host using the current default server, or server if specified. If host is an Internet address and the query type is A or PTR, the name of the host is returned. If host is a name and does not have a trailing period, the search list is used to qualify the name. |
To look up a host not in the current domain, append a period to the name.
| all | Prints the current values of the frequently used options to set. Information about the current default server and host is also printed. | ||||||||||||||||||||||||||||
| class=value | Change the query class to one of:
The class specifies the protocol group of the information. (Default = IN; abbreviation = cl) | ||||||||||||||||||||||||||||
| [no]debug | Turn on or off the display of the full response packet and any intermediate response packets when searching. (Default = nodebug; abbreviation = [no]deb) | ||||||||||||||||||||||||||||
| [no]d2 | Turn debugging mode on or off. This displays more about what nslookup is doing. (Default = nod2) | ||||||||||||||||||||||||||||
| domain=name | Sets the search list to name. | ||||||||||||||||||||||||||||
| [no]search | If the lookup request contains at least one period but doesn’t end with a trailing period, append the domain names in the domain search list to the request until an answer is received. (Default = search) | ||||||||||||||||||||||||||||
| port=value | Change the default TCP/UDP name server port to value. (Default = 53; abbreviation = po) | ||||||||||||||||||||||||||||
| querytype=value, type=value | Specify the type of the information to be returned in response to your query. The value may be one of the following, in upper or lower case:
| ||||||||||||||||||||||||||||
| [no]recurse | Tell the name server to query other servers if it does not have the information. (Default = recurse; abbreviation = [no]rec) | ||||||||||||||||||||||||||||
| retry=number | Set the number of retries to number. | ||||||||||||||||||||||||||||
| timeout=number | Change the initial timeout interval for waiting for a reply to number seconds. | ||||||||||||||||||||||||||||
| [no]vc | Always use a virtual circuit when sending requests to the server. (Default = novc) | ||||||||||||||||||||||||||||
| [no]fail | Try the next nameserver if a nameserver responds with SERVFAIL or a referral, (nofail) or terminate query (fail) on such a response. (Default = nofail) |
Configuration files
nslookup makes use of the configuration file /etc/nsresolv.conf, if it exists, for any special DNS configuration you may need. This file is managed using the command line program resolvconf.
Deprecation
nslookup was briefly classified as «deprecated» by the Internet Systems Consortium in favor of the tools host and dig. They later reversed this decision, but it’s important to note that host and dig can provide you with the same functions as nslookup, at a somewhat higher level of industry acceptance.
Examples
Perform a reverse lookup of the IP address 204.228.150.3. Your domain server responds with the current information it has about that host, and it is displayed on your terminal screen. Output resembles the following:
Query your DNS for information about the mail exchange server(s) for the domain computerhope.com. Output resembles the following:
Query your DNS for all available information related to the domain google.com. Output resembles the following:
Related commands
dig — DNS lookup utility.
host — Convert a hostname to an IP address and vice versa.
ping — Send ICMP ECHO_REQUEST packets to network hosts.
Источник