- PSWindowsUpdate: Managing Windows Updates from PowerShell
- PSWindowsUpdate: Install Windows Update PowerShell Module
- Overview of PSWindowsUpdate Cmdlets
- PowerShell: List All Windows Updates Available for a Computer
- Install-WindowsUpdate: Installing Windows Updates with PowerShell
- Install Windows Update on Remote Computers with PowerShell
- Get-WUHistory: Viewing Windows Update History using PowerShell
- Remove-WindowsUpdate: Uninstalling Windows Updates
- Hide-WindowsUpdate: How to Hide Windows Updates with PowerShell?
- How to get an update through Windows Update
- Detailed steps for Windows Server 2012 R2
- Detailed steps for Windows 7 Service Pack 1
- Windows Update troubleshooting
- Why am I offered an older update?
- My device is frozen at scan. Why?
- Feature updates are not being offered while other updates are
- Issues related to HTTP/Proxy
- The update is not applicable to your computer
- Issues related to firewall configuration
- Issues arising from configuration of conflicting policies
- Device cannot access update files
- Updates aren’t downloading from the intranet endpoint (WSUS or Configuration Manager)
- You have a bad setup in the environment
- High bandwidth usage on Windows 10 by Windows Update
PSWindowsUpdate: Managing Windows Updates from PowerShell
It is very convenient to use the special PSWindowsUpdate module for PowerShell to manage Windows updates from the command line interface. The PSWindowsUpdate is not integrated into Windows and is a third-party module available in Technet Script Gallery. PSWindowsUpdate allows administrators to remotely check, install, remove and hide updates on Windows servers and workstations. The PSWindowsUpdate module is especially valuable to manage updates on Windows Server Core, Hyper-V editions having no graphic interface, as well as when configuring a Windows image in the audit mode.
PSWindowsUpdate: Install Windows Update PowerShell Module
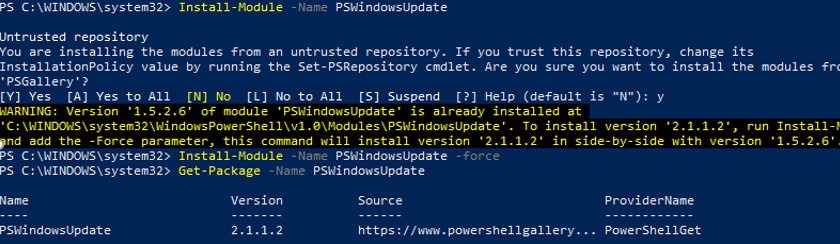
You can install the PSWindowsUpdate module on Windows 10 and Windows Server 2016 from the online repository (PSGallery) using the PackageManagement with a single command:
Install-Module -Name PSWindowsUpdate
In my case, a warning appeared that PSWindowsUpdate 1.5.2.6 was already installed appeared. To install a newer module version, you need to run the command:
Install-Module -Name PSWindowsUpdate –Force
After the installation is complete, you need to check the package:
Get-Package -Name PSWindowsUpdate
If you have an older Windows version (Windows 7/8.1/Windows Server 2008 R2/2012 R2) or you don’t have direct Internet access, you can install PSWindowsUpdate manually.
This module can be installed on any supported Windows versions starting from Vista / Windows Server 2008 with PowerShell 2.0 installed (though, PoSh 3.0 or newer is recommended).
After installing the PSWindowsUpdate module on your computer, you can remotely install it on other computers or servers using the Update-WUModule cmdlet. For example, to copy the PSWindowsUpdate module from your computer to two remote servers, run the commands (you need to access the remote servers via SMB protocol, TCP port 445):
$Targets = «lon-fs02», «lon-db01»
Update-WUModule -ComputerName $Targets –Local
To save (export) the PoSh module to a shared network folder for further importing of the module on other computers, run:
Save-Module -Name PSWindowsUpdate –Path \\lon-fs02\psmodules\
Overview of PSWindowsUpdate Cmdlets
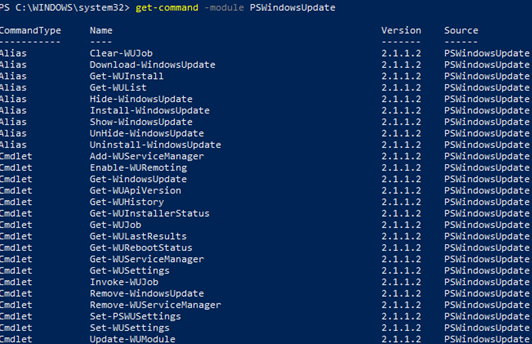
You can display the list of available cmdlets in the PSWindowsUpdate module as follows:
get-command -module PSWindowsUpdate
Let’s describe the usage of the module commands in brief:
- Clear-WUJob – use the Get-WUJob to call the WUJob in Task Scheduler;
- Download-WindowsUpdate (alias for Get-WindowsUpdate –Download ) — get a list of updates and download them;
- Get-WUInstall, Install-WindowsUpdate (alias for Get-WindowsUpdate –Install ) – install updates;
- Hide-WindowsUpdate (alias for Get-WindowsUpdate -Hide:$false ) – hide update;
- Uninstall-WindowsUpdate – remove update using Remove-WindowsUpdate;
- Add-WUServiceManager – register the update server (Windows Update Service Manager) on the computer;
- Enable-WURemoting — enable Windows firewall rules to allow remote use of the PSWindowsUpdate cmdlets;
- Get-WindowsUpdate (Get-WUList) — displays a list of updates that match the specified criteria, allows you to find and install the updates. This is the main cmdlet of the PSWindowsUpdate module. Allows to download and install updates from a WSUS server or Microsoft Update. Allows you to select update categories, specific updates and set the rules of a computer restart when installing the updates;
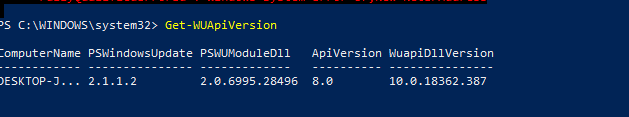
- Get-WUApiVersion – get the Windows Update Agent version on the computer;
- Get-WUHistory – display a list of installed updates (update history);
- Get-WUInstallerStatus — check the Windows Installer service status;
- Get-WUJob – run WUJob update tasks in the Task Scheduler;
- Get-WULastResults — dates of the last search and installation of updates (LastSearchSuccessDate and LastInstallationSuccessDate);
- Get-WURebootStatus — allows you to check whether a reboot is needed to apply a specific update;
- Get-WUServiceManager – list update sources;
- Get-WUSettings – get Windows Update client settings;
- Invoke-WUJob – remotely call WUJobs jobs in the Task Scheduler to immediately execute PSWindowsUpdate commands;
- Remove-WindowsUpdate – allows to uninstall an update by KB ID;
- Remove-WUServiceManager – disable Windows Update Service Manager;
- Set-PSWUSettings – save PSWindowsUpdate module settings to the XML file;
- Set-WUSettings – configure Windows Update client settings;
- Update-WUModule – update the PSWindowsUpdate module version (you can update the module on a remote computer by copying it from the current one, or updating from PSGallery).
PowerShell: List All Windows Updates Available for a Computer
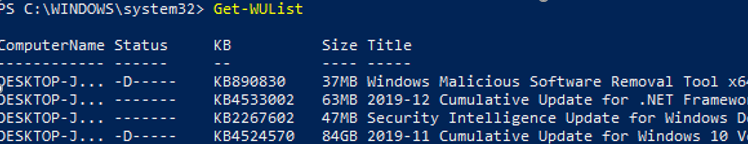
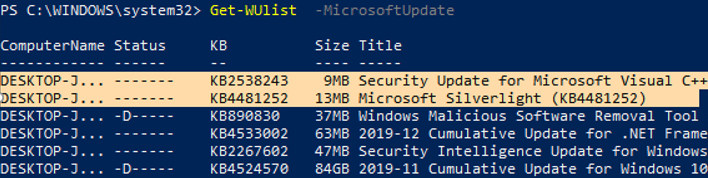
You can list the updates available for this computer on the update server using the Get-WindowsUpdate or Get-WUList commands.
To check the list of available updates on a remote computer, run this command:
Get-WUList –ComputerName server2
You can check where your Windows should get updates from. Run the following command:
As you can see, the computer is configured to receive updates from the local WSUS server (Windows Server Update Service = True). In this case, you should see a list of updates approved for your computer.
If you want to scan your computer on Microsoft Update servers in the Internet (in addition to Windows updates, these servers contain Office and other Microsoft product updates), run this command:
You will get this warning:
To allow scanning on Microsoft Update, run this command:
Add-WUServiceManager -ServiceID «7971f918-a847-4430-9279-4a52d1efe18d» -AddServiceFlag 7
You can now scan to Microsoft Update. As you can see, in this case, additional updates were found for Microsoft Visual C ++ 2008 and Microsoft Silverlight.
To check the version of the Windows Update Agent on the computer, run the command:
To remove certain products or packages from the list of updates received by your computer, you can exclude them by:
- Category (-NotCategory);
- Title (-NotCategory);
- Update number (-NotKBArticleID).
For example, let’s exclude OneDrive, drivers and the specific KB from the list of updates:
Get-WUlist -NotCategory «Drivers» -NotTitle «OneDrive» -NotKBArticleID KB4489873
Install-WindowsUpdate: Installing Windows Updates with PowerShell
To automatically download and install all available updates for your computer, run the command:
Install-WindowsUpdate -MicrosoftUpdate -AcceptAll -AutoReboot
The AcceptAll key accepts installation of all update packages, and AutoReboot allows Windows to automatically restart after the updates are installed.
You can save the update installation history to the log file (you can use it instead of WindowsUpdate.log file).
Install-WindowsUpdate -AcceptAll -Install -AutoReboot | Out-File «c:\logs\$(get-date -f yyyy-MM-dd)-WindowsUpdate.log» -force
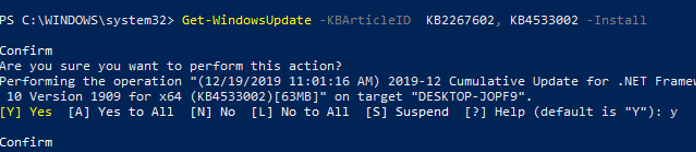
You can install only the specific update packages by KB number:
Get-WindowsUpdate -KBArticleID KB2267602, KB4533002 -Install
In this case, you need to confirm the installation of each update manually.
If you want to exclude some updates from the installation list, run this command:
Install-WindowsUpdate -NotCategory «Drivers» -NotTitle OneDrive -NotKBArticleID KB4011670 -AcceptAll -IgnoreReboot
Install Windows Update on Remote Computers with PowerShell
The PSWindowsUpdate module allows you to install updates remotely on multiple workstations or servers at once (the PSWindowsUpdate must be installed/imported on these computers). It is very convenient since an administrator doesn’t have to log on manually to all servers when update installation is scheduled.
Almost all PSWindowsUpdate module cmdlets allow you to manage and install updates on remote computers. To do this, use the attribute: -Computername server1, server2, server3
In order to manage updates on remote computers, you need to add host names to your winrm trusted host list:
Install the PSWindowsUpdate module on remote computers and allow to access the process dllhost.exe via dynamic RPC ports in the Windows Defender Firewall.
The following command will install all available updates on three remote servers:
In newer versions of the PSWindowsUpdate module, use the following command to remotely install updates on multiple computers:
You can install updates on a remote computer and send an email report to the administrator:
Install-WindowsUpdate -ComputerName nysrv1 -MicrosoftUpdate -AcceptAll — IgnoreReboot -SendReport –PSWUSettings @
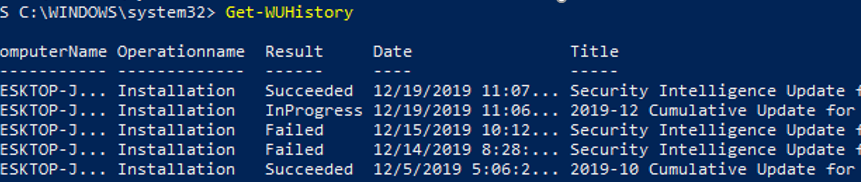
Get-WUHistory: Viewing Windows Update History using PowerShell
Using the Get-WUHistory cmdlet, you can get the list of updates installed on a computer earlier automatically or manually.
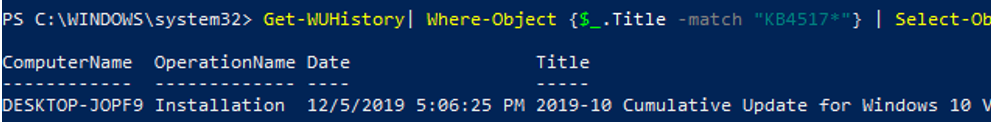
You can get the information about the date of installation of a specific update:
Get-WUHistory| Where-Object <$_.Title -match "KB4517389">| Select-Object *|ft
To find out if the update has been installed on multiple remote computers, you can use this PowerShell code:
«server1″,»server2» | Get-WUHistory| Where-Object <$_.Title -match "KB4011634">| Select-Object *|ft
Remove-WindowsUpdate: Uninstalling Windows Updates
To correctly uninstall the updates from PowerShell, you can use the Remove-WindowsUpdate cmdlet. Just specify the KB number as an argument of the KBArticleID parameter. To delay automatic computer restart, add the –NoRestart key:
Remove-WindowsUpdate -KBArticleID KB4489873 -NoRestart
Hide-WindowsUpdate: How to Hide Windows Updates with PowerShell?
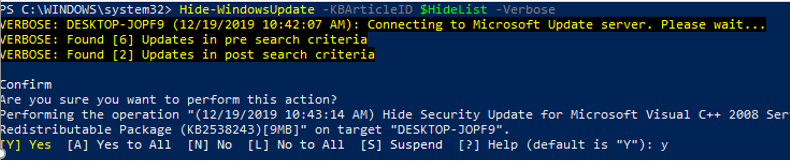
You can hide the specific updates so they will be never installed by Windows Update service on your computer (most often you need to hide the driver updates). For example, to hide the KB4489873 and KB4489243 updates, run these commands:
$HideList = «KB4489873», «KB4489243»
Get-WindowsUpdate -KBArticleID $HideList –Hide
Now the next time you scan for updates using the Get-WUInstall command, the hidden updates won’t be displayed in the list of updates available for installation.
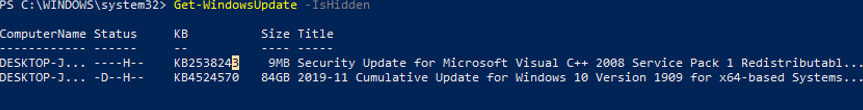
This is how you can display the list of updates hidden on this computer:
Notice that the H (Hidden) attribute has appeared in the Status column of hidden updates.
To remove an update from hidden ones, run this command:
Get-WindowsUpdate -KBArticleID $HideList -WithHidden -Hide:$false
Show-WindowsUpdate -KBArticleID $HideList
For those who feel uncomfortable in the PowerShell console, I would recommend a graphic Windows Update MiniTool to manage Windows 10 updates.
How to get an update through Windows Update
This article describes how to obtain updates from Windows Update in Windows Server 2012 R2.
Original product version: В Windows Server 2012 R2, Windows 7 Service Pack 1
Original KB number: В 3067639
Detailed steps for Windows Server 2012 R2
Swipe in from the right edge of the screen, and then tap Search. Or, if you are using a mouse, point to the lower-right corner of the screen, and then select Search.
In the search box, type Windows Update, and then tap or select Windows Update.
In the details pane, select Check for updates, and then wait while Windows looks for the latest updates for your computer.
If you see a message telling you that important or optional updates are available, or telling you to review important or optional updates, select the message to view the updates to install.
In the list, select the check box for the updates that you want to install under Important or Optional, and then tap or select Install.
Detailed steps for Windows 7 Service Pack 1
Click Start, type update in the search box, in the list of results, click Windows Update.
In the details pane, click Check for updates, and then wait while Windows looks for the latest updates for your computer.
If you see a message telling you that important or optional updates are available, or telling you to review important or optional updates, click the message to view the updates to install.
In the list, select the check box for the updates that you want to install, click OK, and then click Install updates.
Windows Update troubleshooting
If you run into problems when using Windows Update, start with the following steps:
Run the built-in Windows Update troubleshooter to fix common issues. Navigate to Settings > Update & Security > Troubleshoot > Windows Update.
Install the most recent Servicing Stack Update (SSU) that matches your version of Windows from the Microsoft Update Catalog. See Servicing stack updates for more details on servicing stack updates.
Make sure that you install the latest Windows updates, cumulative updates, and rollup updates. To verify the update status, refer to the appropriate update history for your system:
Advanced users can also refer to the log generated by Windows Update for further investigation.
You might encounter the following scenarios when using Windows Update.
Why am I offered an older update?
The update that is offered to a device depends on several factors. The following are some of the most common attributes:
- OS Build
- OS Branch
- OS Locale
- OS Architecture
- Device update management configuration
If the update you’re offered isn’t the most current available, it might be because your device is being managed by a WSUS server, and you’re being offered the updates available on that server. It’s also possible, if your device is part of a deployment group, that your admin is intentionally slowing the rollout of updates. Since the deployment is slow and measured to begin with, all devices will not receive the update on the same day.
My device is frozen at scan. Why?
The Settings UI communicates with the Update Orchestrator service that in turn communicates with to Windows Update service. If these services stop unexpectedly, then you might see this behavior. In such cases, follow these steps:
Close the Settings app and reopen it.
Start Services.msc and check if the following services are running:
- Update State Orchestrator
- Windows Update
Feature updates are not being offered while other updates are
Devices running Windows 10, version 1709 through Windows 10, version 1803 that are configured to update from Windows Update (including Windows Update for Business) are able to install servicing and definition updates but are never offered feature updates.
Checking the WindowsUpdate.log reveals the following error:
The 0x80070426 error code translates to:
Microsoft Account Sign In Assistant (MSA or wlidsvc) is the service in question. The DCAT Flighting service (ServiceId: 855E8A7C-ECB4-4CA3-B045-1DFA50104289) relies on MSA to get the global device ID for the device. Without the MSA service running, the global device ID won’t be generated and sent by the client and the search for feature updates never completes successfully.
To resolve this issue, reset the MSA service to the default StartType of «manual.»
Issues related to HTTP/Proxy
Windows Update uses WinHttp with Partial Range requests (RFC 7233) to download updates and applications from Windows Update servers or on-premises WSUS servers. Therefore proxy servers on the network must support HTTP RANGE requests. If a proxy was configured in Internet Explorer (User level) but not in WinHTTP (System level), connections to Windows Update will fail.
To fix this issue, configure a proxy in WinHTTP by using the following netsh command:
You can also import the proxy settings from Internet Explorer by using the following command: netsh winhttp import proxy source=ie
If downloads through a proxy server fail with a 0x80d05001 DO_E_HTTP_BLOCKSIZE_MISMATCH error, or if you notice high CPU usage while updates are downloading, check the proxy configuration to permit HTTP RANGE requests to run.
You might choose to apply a rule to permit HTTP RANGE requests for the following URLs:
*.download.windowsupdate.com
*.dl.delivery.mp.microsoft.com *.delivery.mp.microsoft.com
If you can’t allow RANGE requests, you’ll be downloading more content than needed in updates (as delta patching will not work).
The update is not applicable to your computer
The most common reasons for this error are described in the following table:
| Cause | Explanation | Resolution |
|---|---|---|
| Update is superseded | As updates for a component are released, the updated component will supersede an older component that is already on the system. When this occurs, the previous update is marked as superseded. If the update that you’re trying to install already has a newer version of the payload on your system, you might receive this error message. | Check that the package that you are installing contains newer versions of the binaries. Or, check that the package is superseded by another new package. |
| Update is already installed | If the update that you’re trying to install was previously installed, for example, by another update that carried the same payload, you may encounter this error message. | Verify that the package that you are trying to install was not previously installed. |
| Wrong update for architecture | Updates are published by CPU architecture. If the update that you’re trying to install does not match the architecture for your CPU, you may encounter this error message. | Verify that the package that you’re trying to install matches the Windows version that you are using. The Windows version information can be found in the «Applies To» section of the article for each update. For example, Windows Server 2012-only updates cannot be installed on Windows Server 2012 R2-based computers. Also, verify that the package that you are installing matches the processor architecture of the Windows version that you are using. For example, an x86-based update cannot be installed on x64-based installations of Windows. |
| Missing prerequisite update | Some updates require a prerequisite update before they can be applied to a system. If you are missing a prerequisite update, you may encounter this error message. For example, KB 2919355 must be installed on Windows 8.1 and Windows Server 2012 R2 computers before many of the updates that were released after April 2014 can be installed. | Check the related articles about the package in the Microsoft Knowledge Base (KB) to make sure that you have the prerequisite updates installed. For example, if you encounter the error message on Windows 8.1 or Windows Server 2012 R2, you may have to install the April 2014 update 2919355 as a prerequisite and one or more pre-requisite servicing updates (KB 2919442 and KB 3173424). To determine if these prerequisite updates are installed, run the following PowerShell command: get-hotfix KB3173424,KB2919355, KB2919442 . If the updates are installed, the command will return the installed date in the InstalledOn section of the output. |
Issues related to firewall configuration
Error that you might see in Windows Update logs:
Go to Services.msc and ensure that Windows Firewall Service is enabled. Stopping the service associated with Windows Firewall with Advanced Security is not supported by Microsoft. For more information, see I need to disable Windows Firewall.
Issues arising from configuration of conflicting policies
Windows Update provides a wide range configuration policy to control the behavior of the Windows Update service in a managed environment. While these policies let you configure the settings at a granular level, misconfiguration or setting conflicting policies may lead to unexpected behaviors.
Device cannot access update files
Ensure that devices can reach necessary Windows Update endpoints through the firewall. For example, for Windows 10, version 2004, the following protocols must be able to reach these respective endpoints:
| Protocol | Endpoint URL |
|---|---|
| TLS 1.2 | *.prod.do.dsp.mp.microsoft.com |
| HTTP | emdl.ws.microsoft.com |
| HTTP | *.dl.delivery.mp.microsoft.com |
| HTTP | *.windowsupdate.com |
| HTTPS | *.delivery.mp.microsoft.com |
| TLS 1.2 | *.update.microsoft.com |
| TLS 1.2 | tsfe.trafficshaping.dsp.mp.microsoft.com |
Be sure not to use HTTPS for those endpoints that specify HTTP, and vice versa. The connection will fail.
The specific endpoints can vary between Windows 10 versions. See, for example, Windows 10 2004 Enterprise connection endpoints. Similar articles for other Windows 10 versions are available in the table of contents nearby.
Updates aren’t downloading from the intranet endpoint (WSUS or Configuration Manager)
Windows 10 devices can receive updates from a variety of sources, including Windows Update online, a Windows Server Update Services server, and others. To determine the source of Windows Updates currently being used on a device, follow these steps:
- Start Windows PowerShell as an administrator.
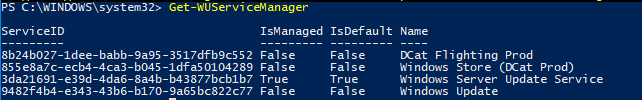
- Run $MUSM = New-Object -ComObject «Microsoft.Update.ServiceManager».
- Run $MUSM.Services.
Check the output for the Name and OffersWindowsUPdates parameters, which you can interpret according to this table.
| Output | Meaning |
|---|---|
| — Name: Microsoft Update -OffersWindowsUpdates: True | — The update source is Microsoft Update, which means that updates for other Microsoft products besides the operating system could also be delivered. — Indicates that the client is configured to receive updates for all Microsoft Products (Office, etc.) |
| — Name: DCat Flighting Prod — OffersWindowsUpdates: True | — Starting with Windows 10 1709, feature updates are always delivered through the DCAT service. — Indicates that the client is configured to receive feature updates from Windows Update. |
| — Name: Windows Store (DCat Prod) — OffersWindowsUpdates: False | -The update source is Insider Updates for Store Apps. — Indicates that the client will not receive or is not configured to receive these updates. |
| — Name: Windows Server Update Service — OffersWindowsUpdates: True | — The source is a Windows Server Updates Services server. — The client is configured to receive updates from WSUS. |
| — Name: Windows Update — OffersWindowsUpdates: True | — The source is Windows Update. — The client is configured to receive updates from Windows Update Online. |
You have a bad setup in the environment
In this example, per the Group Policy set through registry, the system is configured to use WSUS to download updates (note the second line):
From Windows Update logs:
In the above log snippet, we see that the Criteria = «IsHidden = 0 AND DeploymentAction=*» . «*» means there is nothing specified from the server. So, the scan happens but there is no direction to download or install to the agent. So it just scans the update and provides the results.
As shown in the following logs, automatic update runs the scan and finds no update approved for it. So it reports there are no updates to install or download. This is due to an incorrect configuration. The WSUS side should approve the updates for Windows Update so that it fetches the updates and installs them at the specified time according to the policy. Since this scenario doesn’t include Configuration Manager, there’s no way to install unapproved updates. You’re expecting the operational insight agent to do the scan and automatically trigger the download and installation but that won’t happen with this configuration.
High bandwidth usage on Windows 10 by Windows Update
Users might see that Windows 10 is consuming all the bandwidth in the different offices under the system context. This behavior is by design. Components that might consume bandwidth expand beyond Windows Update components.
The following group policies can help mitigate this situation:
Other components that connect to the internet: