- Top Port Scanners on Ubuntu Linux
- 1. Angry IP Scanner
- 4. Nmap — network mapper
- 3. pnscan
- 4. knocker
- Linux / UNIX: Scanning network for open ports with nmap command
- nmap port scanning
- nmap TCP SYN (half-open) scanning
- nmap TCP FIN scanning
- nmap TCP Xmas tree scanning
- nmap TCP Null scanning
- nmap TCP Windows scanning
- nmap TCP RPC scanning
- nmap UDP scanning
- nmap remote software version scanning
- A note about Windows XP / 2003 / Vista version
- 5 Best Free and Open Source Linux Port Scanners
- How to check open ports in Linux using the CLI
- What the hell are a TCP and UDP ports?
- Port numbers
- Check open ports in Linux
- Using netstat to list open ports
- Use ss to list open ports
- Listening ports and applications using lsof command
- nmap command
- The open port doesn’t mean anyone from outside can access those ports
- Conclusion
- Nmap — руководство для начинающих
Top Port Scanners on Ubuntu Linux
Here is a list of port scanners that work on Ubuntu/Linux.
1. Angry IP Scanner
Download and Install from http://www.angryip.org/
Fast and easy to use network scanner and port scanner.
To scan ports got to Tools > Preferences > Ports > Port Selection
Enter the ports you want to scan
Start the scan.
4. Nmap — network mapper
Install : sudo apt-get install nmap
Nmap is a utility for network exploration or security auditing. It supports ping scanning (determine which hosts are up), many port scanning techniques, version detection (determine service protocols and application versions listening behind ports), and TCP/IP fingerprinting (remote host OS or device identification). Nmap also offers flexible target and port specification, decoy/stealth scanning, sunRPC scanning, and more.
nmap also has with an easy to use GUI frontends :
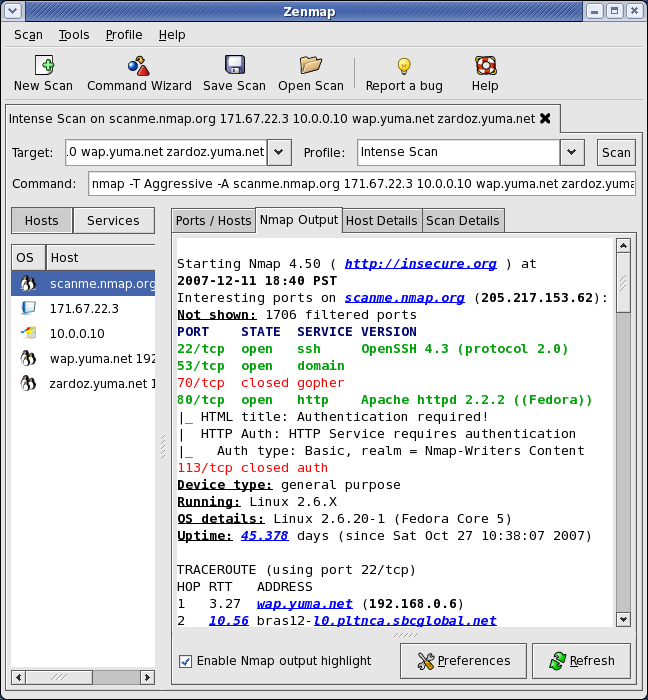
1. zenmap
Install : sudo apt-get install zenmap
http://nmap.org/zenmap/
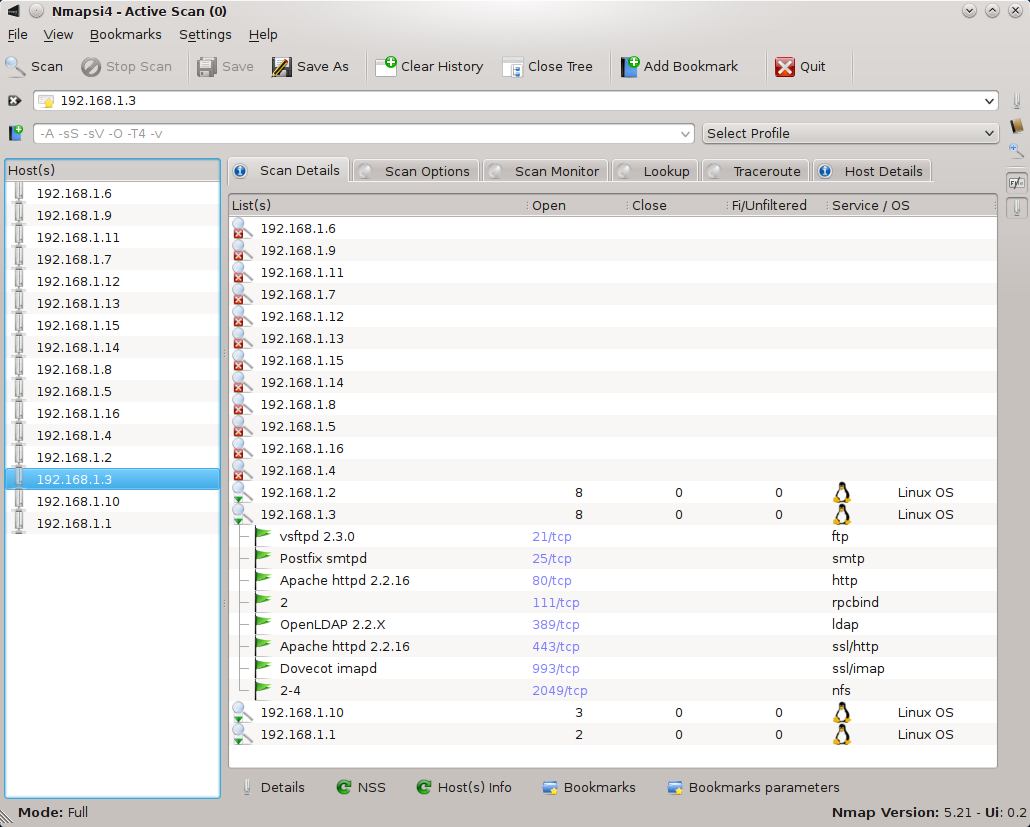
2. Nmapsi4
Install : sudo apt-get install nmapsi4
http://www.nmapsi4.org/
3. Umit
Install : sudo apt-get install umit
http://www.umitproject.org/
3. pnscan
Install : sudo apt-get install pnscan
Pnscan is a multi threaded port scanner that can scan a large network very quickly. If does not have all the features that nmap have but is much faster.
4. knocker
Install : sudo apt-get install knocker
A Tech Enthusiast, Blogger, Linux Fan and a Software Developer. Writes about Computer hardware, Linux and Open Source software and coding in Python, Php and Javascript. He can be reached at [email protected] .
Источник
Linux / UNIX: Scanning network for open ports with nmap command
You can use nmap tool for this job. It is flexible in specifying targets. User can scan entire network or selected host or single server. Nmap is also useful to test your firewall rules. namp is metwork exploration tool and security / port scanner. According to nmap man page:
It is an open source tool for network exploration and security auditing. It was designed to rapidly scan large networks, although it works fine against single hosts. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics. While Nmap is commonly used for security audits, many systems and network administrators find it useful for routine tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime.
nmap port scanning
TCP Connect scanning for localhost and network 192.168.0.0/24
# nmap -v -sT localhost
# nmap -v -sT 192.168.0.0/24
nmap TCP SYN (half-open) scanning
# nmap -v -sS localhost
# nmap -v -sS 192.168.0.0/24
nmap TCP FIN scanning
# nmap -v -sF localhost
# nmap -v -sF 192.168.0.0/24
nmap TCP Xmas tree scanning
Useful to see if firewall protecting against this kind of attack or not:
# nmap -v -sX localhost
# nmap -v -sX 192.168.0.0/24
nmap TCP Null scanning
Useful to see if firewall protecting against this kind attack or not:
# nmap -v -sN localhost
# nmap -v -sN 192.168.0.0/24
nmap TCP Windows scanning
# nmap -v -sW localhost
# nmap -v -sW 192.168.0.0/24
nmap TCP RPC scanning
Useful to find out RPC (such as portmap) services
# nmap -v -sR localhost
# nmap -v -sR 192.168.0.0/24
nmap UDP scanning
Useful to find out UDP ports
# nmap -v -O localhost
# nmap -v -O 192.168.0.0/24
nmap remote software version scanning
You can also find out what software version opening the port.
# nmap -v -sV localhost
# nmap -v -sV 192.168.0.0/24
- No ads and tracking
- In-depth guides for developers and sysadmins at Opensourceflare✨
- Join my Patreon to support independent content creators and start reading latest guides:
- How to set up Redis sentinel cluster on Ubuntu or Debian Linux
- How To Set Up SSH Keys With YubiKey as two-factor authentication (U2F/FIDO2)
- How to set up Mariadb Galera cluster on Ubuntu or Debian Linux
- A podman tutorial for beginners – part I (run Linux containers without Docker and in daemonless mode)
- How to protect Linux against rogue USB devices using USBGuard
Join Patreon ➔
A note about Windows XP / 2003 / Vista version
Windows user can find ipEye and IPSecScan utilities useful. Please note that Nmap also runes on Windows OS.
Read the man page of nmap for more information:
$ man nmap
Источник
5 Best Free and Open Source Linux Port Scanners
A port scanner is a utility which probes a server or host to verify if the virtual ports of a system are open or closed. Ports allow different applications on the same computer to share network resources simultaneously.
Computers that are connected to a local area network or internet run many different services that listen at well-known (and not so well-known) port numbers. Port numbers range from 0 to 65535, with port numbers from 0 to 1023 considered to be the well-known ports. These include ports reserved for the File Transfer Protocol (FTP), Secure Shell (SSH), telnet, Domain Name System (DNS), Hypertext Transfer Protocol (HTTP) used in the World Wide Web, Network News Transfer Protocol (NNTP), to name a few. Port numbers from 1024 to 49151 are known as registered ports, and the range from 49152 to 65535 are allocated to dynamic or private ports.
Port scanning is a popular technique used by attackers to find services that they may be able to compromise. A port scan assists the attacker in finding which ports are available. The scan sends a message to each port, with the response indicating whether the port is used and can therefore be probed further for weaknesses. There are a variety of different forms of scanning which include TCP, SYN, UDP, ACK, Window, and FIN scanning.
However, port scanning has many legitimate uses such as network inventory and the verification of the security of a network. Port scanners therefore represent an important tool for users and system administrators to verify the security policies of their computers and network.
Linux has a good range of port scanners that help administrators identify and rectify weaknesses in a system. To provide an insight into the software that is available, we have compiled a list of 5 of our favorite port scanners. Hopefully, there will be something of interest here for administrators or users that want to scan computers and services that are running on a network. We give our strongest recommendation to Nmap, an indispensable utility to gather information about remote computers.
Let’s explore the 5 port scanners at hand. For each application we have compiled its own portal page, a full description with an in-depth analysis of its features, screenshots, together with links to relevant resources.
Источник
How to check open ports in Linux using the CLI
I need to list all open ports in Linux cloud server. How do I check open ports in Linux using the CLI? Can you give me the command to check open ports in Linux operating system?
To troubleshoot server problems and to avoid security issue, one needs to find out open TCP and UDP ports. In this tutorial, you will learn the different Linux commands to check open ports in Linux for auditing and securing the server.
| Tutorial details | |
|---|---|
| Difficulty level | Easy |
| Root privileges | Yes |
| Requirements | Linux command line |
| Est. reading time | 5 minutes |
What the hell are a TCP and UDP ports?
A port is nothing but a 16-bit number between 0 to 65535. For example, TCP port number 22 may be forwarded to the OpenSSH server. Therefore, 22 port number is a way to identify the sshd (OpenSSH server) process.
Port numbers
- The Well Known Ports are those from 0 through 1023.
- The Registered Ports are those from 1024 through 49151.
- The Dynamic and Private Ports are those from 49152 through 65535.
A registered port is a network port assigned by the Internet Assigned Numbers Authority (IANA) and stored in /etc/services file. Use the cat command or grep command/egrep command to view port numbers and service mappings:
Display a list of applications and their ports assigned by IANA
Check open ports in Linux
The procedure to monitor and display open ports in Linux is as follows:
- Open a Linux terminal application
- Use ss command to display all open TCP and UDP ports in Linux.
- Another option is to use the netstat command to list all ports in Linux.
- Apart from ss / netstat one can use the lsof command to list open files and ports on Linux based system.
- Finally, one can use nmap command to check TCP and UDP ports too.
Let us see all commands and examples in details.
Using netstat to list open ports
- No ads and tracking
- In-depth guides for developers and sysadmins at Opensourceflare✨
- Join my Patreon to support independent content creators and start reading latest guides:
- How to set up Redis sentinel cluster on Ubuntu or Debian Linux
- How To Set Up SSH Keys With YubiKey as two-factor authentication (U2F/FIDO2)
- How to set up Mariadb Galera cluster on Ubuntu or Debian Linux
- A podman tutorial for beginners – part I (run Linux containers without Docker and in daemonless mode)
- How to protect Linux against rogue USB devices using USBGuard
Join Patreon ➔
- -t : All TCP ports
- -u : All UDP ports
- -l : Display listening server sockets
- -p : Show the PID and name of the program to which each socket belongs
- -n : Don’t resolve names
- | grep LISTEN : Only display open ports by applying grep command filter.
Use ss to list open ports
The ss command is used to dump socket statistics. It allows showing information similar to netstat. It can display more TCP and state information than other tools. The syntax is:
sudo ss -tulpn
Sample outputs:
Listening ports and applications using lsof command
Let us run the following to check open TCP and UDP ports using the lsof command:
sudo lsof -i -P -n | grep LISTEN
Where,
- -i : Look for listing ports
- -P : Inhibits the conversion of port numbers to port names for network files. Inhibiting the conversion may make lsof run a little faster. It is also useful when port name lookup is not working properly.
- -n : Do not use DNS name
- | grep LISTEN : Again only show ports in LISTEN state using the grep command as filter.
nmap command
In addition, to above commands one can use the nmap command which is an open source tool for network exploration and security auditing. We are going to use nmap to find and list open ports in Linux:
$ sudo nmap -sT -O localhost
$ sudo nmap -sU -O 192.168.2.254 ##[ list open UDP ports ]##
$ sudo nmap -sT -O 127.0.0.1 ##[ list open TCP ports ]##
$ sudo nmap -sTU -O 192.168.2.24
Sample outputs:
The open port doesn’t mean anyone from outside can access those ports
So far, you know how to find and list open TCP and UDP ports on Linux. However, those ports can still be blocked by software, cloud, or hardware firewall. Hence, you need to verify that your corporate firewall is not blocking incoming or outgoing access. For instance on Linux server we list or dump firewall rules using the following syntax:
sudo iptables -S
# IPv6
sudo ip6tables -S
Conclusion
In conclusion, finding out open ports is one of the most fundamental duties of a Linux system administrator for security reasons. Therefore, close down all unwanted ports and configure firewall such as UFW and FirewallD to open or block ports as per your requirements. After reading this tutorial, you should have a good understanding of how to check for open ports in Linux. See IANA’s offical list of TCP, UDP and other ports here for more information.
🐧 Get the latest tutorials on Linux, Open Source & DevOps via
Источник
Nmap — руководство для начинающих
Многие слышали и пользовались замечательной утилитой nmap. Ее любят и системные администраторы, и взломщики. Даже Голливуд знает про нее — в фильме «Матрица» при взломе используется nmap.
nmap — это аббревиатура от «Network Mapper», на русский язык наиболее корректно можно перевести как «сетевой картограф». Возможно, это не лучший вариант перевода на русский язык, но он довольно точно отображает суть — инструмент для исследования сети и проверки безопасности. Утилита кроссплатформенна, бесплатна, поддерживаются операционных системы Linux, Windows, FreeBSD, OpenBSD, Solaris, Mac OS X.
Рассмотрим использование утилиты в Debian. В стандартной поставке дистрибутива nmap отсутствует, установим его командой
# aptitude install nmap
Nmap умеет сканировать различными методами — например, UDP, TCP connect(), TCP SYN (полуоткрытое), FTP proxy (прорыв через ftp), Reverse-ident, ICMP (ping), FIN, ACK, SYN и NULL-сканирование. Выбор варианта сканирования зависит от указанных ключей, вызов nmap выглядит следующим образом:
Для опытов возьмем специальный хост для экспериментов, созданный самими разработчиками nmap — scanme.nmap.org. Выполним от root’а
Ключи сканирования задавать необязательно — в этом случае nmap проверит хост на наличие открытых портов и служб, которые слушают эти порты.
Запустим командой:
Через несколько секунд получим результат:
Interesting ports on scanme.nmap.org (74.207.244.221):
Not shown: 998 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Ничего необычного, ssh на стандартном порту и http на 80. Nmap распознаёт следующие состояния портов: open, filtered, closed, или unfiltered. Open означает, что приложение на целевой машине готово для принятия пакетов на этот порт. Filtered означает, что брандмауэр, фильтр, или что-то другое в сети блокирует порт, так что Nmap не может определить, является ли порт открытым или закрытым. Closed — не связанны в данный момент ни с каким приложением, но могут быть открыты в любой момент. Unfiltered порты отвечают на запросы Nmap, но нельзя определить, являются ли они открытыми или закрытыми.
# nmap -O scanme.nmap.org
Хинт: Если во время сканирования нажать пробел — можно увидеть текущий прогресс сканирования и на сколько процентов он выполнен. Через несколько секунд получаем ответ, в котором пока что интересна строчка Device type:
Device type: general purpose|WAP|webcam|storage-misc
Running (JUST GUESSING) : Linux 2.6.X|2.4.X (93%), AXIS Linux 2.6.X (89%), Linksys Linux 2.4.X (89%)
Aggressive OS guesses: Linux 2.6.17 — 2.6.28 (93%), Linux 2.6.9 — 2.6.27 (93%), Linux 2.6.24 (Fedora 8) (92%), Linux 2.6.18 (Slackware 11.0) (92%), Linux 2.6.19 — 2.6.26 (92%), OpenWrt (Linux 2.4.32) (91%), Linux 2.6.22 (91%), Linux 2.6.22 (Fedora Core 6) (90%), Linux 2.6.13 — 2.6.27 (90%), Linux 2.6.9 — 2.6.18 (90%)
No exact OS matches for host (test conditions non-ideal).
Вообще, точную версию ядра средствами nmap определить невозможно, но примерную дату «свежести» и саму операционную систему определить можно. Можно просканировать сразу несколько хостов, для этого надо их перечислить через пробел:
# nmap -O example.com example2.com
Вернемся к нашему подопытному хосту. Хочется узнать поподробнее, какой используется софт. Попробуем уточнить полученные данные с помощью ключей -sV:
# nmap -sV example.com example2.com
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.3p1 Debian 3ubuntu7 (protocol 2.0)
80/tcp open http Apache httpd 2.2.14 ((Ubuntu))
Service Info: OS: Linux
Прогресс налицо — мы узнали точные названия используемых служб и даже их версии, а заодно узнали точно, какая операционная система стоит на сервере. С расшифровкой никаких проблем не возникает, все вполне понятно.
Агрессивное сканирование можно провести, указав ключ -A
# nmap -A scanme.nmap.org
Nmap выведет очень много информации, я не стану приводить пример. Сканирование может длится довольно долго, занимая несколько минут.
В локальных сетях или просто имея на руках диапазон ip адресов, удобно проверить их на занятость с помощью ключей -sP:
# nmap -sP 192.168.1.0/24
Сканирование проходит довольно быстро, так как по сути это обычный ping-тест, отвечает ли хост на ping. Следует учесть, что хост может не отвечать на ping из-за настроек фаерволла. Если нужный участок сети нельзя ограничить маской, можно указать диапазон адресов, с какого и по какой надо провести сканирование. Например, есть диапазон адресов с 192.168.1.2 до 192.168.1.5. Тогда выполним:
# nmap -sP 192.168.1.2-5
Ответ будет выглядеть так:
Host 192.168.1.2 is up (0.0023s latency)
Host 192.168.1.3 is up (0.0015s latency)
Host 192.168.1.4 is up (0.0018s latency)
Host 192.168.1.5 is up (0.0026s latency)
В моем случае все ip в данный момент были в сети.
Это далеко не все возможности nmap, но уместить их в рамках одной статьи несколько сложновато.
Если вам ближе GUI — есть замечательная утилита Zenmap — графическая оболочка для nmap, умеющая заодно и строить предполагаемую карту сети.
Хочу предупредить, что сканирование портов на удаленных машинах может нарушать закон.
UDPInflame уточнил, что сканирование портов все-таки не является противозаконным.
Источник