- Permitting Public TCP Traffic to Oracle Compute Cloud Service Instances
- Options
- Before You Begin
- Purpose
- Time to Complete
- Background
- What You Need
- Creating a Security Application
- Creating a Security Rule
- Disabling and Deleting Security Rules
- Disabling a Security Rule
- Deleting a Security Rule
- Want to Learn More?
- Credits
- Linux Firewall (iptables, system-config-firewall)
- Installation
- system-config-firewall
- system-config-firewall-tui
- iptables
- Quick Database Setup
- Connecting to an Instance
- Required IAM Policy
- Prerequisites
- Connecting to a Linux Instance
- Connecting to a Windows Instance
- Prerequisites
- Making the Connection
- Connecting to an Instance on a Private Subnet Using a Bastion
- Troubleshooting the SSH Connection
Permitting Public TCP Traffic to Oracle Compute Cloud Service Instances
Options
Expand All Topics
Hide All Images
Before You Begin
Purpose
This tutorial shows how to permit TCP traffic on a port of your choice from the Internet to an Oracle Compute Cloud Service instance (VM), for the following scenario:
You’ve changed the SSL listen port of the Oracle WebLogic Server Administration Server (in the Oracle WebLogic Server Administration Console) from the default 7002 to another port, say 7004. You must now open port 7004 in Oracle Compute Cloud Service to allow TCP traffic on that port to the Oracle Java Cloud Service node that hosts the Oracle WebLogic Server Administration Server.
Note: You can adapt the steps in this tutorial to permit other traffic flow patterns, such as HTTP requests to all the managed servers in an Oracle Java Cloud Service instance.
Time to Complete
Approximately 15 minutes
Background
When you provision an Oracle Java Cloud Service or Oracle Database Cloud Service instance, by default, certain ports on the underlying Oracle Compute Cloud Service nodes are open. See the links at the end of this tutorial, in the Want to Learn More? section.
To permit traffic on an additional port, you must open that port in Oracle Compute Cloud Service.
What You Need
To perform the steps in this tutorial, you must be a service user with the Compute Monitor and Compute Operations roles.
Creating a Security Application
A security application, in this context, is a mapping between a port number and port type (TCP, UDP, or ICMP).
To open port 7004, you must create a security application for that port in Oracle Compute Cloud Service.
- Sign in to Oracle Cloud My Services and navigate to the Oracle Compute Cloud Service console.
- Click the Network tab and then click the Security Applications tab in the left pane.
- Click Create Security Application.
- In the Create Security Application dialog box, do the following:
- Name: Enter a name for the new security application (for example, tcp_7004). Note this name. You’ll use it later in this tutorial.
- Port Type: Select tcp.
- Port Range Start and Port Range End: In both these fields, enter the port that you want to open (for example, 7004).
- Description: Enter a description for the new security application (for example, TCP traffic to port 7004).
Next, create a security rule to allow TCP traffic from the Internet to the Oracle WebLogic Server Administration Server via port 7004.
Creating a Security Rule
- Sign in to Oracle Cloud My Services and navigate to the Oracle Compute Cloud Service console.
- Go to the Network tab.
- Click the Security Rules tab in the left pane.
- Click Create Security Rule, and do the following:
- Name: Enter a name for the rule (for example, allow_p2admin_tcp_7004).
- Status: Select Enabled.
- Security Application: Select tcp_7004, which is the security application that you created earlier.
- Source: From the Security IP Lists drop-down list, select public-internet.
- Destination: Select ora_admin.
- Description: Enter a description for the rule (for example, Allow TCP traffic to admin server on port 7004).
You can now access the Oracle WebLogic Server Administration Server via port 7004, by using the URL https:// ip_address :7004/console , where ip_address is the public IP address of the Oracle Java Cloud Service node hosting the Oracle WebLogic Server Administration Server. It’s the same address as before the listen port of the administration server was changed. You can find this IP address in the Oracle Java Cloud Service console (Overview tile).
At any time, you can temporarily suspend security rules by disabling them. You can also delete security rules that you no longer need.
Disabling and Deleting Security Rules
Disabling a Security Rule
- Sign in to Oracle Cloud My Services and navigate to the Oracle Compute Cloud Service console.
- Go to the Network tab.
- Click the Security Rules tab in the left pane.
- Identify the security rule you want to disable.
- From the Actions menu, select Update.
- In the resulting dialog box, change Status to Disabled.
- Click Update.
Deleting a Security Rule
- Sign in to Oracle Cloud My Services and navigate to the Oracle Compute Cloud Service console.
- Go to the Network tab.
- Click the Security Rules tab in the left pane.
- Identify the security rule you want to delete.
- From the Actions menu, select Delete.
- At the confirmation prompt, click Yes.
Want to Learn More?
Enabling Access to a Port in the Virtual Machine in Using Oracle Database Cloud Service (Database as a Service)
Managing Security Rules in Using Oracle Compute Cloud Service (for PaaS)
Managing Security Applications in Using Oracle Compute Cloud Service (for PaaS)
Credits
Lead Curriculum Developer: Kumar Dhanagopal
Other Contributors: Octave Orgeron
Источник
Linux Firewall (iptables, system-config-firewall)
This article covers basic Linux firewall management, with specific reference to the information needed for the RHCSA EX200 certification exam. Extra information is required for the RHCE EX300 certification exam, which will be supplied by another article.
Remember, the exams are hands-on, so it doesn’t matter which method you use to achieve the result, so long as the end product is correct.
Installation
Most installations will include the firewall functionality. If you need to manually install it, the following commands will install the IP4 and IP6 firewall functionality. In this article we will only consider the IP4 settings.
Make sure the service is started and will auto-start on reboot.
You can check the current status of the service using the following command.
To disable the firewall, run the following commands.
system-config-firewall
The GUI screen to control the firewall is available from the menu (System > Administration > Firewall) or can be started from the command line using the system-config-firewall command. If it is not already present, it can be installed using the following command.
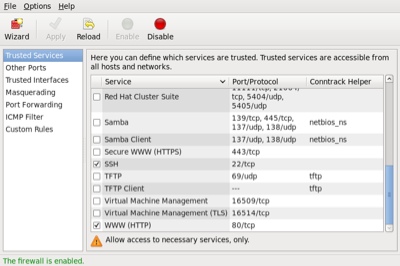
Once started, the toolbar provides buttons to allow the firewall to be enabled/disabled. You can also configure basic trusted services, such as SSH, FTP and HTTP, by putting a tick in the appropriate checkbox and clicking the «Apply» button on the toolbar.
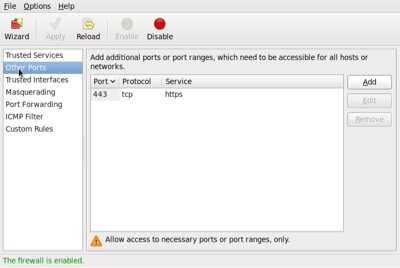
The «Other Ports» section allows you to open ports that are not covered in the «Trusted Services» section.
system-config-firewall-tui
The TUI utility is similar to the GUI utility shown above, but it feels incredibly clumsy in comparison. If it is not already present, it can be installed using the following command.
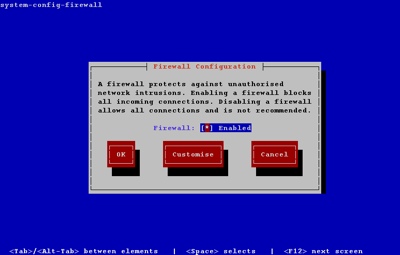
Running the system-config-firewall-tui command from the command line produces the top-level screen, allowing you to enable/disable the firewall. Use the space bar to toggle the setting, the tab key to navigate between buttons and the return key to click them.
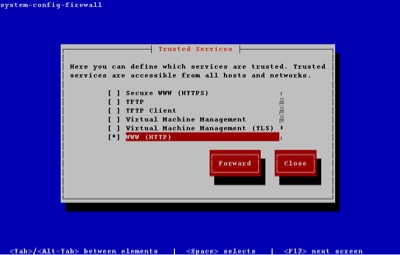
To alter the Trusted Services, tab to the «Customize» button and press the return key. Amend the list using the arrow and space keys.
You can close out of the customization section at any point. The other sections of the GUI tool are available by clicking the «Forward» button on each successive screen.
iptables
In addition to the GUI and TUI interfaces, the firewall rules can be amended directly using the iptables command. There are vast number of parameters, so I will just focus on the elements necessary for the RHCSA exam.
The firewall consists of chains of rules that determine what action should be taken for packets processed by the system. By default, there are three chains defined:
- INPUT : Used to check all packets coming into the system.
- OUPUT : Used to check all packets leaving the system.
- FORWARD : Used to check all packets being routed by the system. Unless you are using your server as a router, this chain is unnecessary.
Each chain can contain multiple explicit rules that are checked in order. If a rule matches, the associated action ( ACCEPT and DROP being the most common) is taken. If no specific rule is found, the default policy is used to determine the action to take.
Since the default policy is a catch-all, one of two basic methods can be chosen for each chain.
- Set the default policy to ACCEPT and explicitly DROP things you don’t want.
- Set the default policy to DROP and explicitly ACCEPT things you do want.
The safest option is to set the default policy to DROP for the INPUT and FORWARD chains, so it is perhaps a little surprising that the GUI and TUI tools set the default policies to ACCEPT , then use an explicit REJECT as the last rule in these chains.
This works fine, but if you accidentally get rid of the last rule in the chain you are in trouble. For this reason, for the remainder of this section I will assume that the default policy for INPUT and FORWARD is DROP . For the OUTPUT chain I will assume any packets originating from the system are safe, so I will ACCEPT any outgoing packets.
The default policy for a chain is set using the «-P» flag. In the following example, assuming no specific rules were present, all communication to and from the server would be prevented.
Warning: If you are administering the firewall via SSH, having a default INPUT policy of DROP will cut your session off if you get rid of the explicit rules that accept SSH access. As a result, it makes sense to start any administration by setting the default policies to ACCEPT and only switch them back to DROP once the chains have been built to your satisfaction. The following example temporarily sets the default policies to ACCEPT .
The next thing we want to do if flush any existing rules, leaving just the default policies. This is done using the «-F» flag.
Now we need to define specific rules for the type of access we want the server to have. Focusing on the INPUT chain, we can grant access to packets in a number of ways.
Once the explicit rules are defined, we need to set the real default policies.
Rule and policy definitions take effect immediately.To make sure they persists beyond reboot the current configuration must be saved to the «/etc/sysconfig/iptables» file using the following command.
If you are using Fedora, you may need to use the following command instead.
As you can imagine, even in a simple configuration this process can get a bit long-winded, so it makes sense to combine all the elements of the firewall definition into a single file so it can be amended and run repeatedly. Create a file called «/root/firewall.sh» with the following contents. Think of this as your starting point for each server.
Make the file executable.
Run the file to set the required firewall rules.
The iptables command also allows you to insert (-I), delete (-D) and replace (-R) rules, but if you work using a file as described above, you never need to use these variations.
Quick Database Setup
If you are using the server as an Oracle database server, you will probably want to make sure the SSH and Oracle listener ports are accessible. You could lock these down to specific source IP addresses, but for a quick setup, you could just do the following, where «1521» is the port used for the listener.
Источник
Connecting to an Instance
You can connect to a running instance by using a Secure Shell (SSH)В or Remote Desktop connection. Most UNIX-style systems include an SSH client by default. Windows 10 and Windows Server 2019 systems should include the OpenSSH client, which you need if you created your instance using the SSH keys generated by Oracle Cloud Infrastructure . For other Windows versions, you can download a free SSH client called PuTTY from http://www.putty.org.
Note
If you created an instance without an SSH key, you can use the serial console to boot into maintenance mode and add or reset the SSH key for the opc user or reset the password for the opc user. Alternately, you can stop the instance, attach the boot volume to a new instance, and configure SSH on the new instance.
Required IAM Policy
To connect to a running instance with SSH, you don’t need an IAM policyВ to grant you access. However, to SSH you need the public IP address of the instance (see Prerequisites below). If there’s a policy that lets you launch an instance, that policy probably also lets you get the instance’s IP address. The simplest policy that does both is listed in Let users launch compute instances.
For administrators: Here’s a more restrictive policy that lets the specified group get the IP address of existing instances and use power actions on the instances (e.g., stop, start, etc.), but not launch or terminate instances. The policy assumes the instances and the cloud network are together in a single compartment (XYZ):
Prerequisites
You’ll need the following information to connect to the instance:
- The public IP address of the instance. You can get the address from the Instance Details page in the Console . Open the navigation menu and click Compute . Under Compute , click Instances. Then, select your instance. Alternatively, you can use the Core Services API ListVnicAttachments and GetVnic operations.
- The default username for the instance. If you used a platform image for Linux, CentOS, or Windows to launch the instance, the username is opc . If you used an Ubuntu platform image to launch the instance, the username is ubuntu .
- For Linux instances: The full path to the private key portion of the SSH keyВ pair that you used when you launched the instance. For more information about key pairs, see Managing Key Pairs on Linux Instances.
- For Windows instances: If you’re connecting to the instance for the first time, you will need the initial password for the instance. You can get the password from the Instance Details page in the Console .
Connecting to a Linux Instance
You connect to a Linux instance using SSH.
Use the following command to set the file permissions so that only you can read the file:
is the full path and name of the file that contains the private key associated with the instance you want to access.
Use the following SSHВ command to access the instance.
Note
Copy the following example to ensure the correct characters are used. If the wrong character is used in ssh -i , a Could not resolve hostname . No such host is known. error might occur.
is the full path and name of the file that contains the private key associated with the instance you want to access.
is the default username for the instance. For Oracle Linux and CentOS images, the default username is opc . For Ubuntu images, the default username is ubuntu .
is your instance IPВ address that you retrieved from the Console .
If the instance uses a key pair that was generated by Oracle Cloud Infrastructure , use the following procedure.
If this is the first time you are using this key pair, you must set the file permissions so that only you can read the file. Do the following:
- In Windows Explorer, navigate to the private key file, right-click the file, and then click Properties.
- On the Security tab, click Advanced.
- On the Permissions tab, for Permission entries, under Principal, ensure that your user account is listed.
- Click Disable Inheritance, and then select Convert inherited permissions into explicit permissions on this object.
- For Permission entries, select each permission entry that is not your user account and click Remove.
- Ensure that the access permission for your user account is Full control.
- Save your changes.
To connect to the instance, open Windows PowerShell and run the following command:
Note
Copy the following example to ensure the correct characters are used. If the wrong character is used in ssh -i , a Could not resolve hostname . No such host is known. error might occur.
is the full path and name of the file that contains the private key associated with the instance you want to access.
is the default username for the instance. For Oracle Linux and CentOS images, the default username is opc . For Ubuntu images, the default username is ubuntu .
is your instance IPВ address that you retrieved from the Console .
SSH private key files generated by Oracle Cloud Infrastructure are not compatible with PuTTY. If you are using a private key file generated during the instance creation process you need to convert the file to a .ppk file before you can use it with PuTTY to connect to the instance.
Note
If you changed the file permissions on your key to connect from a Windows system using OpenSSH, the key will not work with a PuTTY connection. Use OpenSSH to connect instead.
Convert a generated .key private key file:
Click Load, and select the private key generated when you created the instance. The extension for the key file is .key .
Click Save private key.
Specify a name for the key. The extension for new private key is .ppk .
Connect to the Linux instance using a .ppk private key file:
If the instance uses a key pair that you created using PuTTY Key Generator, use the following procedure.
In the Category pane, select Session and enter the following:
Host Name (or IP address):
is the default username for the instance. For Oracle Linux and CentOS images, the default username is opc . For Ubuntu images, the default username is ubuntu .
is your instance public IPВ address that you retrieved from the Console
Click Browse, and then select your .ppk private key file.
Click Open to start the session.
If this is your first time connecting to the instance, you might see a message that the server’s host key is not cached in the registry. Click Yes to continue the connection.
Tip
If the connection fails, you may need to update your PuTTY proxy configuration.
Connecting to a Windows Instance
You can connect to a Windows instance using a Remote Desktop connection. Most Windows systems include a Remote Desktop client by default.
Prerequisites
To use Remote Desktop Protocol (RDP) to access the Windows instance, you need to add a stateful ingress security rule for TCP traffic on destination port 3389 from source 0.0.0.0/0 and any source port. You can implement this security rule in either a network security group that the Windows instance belongs to or a security list that is used by the instance’s subnet.
- Open the navigation menu and click Compute . Under Compute , click Instances.
- Click the instance that you’re interested in.
- Under Instance details, for Virtual cloud network, click the name of the cloud network. The Virtual Cloud Network Details page opens.
To add the rule to a network security group that the instance belongs to:
- Under Resources, click Network Security Groups.
- Click the network security group that you’re interested in.
- Click Add Ingress Rules.
Enter the following values for the rule:
- Stateless: Leave the check box cleared.
- Direction: Leave Ingress selected.
- Source Type: CIDR
- Source CIDR: 0.0.0.0/0
- IPВ Protocol: RDP (TCP/3389)
- Source Port Range: All
- Destination Port Range: 3389
- Description: An optional description of the rule.
- Open the navigation menu and click Compute . Under Compute , click Instances.
- Click the instance that you’re interested in.
- Under Primary VNIC, for Subnet, click the name of the subnet. The Subnet Details page opens.
To add the rule to a security list that is used by the instance’s subnet:
- Under Resources, click Security Lists.
- Click the security list that you’re interested in.
- Click Add Ingress Rules.
Enter the following values for the rule:
- Stateless: Leave the check box cleared.
- Source Type: CIDR
- Source CIDR: 0.0.0.0/0
- IPВ Protocol: RDP (TCP/3389)
- Source Port Range: All
- Destination Port Range: 3389
- Description: An optional description of the rule.
Making the Connection
- Open the Remote Desktop client.
- In the Computer field, enter the public IP address of the instance. You can retrieve the public IP address from the Console .
- The User name is opc . Depending on the Remote Desktop client you are using, you might have to connect to the instance before you can enter this credential.
- Click Connect to start the session.
- Accept the certificate if you are prompted to do so.
If you are connecting to the instance for the first time, enter the initial password that was provided to you by Oracle Cloud Infrastructure when you launched the instance. You will be prompted to change the password as soon as you log in. Your new password must be at least 12 characters long and must comply with Microsoft’s password policy.
Otherwise, enter the password that you created. If you are using a custom image, you might need to know the password for the instance that the image was created from. For details about Windows custom images, see Creating Windows Custom Images.
Connecting to an Instance on a Private Subnet Using a Bastion
A subnet attached to an instance is either public or private. Instances on a private subnet can’t have public IP addresses. Oracle Cloud Infrastructure Bastion provides restricted and time-limited access to instances that don’t have public IP addresses.
Bastions let authorized users connect from specific IP addresses to instances using SSH sessions. When connected to a session, users can interact with the instance by using any software or protocol supported by SSH.
The Bastion service recognizes two types of sessions.
- Managed SSH sessions provide administrative access to the instance’s operating system. To connect to an instance using this session type the Bastion plugin must be enabled on the instance, and plugins must be running. For more information about how to enable and run plugins, see Managing Plugins with Oracle Cloud Agent.
- Port forwarding sessions (also known as SSH tunneling) create a secure connection between a specific port on the client machine and a specific port on the instance. Using this SSH connection you can relay other protocols like the Remote Desktop Protocol (RDP).
Troubleshooting the SSH Connection
If you’re unable to connect to your instance using SSH, follow these troubleshooting steps to identify common problems.
- Verify your connection: In your terminal window, run nc
If the SSH banner displays: You successfully connected to your instance using SSH. The underlying problem might be related to permissions. As a next step, verify your credentials. If the credentials you’re using to SSH to the instance are incorrect, the connection fails.
For Linux instances, you need the full path to the private key portion of the SSH keyВ pair that you used when you launched the instance. For more information about key pairs, see Managing Key Pairs on Linux Instances. For Windows instances, if you’re connecting to the instance for the first time, you need the initial password for the instance. You can get the password from the Instance Details page in the Console .
Capture serial console history: You can capture your instance’s serial console data history in the Console or by using the console-history resource in the CLI. This information can help determine the cause of connectivity problems. For more information about using the CLI, see console-history and Command Line Interface (CLI).
When using the CLI to capture the instance’s serial console data history, you need to include the following option to ensure that full history is captured. Without this option, the data might be truncated: —length 10000000 .
Источник