- How to Update An Oracle Linux Kernel Without Rebooting
- Ksplice Uptrack Command-Line Tools
- Automatic Updates
- Your Package Manager
- Firewall and Proxy Configuration
- Graphical Interface
- Web Interface
- Overview
- Machine Detail Pages
- Access Policies
- Notification and Monitoring
- E-mail Notifications
- Oracle linux upgrade kernel
- OS Kernel Updates
- Oracle Yum Plug-in
- Manual Updates
How to Update An Oracle Linux Kernel Without Rebooting
by the Oracle Linux Ksplice team
Published December 2012
The uptrack-update command applies patches to your Linux kernel while your system is still running.
Articles, software downloads, documentation, and other resources for Oracle sysadmins. Hear about them and discuss on the Oracle Sysadmin Facebook page.
A Ksplice Uptrack subscription gets you so much more than rebootless kernel updates. Here are some details.
Ksplice Uptrack Command-Line Tools
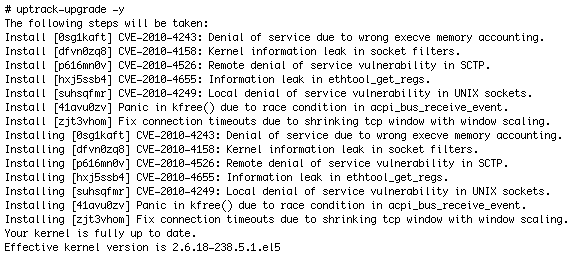
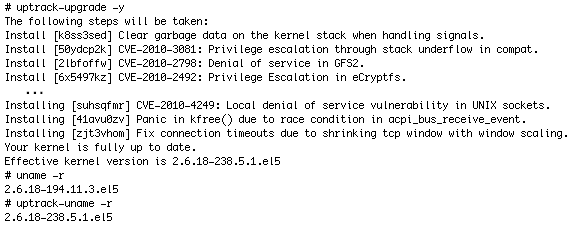
uptrack-upgrade
Ksplice updates are the same security and bug-fix updates you would get from your Linux vendor, packaged in a special rebootless form. To apply Ksplice updates, just run uptrack-upgrade , as shown in Listing 1:
Listing 1. Running the uptrack-upgrade Command
You can apply all available updates, bringing your system instantly up to date, by running uptrack-upgrade -y , or you can apply updates individually by specifying a Ksplice ID (the characters in brackets in Listing 1).
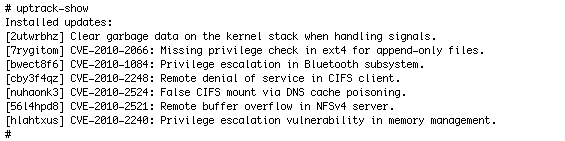
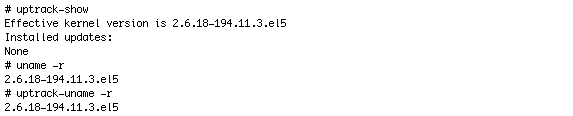
uptrack-show
You can see what updates have been installed by running uptrack-show , as shown in Listing 2:
Listing 2. Running the uptrack-show Command
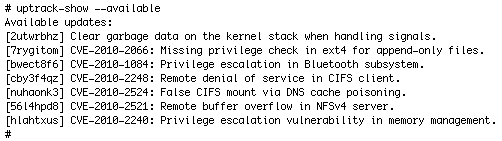
You can see what updates are available to be installed by running uptrack-show —available , as shown in Listing 3:
Listing 3. Running the uptrack-show —available Command
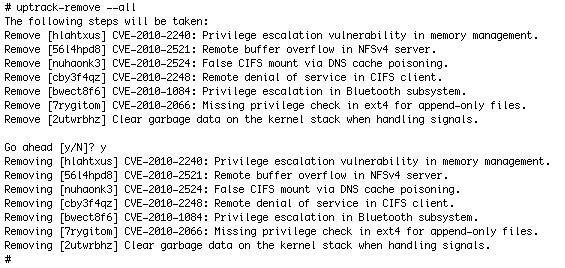
uptrack-remove
Removing Ksplice updates is easy: just run uptrack-remove . As with uptrack-upgrade , you can uninstall all updates, bringing you back to your original stock kernel, or uninstall individual updates by specifying a Ksplice ID, as shown in Listing 4:
Listing 4. Running the uptrack-remove Command
Running uptrack-show verifies that there are no updates installed after running uptrack-remove , as shown in Listing 5:
Listing 5. Running the uptrack-show Command
uptrack-uname
Ksplice Uptrack does not change the output of uname , and uname will continue to reflect the version of the kernel into which a machine was booted.
Instead, once you install updates, use uptrack-uname to see what effective kernel a machine is running. The uptrack-uname command has the same format as uname and supports the common uname flags, including -r and -a .
Before installing updates, the original kernel and effective kernel are the same, and uname and uptrack-uname report the same information, as shown in Listing 6:
Listing 6. Checking the Kernel Version Before Updating
After installing updates, uptrack-uname reflects the updated running kernel, as shown in Listing 7:
Listing 7. Checking the Kernel Version After Updating
You can also see a machine’s effective kernel on the Web interface or through the API.
Automatic Updates
You can configure your systems to automatically install updates as they become available. To enable autoinstall, set autoinstall = yes in your /etc/uptrack/uptrack.conf file, or pass the —autoinstall flag during installation.
Autoinstall is the most popular configuration. It is a scalable way to ensure that updates get installed quickly as they become available, regardless of when they are released.
Please note that enabling autoinstall does not mean the Ksplice Uptrack client itself is automatically upgraded. You will be notified via e-mail when a new Ksplice Uptrack client is available, and you can upgrade the client through your package manager.
Your Package Manager
Ksplice Uptrack updates your running kernel in memory. We recommended that, in addition to using Ksplice, you continue to use your package manager to update the kernel on disk as new kernels become available. That way, if a reboot becomes necessary (for example, after a power loss or a hardware upgrade), you have the option of booting into a newer kernel. Under this plan, you would install all the updates available via both Ksplice Uptrack and your package manager.
Ksplice Uptrack also works great in environments where it is desirable to stay with a particular original kernel version (for example, because of third-party modules that are compiled against that kernel), but you want to stay up to date with all the important security and reliability updates for your kernel.
By default, Ksplice Uptrack will reinstall rebootless updates during the boot process. That way you remain secure even after a reboot. You can configure this behavior with the install_on_reboot option in your /etc/uptrack/uptrack.conf file.
Firewall and Proxy Configuration
The Ksplice Uptrack client communicates with the Ksplice Uptrack server by connecting to https://updates.ksplice.com:443 . You can either make your firewall allow those connections or configure the client to use a proxy server.
To configure Ksplice Uptrack to use a proxy server, edit your /etc/uptrack/uptrack.conf file and set the https_proxy option (in the [Network] section) to a value of the form [protocol://]host[:port] .
Graphical Interface
This feature is currently available for Ubuntu 12.04, 11.10, 11.04, and 10.04 LTS and for Fedora 17 and 16.
If you’d like to see it for your distribution, please contact us.
After Ksplice Uptrack is installed, a panel icon will notify you when new kernel updates are available, as shown in Figure 1:
Figure 1. Ksplice Uptrack Alert Icon
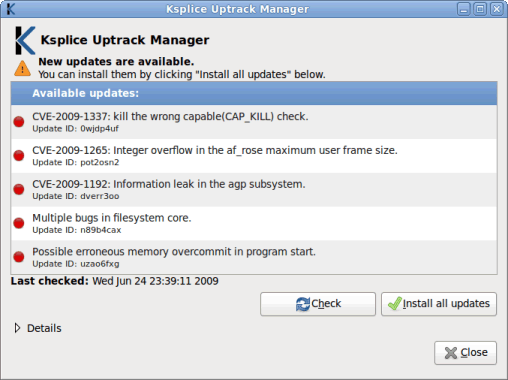
You can click the icon to view the available updates, as shown in Figure 2:
Figure 2. New Updates Available
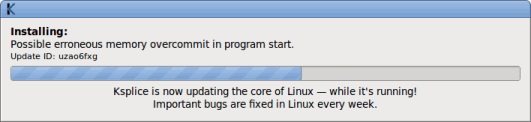
Click the Install all updates button to start the update process. A progress bar shows you the updates as they are being installed, as shown in Figure 3:
Figure 3. Progress Bar During Update
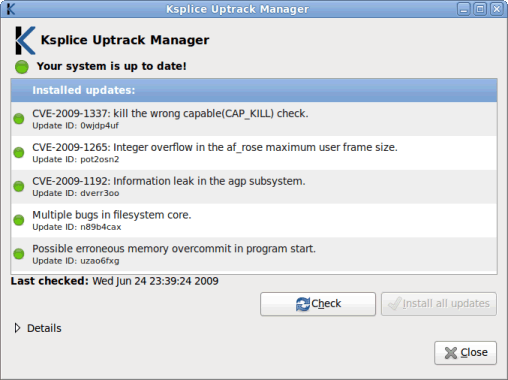
When the process is complete, the update list will look like Figure 4:
Figure 4. Ksplice Uptrack Update List
The panel icon will also return to normal, as shown in Figure 5:
Figure 5. Normal Panel Icons
Your kernel is now up to date and secure!
Web Interface
A Ksplice Uptrack subscription comes with a Web interface that summarizes important information about your machines and will tell you if Ksplice is currently working on new updates for your distributions. Log in to your Web interface at https://uptrack.ksplice.com.
Overview
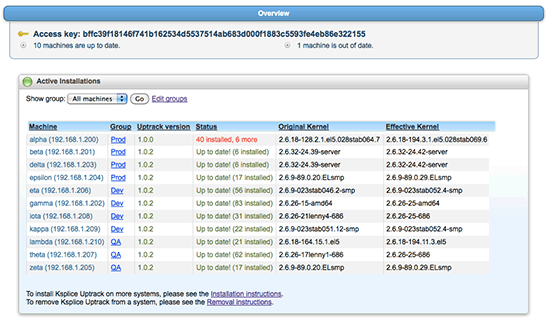
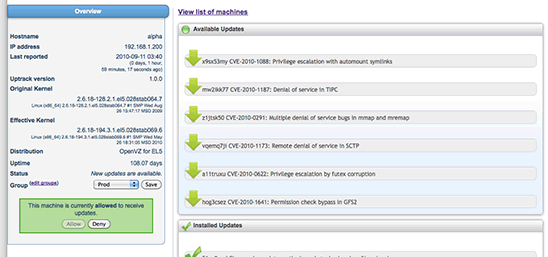
See what machines are up to date and what machines need attention in one easy summary on the Overview page shown in Figure 6:
Figure 6. Ksplice Uptrack Overview Page
Beyond machines with available updates, the Overview page also has notifications for the following items, and more:
- Rebootless updates currently in progress for your distributions
- New Ksplice Uptrack client releases
- Inactive machines (those that have stopped using Ksplice Uptrack or can’t communicate with the Ksplice Uptrack servers)
You can also group your machines for easy management.
Machine Detail Pages
Get an in-depth look at your machine’s status on its machine detail page, where you can see the available and installed updates, basic system information, uptime, and when the machine last communicated with a Ksplice Uptrack server, as shown in Figure 7:
Figure 7. Ksplice Uptrack Machine Detail Page
Access Policies
Want an extra layer of control over which machines using your access can use the Ksplice Uptrack service? Maybe you manage Uptrack-enabled machines for other people and want to let them use the service while still having control over which machines have access.
It’s easy to customize your Ksplice Uptrack access policies to get the access control you want!
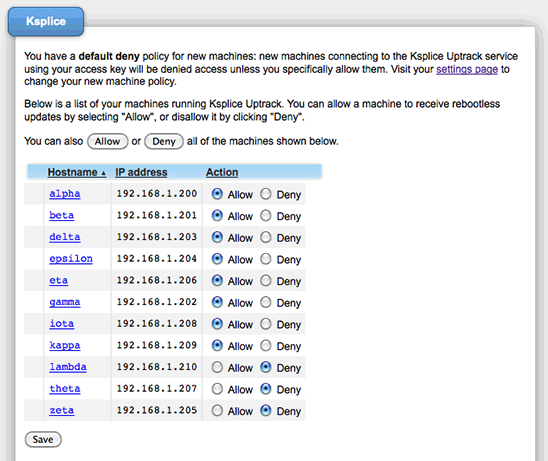
You can set access policies for an individual machine or groups of existing machines as well as set a default access policy for new machines. For example, you might use a default deny policy, in which machines that have just installed Ksplice Uptrack cannot receive updates from the Uptrack servers until you specifically authorize them (see Figure 8):
Figure 8. Ksplice Uptrack Access Policies
Notification and Monitoring
E-mail Notifications
When new rebootless updates are available for one of your distributions, we’ll send an announcement to your technical contact address. (You can configure this address on the Settings page of your Web interface.)
Monitoring
The Python bindings and Nagios plug-in can be installed through your package manager or from a tarball on the Ksplice Uptrack Website.
Источник
Oracle linux upgrade kernel
Oracle Linux 6 Update 7 ships with the latest Unbreakable Enterprise Kernel Release 2 for i386 and Unbreakable Enterprise Kernel Release 3 for x86-64. If you upgrade your system from the installation media, there are four upgrade scenarios:
If the UEK R2 or UEK R3 is not currently installed on the system, only the latest Red Hat Compatible Kernel is installed. The UEK R2 or UEK R3 kernel is not installed.
If UEK R2 is currently installed on an i386 system, the latest version of the UEK R2 kernel is installed.
If UEK R2 is currently installed on an x86-64 system and you upgrade using the Oracle Linux 6 Update 7 installation media for x86-64, which do not contain a UEK R2 repository, the latest version of UEK R2 is not installed.
If UEK R3 is currently installed on an x86-64 system, the latest version of the UEK R3 kernel is installed.
yum uses whatever repositories you have configured on your system to upgrade it. You can find the latest UEK R2 packages in the ol6_i386_UEK_latest and ol6_x86_64_UEK_latest repositories and the latest UEK R3 packages in the ol6_UEKR3_latest repository.
If you want to install the latest UEK R2 kernel on an i386 or x86-64 system, subscribe your system to the ol6_i386_UEK_latest or ol6_x86_64_UEK_latest channel on ULN, or configure the repository in the /etc/yum.repos.d/public-yum-ol6.repo file as shown here:
If you want to update an x86-64 system to use the latest UEK R3 kernel, subscribe your system to the ol6_x86_64_UEKR3_latest channel on ULN, or configure the repositories in the /etc/yum.repos.d/public-yum-ol6.repo file as shown here:
Copyright В© 2017, Oracle and/or its affiliates. All rights reserved. Legal Notices
Источник
OS Kernel Updates
Note
This topic applies only to Linux instances that were launched before February 15, 2017. Linux instances launched on or after February 15, 2017 boot directly from the image and do not require further action for kernel updates.
Oracle Cloud Infrastructure boots each instance from a network drive. This configuration requires additional actions when you update the OS kernel.
Oracle Cloud Infrastructure uses Unified Extensible Firmware Interface (UEFI) firmware and a Preboot eXecution Environment (PXE) interface on the host server to load iPXE from a Trivial File Transfer Protocol (TFTP) server. The iPXE implementation runs a script to boot Oracle Linux. During the boot process, the system downloads the kernel, the initrd file, and the kernel boot parameters from the network. The instance does not use the host’s GRUB boot loader.
Normally, the yum update kernel-uek command edits the GRUB configuration file, either grub.cfg or grub.conf , to configure the next boot. Since bare metal instances do not use the GRUB boot loader, changes to the GRUB configuration file are not implemented. When you update the kernel on your instance, you also must upload the update to the network to ensure a successful boot process. The following approaches address this need:
- Instances launched from platform images include an Oracle yum plug-in that seamlessly handles the upload when you run the yum update kernel-uek command.
- If you use a custom image based on a platform image, the included yum plug-in will continue to work, barring extraordinary changes.
- If you install your own package manager, you must either write your own plug-in or upload the kernel, initrd, and kernel boot parameters manually.
Oracle Yum Plug-in
On instances launched with a platform image, you can find the Oracle yum plug-in at:
The plug-in configuration is at:
The plug-in looks for two variables in the /etc/sysconfig/kernel file, UPDATEDEFAULT and DEFAULTKERNEL . It picks up the updates only when the first variable is set to «yes» and the DEFAULTKERNEL value matches the kernel being updated. For example:
Platform images incorporate the Unbreakable Enterprise Kernel (UEK). If you want to switch to a non-UEK kernel, you must update the DEFAULTKERNEL value to «kernel» before you run yum update kernel .
Manual Updates
Tip
Oracle recommends using the Oracle yum plug-in to update the kernel.
If you manually upload the updates, there are four relevant URLs:
The first three URLs are for uploading files (HTTPВ request type PUT). The fourth URL is for activating the uploaded files (HTTP request type POST). The system discards the uploaded files if they are not activated before the host restarts.
The kernel and initrd are simple file uploads. The cmdline upload must contain the kernel boot parameters found in the grub.cfg or grub.conf file, depending on the Linux version. The following example is an entry from the /boot/efi/EFI/redhat/grub.cfg file in Red Hat Linux 7. The highlighted text represents the parameters to upload.
The following command returns what is being uploaded to the cmdline file.
A typical response resembles the following.
The following commands update the cmdline and initrd files, and then activate the changes.
Источник