- How to manage Linux permissions for users, groups, and others
- Linux security
- Setting up a playground
- How do I create directories and files?
- How do I manage ownership and groups?
- How do I manage permissions?
- How do I use absolute mode?
- More Linux resources
- How do I use symbolic mode?
- Special permissions and Access Control Lists
- Wrap up
- Permissions
- File Permissions
- chmod
- Directory Permissions
- Becoming the Superuser for a Short While
- Changing File Ownership
- Changing Group Ownership
- Further Reading
How to manage Linux permissions for users, groups, and others
Photo by Min An from Pexels
Managing access to resources is a fundamental task for sysadmins. This responsibility consists of three components: identities, resources, and permissions. This article covers several user, group, and file management commands to control access to resources. The article uses a «How do I…?» format, and it assumes you have a few resources to work with. Specifically, I cover the following topics:
- Creating directories and files
- Managing ownership and associated groups
- Setting permissions with absolute and symbolic modes
Linux security
Setting up a playground
I’ve been in IT for about 25 years, and most of that time was spent as a technical trainer. That means that the things that I write are usually structured as some sort of lab or other hands-on opportunity. It’s just how I cover material. With that in mind, I’ll assume you have a couple of identities and resources to experiment with as you read the rest of the article. You can use the following commands to set up a playground. It’s best to do this on a virtual machine rather than your personal Linux box, but these tasks are relatively harmless.
Create two new users and two new groups to work with. Note that you do not need to configure passwords for the users in this exercise, as you won’t log on with those accounts.
Note: You would use the passwd user01 command to set the user’s password.
In your home directory, create a new directory named playground :
Change into the
/playground directory by using the cd command. You are ready to work with the commands and concepts below.
When you’ve completed the article and learned the techniques I’ve covered, delete the two user accounts, the groups, and the playground directory. Use rm -fR /playground , userdel user01 , and groupdel groupA to remove the resources.
How do I create directories and files?
Use the mkdir command to create directories. The touch command is one of many ways to create files.
How do I create a directory named Resources ?
How do I create a directory path (a series of directories that don’t yet exist)?
Note: The goal here is to create the 2020data directory, but the given path’s data directory does not yet exist. The -p option creates parent directories as needed to complete the path.
How do I create a file named file1 ?
How do I create several files at once?
How do I manage ownership and groups?
In the playground directory, display the current owner and group associated with the Resources directory and the files.
How do I display permission, owners, and groups?
The ls -l command displays directory contents in long format. The long format contains both permissions and ownership. You can see that the user account that created the resources also owns those resources. The group association is also that user’s primary group.
How do I change the user/owner associated with file1 ?
How do I change the group associated with file1 ?
How do I change the owner and group at the same time for file2 ?
There is a specific chgrp command, but I prefer only to memorize one command ( chown ) and apply it to both functions (user and group associations) rather than chown for the user and then have to recall chgrp for the group.
So how do I use chgrp ?
How do I change the user/group for a directory and all of its contents?
The above task provides a recursive configuration. Technically, recursive commands are repeated on each specified object. Effectively, recursive means «this and everything in it.» In the above example, you are configuring the related user/group for the Resources directory and everything in it. Without the -R option, you would only affect the Resources directory itself, but not its contents.
How do I manage permissions?
The change mode or chmod command sets permissions. The syntax is straight-forward:
Here are two examples of manipulating permissions for file2 :
But wait! Those appear to be radically different examples (they’re not, actually). What are all those letters and numbers?
We need to discuss absolute mode and symbolic mode.
How do I use absolute mode?
Absolute mode is one of two ways of specifying permissions. I’ve seen this mode referred to as octal or numeric mode, but the term I learned was absolute. That term also makes the most sense to me because it’s an absolute statement of the desired permissions. I always told my students that this seemed like the most complex of the two modes but is actually the simplest. Usually, they agreed.
Each access level (read, write, execute) has an octal value:
| Access level | Octal value |
| Read | 4 |
| Write | 2 |
| Execute | 1 |
Each identity (user, group, others) has a position:
| Identity | Position |
| User | First or left-most |
| Group | Middle |
| Others | Last or right-most |
More Linux resources
The absolute mode syntax states the desired permissions from left to right.
How do I grant the user (owner) read, write, and execute, the group read-only, and all others no access to file2 by using absolute mode?
The three permissions values are associated with identities:
ugo
740
- The 7 is assigned to the user and is the sum of 4+2+1 or read+write+execute (full access)
- The 4 is assigned to the group and is the sum of 4+0+0 (read-only)
- The 0 is assigned to others and is the sum of 0+0+0 (no access)
In this example, the user has rwx, the group has r only, and all others have no access to file2 .
Let’s look at one more example.
How do I grant the user (owner) read and write, the group read-only, and all others read-only to file2 ?
- The user has 6 (read and write)
- The group has 4 (read-only)
- All others have 4 (read-only)
I find this easier because there are no calculations involved. I’m not concerned with adding or subtracting specific permissions based on the current settings. Instead, I say, «set the permissions to be this,» and that’s the end result I get. It’s an absolute statement.
How do I set permissions for the Resources directory and all of its contents by using absolute mode?
How do I use symbolic mode?
Symbolic mode uses more symbols, but the symbols are simpler to understand. That’s attractive to sysadmins that are new to standard Linux permissions.
Each access level has a symbol:
| Access level | Symbol |
| Read | r |
| Write | w |
| Execute | x |
Each identity has a symbol:
| Identity | Symbol |
| User | u |
| Group | g |
| Others | o |
There are also operators to manipulate the permissions:
| Task | Operator |
| Grant a level of access | + |
| Remove a level of access | — |
| Set a level of access | = |
The general chmod command syntax is the same:
Here is an example:
How do I remove the read permissions from others for file2 by using symbolic mode?
This example removes ( — ) the read ( r ) permission from others ( o ) for file2 .
Here’s another simple example:
How do I grant the read and write permissions to the group for file2 ?
This one gives ( + ) read and write ( rw ) to the group ( g ) for file2 .
How do I set permissions for a directory and all of its contents by using symbolic mode?
Special permissions and Access Control Lists
The above discussion covers standard Linux permissions—applying rwx to the user, group, and all others. Linux has far more flexibility, however. Special permissions permit users to run applications with other credentials, control the inheritance of group associations, and keep files from being changed accidentally. Check out this great article on special permissions.
Linux also has a way of enforcing different permissions for different users and groups. Access Control Lists (ACLs) permit sysadmins to define permissions for more than just one user and one group, which adds a great deal more flexibility to standard permissions. For example, user01 can be granted rw- to file1 , while user02 can be granted r— to file1 . Here is a great article on ACLs.
Wrap up
Creating resources, managing users, and setting permissions are fundamental tasks for Linux users. My goal was to provide a quick and easy guide based on common questions or tasks that we must all accomplish regularly. If you’re new to Linux, having a solid grasp of the eight commands discussed above will make your sysadmin life much easier.
Источник
Permissions
The Unix-like operating systems, such as Linux differ from other computing systems in that they are not only multitasking but also multi-user.
What exactly does this mean? It means that more than one user can be operating the computer at the same time. While a desktop or laptop computer only has one keyboard and monitor, it can still be used by more than one user. For example, if the computer is attached to a network, or the Internet, remote users can log in via ssh (secure shell) and operate the computer. In fact, remote users can execute graphical applications and have the output displayed on a remote computer. The X Window system supports this.
The multi-user capability of Unix-like systems is a feature that is deeply ingrained into the design of the operating system. If we remember the environment in which Unix was created, this makes perfect sense. Years ago before computers were «personal,» they were large, expensive, and centralized. A typical university computer system consisted of a large mainframe computer located in some building on campus and terminals were located throughout the campus, each connected to the large central computer. The computer would support many users at the same time.
In order to make this practical, a method had to be devised to protect the users from each other. After all, we wouldn’t want the actions of one user to crash the computer, nor would we allow one user to interfere with the files belonging to another user.
This lesson will cover the following commands:
- chmod — modify file access rights
- su — temporarily become the superuser
- sudo — temporarily become the superuser
- chown — change file ownership
- chgrp — change a file’s group ownership
File Permissions
On a Linux system, each file and directory is assigned access rights for the owner of the file, the members of a group of related users, and everybody else. Rights can be assigned to read a file, to write a file, and to execute a file (i.e., run the file as a program).
To see the permission settings for a file, we can use the ls command. As an example, we will look at the bash program which is located in the /bin directory:
Here we can see:
- The file «/bin/bash» is owned by user «root»
- The superuser has the right to read, write, and execute this file
- The file is owned by the group «root»
- Members of the group «root» can also read and execute this file
- Everybody else can read and execute this file
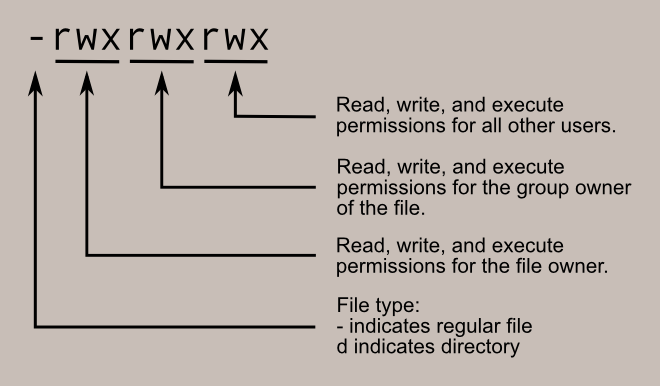
In the diagram below, we see how the first portion of the listing is interpreted. It consists of a character indicating the file type, followed by three sets of three characters that convey the reading, writing and execution permission for the owner, group, and everybody else.
chmod
The chmod command is used to change the permissions of a file or directory. To use it, we specify the desired permission settings and the file or files that we wish to modify. There are two ways to specify the permissions. In this lesson we will focus on one of these, called the octal notation method.
It is easy to think of the permission settings as a series of bits (which is how the computer thinks about them). Here’s how it works:
Now, if we represent each of the three sets of permissions (owner, group, and other) as a single digit, we have a pretty convenient way of expressing the possible permissions settings. For example, if we wanted to set some_file to have read and write permission for the owner, but wanted to keep the file private from others, we would:
Here is a table of numbers that covers all the common settings. The ones beginning with «7» are used with programs (since they enable execution) and the rest are for other kinds of files.
| Value | Meaning |
| 777 | (rwxrwxrwx) No restrictions on permissions. Anybody may do anything. Generally not a desirable setting. |
| 755 | (rwxr-xr-x) The file’s owner may read, write, and execute the file. All others may read and execute the file. This setting is common for programs that are used by all users. |
| 700 | (rwx——) The file’s owner may read, write, and execute the file. Nobody else has any rights. This setting is useful for programs that only the owner may use and must be kept private from others. |
| 666 | (rw-rw-rw-) All users may read and write the file. |
| 644 | (rw-r—r—) The owner may read and write a file, while all others may only read the file. A common setting for data files that everybody may read, but only the owner may change. |
| 600 | (rw——-) The owner may read and write a file. All others have no rights. A common setting for data files that the owner wants to keep private. |
Directory Permissions
The chmod command can also be used to control the access permissions for directories. Again, we can use the octal notation to set permissions, but the meaning of the r, w, and x attributes is different:
- r — Allows the contents of the directory to be listed if the x attribute is also set.
- w — Allows files within the directory to be created, deleted, or renamed if the x attribute is also set.
- x — Allows a directory to be entered (i.e. cd dir ).
Here are some useful settings for directories:
| Value | Meaning |
|---|---|
| 777 | (rwxrwxrwx) No restrictions on permissions. Anybody may list files, create new files in the directory and delete files in the directory. Generally not a good setting. |
| 755 | (rwxr-xr-x) The directory owner has full access. All others may list the directory, but cannot create files nor delete them. This setting is common for directories that you wish to share with other users. |
| 700 | (rwx——) The directory owner has full access. Nobody else has any rights. This setting is useful for directories that only the owner may use and must be kept private from others. |
Becoming the Superuser for a Short While
It is often necessary to become the superuser to perform important system administration tasks, but as we know, we should not stay logged in as the superuser. In most distributions, there is a program that can give you temporary access to the superuser’s privileges. This program is called su (short for substitute user) and can be used in those cases when you need to be the superuser for a small number of tasks. To become the superuser, simply type the su command. You will be prompted for the superuser’s password:
After executing the su command, we have a new shell session as the superuser. To exit the superuser session, type exit and we will return to your previous session.
In most modern distributions, an alternate method is used. Rather than using su , these systems employ the sudo command instead. With sudo , one or more users are granted superuser privileges on an as needed basis. To execute a command as the superuser, the desired command is simply preceded with the sudo command. After the command is entered, the user is prompted for the their own password rather than the superuser’s:
In fact, modern distributions don’t even set the root account password thus making it impossible to log in as the root user. A root shell is still possible with sudo by using the «-i» option:
Changing File Ownership
We can change the owner of a file by using the chown command. Here’s an example: Suppose we wanted to change the owner of some_file from «me» to «you». We could:
Notice that in order to change the owner of a file, we must have superuser privileges. To do this, our example employed the sudo command to execute chown .
chown works the same way on directories as it does on files.
Changing Group Ownership
The group ownership of a file or directory may be changed with chgrp . This command is used like this:
In the example above, we changed the group ownership of some_file from its previous group to «new_group». We must be the owner of the file or directory to perform a chgrp .
Further Reading
- Chapter 9 of The Linux Command Line covers this topic in much more detail.
© 2000-2021, William E. Shotts, Jr. Verbatim copying and distribution of this entire article is permitted in any medium, provided this copyright notice is preserved.
Linux® is a registered trademark of Linus Torvalds.
Источник